- Knowledge Base
- Amazon Web Services
- AWS Identity and Access Management (IAM)
- AWS Multi-Account Centralized Management
Set up and orchestrate your AWS resources in a multi-account environment built with separate AWS accounts - one for each application stage (Development, Test, Staging and Production) or as per your requirements, in order to enforce a strong and secure separation between different types of AWS resources available in the environment. The access (cross-account access) to the entire multi-account environment is built around IAM roles, it follows AWS security best practices and is managed by a dedicated (central) AWS account, known as the Identity Account.
This rule can help you with the following compliance standards:
- PCI
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
The AWS multi-account setup recommended in this guide comes with multiple benefits such as clean separation between different types of AWS resources, centralized management and auditing for user accounts and their access permission, easier and securer authentication process that lets you switch accounts without being required to sign out and sign in for each account and fewer access credentials to create and manage.
Audit
Create AWS accounts for all your application stages (e.g. Development, Test, Staging and Production) and enable cross-account access using IAM roles. With roles you can prevent accidental changes to your AWS environment, especially when combined with auditing tools that can help ensure that your roles are only used when needed. Cloud Conformity recommends creating multiple AWS accounts to provide the highest level of resource and security isolation for your application(s).
Implementation: I. Set up the AWS multi-account environment.
01 Go to Amazon Web Services website at http://aws.amazon.com/ and click Create an AWS account.
02 On the Sign In page, enter your email or mobile number, select I am a new user and click Sign in using our secure server.
03 On the Login Credentials page, fill out the registration form and click Create account.
04 Follow the AWS instructions to complete the registration process. Once your new account is ready, sign in to the AWS Management Console.
05 Navigate to IAM dashboard at http://aws.amazon.com/iam/.
06 In the left navigation panel, choose Roles.
07 On the Roles page, click Create New Role to set up a new IAM role that the users logged in to Identity Account can assume.
08 On the Create Role page, perform the following:
- In the Role Name field enter a name for the role. Choose a name that will reflect the purpose of the role (e.g. Dev-Admin-Role) and click Next Step.
- Choose the Role for Cross-Account Access section, then select the Provide access between AWS accounts you own option. Click Next step to continue the setup process.
- In the Account ID field, enter the Identity Account 12-digit ID. The Identity Account is the central AWS account to which you want to grant access to the entire environment resources. Select Require MFA checkbox to enable Multi-Factor Authentication (MFA) protection, so that only IAM users who sign in with an MFA device can assume this role. Click Next Step to continue.
- On the Attach Policy page, select the permissions policy to attach to the role. This policy defines what actions the IAM users can take and what resources they can access. Since this role is created to provide full access to all resources (except IAM) within the 'Development' AWS account, select the PowerUserAccess policy. When using the PowerUserAccess policy the IAM users cannot change the permissions for the role they're assuming and they are not able to create new users or roles. You can also create your own custom policies using the AWS Policy Generator: https://awspolicygen.s3.amazonaws.com/policygen.html, in order to restrict further the user access to your account resources and services. Click Next Step to continue.
- On the Review page, copy the Role ARN (Amazon Resource Name) and the Give this link to users who can switch roles in the console sign in (switch role) link. Once these access details are copied click Create Role to generate the new IAM role.
09 Repeat step no. 8 to create new IAM roles for your 'Development' AWS account based on your access requirements.
10 Repeat steps no. 1 – 9 to create the rest of recommended AWS accounts (e.g. Test, Staging and Production) and their necessary IAM roles.
Set up the AWS multi-account environment.
Create a dedicated AWS account to grant efficiently access to your AWS resources spread over multiple accounts. This central account, known as the Identity Account, will be responsible for creating, managing and tracking the IAM groups and users that will be used to provide access to the other accounts within your AWS environment.
II. Set up the AWS multi-account environment.
01 Go to Amazon Web Services website at http://aws.amazon.com/ and click Create an AWS account.
02 On the Sign In page, enter your email or mobile number, select I am a new user and click Sign in using our secure server.
03 On the Login Credentials page, fill out the registration form and click Create account.
04 Follow the AWS instructions to complete the registration process. Once your new account is ready, sign in to the AWS Management Console.
05 Navigate to IAM dashboard at http://aws.amazon.com/iam/.
06 First, create the IAM policy that will define the access permissions to your AWS environment resources (i.e. the resources available in all AWS accounts created in Section I). To create the policy, perform the following:
- In the left navigation panel, choose Policies and click Create Policy button from the dashboard top menu.
- On the Create Policy page, select Create Your Own Policy to create your custom managed policy.
- On the Review Policy page, enter the following information:
- In the Policy Name box, enter a name for your custom policy. Choose a unique name that will reflect the policy usage (e.g. MyCrossAccountPolicy).
- In the Description textbox, enter a short description for the policy (optional).
- In the Policy Document textbox, paste the following data and replace the highlighted details with your own details. The highlighted bits represent the AWS accounts IDs and the IAM roles created for each of these accounts in the Section I of this guide:
{ "Version": "2012-10-17", "Statement": { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": [ "arn:aws:iam::565392545550:role/Dev-Admin-Role", "arn:aws:iam::565392545552:role/Test-Admin-Role", "arn:aws:iam::565392545553:role/Staging-Admin-Role", "arn:aws:iam::576539245557:role/Prod-Admin-Role" ] } } - Click Validate Policy button to validate the policy document then click Create Policy to save it.
07 Now create the IAM group that will manage the access permissions to your AWS environment resources, permissions that will be automatically inherited by any IAM users attached to this group. This can be very useful when an employee/team member leaves your organization because you just need to detach his user from the group in order to revoke his access. To create the IAM group, perform the following actions:
- In the left navigation panel, choose Groups and click the Create New Group button from the IAM dashboard top menu.
- On the Set Group Name page, enter a name for the new group and click the Next Step button.
- On the Attach Policy page, in the Filter box, search for the policy name created at step no. 6. Select the policy name returned and click the Next Step button.
- On the Review page, review the new group configuration then click Create Group.
08 Before any users are created and attached to the Identity Account IAM group, you must define a managed policy to set the users baseline permissions to change their password, attach MFA devices and generate and update their own access keys. (!) IMPORTANT: the policy will not grant user access to the AWS resources (regardless of the account), instead it will provide only basic user-related access, useful to change their own credentials. To create the policy, perform the following:
- In the left navigation panel, choose Policies and click Create Policy button from the dashboard top menu.
- On the Create Policy page, select Create Your Own Policy to create your custom managed policy.
- On the Review Policy page, enter the following information:
- In the Policy Name box, enter a name for your custom policy. Choose a unique name that will reflect the policy usage (e.g. IAMUserCredentialsPolicy).
- In the Description textbox, enter a short description for the policy (optional).
- In the Policy Document textbox, paste the following data and replace the highlighted details with your own details. The highlighted bits represent the Identity Account ID and the IAM group name created at previous step:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Stmt1464432593000", "Effect": "Allow", "Action": [ "iam:ChangePassword", "iam:CreateAccessKey", "iam:DeleteAccessKey", "iam:CreateVirtualMFADevice", "iam:DeleteVirtualMFADevice", "iam:EnableMFADevice", "iam:DeactivateMFADevice" ], "Resource": [ "arn:aws:iam::123456789012:group/Staff" ] } ] } - Click Validate Policy button to validate the policy document then click Create Policy to save it.
09 Now it’s time to create the IAM users that will access your AWS environment resources based on the roles which these will assume. By default, the IAM users created at this step have no permissions to assume roles in order to access other AWS accounts. The ability to switch (role) to other AWS accounts and access their resources is enabled only after these users are attached to the group created at step no. 7. To create the necessary IAM users, perform the following:
- In the left navigation panel, choose Users.
- On the Users page, click Create New Users button set up the new IAM user.
- On the Create User page, under Enter User Names, enter the name for the new user in the first box. You can create multiple IAM users at once if necessary.
- Make sure that the Generate an access key for each user checkbox is selected if you need access keys for your user so that AWS can generate the key pair for you.
