Cyberzagrożenia
Attackers in Profile: menuPass and ALPHV/BlackCat
To test the effectiveness of managed services like our Trend Micro managed detection and response offering, MITRE Engenuity™ combined the tools, techniques, and practices of two globally notorious bad actors: menuPass and ALPHV/BlackCat. This blog tells the story of why they were chosen and what makes them threats to be reckoned with.
MITRE Engenuity released its most recent ATT&CK Evaluation report for managed security services on June 18, where Trend achieved 100% detection across all 15 major steps.
Each MITRE Engenuity evaluation features a specific attack, and never the same one twice. For this year’s managed services evaluation, it was the double-whammy of a menuPass and ALPHV/BlackCat ransomware scenario that put managed service providers through their paces—and also reveals some of the complexities involved in threat detection and response.
Why menuPass and ALPHV/BlackCat?
In its news release announcing the managed services evaluation, MITRE Engenuity shared the sobering statistic that 58% of organizations count on some form of managed service to augment their security operations center (SOC), but only about half have confidence in their provider’s team or technology.
Since MITRE Engenuity’s stated goal for the evaluation was to “...provide end-users with clear, objective insights into the defensive capabilities of participants,” a strong attack would have been a natural prerequisite. menuPass and ALPHV/BlackCat both fit that bill, being known for sophistication and deceptiveness.
Given that managed services are the target, it would also make sense for MITRE Engenuity to pick a threat actor known for going after managed service providers. menuPass checks that box, with a reputation preying on organizations’ weakest security links.
Additionally, while most ransomware is designed for Microsoft Windows, ALPHV/BlackCat has also been used to attack Linux, which is often used on servers. Many small and mid-sized companies rely on third-party providers for security management.
Finally, there’s the practical consideration of needing a well-understood model to simulate an authentic, real-world attack. menuPass and ALPHV/BlackCat use known tactics, techniques, and procedures (TTPs) that make them easy to work with.
But who—and what—exactly are menuPass and ALPHV/BlackCat?
Eyes on the bad guys
While none of the evaluation participants knew the attack they’d be up against, Trend had the advantage that its threat research team had long been studying both menuPass and ALPHV/BlackCat and amassed deep insights to inform its managed detection and response (MDR) defenses.
In fact, Trend Micro coined the name menuPass to identify the threat actor group also known as APT10 (APT stands for advanced persistent threat) and ChessMaster. It has at least two subgroups: Earth Tengshe and Earth Kasha, both of which use custom malware for espionage-related exploits in a wide range of regions. menuPass (aka APT10 Umbrella) has been active since at least 2006.
Earth Tengshe and Earth Kasha tend to target public-facing applications with the aim of exfiltrating data and information in the network, a tactic that’s fairly common among threat actors whether their motivation is espionage or extortion.
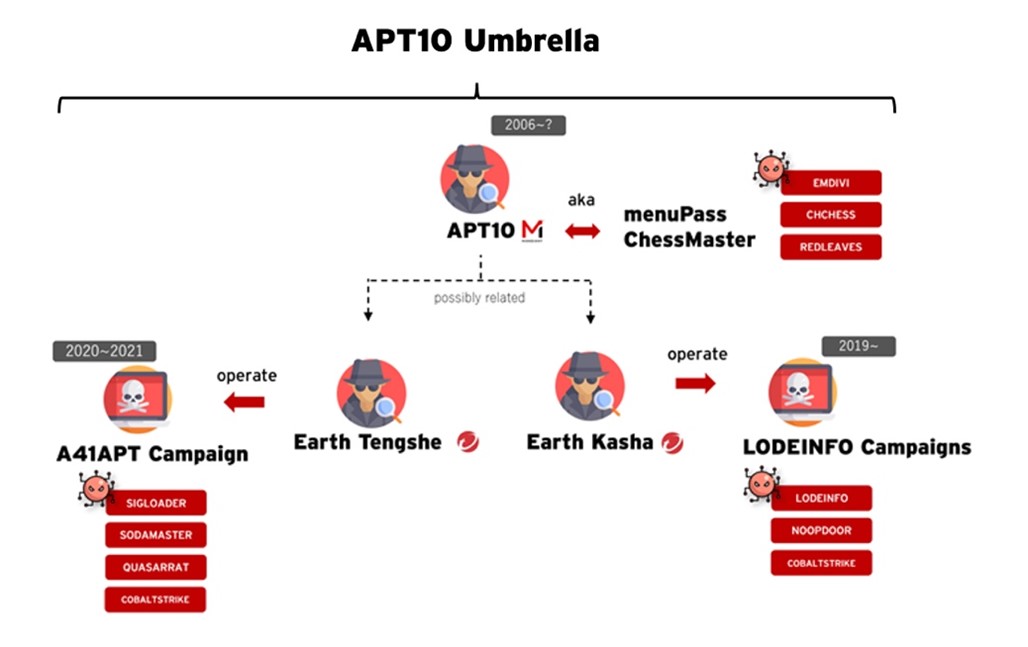
The structural complexities of menuPass/APT10 Umbrella points to one of the basic challenges of threat intelligence: threat actors are not always tidily defined or homogenous.
