Fake Adam Levine “Blind Audition” Video Spreads Adware on Facebook
When Maroon 5 lead singer Adam Levine decided to go through the blind audition for “The Voice 8” despite being a longtime judge, he joked, “I’m so terrified.” Little did he know that just a week after that, Internet users are to chance upon fake spam links of his blind audition video, the routines of which can lead to equally disturbing results: adware downloads.
[Read: 9 Social Media Threats You Need To Be Aware Of]
Using words copied from a news source, the fake spam link on the photo below appear legitimate and compelling. Any unknowing newsfeed browser who sees it may easily mistake it for the real deal.
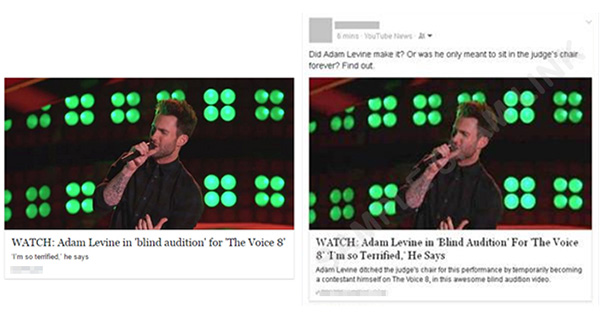
Original video link (left) versus spam link (right)
However, comparing the two, the differences in the title and blurb used are apparent. The link from the fake video link, when checked using the Trend Micro Site Safety Center, revealed that the URL is categorized as a source of malicious software.
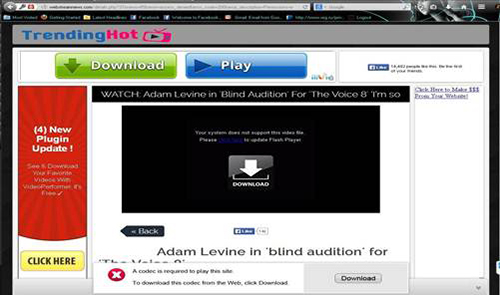
