Złośliwe oprogramowanie
SeroXen Mechanisms: Exploring Distribution, Risks, and Impact
This is the third installment of a three-part technical analysis of the fully undetectable (FUD) obfuscation engine BatCloak and SeroXen malware. In this entry, we document the techniques used to spread and abuse SeroXen, as well as the security risks, impact, implications of, and insights into highly evasive FUD batch obfuscators.
The remote access trojan (RAT) SeroXen tool can be purchased on the clearnet. During our investigation, we uncovered multiple domains selling not only this nefarious tool but also a cracked version of it hosted on a popular crack forum. We also uncovered individuals on popular video sites such as YouTube and TikTok acting as distributors for this piece of fully undetectable (FUD) malicious software. At the time of writing, many of these videos remain available for viewing.
This is the final installment of a three-part series delving into BatCloak and SeroXen. The first entry, titled “The Dark Evolution: Advanced Malicious Actors Unveil Malware Modification Progression,” looked into the evolution of the BatCloak obfuscation engine, while the second part, titled “SeroXen Incorporates Latest BatCloak Engine Iteration,” discussed the SeroXen malware and its inclusion of the latest iteration of BatCloak to generate an FUD “.bat” loader.
Distribution methods: SeroXen’s online platforms
In this section, we break down the different platforms that SeroXen uses to spread malware.
Website

The tool SeroXen sports a sleek website with pages that users might expect from any number of websites selling software on the internet. However, sometime between the last week of May and the first week of June, a new shutdown notice has surfaced on its website due to SeroXen’s popularity and cybercriminal efficacy. Considering the content of the notice, there are strong indications that this shutdown is merely for show and that distribution is still ongoing through other platforms and channels.
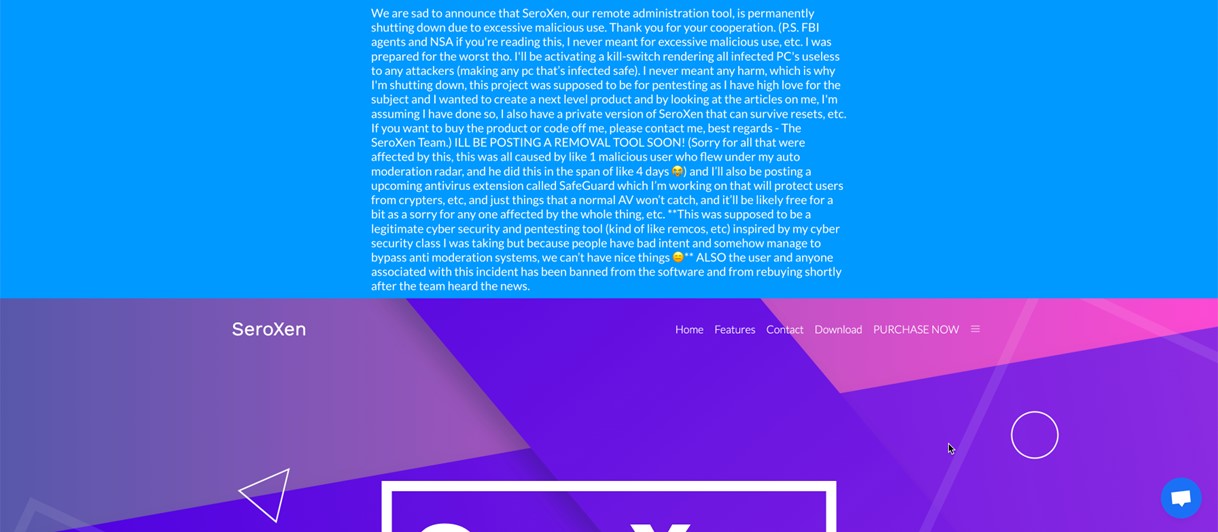
Prior to the shutdown notice, we observed the main SeroXen website offering a comprehensive list of features to prospective consumers. Examining some of the core features advertised by SeroXen shows a rich feature selection, including:
- A Windows Defender-guaranteed bypass for both scan time and runtime.
- FUD scan time and runtime evasion against most antivirus engines.
- Hidden Virtual Network Computing (hVNC).
- Full modern Windows support.

In addition to the sophisticated evasion and FUD component, the inclusion of hVNC is concerning as it is often deployed by highly sophisticated types of malware and advanced persistent threat (APT) groups. The hVNC component allows threat actors to operate a hidden or “virtual” desktop rather than the main desktop to keep the malicious sessions in the background running uninterrupted.
Meanwhile, the SeroXen web application provides users with the option to acquire either a monthly license key or a lifetime key using cryptocurrency.
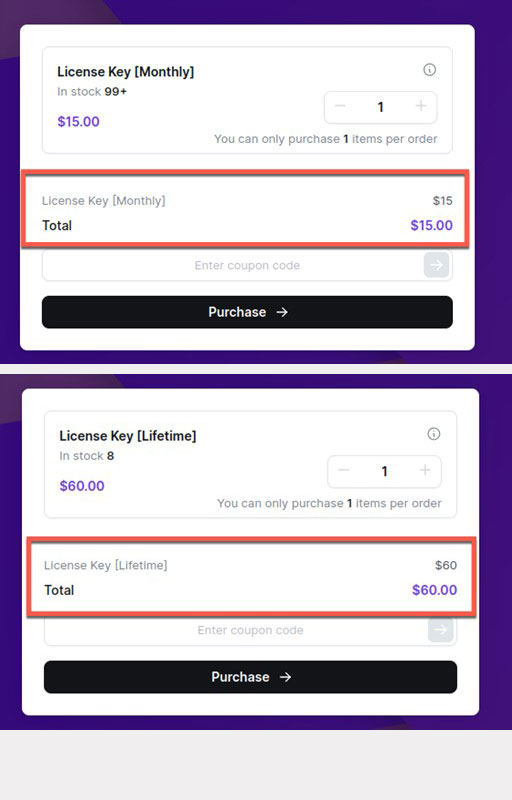

The SeroXen web application also boasts a product support team available from Monday to Friday following a location for a time zone reference in the US. The Telegram account of the developer is also available for messaging, and the relevant channels are still active. At one point, a Discord account might also have been available for contact, although it was already unavailable at the time of this writing.

During our investigation, we encountered the disclosure of the developers and contributors associated with SeroXen’s development. Notably, the list includes the individual who also contributed to the creation of batch obfuscators such as Jlaive, BatCrypt, CryBat, Exe2Bat, and ScrubCrypt. This direct linkage therefore establishes a clear association between these historical FUD batch obfuscators and the SeroXen malware. In June, we also noticed that the website’s acknowledgments included the social media handle of the distributor.

Social media accounts
While investigating SeroXen’s website, we uncovered a link to a review video hosted on YouTube.

The content is presented as a "review" and facilitated by a reseller. More importantly, it functions not only as an evaluation but also as a promotional advertisement coupled with a tutorial showcasing the capabilities of SeroXen. We found a collection of videos that was also attributed to a reseller of the malware. These videos function to endorse and market SeroXen, reinforcing its presence and appeal within the designated market. Details such as knowledge, discounts offered, and claims of being a distributor indicate the increased likelihood of this user being connected to the owner of the web app.


Certain prospective customers of SeroXen have demonstrated an inclination toward exploring specific aspects associated with illicit activities. Their expressed interest encompasses the use of SeroXen in the context of engaging in potentially unlawful endeavors within the Roblox community.

