
A cyberattack is a deliberate and malicious attempt by an individual or group to penetrate the information systems of organisations or individuals in order to steal data, disrupt business operations or supply chains or modify data and use it for blackmail, for example.
Table of Contents
Cyber attack meaning
While ongoing digitalization strategies in organizations increase the dependency on digital technologies and processes and constantly expand the digital attack surface in the modern day, cyber attacks have become one of the most significant threats facing businesses and individuals. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in systems, and adapting to the latest technology advances. A further push towards this trend is based on wide-adoption of AI technologies. As Cyber attacks become more sophisticated, understanding the tactics, techniques and processes behind these attacks is essential for maintaining a secure digital landscape and to protect sensitive information.
Why Cyber Attacks Happen
Cyber attacks occur for various reasons, ranging from financial gain to political agendas. Some of the most common motivations include:
Financial Gain
Many cybercriminals seek monetary rewards by stealing sensitive information such as credit card details, login credentials, or bank account information. Ransomware attacks, in which users are locked out of their systems with the promise of (eventually) regaining access after paying a ransom, are particularly financially motivated
Espionage
Corporate espionage attacks aim to steal intellectual property, trade secrets, research, and other sensitive data to gain a competitive edge. Such attacks are often covert and may go unnoticed for long periods.
Revenge or Malicious Intent
Disgruntled former employees or individuals with a vendetta may carry out cyber attacks to cause reputational damage or disrupt operations.
Desire for Notoriety
Some attackers, often known as “black hat” hackers, conduct cyber attacks to showcase their skills, earn credibility within the hacking community, or simply create chaos.
Types of Cyber Attacks
Cyber attacks come in many forms, each using different techniques and targeting various vulnerabilities. Below are some of the most common types of cyber attacks:
Malware Attacks
Malware which is short for malicious software and is designed to infiltrate, damage, or gain unauthorized access to an organization’s IT environment. In cybersecurity, malware is a persistent threat which can steal sensitive information and can cause widespread damage to users and organizations. Understanding malware's various forms and effects is crucial to develop a comprehensive cybersecurity strategy.
Malware typically uses existing vulnerabilities within an organization’s IT environment in order to achieve the desired goal.
Phishing and Spear Phishing
Phishing is a type of cyber-attack involving sending generic emails by cybercriminals pretending to be legitimate. These emails contain fraudulent links to steal user's private information. Phishing attacks are most effective when users are unaware this is happening by imitating typical communication that is received in the daily business.
Spear phishing stands out as one of the most dangerous and targeted forms of cyber-attacks. Unlike regular phishing attacks, which cast a wide net in hopes of catching unsuspecting victims, spear phishing is a highly personalized and targeted form of a phishing attack that targets a user rather than a network.
Denial of Service (DoS) and Distributed Denial of Service (DDoS)
A DDoS attack is designed to interrupt or shut down a network, service, or website. A DDoS attack happens when attackers utilize a large network of remote PCs called botnets to overwhelm another system’s connection or processor, causing it to deny service to the legitimate traffic it’s receiving. The goal and end result of a successful DDoS attack is to make the website of the target server unavailable to legitimate traffic requests and therefore interrupt important business processes.
Man-in-the-Middle (MitM) Attacks
MitM attacks intercept and alter communications between two parties without their knowledge. Attackers may modify data or capture sensitive information, such as login credentials.
SQL Injection
SQL injection is an attack that illegally manipulates a database by injecting unintended Structured Query Language (SQL) statements into an application that has a relational database (RDBMS). There are several types of SQL injection depending on the method and purpose, and from the perspective of cyber attackers, they range from stealing information, falsifying data, and investigating vulnerabilities.
Zero-Day Exploits
Zero-day exploits target unknown vulnerabilities in software before developers have a chance to issue a patch. These attacks are particularly dangerous because there is no immediate defense.
Ransomware Attacks
Ransomware is malware that encrypts important files on local and network storage and demands a ransom to decrypt the files. Hackers develop this malware to make money through digital extortion. Ransomware is encrypted, so the key cannot be forced and the only way to recover the information is from a backup. The way ransomware works makes it especially damaging. Other types of malware destroy or steal data but leave other recovery options open. With ransomware, if there are no backups, you must pay the ransom to recover the data. Sometimes businesses pay the ransom, and the attacker does not send the decryption key.
Supply Chain Attack
Supply Chain Attack is a type of cyberattack that target less-secure elements in the supply chain of an organization rather than attacking the organization directly. The goal is to infiltrate an organization’s network or systems by compromising a third-party vendor, supplier, or partner that has access to its data, software, or network infrastructure.
Cyber Attacks Phases - Example
We’ll explore the different phases of a cyber attack by examining how 8Base, a well-known ransomware group, executes their attacks. From initial infiltration to data encryption and extortion, we’ll break down each step in their ransomware tactics.
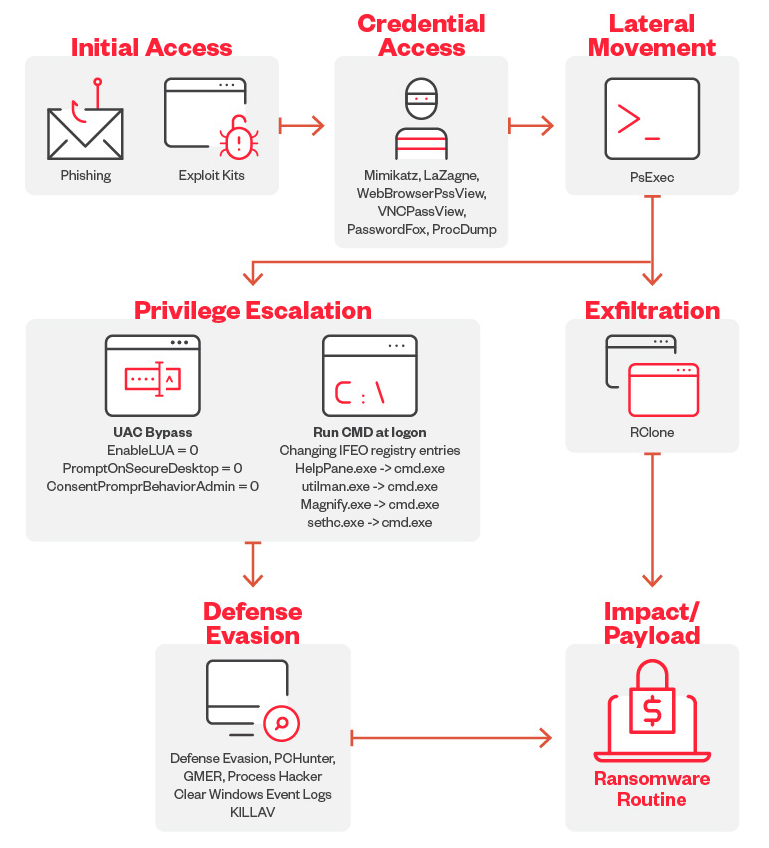
Initial Access
The 8Base ransomware primarily uses phishing scams for initial access. Users are tricked into entering their credentials into a form that looks legitimate.
Credential Access
8Base operators use MIMIKATZ, LaZagne, WebBrowserPassView, VNCPassView, PasswordFox, and ProcDump to retrieve passwords and credentials stored on their victim’s machines.
Defense Evasion
For its defense evasion, the 8Base ransomware drops and executes a batch file named defoff.bat (detected as KILLAV) to disable components of Windows Defender. The 8Base ransomware also uses garbage codes, deletes shadow copies, bypasses Cuckoo Sandbox, clears Windows event logs, disables firewalls, and uses SmokeLoader to decrypt and deliver the payload.
Lateral Movement
For lateral movement, it has been observed that the 8Base ransomware operators use PsExec to deploy the batch file as well as the ransomware binary. PsExec is an example of the misuse of a legitimate tool that is normally available on Windows machines and cannot be considered malware.
Privilege Escalation
8Base ransomware operators modified certain registry entries to bypass User Access Control (UAC). They also modified IFEO registry keys to attach cmd.exe to accessibility programs that are accessible from the lock screen.
Exfiltration
The threat actors behind 8Base ransomware have been detected using the third-party tool and web-service RClone to exfiltrate stolen information.
Impact
The 8Base ransomware uses AES-256 algorithm to encrypt target files and then encrypts each encryption key using RSA-1024 with a hardcoded public key. The encrypted key is then appended to the end of each encrypted file. It has an embedded configuration (decrypted during runtime) which contains the file extensions, file names, and folders to avoid.
Methods and Tactics Used in Cyber Attacks
Cybercriminals use a range of techniques to launch attacks and avoid detection:
Social Engineering
With Social Engineering, attackers manipulate individuals into divulging sensitive information, often by impersonating trusted sources or using fear tactics.
Exploiting Software Vulnerabilities
Cybercriminals exploit unpatched software vulnerabilities to gain unauthorized access to systems. While zero-day vulnerabilities are already a high risk, many IT operations teams are already overwhelmed by the number of known vulnerabilities and the question of which ones should be prioritised in the Patch Management process.
Phishing Attacks
Many phishing attacks succeed due to user mistakes, such as weak passwords, accidental data sharing, or falling for phishing attempts.
These tactics help attackers gain a foothold within systems and access sensitive data, often without immediate detection because they are considered as legit user behaviour.
Impact of Cyber Attacks on Organizations
Cyber attacks can severely impact businesses, leading to damage in brand reputation, downtime, data loss, and financial loss. Some of the most significant effects include:
Operational Disruptions
Malware or denial-of-service (DoS) attacks can cause server and system crashes, interrupting services and leading to financial setbacks. According to the Cost of a Data Breach Report 2024, the average data breach now costs USD 4.45 million globally, reflecting the high price of these interruptions.
Data Compromise
SQL injection attacks allow hackers to alter, delete, or steal critical data from company databases, which can damage business operations and customer trust.
Financial Fraud
Phishing attacks deceive employees into transferring funds or sharing confidential information, resulting in direct financial losses and exposing organizations to future risks.
Ransom Payments
Ransomware attacks lock down essential systems until a ransom is paid. In 2024, the average ransomware payment was reported at nearly USD 1 million, underscoring the financial strain these attacks place on affected companies.
Each cyber attack can leave lasting impacts that require considerable resources for detection, response, and recovery, adding to the total cost of a breach.
How to Prevent a Cyber Attack
Employee Training and Awareness
Since social engineering remains a common entry point for attackers, regular training equips employees with the knowledge to recognize phishing emails, avoid social engineering traps, and follow best practices for protecting sensitive data. Regularly educating staff on these tactics reduces the likelihood of successful attacks.
Attack Surface Management
Attack surface management (ASM) involves identifying and monitoring all external points where an attacker could gain entry into a system. Regularly assessing and reducing these points, such as exposed network ports, unpatched applications, and misconfigured servers, helps reduce vulnerabilities. An effective ASM strategy helps organizations close potential gaps that attackers could exploit.
Data Security Platforms
Data security platforms provide comprehensive oversight of data access and movement across an organization’s systems. These platforms help prevent unauthorized access by tracking sensitive data, identifying potential breaches, and enforcing data protection policies. By centralizing data security management, businesses can enhance data visibility and improve overall resilience to cyber threats due to centralized data analysis rather than having important information spread in multiple tools and data silos.
Identity and Access Management (IAM)
IAM solutions are essential for controlling user access to systems and data. With IAM, organizations can implement role-based access, ensuring that employees only have access to the information needed for their job functions. IAM tools also support identity verification and monitoring, preventing unauthorized access and minimizing the potential damage from compromised accounts.
Regular Security Audits and Penetration Testing
Routine security audits and penetration tests help organizations identify and mitigate vulnerabilities proactively. By actively testing defenses and validating security measures, businesses can strengthen their resilience against emerging threats and avoid common attack vectors.
A modern approach towards penetration testing is the so-called Red Teaming approach.
