Złośliwe oprogramowanie
Yara Used to RickRoll Security Researchers
Yara is a tool that allows the creation of a set of rules for malware tracking and is an invaluable resource that helps automate many processes. But despite Yara’s reliability, it shouldn’t be the only tool used to monitor new versions of malware.
For most security researchers, Yara, a tool that allows them to create their own set of rules for malware tracking, is an invaluable resource that helps automate many processes. However, despite Yara’s reliability, it shouldn’t be the only tool used to monitor new versions of malware. This article will show why.
There are many resources for Yara rules, ranging from the Yara Rules Project repository to blogs and articles that release Yara rules as part of a malware’s Indicators of Compromise (IOCs). In addition, security researches can create their own set of rules to identify specific threats they are looking for. In some cases, they are able to match public rules.
When a Yara rule is triggered, an alert is created, which prompts the researcher to perform more actions. These actions include processes that are a standard part of launching Virtual Machines (VMs), as well as Debuggers and Disassemblers to get to the root of what the sample is attempting to do. This is a common practice for many in the security field.
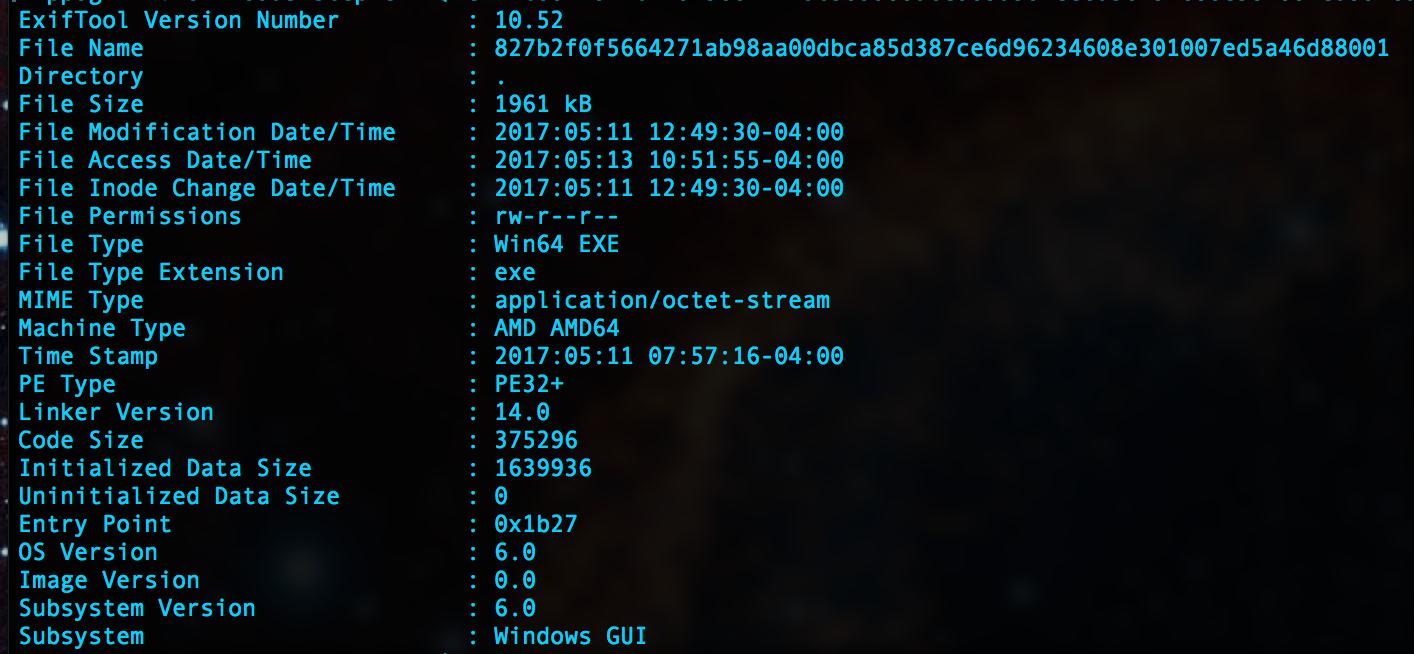
In the process of monitoring for threats, a specific malware sample (Detected by Trend Micro as JOKE_CYBERAVI) triggered multiple rules. This file was first observed at 2017-05-11 14:33:49 UTC. When looking at the timestamp of the PE Header of the exe, the file was created at 12:57:16 UTC. This means that the file was observed roughly 90 minutes after it was created. All in all, we were able to find 26 detections of this file.
Figure 1: File Properties of JOKE_CYBERAVI
Initially, this file looked quite interesting, as there appeared to be anti-debugging methods built into the sample. This technique is used to prevent malware analysts from reverse-engineering malware.
Figure 2: Portion of the malware code
When looking at the PE resources, we noticed something strange about this file. There were three resources RT_MANIFEST, CYB and LOL. Yes, that's right; LOL was within the PE resources.
Figure 3: PE Resources within the malware sample
The 101 section is the file that is dropped and executed. Looking at the pseudocode of the file itself, you can see that this is an .AVI file that is being played.
Figure 4: Portion of the malware code
While executing the file on a windows system, it was hard to tell what this file was since there appeared to be a likely codec problem or some other issues with the player the code was launching.
Figure 5: The .AVI file dropped by the sample
Because the launched player couldn’t play the AVI file, we just extracted the file and played it. To our surprise, it was the music video for Rick Astley’s “Never Gonna Give You Up”, which is often used to “troll” people who got tricked into watching a video. It’s a common internet prank called “RickRolling”.
Figure 6: “Rickrolling” security researchers
We were unsure if this was just a way of telling security researchers to stay away. We tried to find where the CYB within the PE resources was utilized. This was never called at any point, which led us to give the file a closer look. It quickly became apparent that the file contained most of the strings of the Yara rules from the repository mentioned earlier, along with some other popular ones. This appears to be created to catch a bunch of rules people are monitoring, which includes things such as Indetectables RAT and Havex.
Our theory is that this could be some kind of test created to test Yara rules within an organization—or it could be just someone playing a practical joke. Either way, we enjoyed the throwback to the time when Rickrolling was popular.
While it was a pretty interesting exercise—and we do appreciate occasional self-deprecating humor at the expense of the industry—this is a good reminder to not blindly trust these hits. It would be a good idea to refrain from processing and adding detections without more advanced checking such as the Predictive Machine Learning, which is included in security solutions such as Trend Micro XGen™ Security.
The following hashtag was used in this article:
- SHA256: 827b2f0f5664271ab98aa00dbca85d387ce6d96234608e301007ed5a46d88001
Appendix A shows the output from Yara running the rules provided within the Yara-Rules projet github repo. At least 260 hits on various rulesets were flagged.
Appendix A:
| Rule |
| _root_040_zip_Folder_deploy |
| Ajan_asp |
| Ajax_PHP_Command_Shell_php |
| ak74shell_php_php |
| Antichat_Shell_v1_3_php |
| Antichat_Socks5_Server_php_php |
| Asmodeus_v0_1_pl |
| aspydrv_asp |
| Ayyildiz_Tim___AYT__Shell_v_2_1_Biz_html |
| aZRaiLPhp_v1_0_php |
| backdoor1_php |
| backdoorfr_php |
| bdcli100 |
| bin_Client |
| BIN_Client |
| BIN_Server |
| binder2_binder2 |
| by063cli |
| by064cli |
| byshell063_ntboot_2 |
| c99madshell_v2_0_php_php |
| Casus15_php_php |
| cgi_python_py |
| chinese_spam_echoer |
| CmdAsp_asp |
| cmdjsp_jsp |
| connectback2_pl |
| connector |
| createP2P |
| csh_php_php |
| cyberlords_sql_php_php |
| DarkSpy105 |
| dbgiis6cli |
| dbgntboot |
| Debug_cress |
| DeltaCharlie |
| DestructiveTargetCleaningTool5 |
| DestructiveTargetCleaningTool6 |
| DestructiveTargetCleaningTool7 |
| Dive_Shell_1_0___Emperor_Hacking_Team_php |
| Dx_php_php |
| EditServer_Webshell |
| EditServer_Webshell_2 |
| EFSO_2_asp |
| elmaliseker |
| elmaliseker_asp |
| FeliksPack3___PHP_Shells_phpft |
| FeliksPack3___PHP_Shells_ssh |
| FeliksPack3___PHP_Shells_usr |
| FSO_s_casus15_2 |
| FSO_s_phpinj |
| FSO_s_reader |
| FSO_s_zehir4 |
| fuckphpshell_php |
| h4ntu_shell__powered_by_tsoi_ |
| Havex_Trojan_PHP_Server |
| HDConfig |
| hidshell_php_php |
| hkdoordll |
| hkshell_hkrmv |
| hkshell_hkshell |
| HYTop_CaseSwitch_2005 |
| HYTop_DevPack_server |
| HYTop_DevPack_upload |
| HYTop2006_rar_Folder_2006 |
| icyfox007v1_10_rar_Folder_asp |
| IndiaAlfa_One |
| IndiaBravo_generic |
| IndiaBravo_PapaAlfa |
| IndiaBravo_RomeoBravo |
| IndiaBravo_RomeoCharlie |
| IndiaCharlie_One |
| IndiaCharlie_Two |
| installer |
| ironshell_php |
| jsp_reverse_jsp |
| jspshall_jsp |
| JspWebshell_1_2_jsp |
| kacak_asp |
| lamashell_php |
| Lightweight_Backdoor1 |
| LightweightBackdoor2 |
| LightweightBackdoor3 |
| LightweightBackdoor4 |
| LightweightBackdoor5 |
| LightweightBackdoor6 |
| LimaCharlie |
| Liz0ziM_Private_Safe_Mode_Command_Execuriton_Bypass_Exploit_php |
| lurm_safemod_on_cgi |
| Malwareusedbycyberthreatactor1 |
| Malwareusedbycyberthreatactor2 |
| Malwareusedbycyberthreatactor3 |
| Mithril_dllTest |
| Mithril_Mithril |
| Mithril_v1_45_dllTest |
| multiple_php_webshells |
| multiple_webshells_0002 |
| multiple_webshells_0003 |
| multiple_webshells_0005 |
| multiple_webshells_0010 |
| multiple_webshells_0015 |
| multiple_webshells_0016 |
| multiple_webshells_0019 |
| multiple_webshells_0022 |
| multiple_webshells_0030 |
| multiple_webshells_0031 |
| mysql_shell_php |
| MySQL_Web_Interface_Version_0_8_php |
| ngh_php_php |
| NT_Addy_asp |
| PapaAlfa |
| PasswordReminder |
| Pastebin_Webshell |
| perlbot_pl |
| PHANTASMA_php |
| PHP_Backdoor_Connect_pl_php |
| php_backdoor_php |
| PHP_Cloaked_Webshell_SuperFetchExec |
| php_include_w_shell_php |
| PHP_shell |
| PHP_Shell_v1_7 |
| pHpINJ_php_php |
| phpjackal_php |
| phpshell17_php |
| phvayvv_php_php |
| ProxyTool1 |
| ProxyTool2 |
| ProxyTool3 |
| r57shell_php_php |
| rdrbs084 |
| rdrbs100 |
| Reader_asp |
| regshell |
| Rem_View_php_php |
| rknt_zip_Folder_RkNT |
| RkNTLoad |
| RomeoCharlie |
| RomeoEcho |
| RomeoJuliettMikeTwo |
| rootshell_php |
| rst_sql_php_php |
| s72_Shell_v1_1_Coding_html |
| Safe_Mode_Bypass_PHP_4_4_2_and_PHP_5_1_2_php |
| Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php |
| screencap |
| sendmail |
| sh_php_php |
| shankar_php_php |
| shell_php_php |
| shellbot_pl |
| shells_PHP_wso |
| shelltools_g0t_root_Fport |
| shelltools_g0t_root_HideRun |
| shelltools_g0t_root_resolve |
| shelltools_g0t_root_xwhois |
| SierraBravo_packed |
| SierraCharlie |
| sig_2008_php_php |
| SimAttacker___Vrsion_1_0_0___priv8_4_My_friend_php |
| simple_backdoor_php |
| Simple_PHP_BackDooR |
| SimShell_1_0___Simorgh_Security_MGZ_php |
| Sincap_php_php |
| small_php_php |
| sql_php_php |
| STNC_php_php |
| Str_Win32_Http_API |
| Str_Win32_Internet_API |
| Str_Win32_Wininet_Library |
| Str_Win32_Winsock2_Library |
| svchostdll |
| TangoAlfa |
| telnet_cgi |
| telnetd_pl |
| thelast_orice2 |
| Tool_asp |
| Unpack_Injectt |
| vanquish |
| vanquish_2 |
| w3d_php_php |
| WebShell__findsock_php_findsock_shell_php_reverse_shell |
| WebShell_AK_74_Security_Team_Web_Shell_Beta_Version |
| webshell_asp_404 |
| webshell_ASP_aspydrv |
| webshell_asp_EFSO_2 |
| webshell_asp_ice |
| WebShell_Ayyildiz_Tim___AYT__Shell_v_2_1_Biz |
| WebShell_b374k_mini_shell_php_php |
| WebShell_b374k_php |
| webshell_B374kPHP_B374k |
| webshell_bypass_iisuser_p |
| webshell_caidao_shell_404 |
| webshell_caidao_shell_guo |
| webshell_caidao_shell_ice_2 |
| WebShell_CasuS_1_5 |
| webshell_cihshell_fix |
| webshell_dev_core |
| webshell_Dx_Dx |
| webshell_Expdoor_com_ASP |
| webshell_GetPostpHp |
| webshell_gfs_sh_r57shell_r57shell127_SnIpEr_SA_xxx |
| webshell_ghost_source_icesword_silic |
| WebShell_go_shell |
| WebShell_h4ntu_shell__powered_by_tsoi_ |
| WebShell_hiddens_shell_v1 |
| webshell_iMHaPFtp_2 |
| webshell_itsec_PHPJackal_itsecteam_shell_jHn |
| webshell_Java_Shell |
| WebShell_lamashell |
| WebShell_Liz0ziM_Private_Safe_Mode_Command_Execuriton_Bypass_Exploit |
| webshell_MySQL_Web_Interface_Version_0_8 |
| webshell_PHP_b37 |
| WebShell_php_backdoor |
| webshell_PHP_c37 |
| webshell_php_fbi |
| WebShell_php_include_w_shell |
| WebShell_php_webshells_matamu |
| WebShell_php_webshells_MyShell |
| WebShell_php_webshells_NGH |
| WebShell_php_webshells_pHpINJ |
| webshell_phpkit_0_1a_odd |
| webshell_phpspy_2005_full_phpspy_2005_lite_phpspy_2006_PHPSPY |
| WebShell_PhpSpy_Ver_2006 |
| WebShell_qsd_php_backdoor |
| WebShell_ru24_post_sh |
| WebShell_safe0ver |
| webshell_sig_404super |
| WebShell_simattacker |
| WebShell_SimAttacker___Vrsion_1_0_0___priv8_4_My_friend |
| webshell_simple_backdoor |
| WebShell_Simple_PHP_backdoor_by_DK |
| webshell_webshell_cnseay_x |
| webshell_webshell_cnseay02_1 |
| webshell_webshells_new_code |
| webshell_webshells_new_con2 |
| webshell_webshells_new_JSP |
| webshell_webshells_new_pHp |
| webshell_webshells_new_PHP1 |
| webshell_webshells_new_php2 |
| webshell_webshells_new_php5 |
| webshell_webshells_new_php6 |
| webshell_webshells_new_pppp |
| webshell_webshells_new_xxxx |
| WebShell_WinX_Shell |
| webshell_wsb_idc |
| WebShell_zehir4_asp_php |
| wh_bindshell_py |
| WhiskeyAlfa |
| WhiskeyDelta |
| Win32FertgerHavex |
| Win32OPCHavex |
| WinX_Shell_html |
| wiper_encoded_strings |
| wiper_unique_strings |
| xssshell_db |
| xssshell_save |
| zacosmall_php |
| ZXshell2_0_rar_Folder_nc |
| ZXshell2_0_rar_Folder_zxrecv |
| ZXshell2_0_rar_Folder_ZXshell |