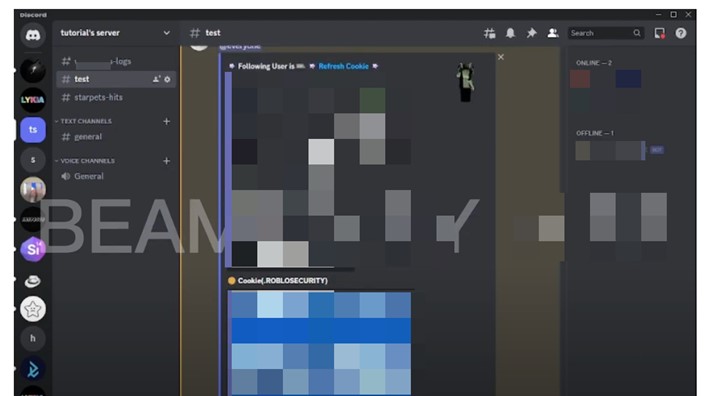
For context, Roblox is a widely popular video game with a user base of over 214 million active monthly users across the globe, predominantly comprised of minors, with approximately 67% of the player demographic aged below 16 years. In the US, over half of Roblox players are minors. In Figure 10, the significance of the inquiry lies in the potential risks and impact associated with the theft of the .ROBLOSECURITY cookie from an unsuspecting victim. If successfully stolen, this cookie would grant a threat actor the ability to compromise the targeted Roblox account by overriding two-factor authentication (2FA).
This exchange also highlights the risk associated with highly evasive and modular types of malware — namely, a modular design with the ability to load additional components to create a bigger impact on targeted and unwitting victims. In this instance, the reseller mentions the ability to use SeroXen with Hazard, a stealer with many features, including the capability to steal Discord webhooks.
At one point, the distributor sold SeroXen on Discord, but their accounts have a history of being terminated. In an exchange with a prospective customer on YouTube, a YouTube channel owner shows a clear understanding of how this tool will be used for criminal activity, after which they encourage a prospective customer to get in touch with them since they are a reseller. We also uncovered the reseller’s Twitter profile, which hosted more promotional content for SeroXen.