Strong Password Policies and Multi-Factor Authentication
Implementing strong password policies and enforcing multi-factor authentication (MFA) can significantly reduce the risk of unauthorized access.
How to Detect a Cyber Attack
Security Information and Event Management (SIEM)
SIEM systems collect and analyze data from various sources across an organization’s IT environment to detect suspicious activities. By centralizing logs and correlating security events, SIEM provides real-time insights into potential threats and allows teams to identify unusual patterns that may indicate an attack.
An innovative approach called Agentic SIEM effectively reduces efforts that are needed to collect, normalize and correlate data from numerous datacenters.
Endpoint Detection and Response (EDR)
EDR tools monitor endpoints, such as computers and mobile devices, for abnormal behavior. They continuously scan for signs of intrusion, such as unauthorized access or malware, and can respond to threats by isolating infected endpoints. EDR solutions help detect attacks early, limiting the scope and impact of a breach.
Anomaly Detection
Anomaly detection involves identifying behaviors that deviate from an established baseline. By tracking metrics like network traffic or user behavior, anomaly detection tools can flag irregular activities, such as unauthorized access attempts or sudden data transfers, that might signal a cyber attack in progress.
Honeypots
Honeypots are decoy systems or files that mimic valuable assets to attract attackers. When attackers interact with a honeypot, they reveal their presence, tactics, and intentions without affecting actual data or systems. Honeypots help detect attacks early while providing valuable intelligence on attacker methods.
Threat Intelligence
Threat intelligence involves collecting information about known threats and vulnerabilities from external sources to anticipate potential attacks. This intelligence is integrated into security systems to proactively detect indicators of compromise. Threat intelligence provides a strategic layer of detection, alerting teams to active threats targeting similar organizations or industries.
Threat Hunting
Threat hunting is a proactive approach to identifying hidden threats within an organization’s network. Skilled security analysts search for evidence of malicious activity that may have evaded automated defenses. By actively hunting for indicators of compromise, threat hunting teams can detect sophisticated attacks before they escalate.
How to Respond to a Cyber Attack
Incident Response Plan
A well-defined incident response plan is the cornerstone of effective attack mitigation. This plan outlines the essential steps to be taken immediately after detecting a cyber attack, including designating key roles, notifying stakeholders, and isolating affected systems. The goal is to minimize damage by containing the threat quickly, ensuring a coordinated response across all teams, and setting clear actions to protect critical assets.
Security Orchestration, Automation, and Response (SOAR)
SOAR platforms streamline response processes by integrating security tools and automating repetitive tasks. In the event of an attack, SOAR can automatically initiate actions such as isolating infected systems, blocking malicious IP addresses, or deploying patches. By automating workflows, SOAR reduces response time, enabling security teams to address threats swiftly and focus on complex, high-priority tasks.
Extended Detection and Response (XDR)
XDR provides a unified approach to detecting and responding to threats across multiple layers of an organization’s environment, including endpoints, networks, and cloud infrastructure. In a cyber attack, XDR aggregates and analyzes data from all sources to offer a comprehensive view of the threat’s origin, scope, and impact. This visibility allows security teams to respond with targeted actions, containing the attack more effectively and preventing its spread across systems.
Documenting and Analyzing the Incident
After the incident is resolved, it is important to create detailed documentation that helps the organization to understand how the attack unfolded, what went well, and identify any security gaps. This post-incident analysis can also help to improve your Incident Response Plan, as the lessons learned can improve your response strategies, procedures other details that may have been lacking previously.
Hacktivism
Hacktivism refers to cybercriminal attacks that often involve breaking into systems for politically or socially motivated purposes, usually to make a statement in support of a cause or against governments or organizations.
Derived from combining the words "hack" and "activism", the term “hacktivism” was first coined in 1996 by Omega, a member of the hacker collective Cult of the Dead Cow.
What motivates Hacktivists
In the past, hacktivist actions were likened to symbolic, digital graffiti. Nowadays, hacktivist groups resemble urban gangs. Previously composed of low-skilled individuals, these groups have evolved into medium- to high-skill teams, often smaller in size but far more capable. The escalation in skill has directly increased the risks posed to organizations.