Users who click on the link are asked to give permission for their profile to be linked to a video player’s page, which then redirects them to another website that asks them to install a suspicious video player. The file is detected as ADW_BRANTALL, an installer bundled with potentially unwanted applications.
As of this writing, the total volume of traffic to the two links in this threat has reached almost 17,000. The first link used to lure Facebook users was mostly accessed by victims in the United States (29.94%), Singapore (22.01%), the Philippines (21.07%), Australia (4.95%) and New Zealand (4.33%).
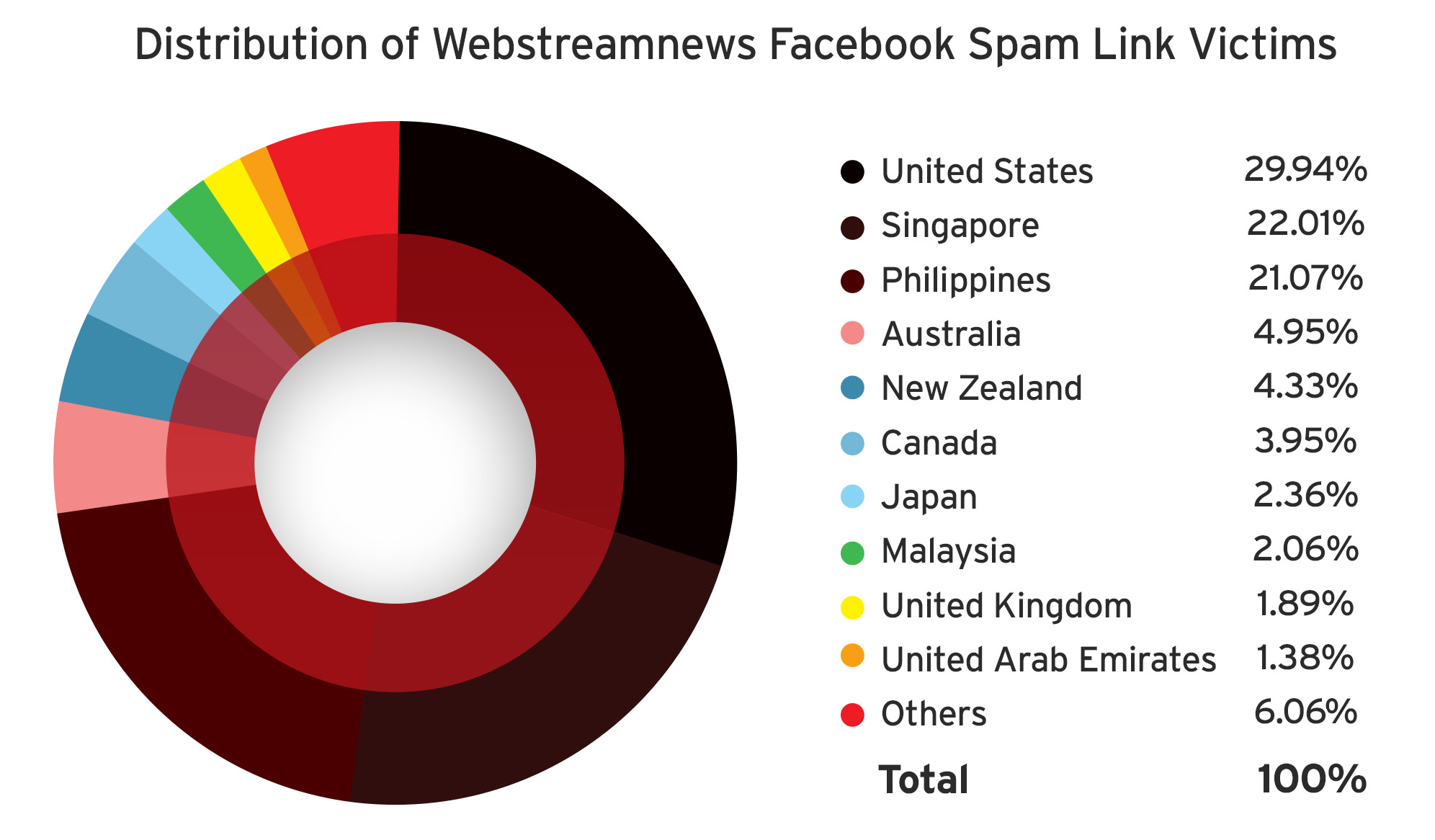
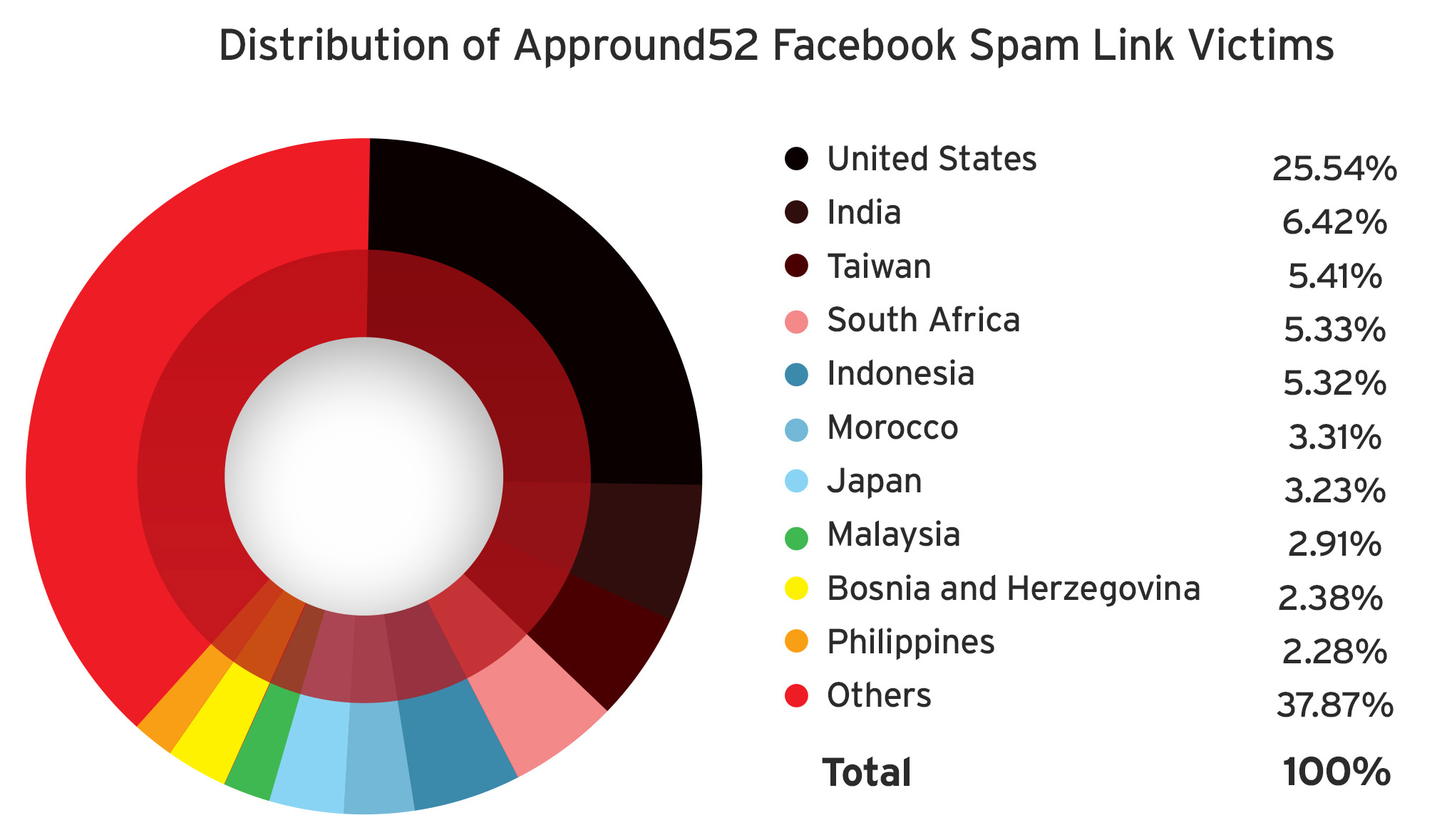
Attention to Adware
Adware, though not inherently malicious, is a type of software that causes unwanted effects on a system, such as pop-up advertisements and, in some instances, can slow down network connections and affect system performance.
Recently, there were reports of certain consumer-grade Lenovo laptop models that were shipped with a visual search technology that not only exhibited adware behaviors, but also allowed cybercriminals to snoop into secure communications via man-in-the-middle (MitM) attacks.
[Read: Superfish Adware in Lenovo Consumer Laptops Violates SSL, Affects Companies via BYOD]
Sometimes, adware can also pose risks to end users, as in the case of the MEVADE/SEFNIT malware, which was downloaded to victim’s computers after adware was installed.
[Read: Adware Gone Bad: The Adware and MEVADE/SEFNIT Connection]
What To Do About This Threat
Social media sites are rife with social engineering lures that cybercriminals use to piggy-back on breaking news and viral topics. Sometimes, they make the celebrity news themselves, such as the time when news of Beastie Boys’ Adam Yauch’s death led to malware downloads.
[Read: The Most Popular Social Engineering Lures Used in 2014]
The first step to avoid being victimized by similar threats is knowing what to watch out for. In this case, it's always wise to check the link and to only click on trusted sources, especially when it comes to viral or highly compelling topics. Should you click on a wrong link, always be aware of red flags such as sites that ask for permission to access your profile or ones that require you to download software you’re not familiar with.
For better protection, you can use security software that aggregates information in real time to catch high risk and malicious routines before they even run on your system.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks