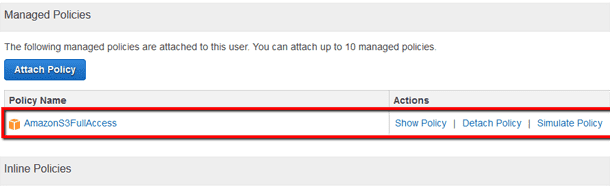
Ensure that the existing IAM policies are attached only to groups in order to efficiently assign permissions to all the users within your AWS account.
This rule can help you with the following compliance standards:
- CISAWSF
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
Defining permissions at the IAM group level instead of IAM user level will allow you manage more efficiently the user-based access to your AWS resources. With this new model you can create groups, attach the necessary policies for each group, then assign IAM users to these groups as needed. The model has few valuable advantages such as removing duplication of information and effort as you don't need to define policies for each individual user anymore or switching existing users between groups as they receive different roles in your organization.
Audit
To determine if your IAM users have any policies attached, perform the following:
Remediation / Resolution
To change the access permissions model and attach policies to IAM groups instead of users, perform the following:
References
- AWS Documentation
- AWS Identity and Access Management FAQs
- IAM Best Practices
- Managing IAM Users
- Creating Your First IAM User and Administrators Group
- Attaching a Policy to an IAM Group
- Adding and Removing Users in an IAM Groups
- AWS Command Line Interface (CLI) Documentation
- iam
- list-users
- list-attached-user-policies
- detach-user-policy
- create-group
- attach-group-policy
- add-user-to-group