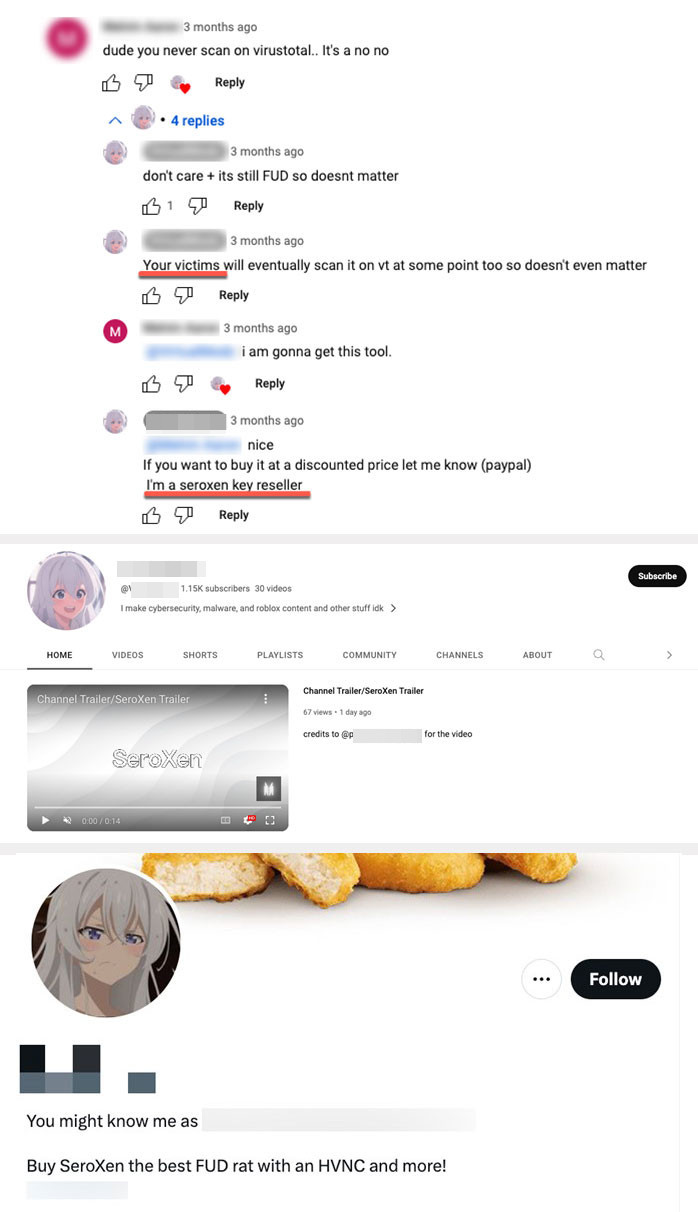
As of this blog entry’s week of publishing, we noted that the social media distributor confirmed that SeroXen’s “sale” (referred to only as “offsale” on the website) is now offline. Still, this mainstream availability and exchange raise substantial concerns, given its occurrence outside the boundaries of underground hacking forums. While researchers and ordinary users alike might expect this kind of complacence and leeway on the darknet, they do not expect the same on a popular mainstream platform such as YouTube. This underscores the potential implications of the exchange, as it indicates that cybercriminals have become bolder in infiltrating mainstream platforms online. In turn, malicious activities and discussions related to illicit cybersecurity practices are now able to infiltrate mainstream online platforms.
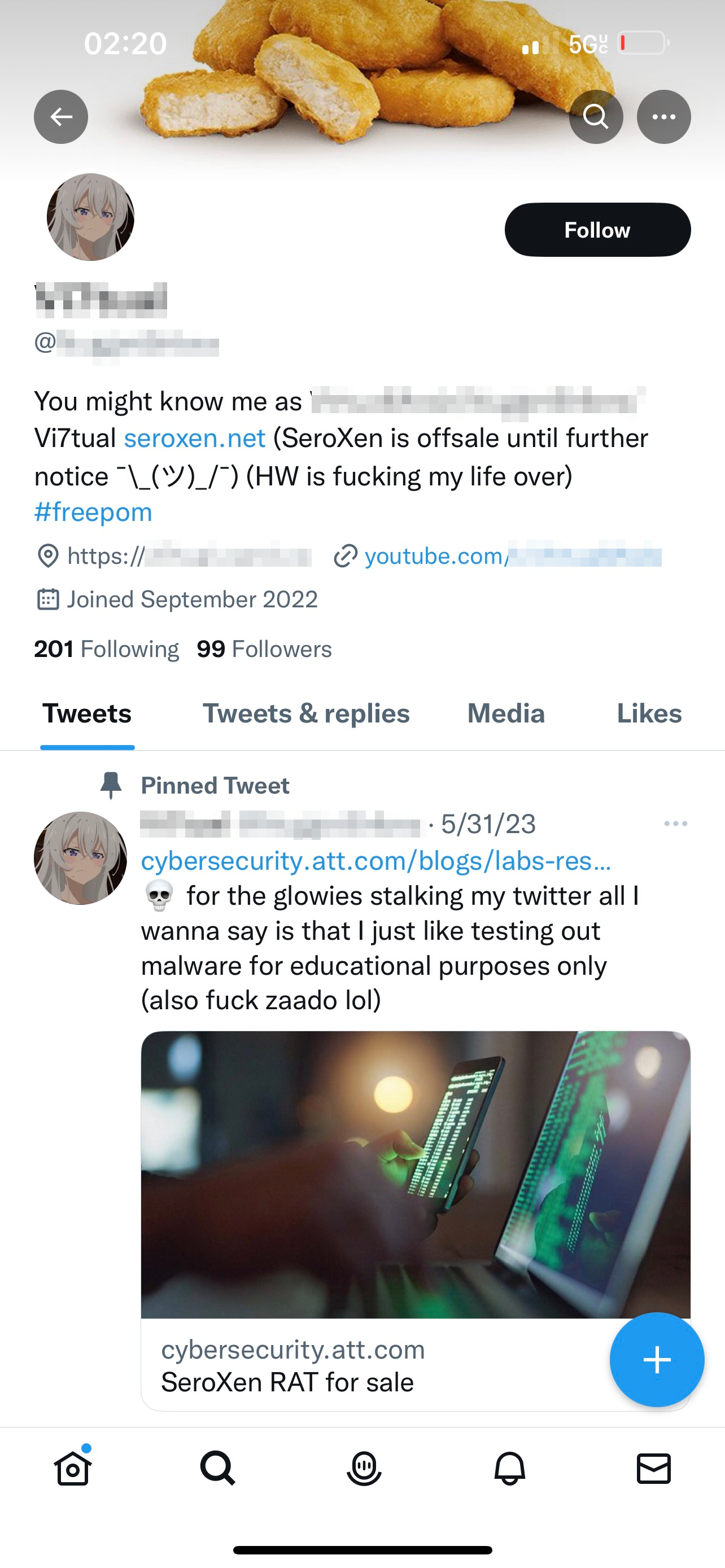
Additionally, during the investigation of this reseller’s YouTube profile we uncovered a batch-to-dropper file uploaded to Virus Total around the time of the latest SeroXen promotional video. The name of the batch file matches the username of this reseller’s YouTube profile. This batch attempts to download an infected batch file from Discord and run the infected file that leads to a SeroXen infection.


SeroXen’s forum presence
We also discovered that the author of SeroXen actively engages with prominent hacking enthusiast forums to promote and distribute the malware. This strategic use of established forums catering to the hacking community serves as an additional avenue for the author to market and sell SeroXen, expanding its reach.

Upon investigating the post of SeroXen’s developer, we saw that the author of Jlaive, BatCrypt, CryBat, Exe2Bat, and ScrubCrypt was once again acknowledged as playing a part in the development of SeroXen’s FUD capabilities. Additionally, on another forum, we found a cracked version of SeroXen that allows cybercriminals to bypass the payment requirement set up by the malware’s original developers.


Examining the prevalence and impact of SeroXen
Throughout our investigation of the scope of infections, we discovered a substantial collection of forum posts containing reports from victims who fell prey to the SeroXen infection. This particular strain of malware showed a notable increase in users reporting their infections, with well-meaning individuals advising victims to implement security and antivirus solutions, which all failed to detect any malicious activity. This then perpetuates a distressing cycle of infections driven by the malware's FUD capabilities.
Understanding SeroXen infections through an analysis of community discussions
We conducted an analysis on Reddit by analyzing reports of SeroXen infections. Many of these posts reported that the users noticed suspicious actions but were powerless to remediate the ongoing infection.
We went through different forum threads and observed a common theme among the scores of individuals whose systems were infected: they were downloading and executing highly suspect pieces of software hosted on Discord and other file-hosting services related to special interests. We also noticed reports of deceptive batch installers (downloaded from GitHub) claiming to be legitimate software installers or tools for highly sought-after applications and interests like Photoshop, image loggers, TikTok, quality-of-life tools, and Tor, among others. The primary intention behind this fraudulent activity is to lure unsuspecting individuals into unintentionally installing malicious programs that lead to compromise.

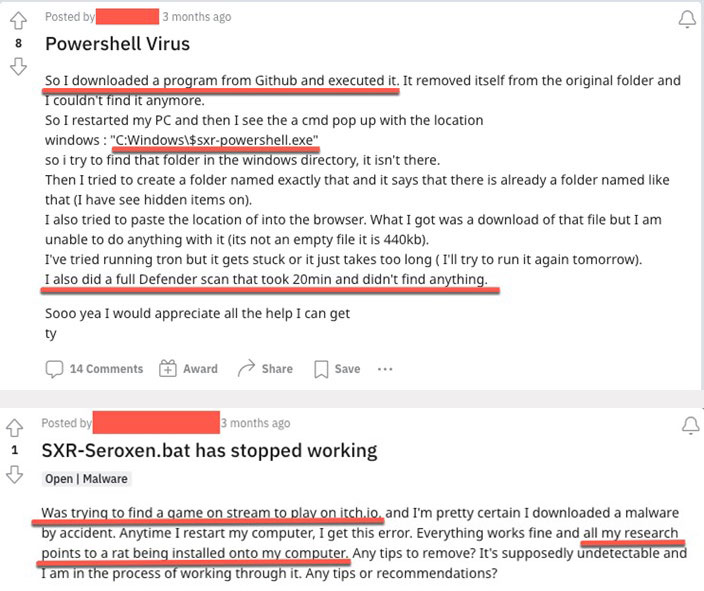
Based on our analysis of the collected samples, one of the largest target communities are gamers playing popular titles such as Roblox, Valorant, Counter Strike, Call of Duty, and Fortnite. These multiplayer online games contain a rich ecosystem of desirable, high-value, and in-game items that make a rich in-game economy, making them a viable target of malicious actors using SeroXen. In particular, theft appears to be the primary motive driving these infections. Over the years, a thriving underground ecosystem has been established for the illicit resale of stolen in-game items, with a particular emphasis on the popular game Roblox via beaming.
What is Roblox beaming?
Within the Roblox community, the unauthorized sale of items, referred to as "beaming" in the community, has proven itself to be an immensely profitable venture for nefarious actors. It is worth noting that certain rare items within Roblox, known as “limiteds,” can command significant prices that reach thousands of dollars in real-world commercial values. Discord has served as fertile ground for buying and selling these items, allowing cybercriminals to exploit and profit from unsuspecting children who fall victim to their schemes.
During our investigation, we uncovered a thriving underground community using Discord to post stolen cookies to beam victims. Frequently, the practice of beaming is employed to generate content specifically intended for popular online platforms like YouTube and TikTok. Numerous individuals, often including minors, are subjected to beaming for the purpose of entertainment. Over the course of our investigation, we also uncovered many instances of beaming tutorials and how-to videos on both TikTok and YouTube.
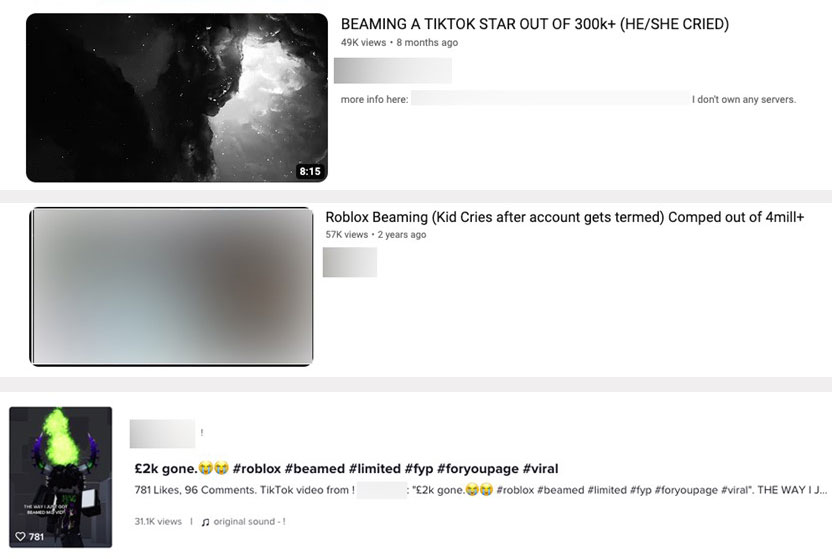
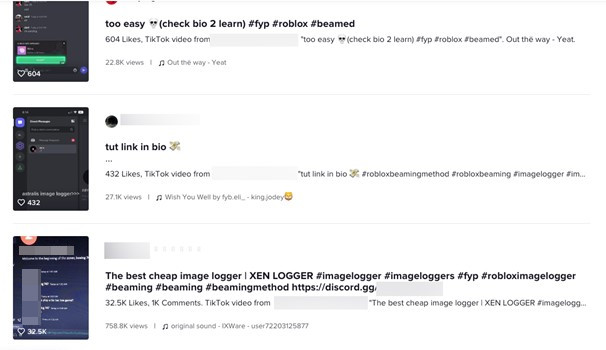
Furthermore, our findings have revealed that these video platforms frequently function as recruitment platforms, funneling individuals into beaming Discord channels to engage in unethical and detrimental activities.

