Zgodność z przepisami i ryzyko
World Tour Survey: Cloud Engineers Wrestle with Risk
Trend surveyed 750 cybersecurity professionals in 49 countries to learn more about the state of cybersecurity, from job pressures to the need for more advanced tools. Explore what cloud security engineers teams had to say.
Cybercriminals have more tools than ever to disrupt business operations, steal data for ransom, and manipulate employees into exposing sensitive information. Generative AI (GenAI) is taking those capabilities to new levels by enhancing phishing attacks and enabling audio and video deepfakes.
Security professionals are also facing new pressures from chief executives and corporate boards who increasingly understand the legal, financial, and reputational risks cyber threats pose to businesses.
To find out how these and other developments are shaping the day-to-day experience of cybersecurity professionals worldwide, Trend conducted its inaugural Risk to Resilience World Tour Survey. We surveyed more than 750 cybersecurity professionals in 49 countries, with a focus on four key roles:
- Chief information security officer (CISO) –Read more here.
- Security operations center (SOC) team – Read more here
- IT operations staff – Read more here
- Cloud security engineers
This blog explores our findings from cloud security engineer respondents. Check out the full report, The Defenders, to read about the other roles.
Cloud security engineers: Letting in the light
Modern enterprises depend on cloud services, applications, and infrastructure—making the protection of cloud assets and services vitally important. The expertise of cloud security engineers is required to provide visibility into the full range of cloud exposures.
Compliance is critical
While organizations can benefit immensely from the cloud, compliance needs to accounted for. Cloud environments require special protection because they typically store sensitive data that is governed by strong compliance requirements for data storage, protection, and transaction management. Customer data and personal identifying information (PII) breaches run the risk of negatively impacting your financial and/or reputational standing.
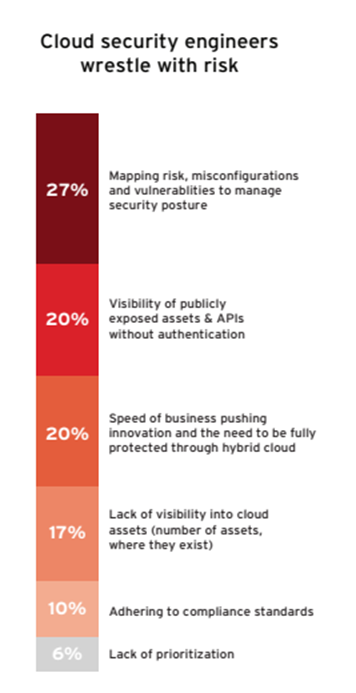
Gaining full visibility into cloud vulnerabilities, misconfigurations, and threat activity helps mitigate this risk. Yet cloud telemetry has long been siloed from the rest of the security stack. Cloud security engineers understand that this needs to change, with survey results indicating that mapping risk, misconfigurations and vulnerabilities is their top challenge (27%) when implementing and maintaining cloud security. Misconfigurations in particular continue to be the primary access point for attackers into cloud infrastructure.
Minimizing exposure at high speed
The Risk to Resilience World Tour Survey indicates that cloud security engineers face other challenges as well. These include visibility of publicly exposed assets and APIs (20%) as well as, at the same percentage, businesses pursuing innovation while needing to fully protect data and applications in hybrid cloud environments.
What’s needed most are tools to empower cloud security team analysts by enabling them to correlate data and automate responses across hybrid and multi-cloud environments. Operations then benefit from consolidation between cloud telemetry from the broader environment. This provides a single, streamlined view, integrating cloud risk with the rest of the IT environment.
Despite these risks and challenges, cloud security engineers are generally confident about their organizations’ ability to mitigate cloud risk and maintain compliance. 92% rate their confidence three or higher on a scale of five. A similar majority is confident in their ability to respond to cloud security threats, with 88% rating theirs in this regard at three or higher and 25% at five.
The paths to managing cyber risk are converging
CISOs and security teams battle with resource constraints. IT operations seek greater integration. Cloud security engineers strive for expanded visibility. All of these needs can be addressed with the AI-powered automation, contextualized data, and integration of a platform-based approach to cybersecurity.
Consolidating security within a single platform that can integrate third-party toolsets gives security leaders what they need with more flexibility, greater efficiency, minimized sprawl, and reduced total cost of ownership.
This approach meets security teams where they’re at and respects the investments organizations have made to date, while transforming working models to drive strong user experience and security outcomes. Rich telemetry is more readily available, empowering teams to make more proactive and effective risk remediation decisions.
Trend Vision One™ delivers the benefits of a platform approach with comprehensive protection, prevention, detection, and response capabilities—all powered by AI and leading threat research and intelligence. It supports diverse hybrid IT environments, automates and orchestrates workflows, and delivers expert cybersecurity services to simplify and converge security operations holistically—all while measuring and communicating overall risk management and performance to stakeholders.
Explore more resources:
- Read the full report
- Intercepting Impact: 2024 Trend Micro Cyber Risk Report
- Explore our Trend Vision One platform

