Defending the Expanding Attack Surface: Trend Micro 2022 Midyear Cybersecurity Report
In the beginning of 2022, many companies around the world began calling for most, if not all, of their workforce to return to the office on a full-time basis, a phenomenon aptly referred to as “the Great Return.” Meanwhile, some companies embraced permanent hybrid work or remote setups. This diffused labor pool, together with a widened digital attack surface, has made it increasingly difficult for cybersecurity teams to keep different work structures secure — a susceptibility thread that cybercriminals are quick to pull on to launch critical attacks and exploit vulnerabilities.
We observed how malicious actors favored ransomware-as-a-service (RaaS) methods for faster deployments and bigger payouts. They also used relatively new ransomware families in high-profile attacks and increasingly targeted Linux-based systems with attacks. Ransomware operators also resorted to both novel and tried-and-tested methods to attack cloud environments.
In our midyear security roundup, we highlight the most significant security stories that made a considerable impact on the threat landscape in the first half of the year.
Malicious actors cause Emotet’s resurgence, lock in on Linux

In January 2021, international law enforcement and judicial authorities dismantled the Emotet botnet’s infrastructure. However, after only 10 months, a Trickbot campaign used the same infrastructure. In late 2021, AdvIntel researchers attributed Emotet’s resurgence to its use by Conti ransomware operators. In May 2022, we discovered novel Emotet variants that aimed to trick victims into accessing malicious links and enabling macro content via old and new techniques.
As part of a malware-as-a-service (MaaS) scheme, malicious actors used Emotet as a loader to deploy Conti and other ransomware families to Emotet-infected systems that malicious actors deemed profitable. This aligned with our 2022 security prediction that commodity malware would grow into a formidable threat as ransomware operators continuously integrated it into their attacks.
Data from Trend Micro Smart Protection Network (SPN) shows that Emotet has continued to thrive in 2022. The first half of 2022 saw a whopping 976.7% increase in Emotet detections compared to the first half of 2021, with Japan having the highest number of detections.
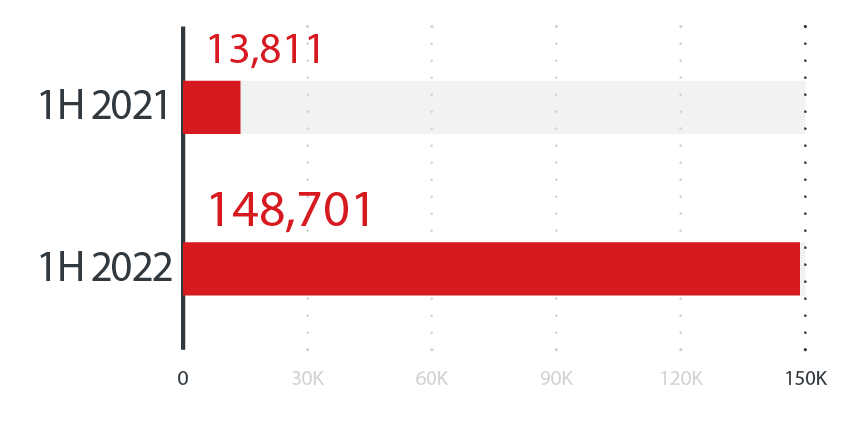
Emotet detections increased by over 10 times in the first half of 2022 compared to the first half of the previous year, likely because of prolific threat actors using it as part of their operations.
Source: Trend Micro Smart Protection Network
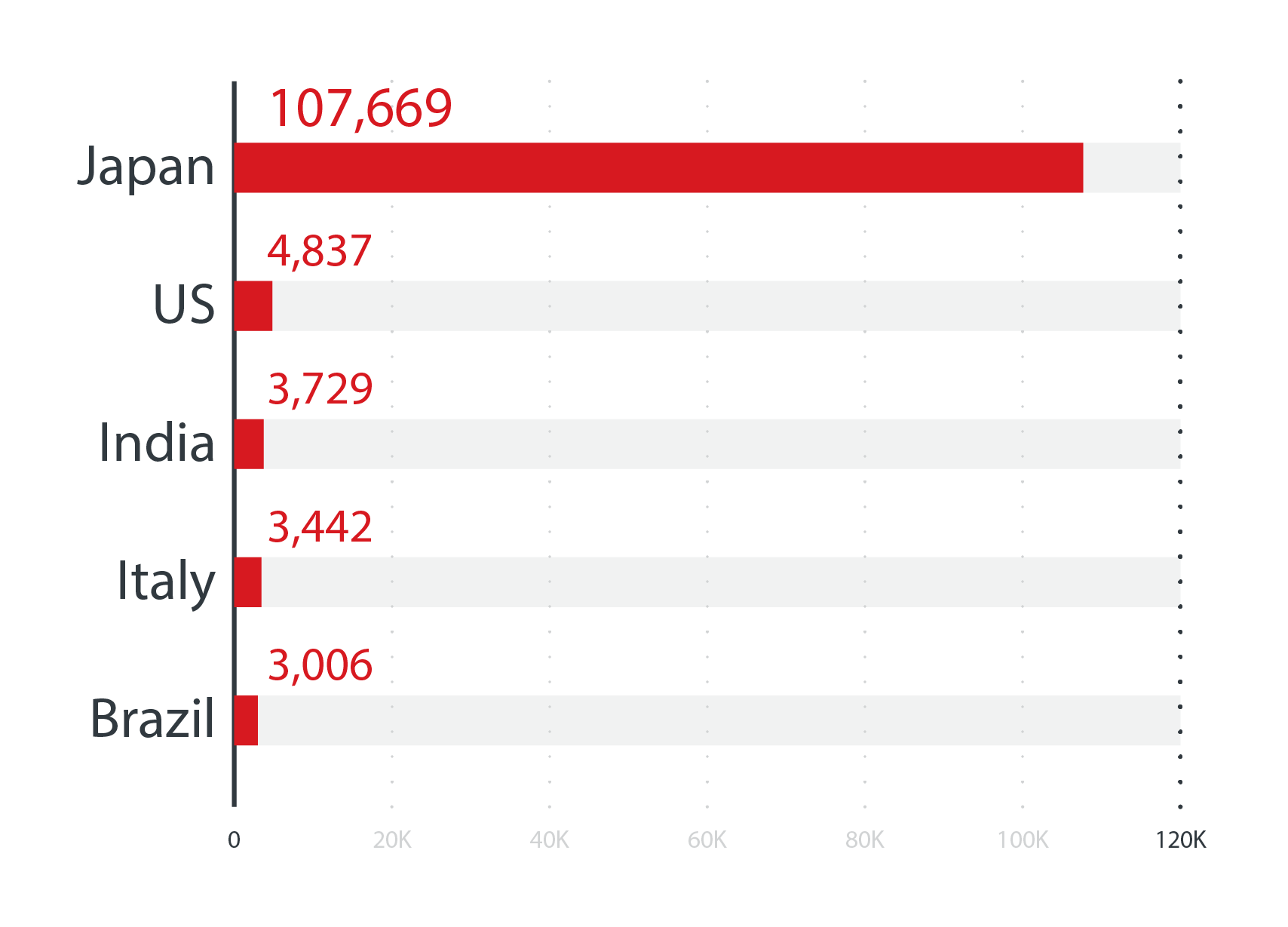
The countries with the highest number of Emotet detections in the first half of 2022
Source: Trend Micro Smart Protection Network
Aside from upping the ante by using MaaS schemes in their attacks, malicious actors are also continuously expanding their attack reach by targeting one of the most powerful operating systems used in cloud platforms and servers worldwide: Linux.
In October 2021, LockBit Linux-ESXi Locker version 1.0 started targeting and encrypting ESXi servers. This year, we discovered a new ransomware variant, called Cheerscrypt that also targeted ESXi servers. Successful infection of these servers, which are widely used by enterprises, could cause significant security issues in critical infrastructures. The emergence of these new Linux ransomware families directly corresponds to what we saw in our SPN data for the first half of the year: a 75% increase in ransomware attacks targeting Linux systems in the first half of 2022 compared to the first half of 2021.
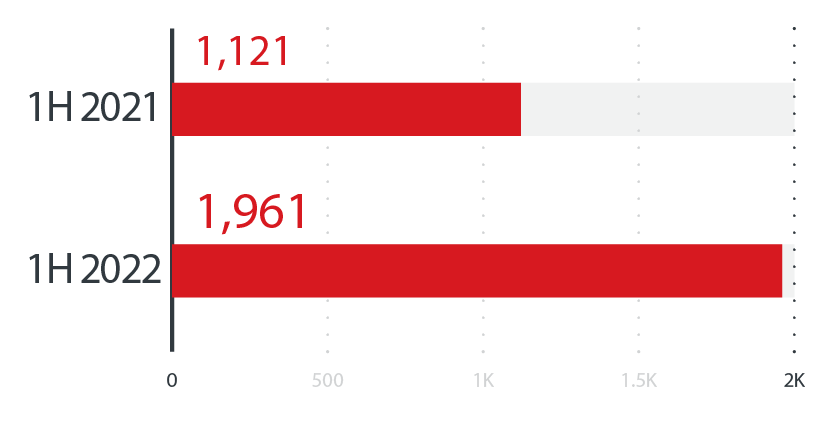
A half-year comparison of the ransomware detection numbers for Linux-based machines
Source: Trend Micro Smart Protection Network

RaaS model prevails, while big game-hunting ransomware families hit organizations worldwide

The RaaS model, which allows affiliates to buy or rent ransomware tools and infrastructures, also made waves in the first half of 2022. Based on the data we gathered, there were 67 active RaaS and extortion groups and over 1,200 victim organizations that were reported in the first six months of this year alone.
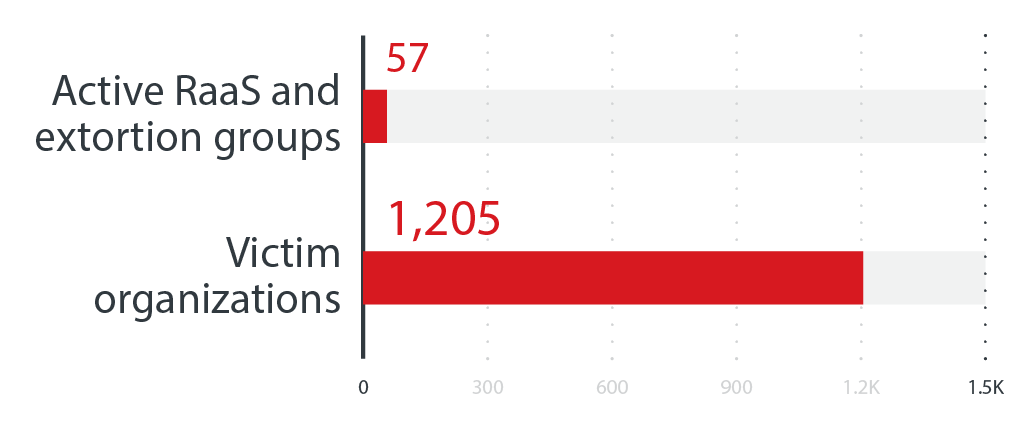
The numbers of active RaaS and extortion groups and the number of victim organizations of successful ransomware attacks in the first half of 2022
Source: RaaS and extortion groups’ leak sites
More streamlined than conventional ransomware models, the RaaS system allows malicious actors — even ones without significant technical backgrounds — to deploy ransomware attacks faster and easier. Based on SPN data, we saw three ransomware families that dominated the RaaS arena in terms of detections: the notorious LockBit and Conti ransomware families and BlackCat, a ransomware family written in the Rust programming language that emerged at the tail end of 2021.
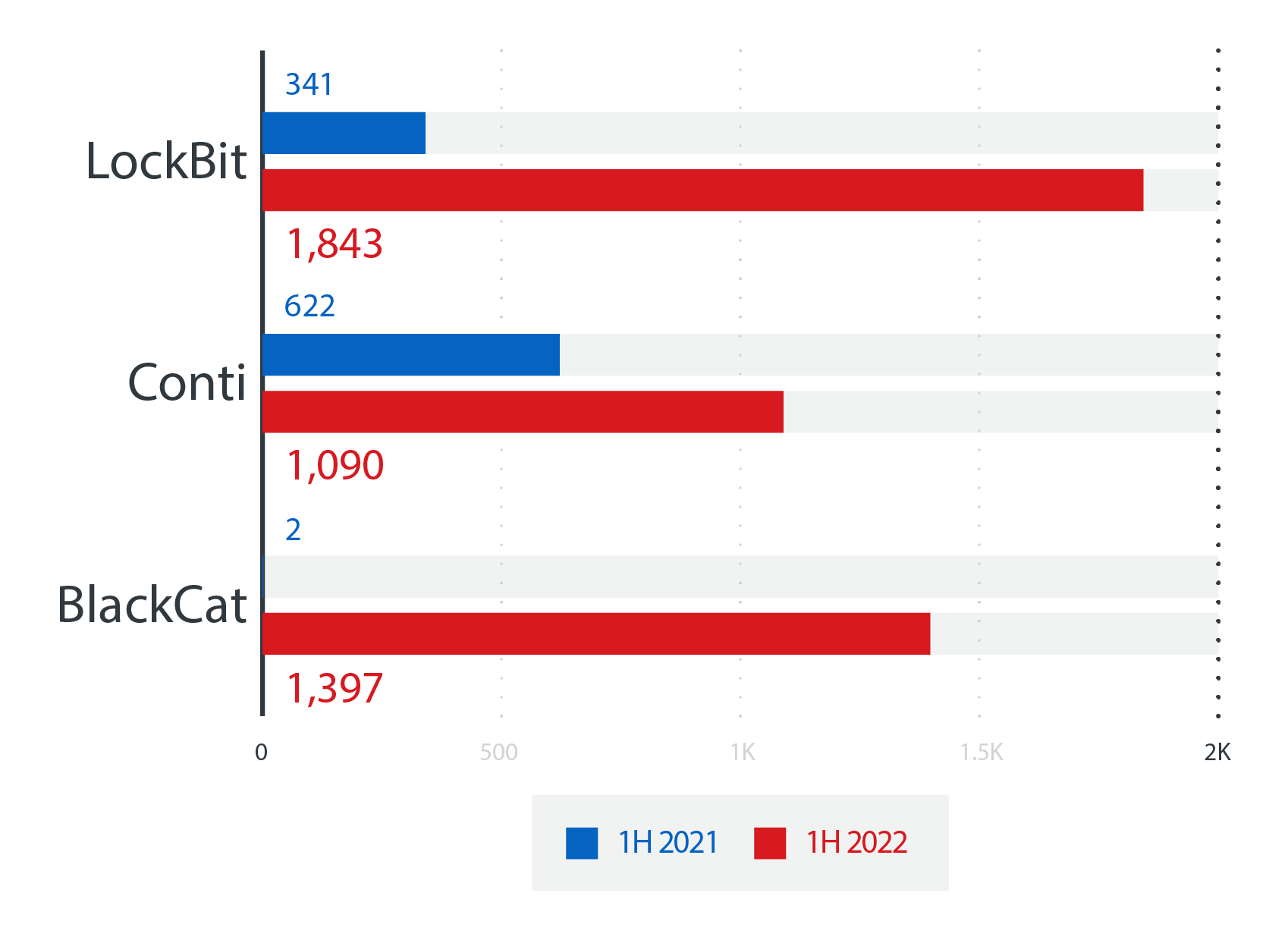
LockBit, Conti, and BlackCat saw a significant increase in detections in the first six months of 2022 compared to the first half of the previous year: The detection numbers for LockBit, Conti, and BlackCat
Source: Trend Micro Smart Protection Network
In our security predictions for this year, we foresaw that ransomware families would go after bigger targets using more advanced methods of extortion — a prediction that fits the bill of the notable ransomware families that we reported on in the first half of 2022.
One of these ransomware families is Black Basta, which emerged in April 2022 and whose operating group has claimed to be behind as many as 50 breaches since June. Black Basta uses a sophisticated encryption routine that involves deleting the service called Fax and creating a new one using the malware’s path and then adding it to the registry for persistence. It also uses a double extortion technique that involves siphoning off critical and confidential data before encrypting it with the goal of threatening and persuading victims to pay the ransom amount. Interestingly, Black Basta’s ransom note is hard-coded into the malware itself, which suggests its possible use of unique binaries for each of its victims.

The wallpaper created by Black Basta using the .jpg file that is dropped in the %temp% folder
