
Hackers know these attacks—do you? Learn how to stop the most common cyber threats before they strike.
Table of Contents
What is a cyberattack?
Cyberattacks come in many forms and have become a common threat as we become more reliant on digital devices and infrastructure which affects both individuals and organizations alike. A cyberattack is an intentional and malicious attempt by an individual or group to breach the information systems of organizations or individuals to steal, disrupt, or alter data. With the rapid adoption of new technologies cyberattacks have been on the rise. Understanding the different types of cyberattacks and their potential consequences is crucial for protecting personal and corporate information.
15 Most Common Types of Cyberattacks
Cyber attacks come in many forms, each using different techniques and targeting various vulnerabilities. Below are some of the most common types:
Malware Attacks
Malware, or malicious software, refers to a wide spectrum of harmful programs intended to disrupt, damage, or gain unauthorized access to computer systems. This includes viruses, worms, Trojans, ransomware, spyware, and adware. Malware can infect devices through a variety of routes, including email attachments, compromised websites, and software downloads. Once installed, it performs malicious actions such as data theft, system hijacking, and device incapacitation. It may operate stealthily to evade detection, exploiting vulnerabilities in software or utilizing social engineering tactics to trick users into inadvertently installing it, posing significant risks to cybersecurity and data privacy. Malware removal typically involves using specialized antivirus software to scan, detect, and quarantine or delete malicious files or programs, restoring the infected device to a secure state.
Phishing and Spear Phishing
Phishing is a type of cyber-attack involving sending generic emails by cybercriminals pretending to be legitimate. These emails contain fraudulent links to steal user's private information. Phishing attacks are most effective when users are unaware this is happening.
Phishing is primarily used in reference to generic email attacks. This is when an attacker sends out emails to as many addresses as possible, using common services like PayPal or Bank of America.
Phishing has evolved throughout the years to include attacks that address different types of data. In addition to money, attacks can also target sensitive data or photos.
Spear phishing stands out as one of the most dangerous and targeted forms of cyber-attacks. Unlike regular phishing attacks, which cast a wide net in hopes of catching unsuspecting victims, spear phishing is a highly personalized and targeted form of a phishing attack that targets a user rather than a network.

Denial of Service (DoS) and Distributed Denial of Service (DDoS)
A DDoS attack is designed to interrupt or shut down a network, service, or website. A DDoS attack happens when attackers utilize a large network of remote PCs called botnets to overwhelm another system’s connection or processor, causing it to deny service to the legitimate traffic it’s receiving. The goal and end result of a successful DDoS attack is to make the website of the target server unavailable to legitimate traffic requests.
DDoS attacks have a variety of purposes, from pranksters and personal vendettas against companies and organizations to criminals who use DDoS attacks as a form of blackmail for financial gain and protests to attract social attention (e.g., hacktivists). For these purposes, for example, government agencies and companies have been frequently targeted by DDoS attacks in recent years, making it a type of cyber attack to be wary of. There are also criminals in the underground market who sell tools for DDoS attacks and services to carry out DDoS attacks. As such, the barriers to carrying out DDoS attacks have been lowered, and the threat of DDoS attacks is expected to continue to grow.
Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack is a type of attack that involves a malicious element “listening in” on communications between parties, and is a significant threat to organizations. Such attacks compromise the data being sent and received, as interceptors not only have access to information, they can also input their own data. Given the importance of the information that goes back and forth within an organization, MiTM attacks represent a very real and potent threat that IT professionals need to be able to address.
SQL Injection
SQL injection is an attack that illegally manipulates a database by injecting unintended Structured Query Language (SQL) statements into an application that has a relational database (RDBMS). There are several types of SQL injection depending on the method and purpose, and from the perspective of cyber attackers, they range from stealing information, falsifying data, and investigating vulnerabilities. Although it is an old attack, it is still causing a lot of damage today, so it is one of the attacks that corporate organizations should be particularly wary of.
Although SQL injection is an old attack, there are still many confirmed cases of it causing great damage in recent years. Therefore, it is still an attack that organizations should be wary of. If a technique such as UNION injection is used and the attack is successful, it may lead to a large-scale information leak. However, by taking appropriate measures, it is possible to prevent such damage before it occurs. As a security measure for corporate organizations, in addition to the measures from the perspective of defense in depth mentioned above, we recommend that safety assessments are regularly carried out, such as external penetration tests and vulnerability diagnosis.
Zero-Day Exploits
A zero-day vulnerability is a flaw, weakness, or bug in software, firmware, or hardware that may have already been publicly disclosed but remain unpatched. Researchers may have already disclosed the vulnerability, and the vendor or developer may already be aware of the security issue, but an official patch or update that addresses it hasn’t been released.
The flaw is referred to as a “zero-day” vulnerability because the vendor or developer — and accordingly, the users and organizations whose systems are affected by the vulnerability — have just learned of the vulnerability. Once the vulnerability becomes public and the vendor or developer already deployed a patch for it, it becomes a known, or “n-day” vulnerability.
When hackers or threat actors successfully develop and deploy proofs of concept (PoCs) or an actual malware that exploits the vulnerability while the vendor is still working on rolling out a patch (or sometimes, unaware of the vulnerability’s existence), it becomes a zero-day exploit or attack. While developers and vendors, as well as researchers and security experts, continuously invest time and effort to find and fix security flaws, the same can be said for threat actors, too. The result is an arms race between threat actors finding and trying to exploit a vulnerability and the vendors working to release a patch to fix it.
Ransomware Attacks
Ransomware is malware that encrypts important files on local and network storage and demands a ransom to decrypt the files. Hackers develop this malware to make money through digital extortion. Ransomware is encrypted, so the key cannot be forced and the only way to recover the information is from a backup.
The way ransomware works makes it especially damaging. Other types of malware destroy or steal data but leave other recovery options open. With ransomware, if there are no backups, you must pay the ransom to recover the data. Sometimes businesses pay the ransom, and the attacker does not send the decryption key.
Once the ransomware starts to work, it scans local and network storage, looking for files to encrypt. It targets files it assumes are important to your business or to individuals. This includes backup files that could help recover the information.
Different types of ransomware target different sets of files, but there are also common targets. Most ransomware targets Microsoft Office files because they often store critical business information. Targeting important files increases the chance that you will pay the ransom.
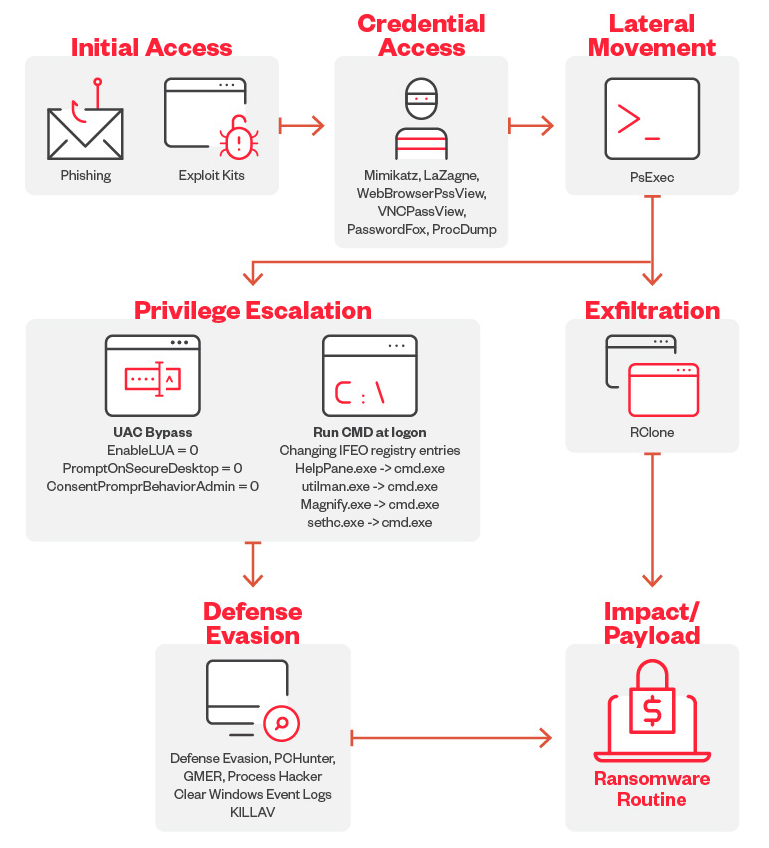
Supply Chain Attack
Supply Chain Attack is a type of cyberattack that target less-secure elements in the supply chain of an organization rather than attacking the organization directly. The goal is to infiltrate an organization’s network or systems by compromising a third-party vendor, supplier, or partner that has access to its data, software, or network infrastructure.
Instead of attacking the target organization directly, these attacks compromise a trusted third party, such as a software provider, hardware supplier, or service contractor. This third party then becomes a conduit for delivering the malicious payload to the final target.
The impact of a supply chain attack can be significant, affecting not just the primary target but potentially thousands of other organizations that rely on the compromised third party.
Cross-Site Scripting (XSS)
Cross-site Scripting (XSS) is a security vulnerability usually found in websites and/or web applications that accept user input. Examples of these include search engines, login forms, message boards and comment boxes.
Cybercriminals exploit this vulnerability by inputting strings of executable malicious code into these functions. This injects the malicious code into the targeted website’s content, making it a part of the website and thus allowing it to affect victims who may visit or view that website. The code may also present itself as transient content that isn’t actually part of the website but only appears to be to the visitor. This makes it look like the website is indeed compromised by cybercriminals.
Cybercriminals may also use this vulnerability to take control or directly compromise a website, as well as exploit other existing vulnerabilities on the website's server or software.
Social Engineering Attacks
Social engineering is a type of attack that uses human interaction and manipulation to achieve the attacker’s aims. It often involves persuading victims to compromise their security or break security best practices for the attacker’s financial or informational gain. Threat actors use social engineering to disguise themselves and their motives, often by acting as trusted individuals.
Ultimately, the key aim is to influence, to hack the mind — rather than a system. Many such exploits rely on people’s good nature or fear of negative situations. Social engineering is popular among attackers because it is easier to exploit people rather than network and software vulnerabilities.
Whaling Attacks
Whaling is a specialized type of phishing attack that targets C-level or High-Profile individuals within organizations, such as executives, managers, and other senior leaders. The term "whaling" reflects the attack’s focus on the "big fish", who hold significant authority and access to sensitive information. Unlike traditional phishing attacks that can target the average person and rely on volume, whaling is a highly targeted attack, which uses detailed information about the victim to craft convincing and personalized emails.
High-profile individuals are attractive targets for cybercriminals because they often have access to valuable information, financial resources, and decision-making power. By compromising an executive's email account, attackers can authorize fraudulent transactions, access confidential data, and manipulate organizational processes.

Phishing vs. whaling
Trojan Horses
In cybersecurity, the term "Trojan" or "Trojan Horse" refers to a type of malware that tricks users by disguising itself as legitimate software. This digital threat is named after the ancient Greek legend of the Trojan Horse, where Greek soldiers hid inside a wooden horse to infiltrate and capture the city of Troy. Similarly, a Trojan in cybersecurity hides its malicious intent under the guise of a harmless application, tricking users into executing harmful code on their devices. Trojans have evolved into one of the most common and versatile forms of malware, posing major risks to both people and organizations. Unlike viruses or worms, Trojans cannot replicate themselves or self-execute and instead rely on social engineering techniques to be installed.
If a Trojan is successfully installed on a user’s device, it can perform several malicious actions depending on their type and purpose. Such as providing a back door entry for hackers, accessing data, passwords and other sensitive information.
Prompt Injection Attack
Prompt injection is a type of cyberattack that targets services that use AI. It involves inserting malicious input (prompts) to extract unintended or sensitive information from the system, beyond what the developer intended.