FUD batch obfuscation techniques coupled with hVNC-capable toolkits provide actors powerful tools not only for stealing content but also for creating significant psychological distress in communities with a significant number of minors.
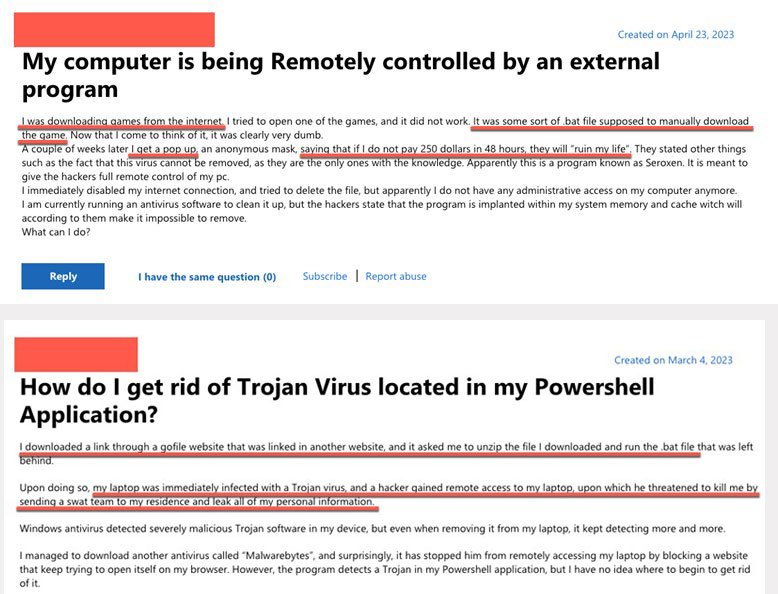
Examining SeroXen infections with insights from the Microsoft Support community
During our investigation of the prevalence and impact of SeroXen infections, we also examined posts within the Microsoft Support community. We observed striking similarities between the infection chain reported in this community and the discussions in Reddit. Moreover, a deeper understanding of the actions perpetrated revealed two distinct and concerning patterns. The first pattern involved direct extortion tactics, while the second involved the issuance of threats to victims' lives through swatting.
Conclusion
Considering the capabilities and potential damage resulting from this tool, the costs for entry are low to null (given the cracked versions available online). This means that both cybercriminals and script kiddies experimenting with malware deployments can avail of SeroXen. Depending on the goals of cybercriminals — whether they care for arrests and notoriety or simply want to spread the tool — the sophistication of the infection routines does not appear to match with the chosen methods for distribution. The almost-amateur approach of using social media for aggressive promotion, considering how it can be easily traced, makes these developers seem like novices by advanced threat actors’ standards. That being said, the real-life consequences of abusing highly evasive malware as a tool to threaten other users via swatting and other threats to personal safety remain highly concerning especially as these developers might interact with online communities populated by minors.
The addition of SeroXen and BatCloak to the malware arsenal of malicious actors highlights the evolution of FUD obfuscators with a low barrier to entry. This can be considered an upcoming trend for a range of cybercriminals who can use a wide range of distribution mechanisms like Discord and social media platforms and their features (such as YouTube and short-from videos in TikTok) to push their preferred types of destructive software for abuse. Additionally, this trend also highlights the potential of highly evasive malware to proliferate in communities that host a significant number of minors who might be ill-equipped to confront destructive pieces of malware. Considering the low-to-nil detections in public repositories once a piece of malware is armed with these tools, this evolution presents new challenges to security teams and organizations alike, especially since FUD obfuscation can be used to deliver any kind of imaginable threat, including those that are not yet known.
Parents and guardians are encouraged to proactively familiarize themselves with the contemporary digital dynamics their children use regularly. This includes gaining an understanding of the various online communities that their children participate in, as well as communicating essential safe online practices and skills to their children. Adults are also encouraged to familiarize themselves with the colloquialisms minors use online and the platforms they frequent. By becoming familiar with these areas and simultaneously equipping children with such knowledge, guardians can play a pivotal role in ensuring everyone’s online safety and well-being.
Trend Vision One™️ enables security teams to continuously identify the attack surface, including known, unknown, managed, and unmanaged cyber assets. It automatically prioritizes risks, including vulnerabilities, for remediation, taking into account critical factors such as the likelihood and impact of potential attacks. Vision One offers comprehensive prevention, detection, and response capabilities backed by AI, advanced threat research, and intelligence. This leads to faster mean time to detect, respond, and remediate, improving the overall security posture and effectiveness.
When uncertain of intrusions, behaviors, and routines, assume compromise or breach immediately to isolate affected artifacts or tool chains. With a broader perspective and rapid response, an organization can address these and keep the rest of its systems protected. Organizations should consider a cutting-edge multilayered defensive strategy and comprehensive security solutions such as Trend Micro™ XDR that can detect, scan, and block malicious content across the modern threat landscape.
Our commitment to online safety
Trend Micro is committed to digital safety through our Trend Micro Initiative for Education , our outreach program that aims to improve internet safety awareness, digital literacy, and malware defense capabilities for a safer digital world. Our initiatives and participation for security and safety include but are not limited to:
- Internet Safety for Kids and Families (ISKF)
- Internet Safety for Home and Small Businesses (IHSB)
- Cybersecurity Education for Universities (CEU)
If you receive a swatting threat or information that an individual is planning to engage in swatting activities, please report it to local law enforcement and/or the Federal Bureau of Investigation (FBI) at 1-800-CALL-FBI immediately.