- Click Create to create the IAM user.
- Click Download Credentials to save the CSV file that contain your user access key (Access Key ID and Secret Access Key) to a secure location on your machine. Once the file is downloaded, click the Close link to return to the Users page.
- Click on the newly created IAM user name to access its configuration page.
- Select the Permissions tab and click the Attach Policy button to define the user access permissions.
- On the Attach Policy page, in the Filter box, search for the policy name created at step no. 8. Select the policy name returned and click the Attach Policy button.
- Select the Security Credentials tab to set up a password for the newly created IAM user.
- Under Sign-In Credentials section, click the Manage Password button to assign a new password.
- On the Manage Password page, select one of the following options to create the user password:
- Select Assign an auto-generated password if you want AWS IAM to generate automatically a new password for you.
- Select Assign a custom password to provide your own custom password.
- Click Download Credentials to save the file that contains your new IAM user password to a secure location on your machine. Once the file is downloaded, click the Close link to return to the user configuration page.
- In the left navigation panel, choose Dashboard and copy the sign-in link available under IAM users sign-in link section.
- Repeat steps a – n to create new IAM users (as per your requirements).
11 Once you create all the necessary IAM users, attach them to the IAM group by performing the following:
- In the left navigation panel, choose Groups and click on the group name to access its configuration page.
- On the group configuration page, select the Users tab.
- Click Add Users to Group button and select the IAM users that you need to access your AWS environment resources.
- Click Add Users to attach the selected users to the group. Now all the IAM users within the group will inherit its access permissions.
12 To revoke a certain user access to the environment simply detach the user from the group by using the following:
- In the left navigation panel, choose Groups then click on the group name.
- On the group configuration page, select the Users tab.
- Click Remove Users to Group button and select the necessary IAM users that are no longer required to access your AWS environment.
- Click Remove Users to detach the selected users from the IAM group and revoke their access.
Harden IAM user access credentials.
Enforce Multi-Factor Authentication (MFA) and a strong password policy for all the IAM users that access your environment resources through the Identity Account.
Note: As example, this guide will use Google Authenticator as MFA device since is one of the most popular MFA virtual applications used by AWS customers. To explore other MFA devices (virtual and hardware) and their features visit http://aws.amazon.com/iam/details/mfa/.III. Harden IAM user access credentials.
01 Enable Multi-Factor Authentication (MFA):
- Sign in to the Identity Account using the root credentials.
- Navigate to IAM dashboard at https://console.aws.amazon.com/iam/.
- In the left navigation panel, select Users.
- Click on the IAM user name that you want to update, created in Section II (9).
- On the IAM user configuration page, select Security Credentials tab.
- Inside the Sign-In Credentials section, click the Manage MFA Device button next to Multi-Factor Authentication Device to initiate the MFA device setup process.
- In the Manage MFA Device dialog box, select A virtual MFA device and click Next Step.
- Now install the AWS MFA-compatible application. The MFA application used in this example is Google Authenticator. This guide assumes that you have already the application installed on your smartphone at this point, otherwise just follow these simple steps: https://support.google.com/accounts/answer/1066447?hl=en. Once the application is installed, click Next Step.
- Scan the QR code using the Google Authenticator application and enter two consecutive authentication codes in the Authentication Code 1 and Authentication Code 2 boxes, then click Activate Virtual MFA to complete the setup process. If successful, the following message will be displayed: “The MFA device was successfully associated.”. Click Finish to exit the setup wizard. The MFA passcode box will be displayed for the IAM user during the authentication process.
- Repeat steps no. d – i for all the IAM users available in your AWS Identity Account.
02 Enforce a strong IAM password policy:
- Sign in to the Identity Account using the root credentials.
- Navigate to IAM dashboard at https://console.aws.amazon.com/iam/.
- In the left navigation panel, select Account Settings.
- In the Password Policy section, set the following:
- Inside the Password Policy section, in the Minimum password length box, enter a minimum value of 14 to force IAM users to change their passwords length in order to secure the user access to the Identity Account.