Another notable ransomware family, called Nokoyawa, surfaced in the first half of this year and targeted victims in the South American region, specifically in Argentina. Nokoyawa shares common tools and techniques with Hive, a notorious ransomware family that was used to launch ransomware attacks on more than 300 US healthcare organizations in 2021. After analyzing Nokoyawa’s technical details, we were able to observe the distinctions between the two ransomware families: Their binaries were compiled using different languages, and Nokoyawa did not use any packer whatsoever while Hive used UPX.

Cloud misconfiguration is still a top concern, while cloud-based cryptocurrency-mining attacks that use evolutionary tactics are on the rise

Our security predictions anticipated that cloud attackers would use both traditional and novel methods in their attacks this year. Insofar as our observations in the first six months of 2022 are concerned, this prediction is also accurate. We believe that these varied and evolutionary attacks accurately reflect the state of the widening digital attack surface, including how cybercriminals will continue to take advantage of it for ill gain.
In recent years, cloud-based containers have enabled organizations to optimize their processes and development cycles. Because of the ubiquity of these containers and the fact that many such platforms are misconfigured, they continue to be targeted by cybercriminals. According to a May 2022 survey from Red Hat, 53% of survey respondents composed of 300 DevOps, engineering, and security professionals said that they detected a misconfiguration in their containers and/or Kubernetes deployments.
Earlier this year, we investigated Kubernetes clusters that were publicly exposed via port 10250 and found that 243,469 cluster nodes were exposed and identified on Shodan. Out of these, approximately 600 nodes returned the “200 – OK” notification when queried. Notably, an attacker could abuse these nodes by installing and running malicious programs via the kubelet API. Although majority of these Kubernetes cluster nodes blocked anonymous requests and returned “401 Status Code – Unauthorized,” these could still be compromised by a skilled malicious actor via the kubelet authentication token or other exploits.
Aside from containers, we observed that cybercriminal teams remained invested in stealing cryptocurrency-mining capabilities from victims’ resources in the first half of the year by continuously upgrading their attack arsenals and tactics.
