Ensure that All Features is enabled within your Amazon Organizations to achieve full control over the use of AWS services and actions across multiple AWS accounts using Service Control Policies (SCPs). An SCP is a type of organization control policy that can be used to restrict what users and even administrators can do in affected AWS accounts. For example, the master account from an organization can apply SCPs that can prevent member accounts from leaving the organization. A Service Control Policy is similar to an IAM access policy except the SCP does not grant any access permissions but instead it acts like a filter that allows only the specified services and actions to be used within the organization. SCPs make use of whitelisting and blacklisting methods to filter the permissions that are available to member accounts. When whitelisting is used, you can explicitly specify the access that is allowed and all other access is implicitly blocked. When blacklisting is used, you can explicitly specify the access that is not allowed and all other access is granted.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
To demonstrate how AWS Organizations Permission Model and SCPs work, please consider the following example:
To make sure that only the given set of services is accessible within your AWS account you should create an "Allow" policy using whitelisting to grant access only to the necessary services (in this case AWS EC2, RDS, S3, Glacier and DynamoDB). To keep this example simple, you can attach a "Corporate" Service Control Policy (SCP) to your entire organization and assign it to the root. As the root is the top element of an organization’s tree, SCPs applied to the tree apply to every member/linked account within the organization.
Now create a "Production" Organizational Unit (OU) to place the member/linked accounts. All these accounts should have two SCPs, named "CloudConformity Company" and "Corporate", applied to them. In this example, SCPs apply the more restrictive intersection of the two policies to the member accounts within "Production" OU. If the "CloudConformity Company" SCP allows EC2, RDS, S3, Glacier, DynamoDB, Lambda, Redshift and Kinesis, the policy application for accounts in the "Production" OU would be the intersection, as shown in this chart.
The accounts in the "Production" OU have both the "CloudConformity Company" SCP and the "Corporate" SCP applied to them. The intersection of the two policies applies, so these member accounts have access to EC2, RDS, S3, Glacier and DynamoDB. Because Amazon Lambda, Redshift and Kinesis are not within the "Corporate" SCP, the linked accounts in the "Production" OU are not allowed to access them.
In conclusion, you have an extra layer of protection, limiting the accounts within your organization to only those AWS services that are compliant with "Corporate" regulations.
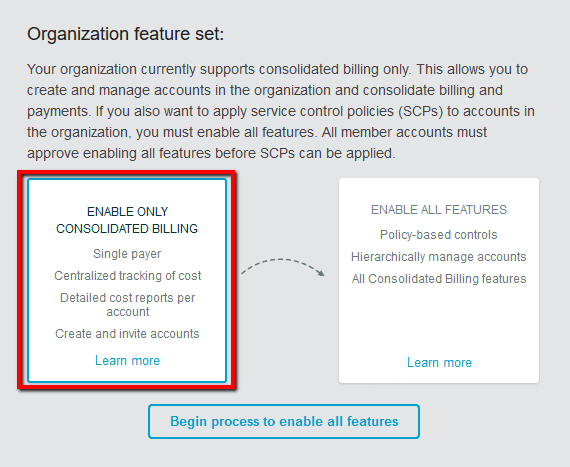
Note 1: If you previously signed up for Consolidated Billing feature using the AWS Billing and Cost Management service, your Consolidated Billing account family has been migrated automatically to a new organization within AWS Organizations. As this new organization, created automatically by AWS, has just the Consolidated Billing features set enabled, this conformity rule demonstrates how to enable All Features set so that your organization can provide Consolidated Billing capabilities plus advanced policy-based management through Service Control Policies (SCPs).Note 2: The migration from Consolidated Billing features set to All Features set within an organization is one-way and switching back to Consolidated Billing features only is not currently supported.With All Features enabled, you can apply Service Control Policies (SCPs) to limit what the member accounts in your organization can do, as well as create, manage and pay for the organization’s accounts through Consolidated Billing.
Audit
To check if your AWS organizations have All Features set enabled, perform the following:
Remediation / Resolution
To enable All Features set for your AWS organization and attach Service Control Policies (SCPs) to your member accounts and Organizational Units (OUs), perform the following:
References
- AWS Documentation
- AWS Organizations
- What is AWS Organizations?
- AWS Organizations Terminology and Concepts
- Enabling All Features in Your Organization
- Managing Organization Policies
- Consolidated Billing for Organizations
- AWS Command Line Interface (CLI) Documentation
- organizations
- describe-organization
- enable-all-features
- accept-handshake