- In the Password Policy section, select the Require at least one uppercase letter checkbox to force IAM users to include at least one uppercase letter in their password pattern.
- In the Password Policy section, select the Require at least one lowercase letter checkbox to force IAM users to include at least one lowercase letter when they set the password.
- In the Password Policy section, select the Require at least one number checkbox to force IAM users to include at least one number in their password pattern.
- In the Password Policy section, select the Require at least one non-alphanumeric character checkbox to force users to include at least one non-alphanumeric character in their password pattern.
- In the Password Policy section, select the Enable password expiration checkbox and enter a value equal or less than 90 in the Password expiration period (in days) box to force IAM users to use an expiration date for their passwords.
- In the Password Policy section, select the Prevent password reuse checkbox and enter a value between 1 and 24 in the Number of passwords to remember box to enable reuse prevention for their passwords.
- Click Apply password policy button to apply the IAM password policy defined above.
AWS environment audit
Enable API logging for the entire AWS environment by activating AWS CloudTrail and AWS Config AWS at the global level and aggregate all the audit data recorded by these services into an S3 bucket within the Identity Account.
IV. AWS environment audit
01 Create the S3 bucket that will store the logging data recorded by CloudTrail and Config services across all your AWS accounts:
- Sign in to the Identity Account using the root credentials.
- Navigate to S3 dashboard at https://console.aws.amazon.com/s3/ and click Create Bucket.
- In the Create a Bucket dialog box, enter a unique name for the bucket that will reflect its usage (e.g. aws-multi-account-api-logging) and select the AWS region where the bucket will be created.
- Click Create to set up the bucket. Since the bucket is created using the root account, the only user that can access it for auditing purposes is the Identity Account (root) owner.
- Select the newly created S3 bucket and click the Properties tab from the S3 dashboard top right menu.
- Click on the Permissions tab from the Properties panel to expand the ACL (Access Control List) configuration section for the selected bucket.
- Under the ACL grantee listed click Add bucket policy to attach an access policy which allows AWS Config and CloudTrail to send configuration information and logging data to the bucket.
- Inside the Bucket Policy Editor textbox, paste the ACL policy document listed below and click the Save button to attach it. Once the policy is active, both AWS Config and CloudTrail can send data to the selected bucket. Replace the highlighted details (bucket name and AWS accounts IDs) with your own details before you attach the policy:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AWSLoggingBucketPermissionsCheck", "Effect": "Allow", "Principal": { "Service": [ "config.amazonaws.com", "cloudtrail.amazonaws.com" ] }, "Action": "s3:GetBucketAcl", "Resource": "arn:aws:s3:::aws-multi-account-api-logging" }, { "Sid": "AWSLoggingBucketDelivery", "Effect": "Allow", "Principal": { "Service": [ "config.amazonaws.com", "cloudtrail.amazonaws.com" ] }, "Action": "s3:PutObject", "Resource": [ "arn:aws:s3:::aws-multi-account-api-logging/ config/AWSLogs/565392545550/Config/*", "arn:aws:s3:::aws-multi-account-api-logging/ config/AWSLogs/565392545552/Config/*", "arn:aws:s3:::aws-multi-account-api-logging/ config/AWSLogs/565392545553/Config/*", "arn:aws:s3:::aws-multi-account-api-logging/ config/AWSLogs/576539245557/Config/*", "arn:aws:s3:::aws-multi-account-api-logging/ cloudtrail/AWSLogs/565392545550/*", "arn:aws:s3:::aws-multi-account-api-logging/ cloudtrail/AWSLogs/565392545552/*", "arn:aws:s3:::aws-multi-account-api-logging/ cloudtrail/AWSLogs/565392545553/*", "arn:aws:s3:::aws-multi-account-api-logging/ cloudtrail/AWSLogs/576539245557/*" ], "Condition": { "StringEquals": { "s3:x-amz-acl": "bucket-owner-full-control" } } } ] }
02 Enable AWS Config service to gain complete visibility over your AWS infrastructure configuration changes. The data recorded by the Config service can be extremely useful during security audits or troubleshooting sessions:
- Sign in to the AWS account created in Section I (e.g. 'Development' account) using its root credentials.
