On June 2023, the SANS Institute published a new report, “Breaking IT/OT Silos With ICS/OT Visibility” written by Jason Christopher, SANS analyst, with the cooperation of Trend Micro. This survey explores how respondents tackle ICS/OT visibility challenges, the gaps across the IT-OT boundary, the roadblocks to expanding visibility, and the maturity comparisons from both domains. This survey had nearly 350 respondents responsible for IT and OT security across a wide variety of industrial sectors worldwide.
This article discusses the challenges of current OT visibility while referring to the essence of the report.
The cybersecurity capability in OT is less mature than in IT
In this survey, we asked participants whether OT security for cybersecurity capabilities is less mature or more mature than IT in their organizations with reference to the NIST CSF.
As an average of all items, 39.5% answered that OT has a lower level of maturity. (18% answered OT security is more mature, and 36.4% at the same level)
Categorizing security capabilities into the five cores of the NIST CSF and aggregating them for each core, the most was that Detect is lower maturity in OT security than in IT. (42%)
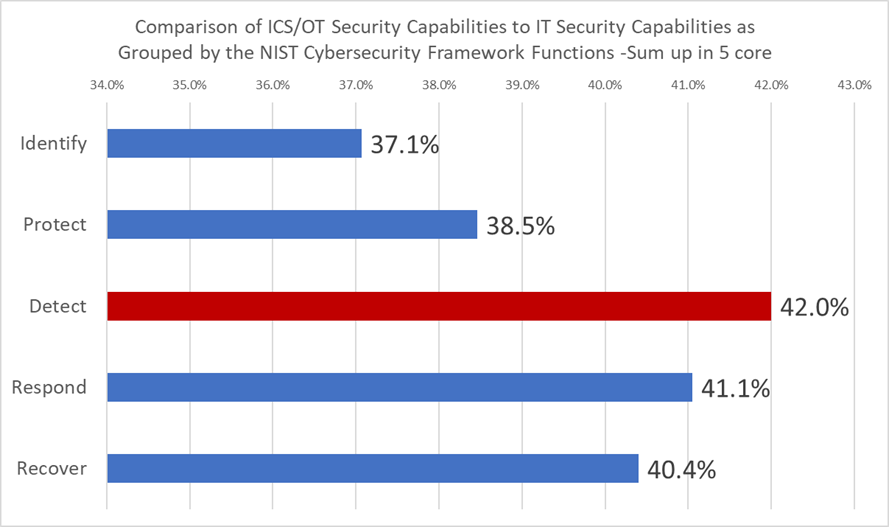
Furthermore, looking at the specific security capabilities, the score of “Cyber event detection” is the most(45.7%).
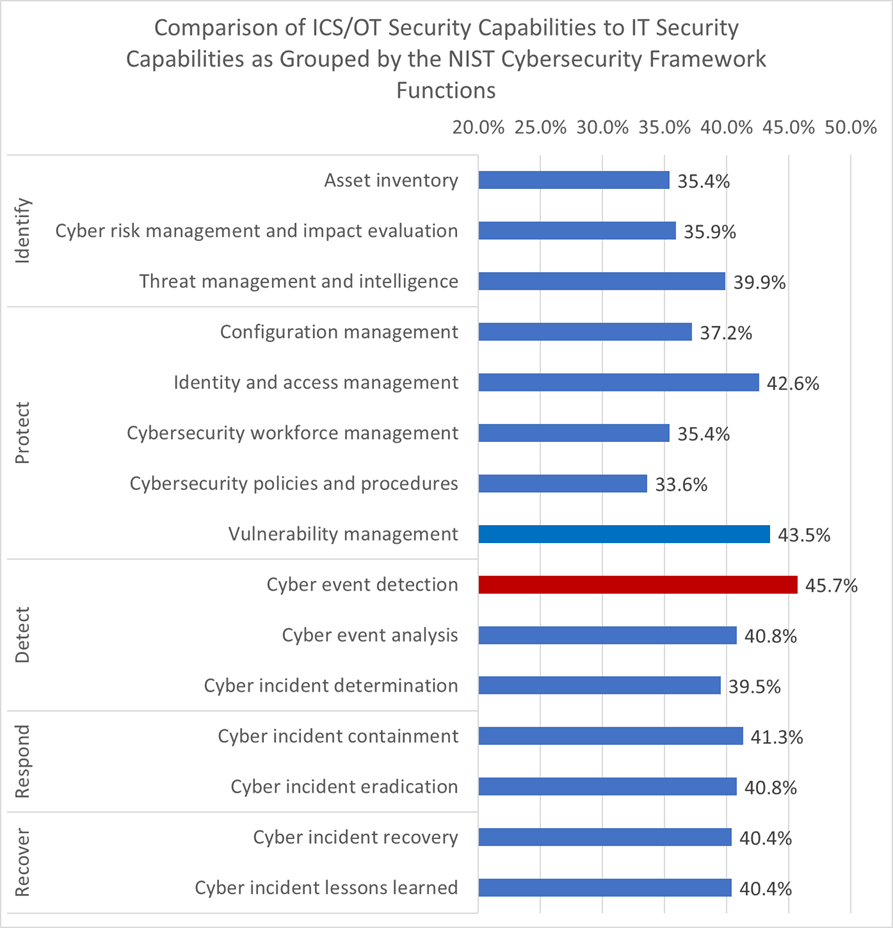
The OT environment has more diverse legacy assets, and protocol stacks dedicated to ICS/OT, making it difficult to implement sensors to detect malicious behavior or apply the patches on the assets. The inability to implement uniform measures in the same way as IT security is an obstacle to increasing the maturity level.
Detection in OT: Endpoint and Network
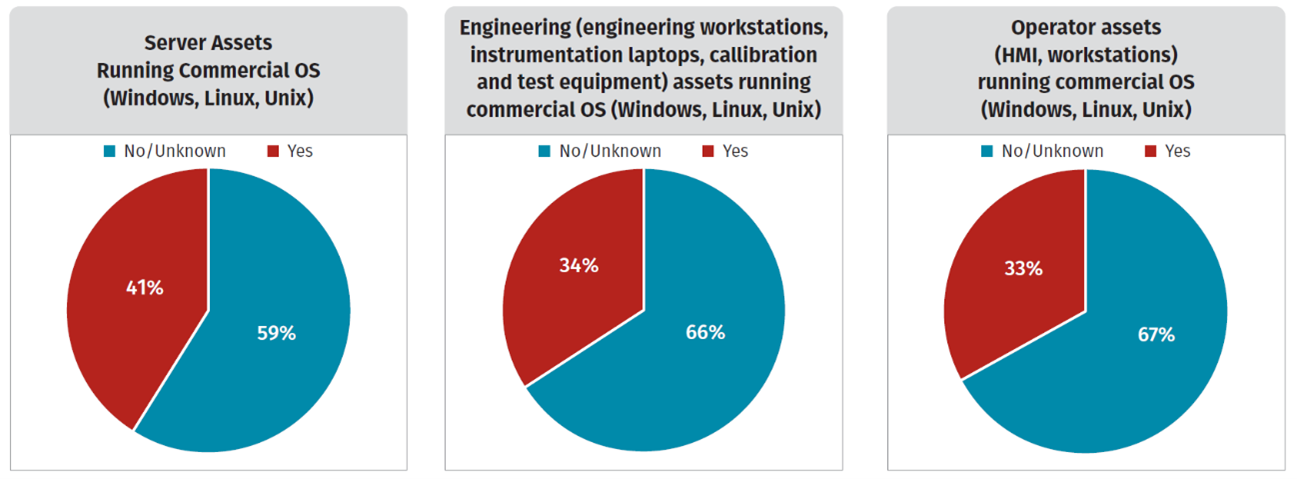
The survey asked respondents about their Endpoint Detection and Response (EDR) and Network Security Monitoring (NSM) implementations to measure their visibility in their OT environments. They answered whether EDR (including antivirus) was implemented in the following three places.
- Server assets running commercial OS (Windows, Linux, Unix): 41%
- Engineering (engineering workstations, instrumentation laptops, calibration and test equipment) assets running commercial OS (Windows, Unix, Linux): 34%
- Operator assets (HMI, workstations) running commercial OS (Windows, Linux, Unix): 33%
In addition, 76% of organizations that have already deployed EDR said they plan to expand their deployment within 24 months.
We also asked whether NSM (including IDS) was implemented at the following levels referring to the Purdue model.
- Purdue Level 4 (Enterprise): 30%
- Purdue Level 3.5 (DMZ): 36%
- Purdue Level 3 (Site or SCADA-wide): 38%
- Purdue Level 2 (Control): 20%
- Purdue Levels 1/0 (Sensors and Actuators): 8%
Like EDR, 70% of organizations that have already implemented NSM said they have plans to expand implementation within 24 months.
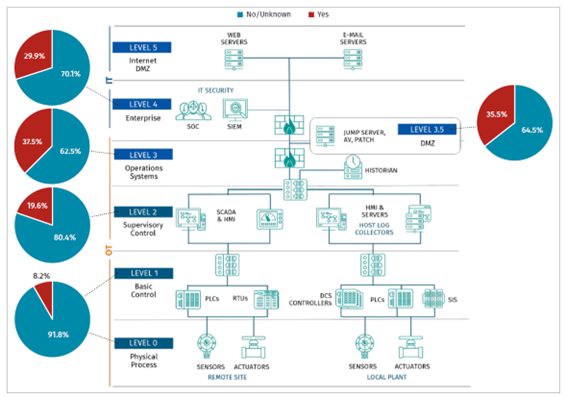
In this survey, EDR implementation rates tended to vary depending on the respondent's industry and size of organization. The implementation rate of NSM was relatively high in DMZ and Level 3, and the implementation rate decreased according to the lower layers. But I think it is not appropriate to conclude the decisive trend from the average value in the questions, because there are variations in the places where they are implemented EDR and NSM depending on the organization. The implementation rate shown here is just a rough standard. Where and how much to invest depends on the environment and decision-making of the organization. Asset owners can use the result as a reference to see where to implement EDR and NSM and evaluate their implementation plans.
To learn about how to assess risk in your OT environment to invest appropriately, please refer to our practices of risk assessment in smart factories.
Reference:
Breaking IT/OT Silos with ICS/OT Visibility - 2023 SANS ICS/OT visibility survey