Prompt injection is especially challenging to detect and block in natural language-based AI services, such as conversational AI, because the inputs are written in human language, which lacks a fixed structure or rules, unlike traditional injection attacks that target structured query formats.
Keylogger Attack
A keylogger (short for keystroke logger) is a type of surveillance technology that tracks and records each keystroke made on a computer or mobile device. While keyloggers are often associated with malicious cyber activity—such as stealing login credentials or sensitive data—they can also be used in legitimate scenarios, such as employee supervision or parental control software.
Keyloggers operate by intercepting and recording user input, often leveraging stealth tactics to remain hidden from users and security software.
IoT-Based Attacks
The rise of Internet of Things (IoT) devices has introduced new security challenges, as many IoT gadgets lack robust protection. Attackers will aim to exploit these vulnerabilities, often using compromised devices in large-scale botnets, such as the infamous Mirai botnet, to launch DDoS attacks or infiltrate broader networks. Securing IoT devices has become essential to minimizing risks associated with these rapidly expanding digital connections.
How to Protect Against Cyberattacks
Update your Software
Keeping all your software and systems updated adds additional resilience to your security measures. The updates usually contain patches to any known vulnerabilities that have been found.
Use Strong Passwords and Two-Factor Authentication (2FA)
You should use strong passwords that contain a minimum of 12 characters, with a combination of upper and lowercase letters, numbers and special characters. Try not to re-use the same password for different accounts as it increases the risk of a hacker gaining access to your information. You should also enable 2FA to add extra layers of security for your online accounts.
Employee Training and Awareness
Since social engineering remains a common entry point for attackers, regular training equips employees with the knowledge to recognize phishing emails, avoid social engineering traps, and follow best practices for protecting sensitive data. Educating staff on these tactics reduces the likelihood of successful attacks.
Install a Firewall
Firewalls are useful in preventing a variety of attacks to block unauthorized access such as ddos or backdoor attacks. Firewalls control the network traffic moving through your system and will block non-permitted traffic coming in or going out.
Strengthening Security with XDR
Extended Detection and Response (XDR) enhances cybersecurity by integrating data from endpoints, email, networks, and cloud environments. It detects and responds to threats in real-time, preventing attacks like ransomware from spreading across enterprise networks. With AI-driven analytics and automation, XDR improves threat detection, reduces response time, and strengthens overall security.
How Cyber Attacks Are Evolving in 2025
Cyber attacks are growing in scale, complexity, and impact. From ransomware and phishing to supply chain breaches and AI-powered exploits, attackers are constantly adapting to bypass defenses and exploit vulnerabilities. Understanding how these threats are evolving is essential for building resilient digital operations.
2025 Cyber Risk Report
Trend Micro’s latest report dives deep into the shifting cyber threat landscape, offering insights into emerging attack vectors, evolving risk patterns, and strategic recommendations for organizations. It’s a valuable resource for anyone looking to stay ahead of the next wave of cyber attacks.
Stop cyberattacks faster and strengthen your defenses with Trend Micro
Stopping adversaries faster and taking control of your risks and cyberattacks starts with a single platform. Manage security comprehensively with full prevention, detection, and response capabilities powered by AI, leading threat research, and advanced intelligence.
Trend Vision One supports diverse hybrid IT environments, automates and orchestrates workflows, and provides expert cybersecurity services so you can simplify and unify your security operations.
Jon Clay has worked in the cybersecurity space for over 29 years. Jon uses his industry experience to educate and share insights on all Trend Micro externally published threat research and intelligence.
Frequently Asked Questions (FAQs)
What is a cyberattack?
A cyberattack is a malicious attempt to breach systems, steal data, or disrupt operations using unauthorized access, malware, or digital exploitation techniques.
What are the most common attacks?
Common cyberattacks include phishing, ransomware, malware infections, DDoS attacks, password breaches, and social engineering targeting users, networks, and online services.
How to protect against cyberattacks?
Protect against cyberattacks by updating software, using strong authentication, enabling firewalls, monitoring networks, training users, and implementing reliable endpoint security tools.