Hacktivist groups are defined by distinct political beliefs reflected in both the nature of their attacks and their targets. Unlike cybercriminals, hacktivists typically do not seek financial gain, though we have observed overlaps with cybercrime. For the most part, these groups focus on advancing their political agendas, which vary in transparency. Broadly, their motivations can be classified into four distinct groups: ideological, political, nationalistic, and opportunistic. While some groups strictly align with one category, others pursue multiple agendas, often with a primary focus supplemented by secondary causes.
Cybercrime
Cybercrime refers to organized criminal activities that are carried out using computers or networks, often for financial gain. These attacks typically target individuals, organizations, or financial institutions to steal sensitive information, extort money, or disrupt services.
Criminal activities are sometimes very specialized while different actors work together or offer services specialized for a specific purpose such as offering Ransomware-as-a-Service or Initial Access services on darkweb marketplaces.
The term encompasses a wide range of offenses as described before.
Nation-State Attacks
Nation-state cyber attacks are cyber operations conducted or sponsored by a country to achieve strategic objectives, such as espionage, disruption, or sabotage. These attacks are typically aimed at other governments, critical infrastructure, or major private enterprises.
Nation-state actors possess significant resources, access to cutting-edge technology, and skilled personnel, allowing them to conduct long-term, highly sophisticated campaigns often referred to as Advanced Persistent Threats (APTs).
What motivates Nation-State Actors
Nation-state attacks are driven by national interests. These can include gathering intelligence, weakening rival nations, influencing foreign elections, or preparing for geopolitical conflicts.
Such operations are usually covert and are intended to go undetected for long periods. Unlike hacktivists or cybercriminals, nation-state actors follow structured, government-led strategies and often operate with impunity due to diplomatic protections or jurisdictional complexities.
Their objectives can be classified into several categories: cyber espionage, cyber warfare, economic disruption, and psychological operations. The consequences of such attacks can be far-reaching, influencing international relations and global security.
How Cyber Attacks Are Evolving in 2025
Cyber attacks are growing in scale, complexity, and impact. From ransomware and phishing to supply chain breaches and AI-powered exploits, attackers are constantly adapting to bypass defenses and exploit vulnerabilities. Understanding how these threats are evolving is essential for building resilient digital operations.
2025 Cyber Risk Report
Trend Micro’s latest report dives deep into the shifting cyber threat landscape, offering insights into emerging attack vectors, evolving risk patterns, and strategic recommendations for organizations. It’s a valuable resource for anyone looking to stay ahead of the next wave of cyber attacks.
Defending Against Cyber Attacks with Trend Micro
Understanding what a cyber attack is, whether it's ransomware, phishing, or supply chain exploitation, is only the first step. The next is building a proactive defense strategy that can adapt to evolving threats and protect your organization across endpoints, networks, cloud environments, and email systems.
Trend Micro’s enterprise cybersecurity platform, Trend Vision One, offers comprehensive protection powered by AI, extended detection and response (XDR), and cyber risk exposure management. It enables security teams to detect, investigate, and respond to threats faster and more effectively, turning visibility into action and risk into resilience.
Thomas Margner is Senior Manager Solution Sales at Trend Micro and works from Germany. He holds a Diploma in Applied Computer Science from DH Baden-Württemberg and a Bachelor of Science from The Open University as well as various industry certifications.
Frequently Asked Questions (FAQs)
What is a cyber attack?
A cyber attack is a malicious attempt to access, damage, or disrupt computer systems, networks, or digital data.
How to prevent a cyber attack?
Prevent cyber attacks by using firewalls, strong passwords, antivirus software, regular updates, and employee cybersecurity awareness training.
What is a cyber attack example?
A phishing email tricking users into revealing passwords is a common and dangerous example of a cyber attack.
What can cause a cyber attack?
Cyber attacks can be caused by hackers, malware, phishing, insider threats, or poor cybersecurity practices and outdated software systems.
What is the most used form of cyber attack?
Phishing is the most common cyber attack, tricking users into revealing sensitive information through deceptive emails or fake websites.