- Navigate to AWS Config dashboard at https://console.aws.amazon.com/config/ and click Get started to open the Settings page.
- To track all supported AWS resources, under Resource types to record section, perform the following:
- Check Record all resources supported in this region checkbox to track configuration changes for every supported type of regional AWS resource.
- Check Include global resources to include any types of global AWS resources (e.g. AWS IAM) to the existent list of supported resources.
- Inside the Amazon S3 Bucket section designate the S3 bucket that will receive the service configuration history and configuration snapshot files. This data can be used later with the AWS Config console timeline or a 3rd-party tool. Select Choose a bucket from another account and enter the S3 bucket name created in the Identity Account in Section IV (1) of this guide. Next to Bucket Name box, enter config as unique prefix (must match the prefix used in the S3 policy created in the Section IV (1.h.)).
- Inside the Amazon SNS Topic section, check Enable configuration changes and notifications to be streamed to an Amazon SNS topic so that AWS Config can send configuration changes notifications to an SNS topic. Select Create a new topic to create a new SNS topic. In the Topic Name box, enter a unique name for the new SNS topic.
- Inside the AWS Config Role section, select Create a role to create a new IAM role to grant the Config service permission to send the recorded configuration information to AWS S3 and AWS SNS. In the Role Name box, enter a unique name for the new IAM role that will be created by AWS Config.
- Click the Continue button to continue the setup process.
- On the AWS Config is requesting permissions to read your resources configurations page, click View Details and View Policy Document to review the IAM role required by the service and its policy (created by default), then click Allow.
- On the Resource inventory page, under Recording is on section, you should see the Taking inventory... event status in progress. The Config service setup process is complete once the Taking inventory... status label is no longer visible.
- To stream AWS Config configuration changes notifications to the SNS topic created earlier, navigate to AWS SNS dashboard at https://console.aws.amazon.com/sns/v2/.
- In the left navigation panel, select Topics and open the SNS topic specified during the AWS Config setup by clicking on its ARN name.
- On the Topic Details <topic name> page, under Subscriptions section, click the Create subscription button.
- Select Email as subscription protocol from the Protocol dropdown list and for the Endpoint just enter the email address where you will receive the AWS Config notifications for this account.
- Click Create Subscription.
- Use your email client application and open the message from AWS Notifications, then click on the appropriate link to confirm your subscription to the SNS topic.
- Repeat steps a – n to enable the Config service for the other AWS accounts within your environment (e.g. Test, Staging, Production).
03 Enable AWS CloudTrail service in order to track API calls for all the AWS resources within your environment and use the recorded data for auditing purposes:
- Sign in to the AWS account created in Section I (e.g. 'Development' account) using its root credentials.
- Navigate to AWS Config dashboard at https://console.aws.amazon.com/cloudtrail/ and click the Get Started Now button to open the CloudTrail service subscription page.
- In the Trail Name box, enter a unique name for the new trail, name that will reflect its usage (e.g. aws-multi-account-trail).
- Select Yes next to Apply trail to all regions in order to enable CloudTrail to log the API activity across all AWS regions.
- Select No next to Create a new S3 bucket and enter the S3 bucket name created for the Identity Account (Section IV (1)) in the S3 bucket box.
- Click the Advanced link to expand the trail configuration section.
- In the Log file prefix box enter cloudtrail as unique prefix (must match the prefix used in the S3 policy created in the Section IV (1.h.)).
- Select Yes next to Enable log file validation to enable CloudTrail log file integrity validation.
- Select Yes next to Send SNS notification for every log file delivery so the AWS CloudTrail can send notifications of the log file delivery process to an SNS topic.
- Select Yes next to Create a new SNS topic to create a new SNS topic and enter a name for it in the SNS topic box.
- Click Turn on to activate the Cloudtrail service for the selected account and create the new trail.
- To stream AWS CloudTrail log file delivery notifications to the SNS topic created earlier, navigate to AWS SNS dashboard at https://console.aws.amazon.com/sns/v2/.
- In the left navigation panel, select Topics and open the SNS topic specified during the AWS CloudTrail setup by clicking on its ARN name.
- On the Topic Details <topic name> page, under Subscriptions section, click the Create subscription button.
- Select Email as subscription protocol from the Protocol dropdown list and for the Endpoint just enter the email address where you will receive the AWS CloudTrail log file delivery notifications for this account.
- Click Create Subscription.
- Use your email client application to open the message from AWS Notifications, then click on the appropriate link to confirm your subscription to the SNS topic.
- Repeat steps a – q to enable AWS CloudTrail for the other accounts within your AWS environment (e.g. Test, Staging, Production).
Switch roles and enable cross-account access.
Switching roles enables you to manage resources across AWS accounts using a single IAM user. To switch roles in order to access the AWS accounts created in Section I, sign in to your Identity Account using the appropriate IAM user and quickly access the accounts within your AWS environment using the Identity Menu:

V. Switch roles and enable cross-account access.
01 Sign out from your Identity Account root session, paste the sign-in link copied at step no. 9 (n) into your browser address bar and Sign in again with the IAM user created at step no. 9.
02 Click on the account user name from the navigation bar and select Switch Role from the dropdown menu.
03 Click on the Switch Role button and enter the following information:
- In the Account box, enter the 12-digit ID (e.g.
565392545550) of the account in which the role was created, i.e. the 'Development' account created in Section I of this guide. - In the Role box, enter the name of the role created in Section I at step no. 8.
- In the Display Name box, enter the name/label recommended by AWS. This label will be displayed in the Identity Account menu (Identity Menu) when this role is active.
- Click Switch Role to switch to the selected role and start using the access permissions that the role grants you. The display name and color will now replace the user name in the account navigation bar:
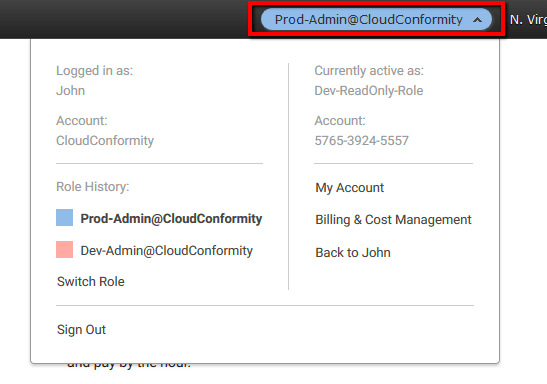 .
.
04 Repeat step c. to switch the role and access the other AWS accounts in your environment. AWS Console will retain your switch role access information in the Role History so you don’t have to enter all the details presented at step c. every time you need to switch roles. To switch easily between AWS accounts just select the appropriate role from the Identity Menu, under Role History section:
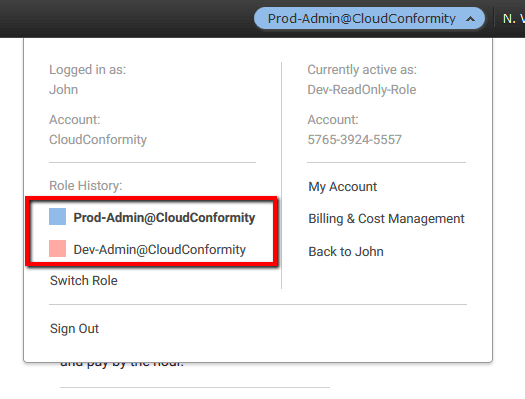
References
- AWS Documentation
- AWS Multiple Account Security Strategy
- AWS Identity and Access Management FAQs
- IAM Best Practices
- Tutorial: Delegate Access Across AWS Accounts Using IAM Roles
- Creating a Role to Delegate Permissions to an IAM User
- Examples of Policies for Delegating Access
- Switching to a Role (AWS Management Console)
- AWS Policy Generator
- Permissions for the Amazon S3 Bucket
- Setting Bucket Policy for Multiple Accounts
