Ensure that Amazon Organizations service is currently in use to gain central control over the use of AWS services across multiple AWS accounts (using Service Control Policies) in order to help you comply with the security and compliance policies within your company. AWS Organizations is an account management tool that enables you to centralize multiple AWS accounts into an organization that you create and administer. Amazon Organizations is available to all customers at no additional cost and has two main feature sets:
Consolidated Billing features – which provides basic management tools that you can use to centrally manage all the accounts (master and member accounts) within your organization. With this feature you can get a combined view of AWS charges incurred by all your accounts and also take advantage of pricing benefits from aggregated usage. This represents the default feature set applied to an organization that is migrated from a Consolidated Billing family of AWS accounts.
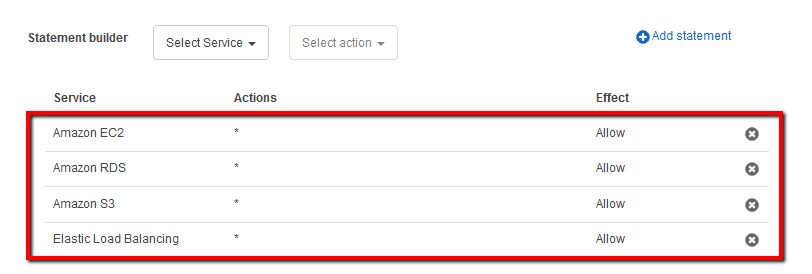
All features – provides Consolidated Billing capabilities plus advanced policy-based management through Service Control Policies (SCPs), which give you fine-grained control over which services and actions that member AWS accounts can access and use. Service Control Policies are similar to IAM policies except they don't grant any access permissions, instead they act as filters that allow only the specified services to be used in affected accounts. This represents the complete feature set that is available to an organization.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
You can use AWS Organizations service for: controlling access to AWS services (i.e. managing individual account permissions at scale) – using Service Control Policies (SCPs) that control AWS service use across multiple AWS accounts by working around the permissions that these policies can grant to entities in an account such as IAM users and roles, central management of policies across multiple AWS accounts – Organizations provides the necessary tools to centrally manage policies across multiple accounts without requiring custom scripts or manual implementations, automating AWS account creation and management – using the service API to create new accounts programmatically and to add them to groups, simplify billing – by enabling you to set up a single payment method for all the AWS accounts within your organization through the Consolidated Billing feature.
Audit
To check if your AWS account belongs to an Organization, perform the following:
Remediation / Resolution
To make use of Amazon Organizations service and benefit from centralized control over the use of AWS services across multiple accounts you must create first an organization (with All features set enabled) using your current AWS account as the master account then invite other accounts to join your organization. Once the member accounts respond to your invitation, create Organizational Units (OUs) to place the new member accounts. The final step is to apply restrictions to what actions can be delegated to users and roles within the member accounts by using Service Control Policies (SCPs). An SCP will allow you to explicitly specify the access that is allowed (safelisting) or to explicitly specify the access that is not allowed (blocklisting). To create and configure your organization, you need to perform the following actions:
References
- AWS Documentation
- AWS Organizations
- What is AWS Organizations?
- AWS Organizations Terminology and Concepts
- Tutorial: Creating and Configuring an Organization
- AWS Command Line Interface (CLI) Documentation
- organizations
- describe-organization
- create-organization
- invite-account-to-organization
- list-roots
- create-organizational-unit
- move-account
- enable-policy-type
- enable-policy-type
- create-policy
- attach-policy
- AWS Blog(s)
- AWS Organizations Now Generally Available