Pushing the Outer Limits: Trend Micro 2024 Midyear Cybersecurity Threat Report
PUSHING THE
OUTER LIMITS
TREND MICRO 2024 MIDYEAR CYBERSECURITY THREAT REPORT
With the goal of creating fast, evasive, and sophisticated threats and campaigns, malicious actors are always on the prowl for new technologies to abuse, significant world events to exploit, and mismanaged and vulnerable assets to compromise. This is what we’ve observed in the first half of the year, with cybercriminals injecting new technologies including artificial intelligence (AI) to time-tested attacks, exploiting global events such as the Olympics and national elections for ill gain and targeting misconfigured and exposed assets to surreptitiously invade systems and steal sensitive data.
In years past, cybersecurity has metamorphosed to keep abreast with increasingly complex and calculated attacks. And in the years to come, the security industry — and the way in which business leaders and security teams tackle ever-changing threats and risks — would need to stay ahead of the curve via robust data-driven insights and a holistic, risk-based approach to keep systems and data safe.
In this report, we highlight the most pressing cybersecurity events we’ve covered and the notable security trends we’ve observed in the first six months of 2024. To give a clearer picture of the cyberthreat landscape, our midyear report also features data from our eXtended Detection and Response (XDR) solution and our cyber risk lifecycle management solution, the Attack Surface Risk Management (ASRM), which are both part of our flagship cybersecurity platform, Vision One.
Ransomware and phishing are subjected to massive law enforcement disruptions
LockBit topped the list of ransomware families with the highest file detections during the first half of this year. Banking institutions were hit hardest by ransomware attacks in the first half of 2024, followed closely by organizations in the technology industry.
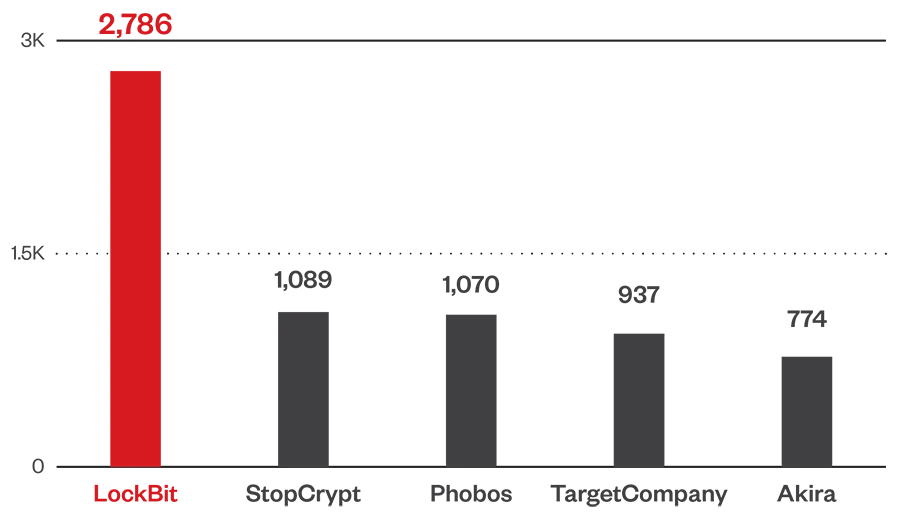
Source: Trend Research telemetry data
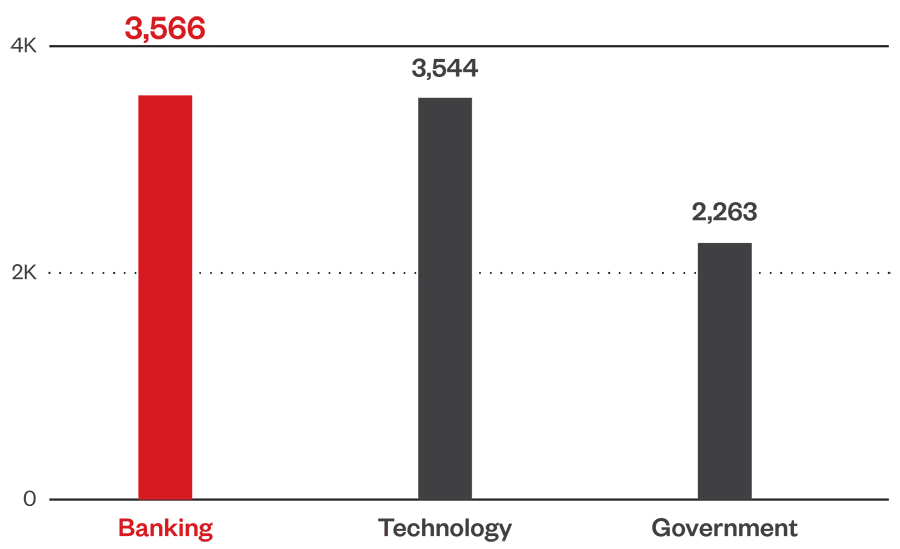
Source: Trend Research telemetry data
In the first half of 2024, we’ve seen law enforcement agencies launch major operations to disrupt ransomware groups, compromising botnets and platforms used by cybercriminals to deploy ransomware and carry out phishing operations.
In February 2024, a targeted law enforcement operation dubbed Operation Cronos disrupted the biggest financial threat actor group of 2023, LockBit.
Despite its operations being hampered, reputation being tarnished, and affiliates’ identities being disclosed, LockBit made efforts to appear like they were unaffected, although our own analysis shows otherwise and that these numbers are inflated.
Experienced ransomware groups such as LockBit understand that they need to evolve to keep their coveted spots in the ransomware community. During Operation Cronos, we analyzed an in-development LockBit sample with a completely new code base that we track as LockBit-NG-Dev (where NG stands for “new generation”). Based on our analysis, LockBit-NG-Dev is written in .NET, is compiled using CoreRT, and is believed to be platform-agnostic.
On top of its crippled ecosystem and the ongoing dismantling of its affiliate network, LockBit was dealt more blows to its operations and prominence under sanctions imposed as part of Operation Cronos: The second phase of the operation, which was announced in May 2024, involved asset freezes and travel bans levied against the ransomware group’s alleged administrator and developer, who currently has a 26-count indictment against him in the US.
Another grand law enforcement disruption happened in May 2024 in the form of Operation Endgame.
Operation Endgame disrupted ransomware-linked botnets and droppers such as IcedID, Pikabot, Smokeloader, and Trickbot.
This joint endeavor resulted in the disruption of 100 servers and the seizure of over 2,000 malicious domains.
Although Operation Endgame is, by far, the largest operation against botnets in recent history that greatly impacts many ransomware groups’ operations, ransomware operators are bound to explore other ways to infect victims’ systems – such as exploiting critical vulnerabilities, abusing remote monitoring and management (RMM) tools, launching bring-your-own-vulnerable-driver (BYOVD) attacks, and using custom shell scripts.
Cybercriminals were dealt a blow in April 2024, during which Operation Stargrew took down LabHost, a cybercrime platform that emerged in late 2021 and provided phishing-as-a-service (PhaaS).
LabHost had more than 2,000 criminal users at the time of the takedown. Its tiered membership model offered a variety of phishing options, with monthly fees ranging from US$179 to US$300. These phishing services targeted banks and businesses worldwide, particularly those in Canada, the US, and the UK.
Operation Stargrew was a collaborative effort led by the Metropolitan Police Service in the UK, in cooperation with international law enforcement agencies and industry partners that included Trend Micro. The LabHost platform was disabled, fraudulent sites linked to it have been seized, and 37 key arrests were made as part of this joint operation.
Notable TTPs in ransomware attacks for 1H 2024

BlackBasta
BlackBasta
Early this year, we've reported on how ransomware actors, including Black Basta and Bl00dy Ransomware gangs, have exploited ConnectWise ScreenConnect software vulnerabilities (CVE-2024-1708 and CVE-2024-1709) to compromise systems, steal data, and hamper operations.

Team City
Team City
Threat actors also exploited two critical Team City On-Premises vulnerabilities (CVE-2024-27198 and CVE-2024-27199) that allowed them to achieve remote code execution (RCE) on an infected system.
Microsoft Quick Assist
Microsoft Quick Assist
Black Basta actors were observed misusing Microsoft Quick Assist in social engineering attacks that involve voice phishing (vishing), deploying RMM tools, and delivering ransomware.

Kasseika ransomware
Kasseika ransomware
Kasseika ransomware operators deployed BYOVD attacks and abused Martini driver to terminate the victim machine’s antivirus related processes.

Agenda ransomware
Agenda ransomware
Agenda ransomware operators were seen to use the Rust variant, which uses a custom PowerShell script, to propagate to VMWare vCenter and ESXi servers. Agenda ransomware also added a new feature: It prints out the ransomware note on connected printers.

TargetCompany ransomware
TargetCompany ransomware
The TargetCompany ransomware group launched a new Linux variant that uses a custom shell script for payload delivery and execution.
In the first half of the year, ransomware actors employed a variety of techniques in their attacks. The table below highlights the evolving tactics and persistence mechanisms that ransomware groups commonly adopted to compromise and move within targeted networks.
Initial access
- Distributed, with
a variety of techniques
used
Persistence
- bitsadmin_transfer
- encoded_command
Credential access
- lsass_dump
- esentutl_copy
- ntdsutil_dumping
Lateral movement
- portscan
- adfind
Most used commands and processes observed in ransomware attacks per phase in 1H 2024
Source: Trend Micro Vision One – Targeted Attack Detection data
Malicious actors lock in on dangling resources, exposed credentials, and vulnerabilities to compromise cloud-based apps, services, and assets
Accessing high-risk cloud applications dominated the list of risk events in the first half of the year. The lack of updated endpoint protection in unmanaged devices exposes businesses to further risk. More risk-related data and insights can be found in Intercepting Impact, the 2024 Trend Micro cyber risk report.
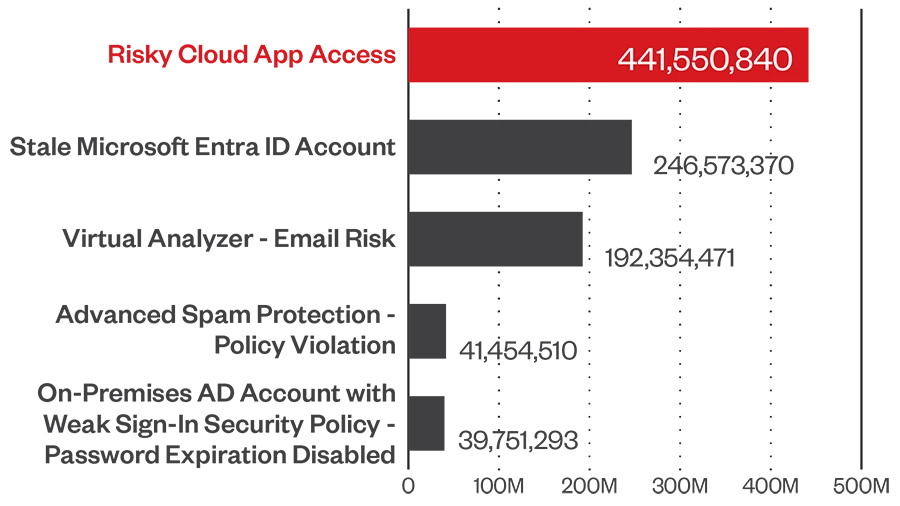
Source: Trend Research telemetry data
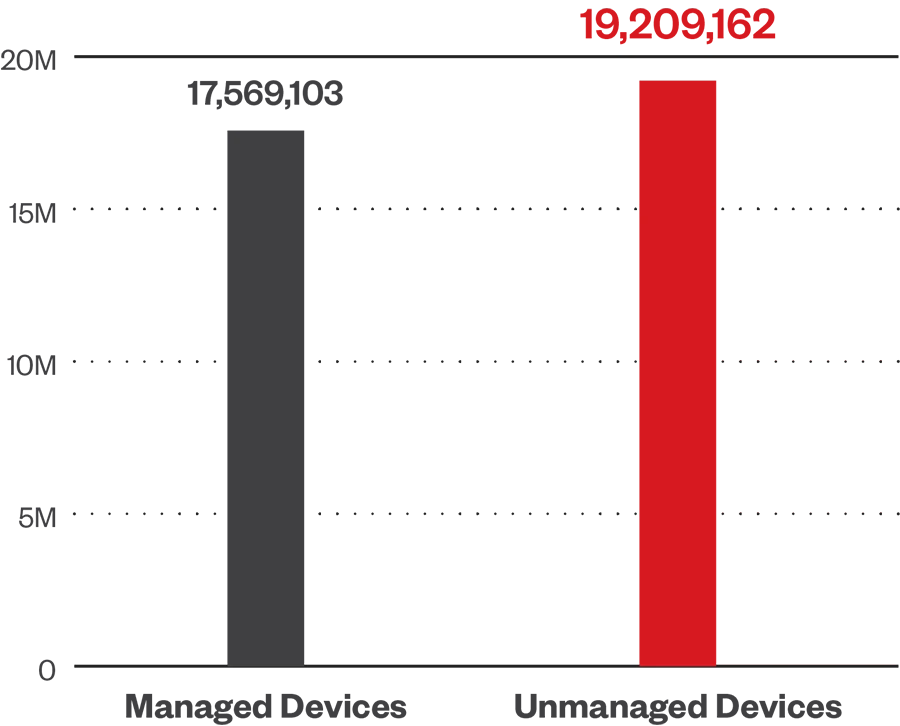
Source: Trend Research telemetry data
Managed devices
Devices which have installed Trend Micro endpoint security solutions and are actively monitored and maintained by an organization's IT team.
Unmanaged devices
Devices discovered by security solutions and are not under Trend Micro control or oversight of an organization's IT or security management systems.
It’s not all new tactics in the first half of 2024: We’re still seeing cybercriminals gravitating toward time tested attacks and looking for exposed sensitive information to gain a foothold in victims’ environments and steal critical information.
Recently, it was reported that The New York Times suffered from a data breach when a malicious actor exploited an exposed credential to a cloud-based third-party platform. An anonymous 4chan user claimed to have access to 5,000 unencrypted GitHub repositories containing 3.6 million files, including sensitive authentication details, and even source code for the web-based game Wordle.
Earlier this year, we reported on a cryptojacking campaign that exploits exposed Docker remote API servers: Based on our analysis, malicious actors abused exposed Docker servers to deploy cryptocurrency miners via Docker images from the Commando project, an open-source GitHub project used by developers. We’ve also observed cybercriminals taking advantage of legitimate yet misconfigured tools in their attacks
In March, we talked about how developers need to secure their APISIX API gateway configurations by changing the hardcoded default master API token for accessing the administration API. We’ve seen multiple exposed instances in the wild that malicious actors could exploit to perform remote code execution (RCE).
Another API gateway we’ve focused on in the first half of 2024 was the Kong API gateway. Our report discusses the growing number of exposed Kong API gateway instances we’ve observed in the wild, which has been on an upward trend since 2021, and how such exposures can allow cybercriminals to put back-end services at risk.
In May 2024, we reported on the misconfigured deployments that we’ve found in the open-source monitoring tool Container Advisor (CAdvisor). Malicious actors could perform reconnaissance, lateral movement, privilege escalation, supplychain compromise, and vulnerability exploitation when they get ahold of unsecure CAdvisor instances that exposed sensitive environmental variables.
APT campaigns upgraded their arsenal to expand their reach
In the first half of 2024, APT groups continued to explore new ways of innovating their repertoire of tools and tactics in a bid to ensnare a bigger pool of victims.
Compromised internet-facing routers have appealed to both nation-state threat actors and cybercriminals for their use as an anonymization layer. Whereas APT groups like Sandworm opt to use their own dedicated proxy botnets, APT29 favors commercial residential proxy networks, and Pawn Storm used the third-party proxy botnet of Ubiquiti EdgeRouter devices before the botnet was disrupted by the FBI in January 2024.
We also reported on Earth Krahang’s APT campaign and the group’s preferred tactic of leveraging compromised government infrastructure to carry out its operations. We identified connections between Earth Krahang and the China-nexus threat actor Earth Lusca through similarities in their infrastructure and backdoors used, although it’s possible that these are two intrusion sets operating independently.
Threat group Earth Lusca was also behind a new campaign featuring social engineering tactics that capitalized on China-Taiwan relations: Earth Lusca disseminated their malware using email lures that were likely based on legitimate documents stolen from geopolitical experts, just ahead of the Taiwanese national elections in early 2024.
Cyberespionage group Earth Hundun has persisted in carrying out attacks using the Waterbear backdoor, notorious for the constant updates that have given it a bevy of advanced evasion techniques. Earth Hundun has been using and further developing its most recent variant, Deuterbear, with additional features: Deuterbear has a shellcode format, is capable of anti-memory scanning, and has the same traffic key as its downloader.
Fraudsters are poised to exploit still-uncharted frontiers of AI
As businesses explore new use cases for AI technology, missteps are inevitable and may create fresh opportunities for the criminal element in the process. Cybercriminals, too, have been known to pivot to new directions in their push to harness the benefits of AI.
In June, Microsoft delayed the release of its controversial Recall feature owing to privacy concerns over the AI tool’s tracking of user activity. Recall, which was supposed to be rolled out in Copilot+ PCs in June, takes and locally stores screenshots of users’ computer usage, potentially making it a target for malicious actors who are after user credentials and other confidential data.
During the first half of 2024, we’ve observed that cybercriminals have shifted their attentions to jailbreaking existing large language models (LLMs) instead of training their own. “Jailbreakas-a-service” offerings have been on the rise, designed to bypass LLMs’ built-in ethical safeguards through various means like prompting LLMs with hypothetical questions, roleplay scenarios, or questions in a foreign language.
AI-enabled fraud is shaping up to be a formidable threat thanks to tools like GoldPickaxe.iOS, a trojan discovered in February that’s able to collect biometric data with which to make deepfakes. These scams have also proven lucrative, as when fraudsters made a $25.6 million payday in February after impersonating London-based company Asup’s chief financial officer in a deepfaked video call.
OpenAI and Microsoft have also identified China-affiliated threat actor Earth Lusca among the threat actors that used OpenAI’s services to perform tasks like information-gathering, generating content and translations that may be used in phishing, and creating scripts likely to fine-tune their attacks. Since the release of their joint findings in February, OpenAI has disabled the accounts related to the APT actor.
Cybercriminals have capitalized on the increased interest in AI technologies around the world, as evidenced by Void Arachne: As part of its campaign targeting Chinese-speaking users, the threat group was observed bundling legitimate AI software with their malicious payload. To cast a wider net of potential victims, the group has also been proliferating malicious installer files that contain nudifiers and other deepfake-generating AI tools.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Related Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- Complexity and Visibility Gaps in Power Automate
- Do Security Blogs Enable Vibe-Coded Cybercrime?
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One