Based on research that we conducted in 2021 and published earlier this year, we determined the five most prominent malicious actor groups in the cryptocurrency mining space and how they had conducted their operations:
Outlaw
- Prefers to stick to the tools and techniques it has used over the years
- Targets internet-of-things (IoT) devices and Linux cloud servers by exploiting known vulnerabilities or performing brute-force Secure Shell Protocol (SSH) attacks

TeamTNT
- Is one of the most technically proficient cryptocurrency mining-focused threat actors due to its ability to adapt quickly and update its arsenal
- Is known for being very active on social media
- Is known for exploiting misconfigurations and vulnerable software to compromise hosts prior to stealing credentials for lateral movement
Kinsing
- Shares similarities with TeamTNT in terms of its ability to adapt quickly and update its toolkit
- Has no active social media or underground forum presence
- Is known for quickly abusing new exploits in a short period, as with its use of the Log4Shell vulnerability only a few days after the flaw was made public
8220
8220
- Is known for exploiting vulnerabilities, especially those that affect the Oracle WebLogic Server
- Was 10 times more active in 2021 than in 2020
- Is known for competing with Kinsing for the same resources, with both deleting each other’s components from compromised machines to exploit as many resources as possible
Kek Security
Kek Security
- Is a relatively new group that uses sophisticated techniques and integrates new exploits in its attacks
- Is known for continuously developing its own malware that incorporates better obfuscation capabilities
Threat landscape in brief
63,789,373,773
Overall number of threats blocked in the first half of 2022
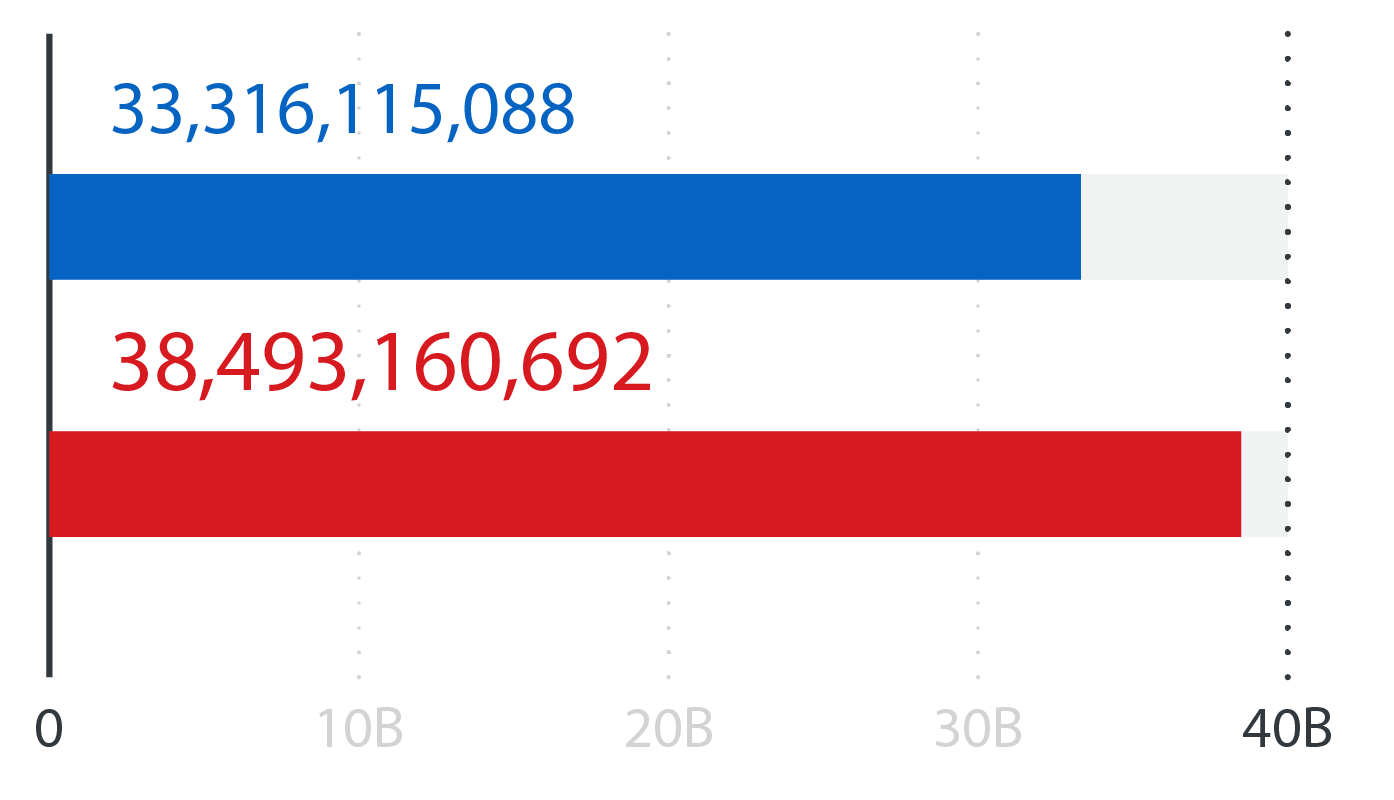
Blocked email threats
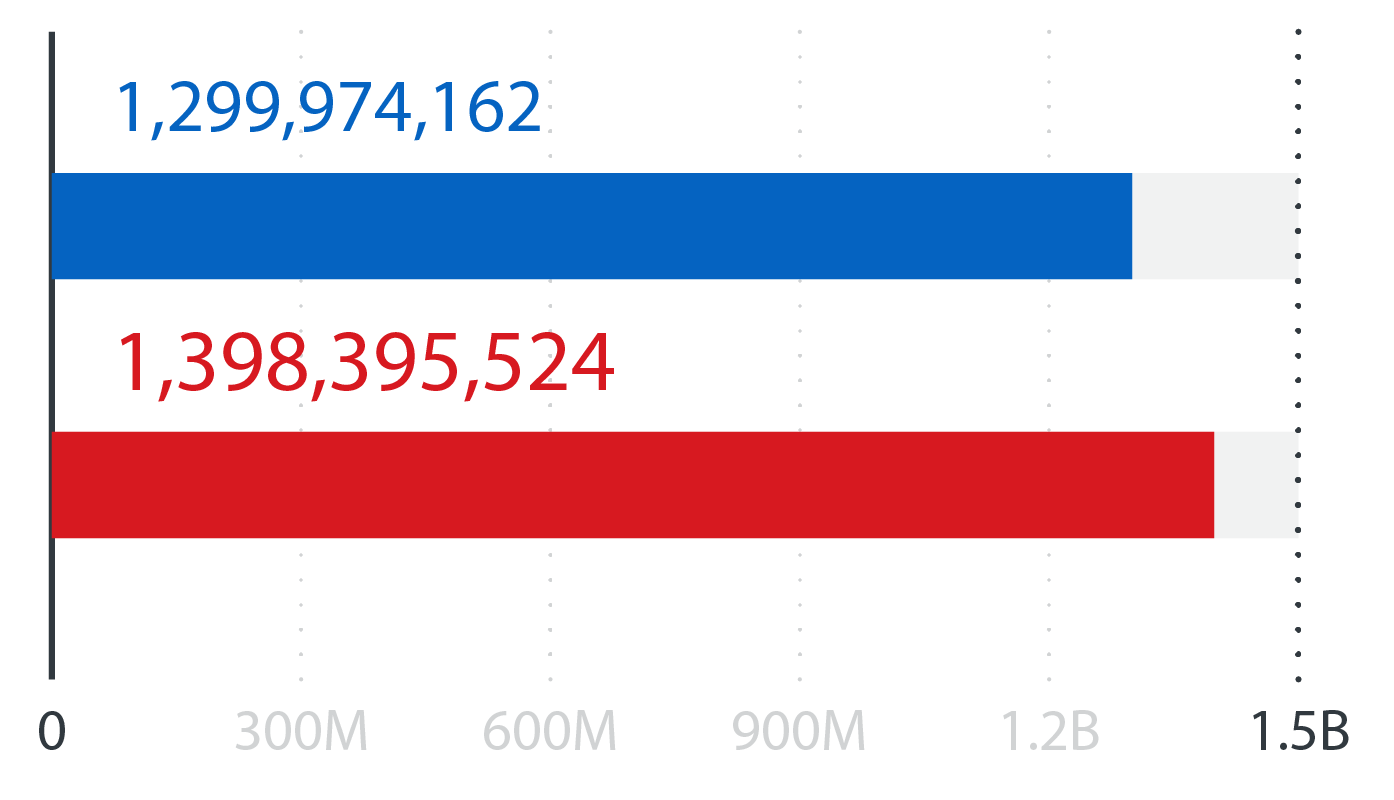
