Smart Yet Flawed: IoT Device Vulnerabilities Explained
 View Infographic: Common IoT Device Vulnerabilities
View Infographic: Common IoT Device Vulnerabilities
The variety and range of functions of smart devices present countless ways of improving different industries and environments. While the “things” in the internet of things (IoT) benefit homes, factories, and cities, these devices can also introduce blind spots and security risks in the form of vulnerabilities.
Vulnerable smart devices open networks to attack and can weaken the overall security of the internet. For now, it is better to be cautious and understand that “smart” can also mean vulnerable to threats.
Why are IoT devices vulnerable?
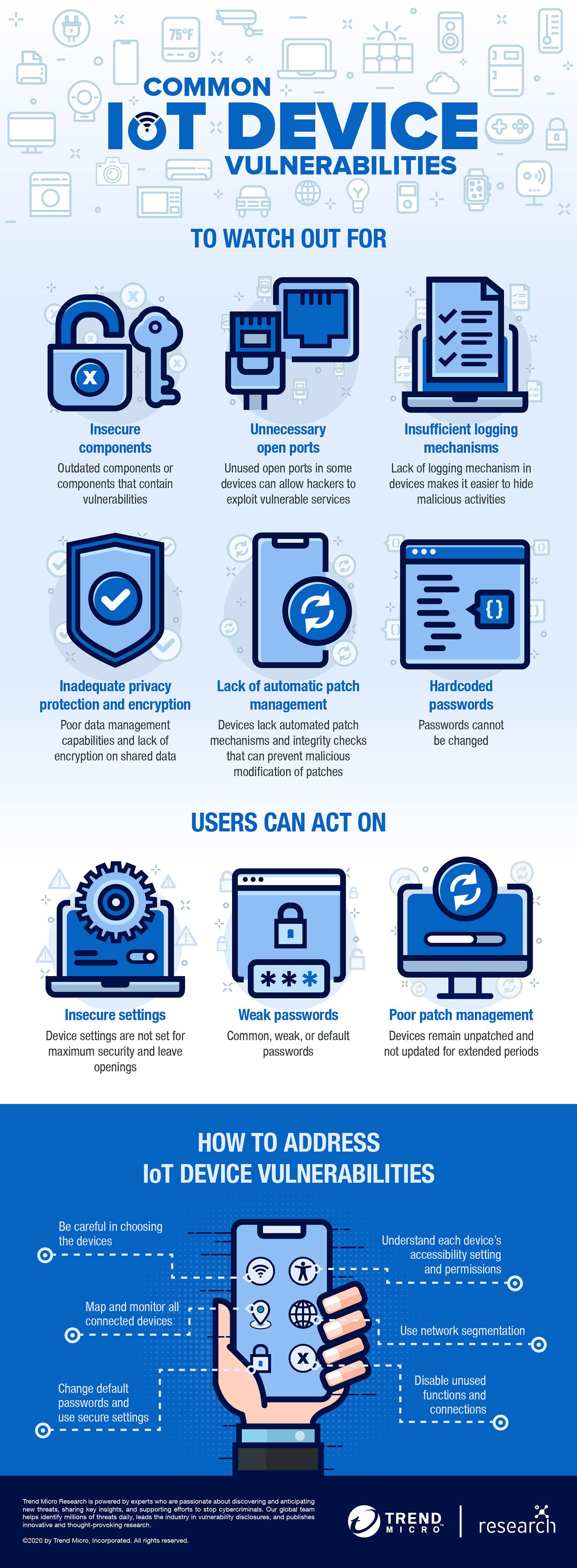
IoT devices are vulnerable largely because these devices lack the necessary built-in security to counter threats. Aside from the technical aspects, users also contribute to the devices’ vulnerability to threats. Here are some of the reasons these smart devices remain vulnerable:
- Limited computational abilities and hardware limitations. These devices have specific functions that warrant only limited computational abilities, leaving little room for robust security mechanisms and data protection.
- Heterogeneous transmission technology. Devices often use a variety of transmission technology. This can make it difficult to establish standard protection methods and protocols.
- Components of the device are vulnerable. Vulnerable basic components affect millions of deployed smart devices.
- Users lacking security awareness. Lack of user security awareness could expose smart devices to vulnerabilities and attack openings.
Device vulnerabilities allow cybercriminals to use them as a foothold for their attacks, which reinforces the importance of security from the design phase.
How do device vulnerabilities affect users?
Looking into some of the more notable attacks on IoT devices shows how it can affect users. Threat actors can use vulnerable devices for lateral movement, allowing them to reach critical targets. Attackers can also use vulnerabilities to target devices themselves and weaponize them for larger campaigns or use them to spread malware to the network.
IoT botnets serve as an example that demonstrates the impact of device vulnerabilities and how cybercriminals have evolved to use them. In 2016, Mirai, one of the most prominent types of IoT botnet malware, made a name for itself by taking down prominent websites in a distributed denial of service (DDoS) campaign consisting of thousands of compromised household IoT devices.
From a business perspective, IoT devices further blur the distinction between the necessary security of businesses and homes, especially in work-from-home scenarios. Introducing IoT devices to the household can open new entry points in an environment that might have weak security, exposing employees to malware and attacks that could slip into a company’s network. It’s a significant consideration when implementing bring your own device (BYOD) and work-from-home arrangements.
Attackers can also use IoT devices with existing issues to get into internal networks. These threats range from DNS rebinding attacks that allow for gathering and exfiltrating information from internal networks to new attacks via side channels, such as infrared laser inducted attacks against smart devices in homes and corporate environments.
Examples of IoT device vulnerabilities
There have been many cases that demonstrate the impact of IoT vulnerabilities; some of them involve real-world settings and others as research into these devices. The Open Web Application Security Project (OWASP), a non-profit foundation for improving software, annually releases a list of the top IoT vulnerabilities. Examples of these common flaws include the following:
Weak, guessable, or hardcoded passwords
New variants of malware typically use this vulnerability. For example, we found a Mirai variant called Mukashi, which took advantage of CVE-2020-9054 and used brute force attacks with default credentials to log into Zyxel NAS products.
Insecure ecosystem interfaces
Our research into complex IoT environments revealed exposed automation platforms that chain the functions of multiple devices. The exposed automation server contained important information like the home’s geolocation and hardcoded passwords. The implications of a compromised automation platform are further discussed in the research.
Insecure network services
A research conducted by Trend Micro in 2017 looked into the security of Sonos smart speakers. The study found how simple open ports exposed the device to anyone on the internet and revealed sensitive user information.
Cases that demonstrate the consequences of device vulnerabilities on users and networks are not difficult to find, and such cases will likely continue to be reported in the future. Users should be mindful of these common vulnerabilities and take the necessary precautions against exploits. We detail more IoT-related attacks and provide security recommendations in our IoT resource page.
Who is responsible for securing IoT devices?
The potential for unpredictable cascading effects of vulnerabilities and poor security in the IoT greatly affects the overall security of the internet. Ensuring that these devices are secure is the shared responsibility of its stakeholders.
Manufacturers need to address known vulnerabilities in succeeding products, release patches for existing ones, and report the end of support for older products. IoT device manufacturers also need to consider security right from the design phase, then conduct penetration tests to ensure that there are no unforeseen openings for a system and device in production. Companies should also have a system in place for accepting vulnerability reports from outside entities on their deployed products.
Users must also gain a better comprehension of the security risks that come with connecting these devices and their role in securing them. Changing default passwords, updating firmware, and choosing secure settings, among others, can mitigate the risks.
[Read: The First Steps in Effective IoT Device Security]
For a more complete and multi-layered defense, users can employ comprehensive protections such as the Trend Micro™ Security and Trend Micro™ Internet Security solutions, which offer effective safeguards against threats to IoT devices through features that can detect malware at the endpoint level. Connected devices can also be protected by security software such as the Trend Micro™ Home Network Security and Trend Micro™ Home Network Security SDK solutions, which can check internet traffic between the router and all connected devices. The Trend Micro™ Deep Discovery™ Inspector network appliance can monitor all ports and network protocols for advanced threats and protect enterprises from targeted attacks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One