ALPHV/BlackCat brings its own wrinkles to the puzzle. Sometimes it is regarded as a Rust-based ransomware available as a service and sometimes it’s referred to as the threat actor group responsible for producing and overseeing that as-as-service offering.
MITRE Engenuity clearly puts ALPHV/BlackCat in that latter bucket, explaining, “A ransomware-as-a-service operation, ALPHV/BlackCat emerged in 2021, targeting various industries with a flexible ransomware strain capable of cross-platform attacks on Windows, Linux, and VMware systems.”
MITRE Engenuity borrowed “signature behaviors” from both menuPass and ALPHV/BlackCat to mount a “multi-subsidiary compromise with overlapping operations focusing on defense evasion, exploiting trusted relationships, data encryption, and inhibiting system recovery.”
From menuPass, the evaluation took a mix of living-off-the-land techniques, custom, fileless malware, anti-analysis tactics, and exploitation of trusted third-party relationships for credential access. It copied ALPHV/BlackCat defense evasion techniques as well, along with data exfiltration, data encryption, data destruction, and system recovery obstruction.
Where are they now?
While the TTPs used for the MITRE Engenuity managed service evaluation are well known and documented, threat actors don’t stay frozen in time. Trend™ Research is continuing to track both menuPass and ALPHV/BlackCat.
As a state-sponsored cyber espionage group, menuPass (APT10 Umbrella) is constantly shifting targets based on whatever nation state is paying them. Its goals are generally the same: brokerage of information, and theft of personally identifying information and related activities. In 2018 it was reported that members of the group had been indicted, but the group itself has since resurfaced, creating a splash during the pandemic with apparent (unsuccessful) intrusions against Indian vaccine makers and then playing a role in the A41APT multi-industry data theft campaign.
Because menuPass has so many subgroups and splinters, it’s imprecise to attribute any specific campaign to the umbrella entity, or to consider any single motive, toolset, or TTP to be definitively identifying.
The ALPHV/BlackCat group that ‘inspired’ the MITRE Engenuity attack approach for this year’s managed services evaluation is defunct, splitting up in an internal fight over the ransom paid by Change Healthcare in winter 2024. Even so, ransomware threat actor groups have a tendency to burn out, reform, and resurface since ransomware is a lucrative business.
In general, threat actors’ TTPs are becoming increasingly similar in response to cybercrime ‘best practices’ and evolving security techniques.
Threat intelligence is critical
Defending against actors like menuPass and ALPHV/BlackCat requires a combination of advanced cybersecurity tools and leading threat intelligence. The importance of the second part of that formula can’t be understated. Knowing where a threat is coming from, what’s likely motivating it, and what the attackers’ next moves may be can all aid better, more effective decisions for tracking and mitigating threats.
Trend Micro™ Managed Detection and Response (MDR) service is built on our Trend Vision One™ platform and informed by Trend Research threat intelligence and the findings of our Trend Micro™ Zero-Day Initiative™ (ZDI). Trend Vision One provides the automated detection and response capabilities, while the understanding of threat behaviors and how to handle them comes from Trend Research.
Beyond advanced persistent threats and ransomware, other major focuses of Trend Research today include securing AI, cloud, and network threats and understanding the risk landscape overall—what it’s made of and how it’s changing. We’re committed to continuing our work to bring insight to cybersecurity to provide the most effective managed security services possible and drive the advancement of security technologies.
Next steps
For more on our Trend MDR, XDR, and other related topics, check out these additional resources:

