Pathway to Zero Trust
The Zero Trust security model is now well known, but for organizations planning to adopt this approach there are several important questions to consider. How does Zero Trust relate to XDR? How can Zero Trust be applied to your existing infrastructure? Will it create more work for already overburdened security teams? And what are the tangible benefits for your organization?
Read our report to learn more: What is Zero Trust? (Really)
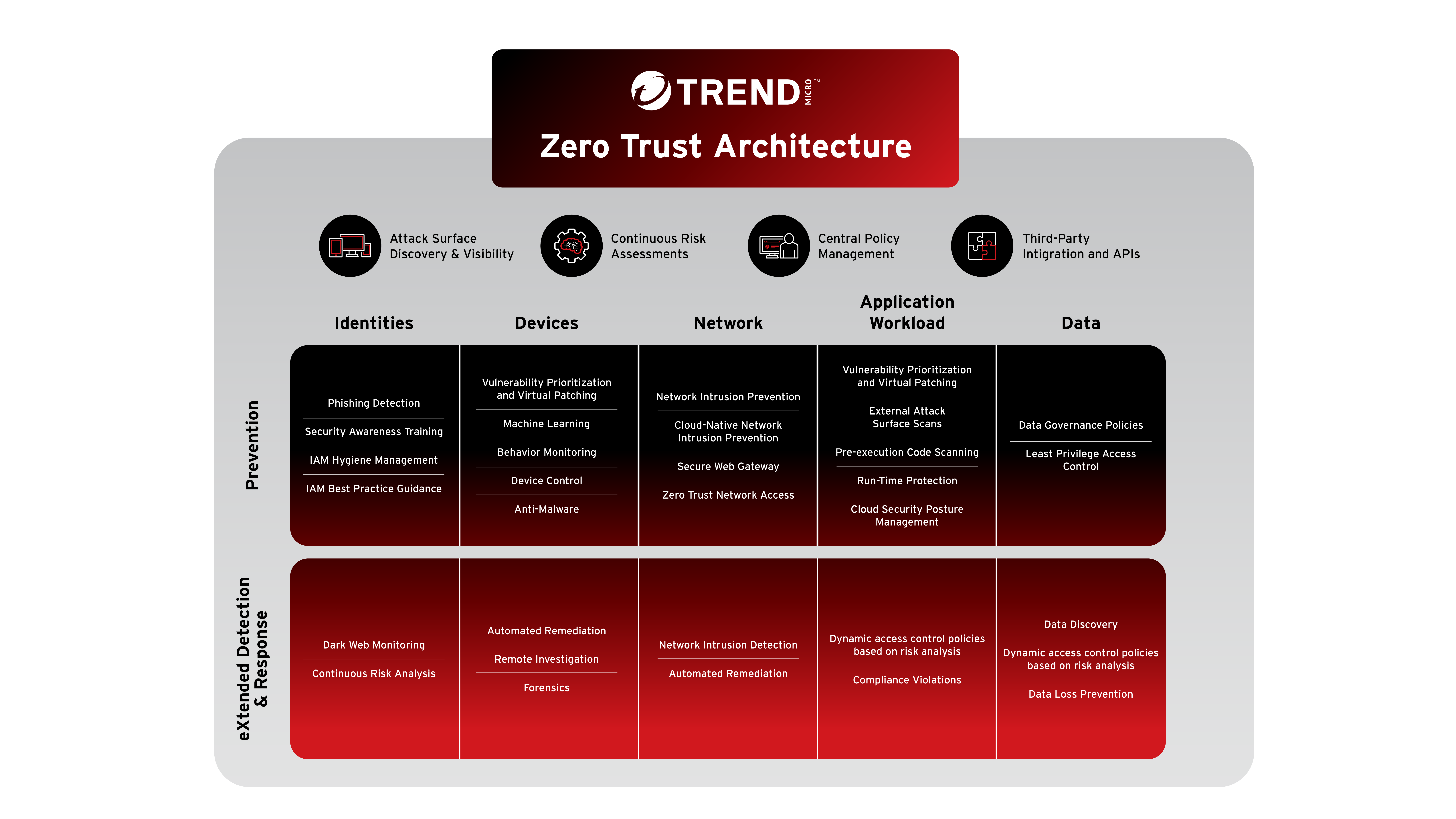
It’s important to remember that Zero Trust is a philosophical approach. There is no such thing as a single product that can be plugged in and save the day. By utilizing security tools that support the pillars of Zero Trust (posture, continuous assessment, and assumed compromise), you can improve your overall security posture. The graphic below outlines tools that can help achieve the main elements of the Zero Trust approach:
XDR and Zero Trust
XDR alone is an effective security capability. However, when used in tandem with the Zero Trust approach, organizations can further enhance their security. XDR has two significant assets that can support a Zero Trust strategy: strong endpoint controls (user, cloud workload, device, etc.) and organization-wide data collection and correlation from across the IT infrastructure. Here’s how it works:
Strong endpoint controls deliver a solid foundation for verifying and establishing trust by providing security teams with comprehensive visibility into potential threats and endpoint/device activities. Without visibility, you can’t verify and establish trust in good faith.
Additionally, since XDR is constantly collecting and correlating data, it establishes the continuous assessment pillar of the Zero Trust strategy. This means that even after you’ve approved initial access for an endpoint, that asset will continually be reviewed and reassessed to ensure it remains uncompromised. In the event the endpoint starts acting suspicious, such as multiple logins from various locations in impossible time frames, XDR will send a notification to security teams, allowing them to withdraw access and terminate a potential attack vector.
Zero Trust and XDR also help alleviate work for security teams. With a Zero Trust strategy that leverages XDR, many security weaknesses and gaps can be detected by XDR and subsequently blocked by enforcement points, eliminating a significant number of vulnerabilities security teams would otherwise have to manually resolve. By closing security gaps, security teams have more time to focus on investigating advanced attacks or on portions of the organization that are furthest from achieving Zero Trust. As always, the fewer number of attacks, the easier it is for enterprises to achieve their business goals, something the board can understand.
Where to start?
While the Zero Trust concept has been around since the early 2010s, organizations have only recently begun to implement it. Therefore, it can be tough to know where to start in your journey with XDR and Zero Trust. It doesn’t help that many security vendors are making confusing claims that their products are “Zero Trust certified” when no such certifications exist.
The National Institute of Standards and Technology (NIST) released NIST SP-800-207, which is a high-level framework that describes the importance of Zero Trust and provides use cases and technology recommendations. This valuable document outlines the architecture-level goals of Zero Trust, but despite what “zero trust washing” vendors say, there is no such thing as “certified NIST SP 800-207 compliant.” Zero Trust is not a product but a set of goals and principles to be achieved.
Leading analyst firms such as Gartner, Forrester, IDC, and ESG have refined their Zero Trust definitions and frameworks to simplify the process for organizations. While analyst firms may have their own way of describing a combination of CASB, Secure Web Gateway, and ZTNA, a more advanced VPN, using Zero Trust principles, they all agree that this can be used in a SD-WAN environment.
Ultimately, each organization needs to consider the nuances of their environment and the security tools available but leveraging the NIST special publication and analyst knowledge is a reliable place to start.
For more insights on leveraging XDR capabilities to establish the Zero Trust pillars, read our report: What is Zero Trust? (Really)