
Remote and hybrid work environments have become the new norm. The fact that email become increasingly integral to your business operations has led malicious actors to favor email as an attack vector. In 2023, Trend Vision One™ – Email and Collaboration Security discovered more than 45 million high-risk email threats, in addition to those detected by built-in Microsoft 365 and Google Workspace security. As adversaries become stealthier and more organized, it’s more important than ever to take your organizational defenses beyond native security.
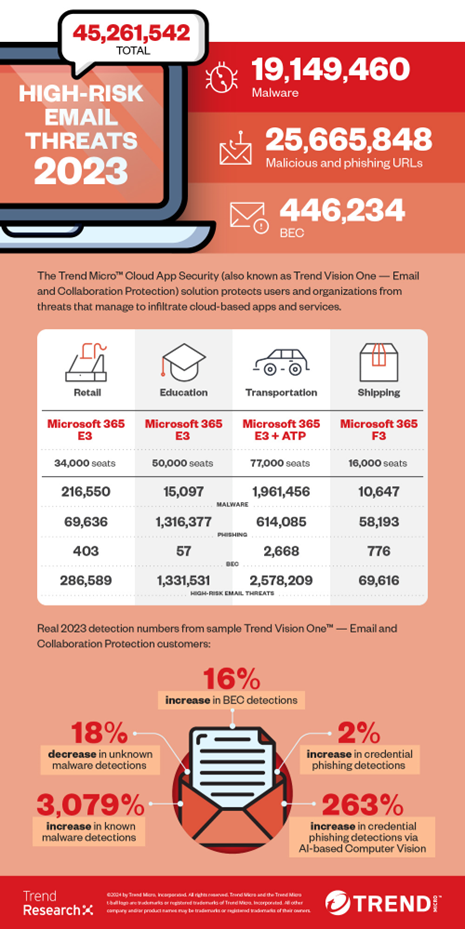
With flexible and remote workforces continue to cause gaps in cloud security to be exploited, cybercriminals are leveraging blind spots in email services’ built-in security. In fact, 46% of all threats blocked by Trend Micro in 2023 were email threats.
Unfortunately, built-in security for popular email services, like Microsoft 365 and Google Workspace, is simply not enough to stop malicious emails from infiltrating enterprises. Tools like Email and Collaboration Security have become a vital part of your defense strategy, as this security platform supplements built-in security and acts as a second layer of defense that can catch highly evasive and complex threats.
Malware attacks surged, known malware detections dropped
Trend detected and blocked 19.1 million malware files in 2023. This represents a 349% rise when compared to 2022. The number of known malware threats also spiked to 16 million, indicating a massive 3,079% surge. Nevertheless, it is important to mention that the number of unknown malware files to 3 million, representing a 18% decline.
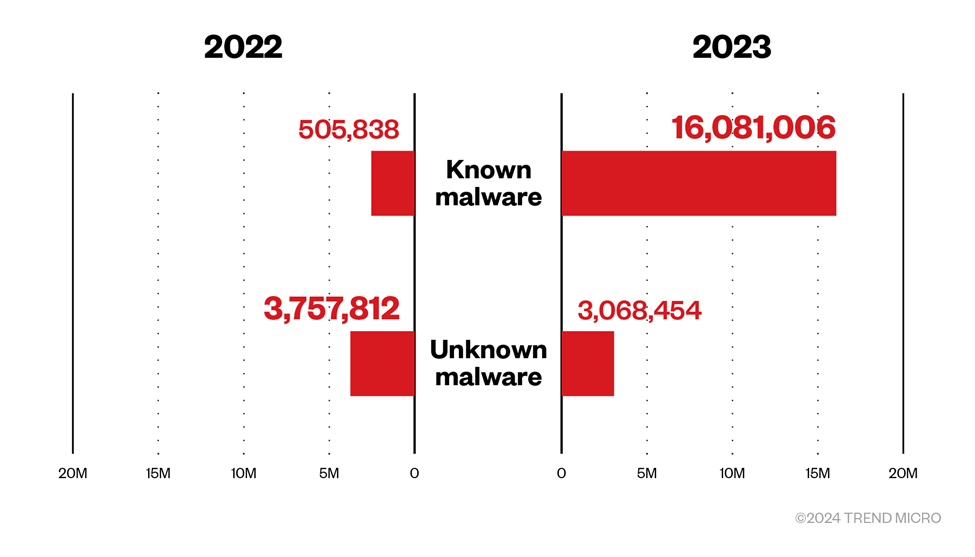
A mid-2022 measure implemented by Microsoft continues contribute to these drop in detections. During this period, Microsoft took action to prevent the execution of macro programs in Microsoft 365 documents, particularly those obtained from the internet or received as email attachments. Over the past eight years, the prevailing method for initial access has been through Microsoft 365 documents containing malicious macros, commonly distributed to targets via email.
Phishing remains a common attack method
According to a report by security company Egress, 94% of organizations have fallen victim to phishing attacks in 2023. This accounts for the 40% increase in phishing incidents from 2022, where we detected and blocked a total of over 14 million attacks.
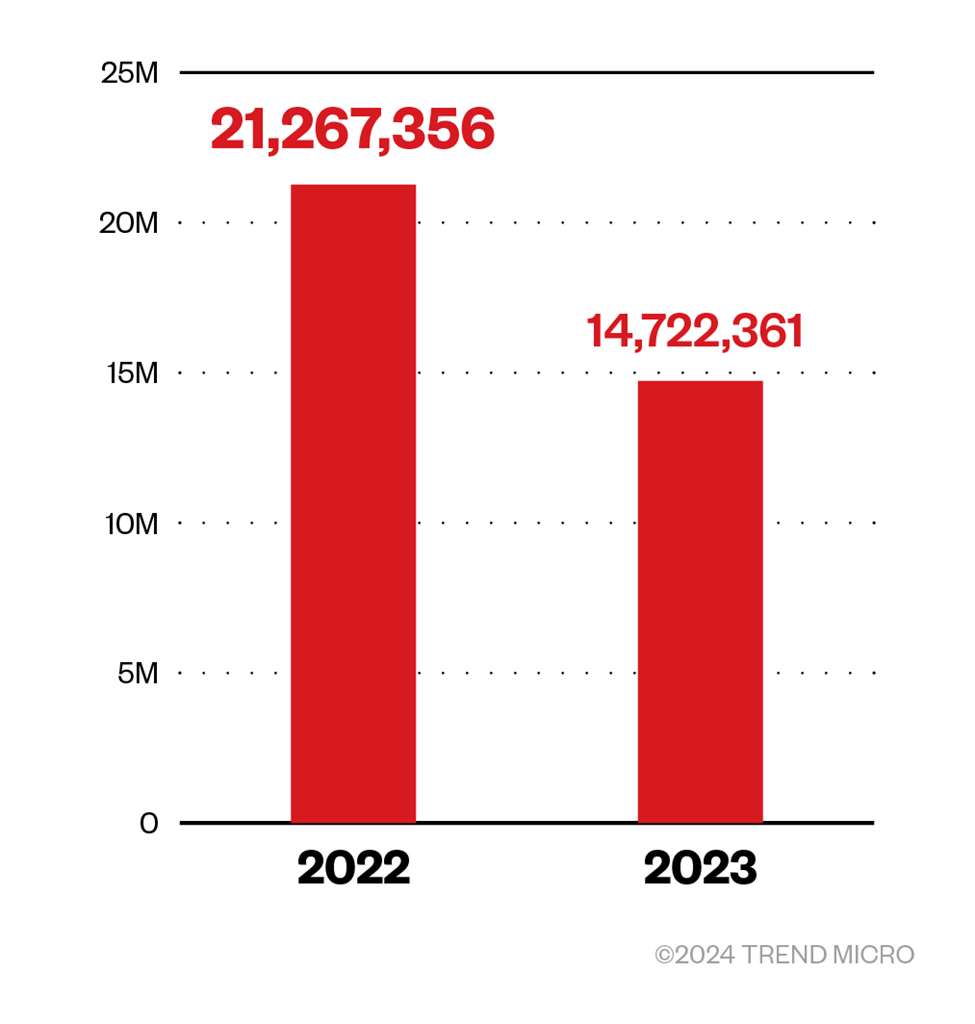
We also observed a 45% decrease in phishing attacks detected via spam count in 2023, with close to 8 million total detections.
It’s important to note that Email and Collaboration Security detection efforts count phishing links within attachments as potential malware, which explains the drop in phishing detections. Cybercriminals are now opting to incorporate phishing links inside email attachments versus directly in the email body for obfuscation purposes.
Phishing attacks aimed at stealing info and data, also known as credential phishing, saw a 17% growth in 2023, with nearly 7 million detections. Trend saw minimal growth for known credential phishing detections at 5%, while unknown credential phishing detections leaped a significant 29%.
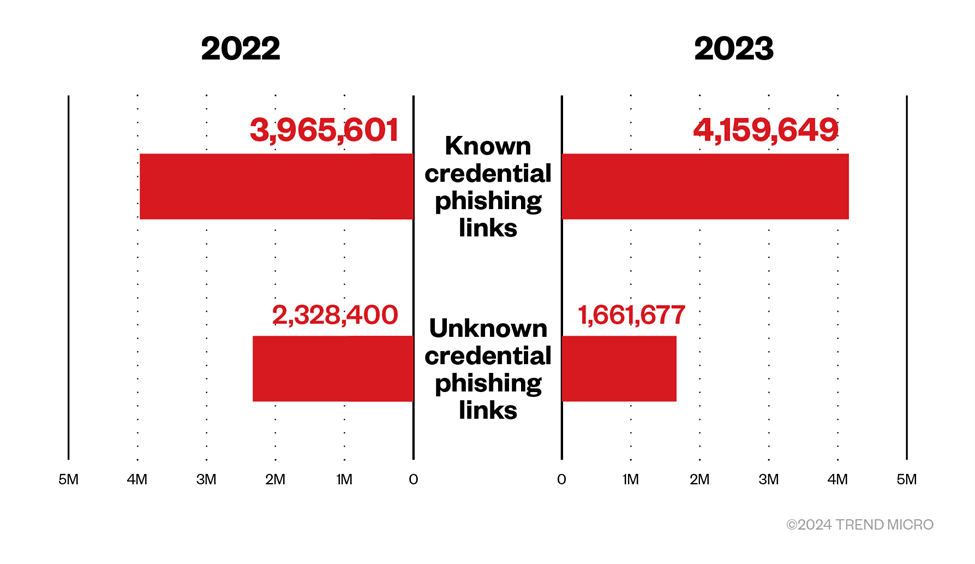
However, 870,555 credential phishing links were discovered via Computer Vision, an image analysis and machine learning (ML) technology that detects credential phishing emails by checking site content like branded elements and login forms. Our findings represent a whopping 263% increase compared to 2022.
BEC continues to be a lucrative attack option
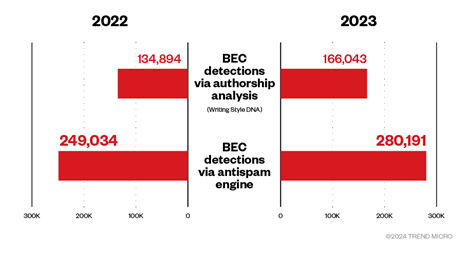
Trend™ Research disclosed that business email compromise (BEC) detections rose to 446,234 in 2023, a growth of 16%. The number of BEC attacks that were detected via Trend Micro™ Writing Style DNA reached 166,034, while 280,191 were detected through the anti-spam engine, representing a 13% increase.
Cybercriminals continued to evolve their tactics to take advantage of new work setups. Trend Research determined that BEC actors mostly impersonated executives or high-ranking management personnel by spoofing general employees’ names. With arrival of sophisticated chat AI tools are expected to make cybercriminals more adept at these type of spoofs.
Next steps
Visibility across the enterprise is paramount in the new normal of remote and hybrid work environments. You need to continually discover, assess, and mitigate risk across your digital attack surface to keep your users secure and the business out of the headlines.
To gain comprehensive visibility, cybersecurity leaders should leverage a SaaS-based platform that supplements the built-in security features in email platforms like Microsoft 365 and Google Workspace.
SaaS-based solutions like Cloud App Security are easy to set up, use sophisticated techniques like ML, and are a part of our Trend Vision One™. This single modern cloud-native security operations platform delivers key capabilities like power purpose-built XDR, attack surface management, and zero-trust capabilities so you can move faster than your adversaries and protect business operations.
Learn more about the facts and figures of email threats for 2022 as well as mitigation strategies in our exclusive email threat landscape report: Cybercriminal Tactics, Techniques That Organizations Need to Know.