Blocked malicious URLs
Blocked malicious files
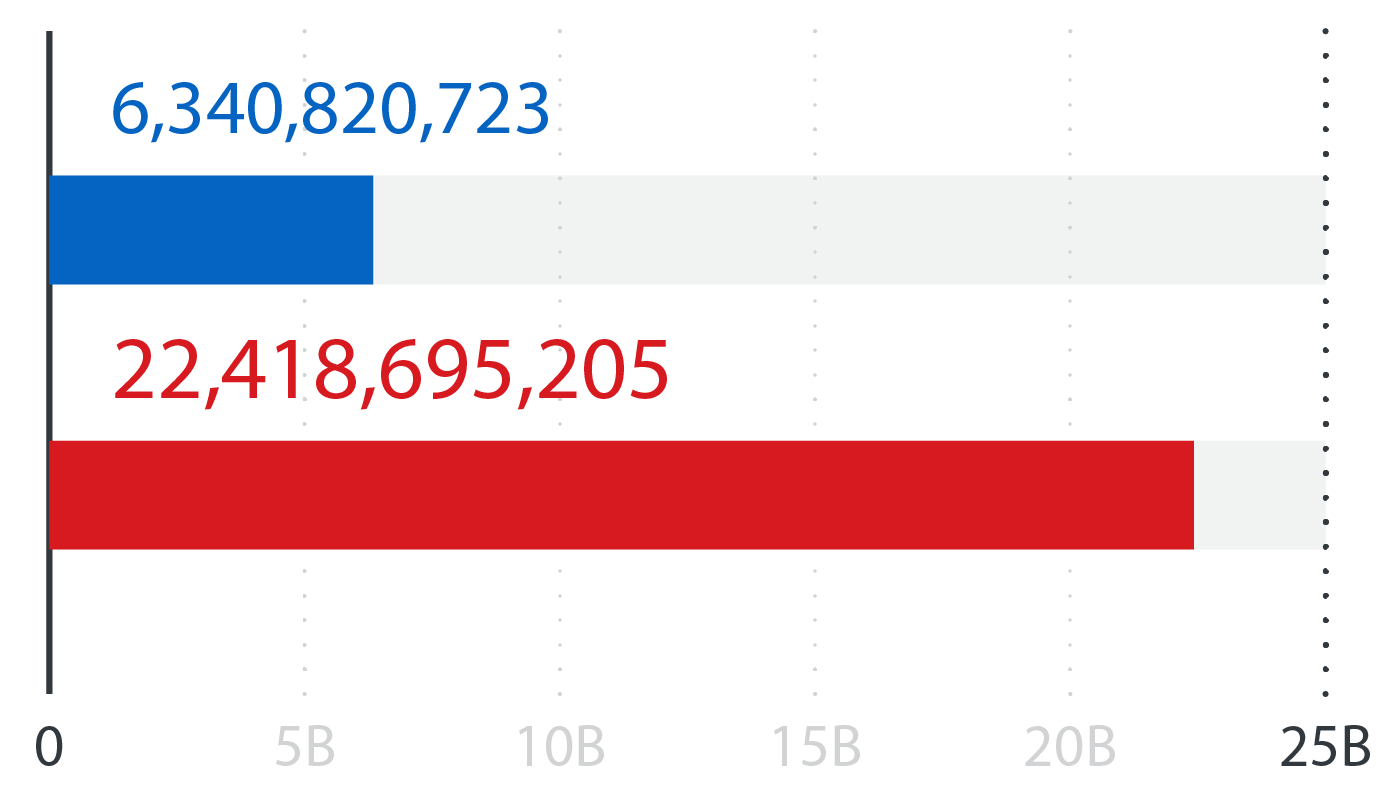
Email reputation queries
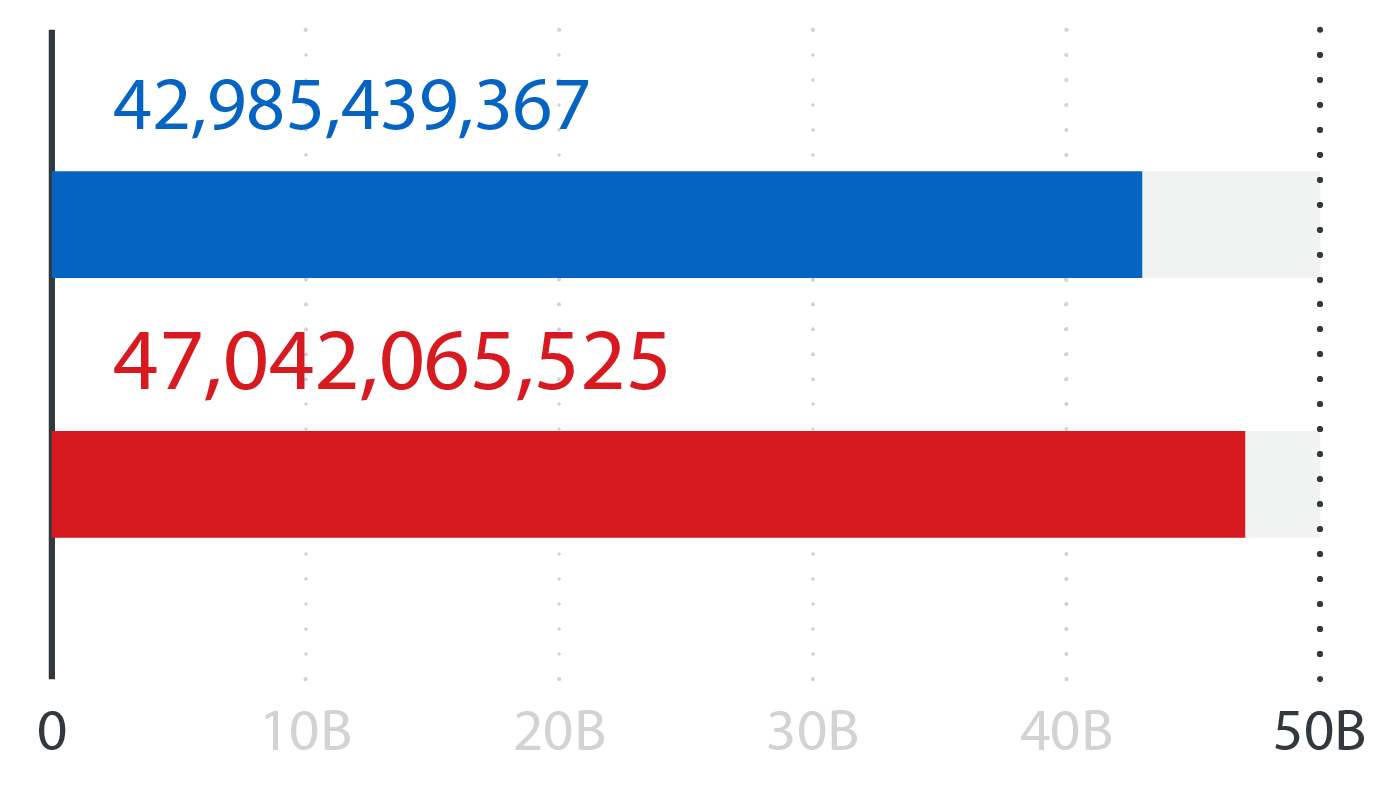
URL reputation queries
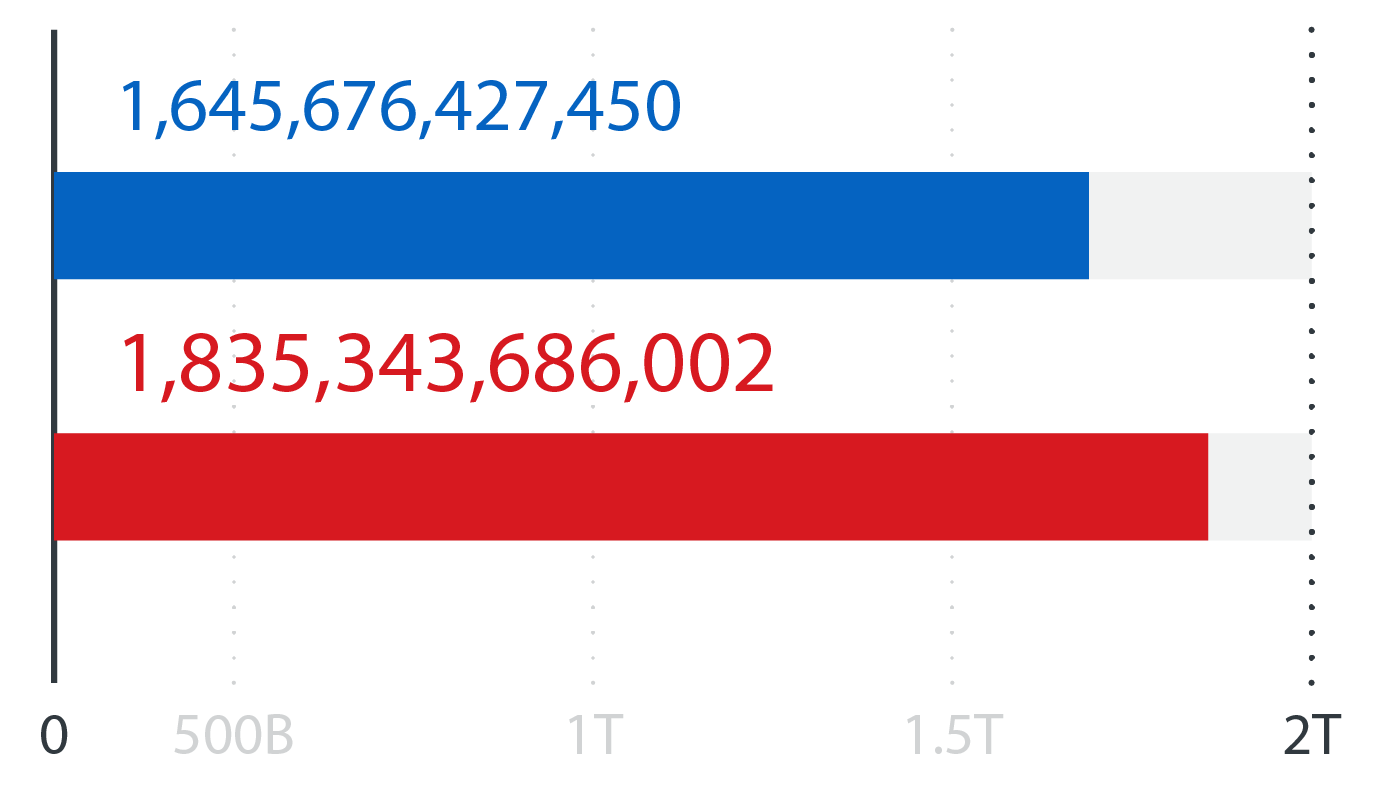
File reputation queries
![]()
Download our full midyear roundup report to learn vital insights and security recommendations aimed at helping organizations build a holistic and multilayered cybersecurity strategy to keep them protected against both current and future threats in the midst of a widening attack surface.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.


 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks