Ransomware Recap: Locky Returns, Cerber Evolves Anew
When the ransomware Locky was first discovered in early 2016, it relied on a malicious macro embedded in Microsoft Word (MS) documents as its main distribution technique. After a brief campaign hiatus, a new variant of Locky (Detected by Trend Micro as PDF_LOCKY.A) has emerged that uses a macro-enabled Microsoft Word document nested within a PDF file as a new propagation method.
Like previous variants, Locky arrives via spam emails containing a PDF file attachment. The PDF file contains a *.docm (the extension used for documents containing macros) file attached. After the file is opened, the *.docm file containing the macro will continue to run alongside the code, disguised as a social engineering attack. One notable characteristic of this instruction is that it doesn’t match the UI—the mentioned buttons don’t actually exist.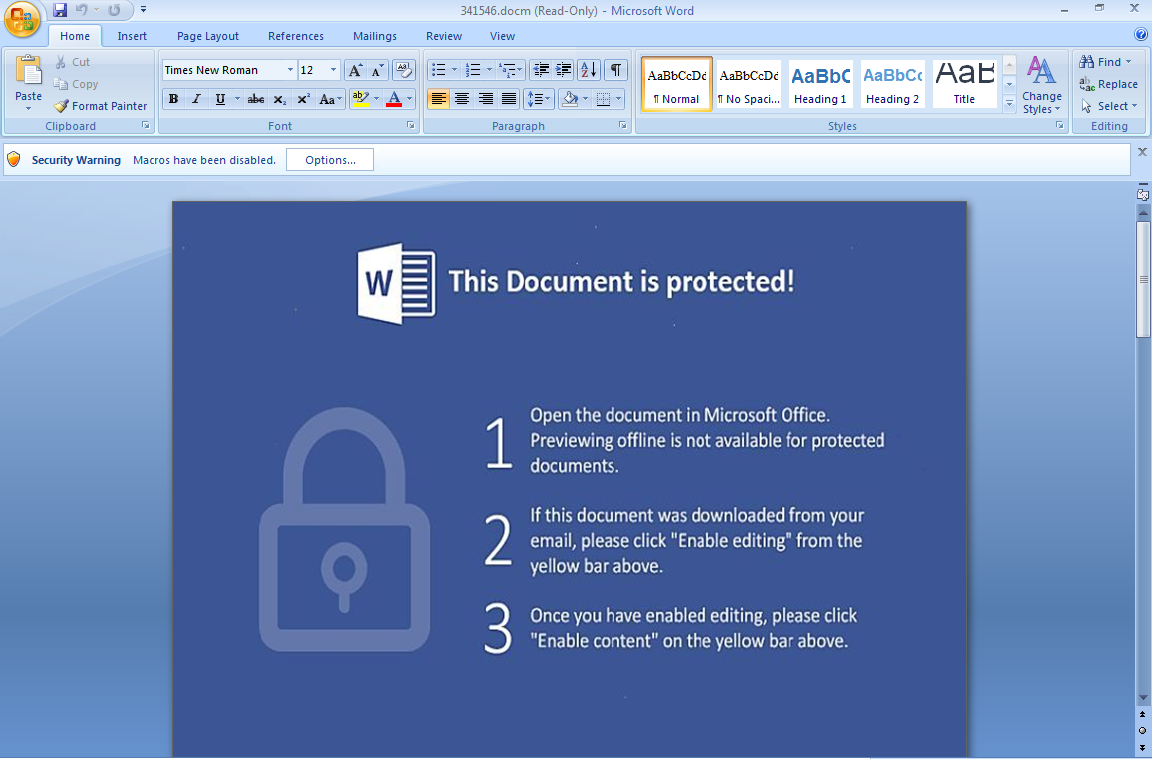
The macro will then be executed, resulting in the download of the ransomware file from a Command & Control (C&C) server. The following files will then be placed in the user’s %temp% folder: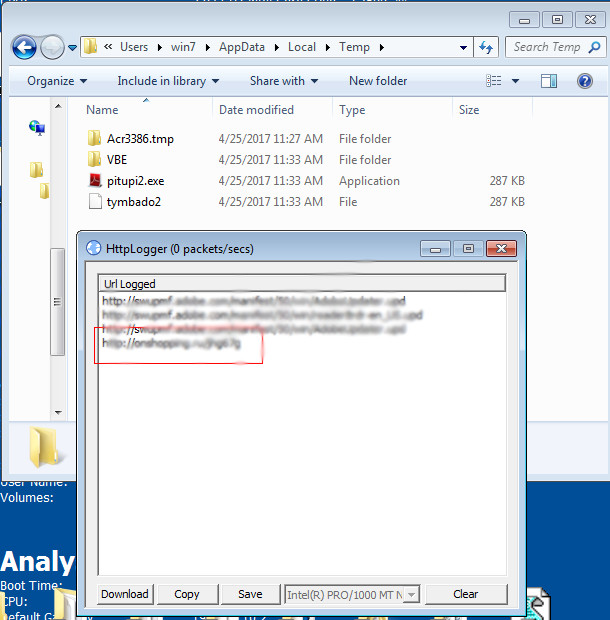
The list of targeted files and the .osiris affix are carried over from previous Locky variants. After the encryption routine finishes, the following ransom note will be displayed: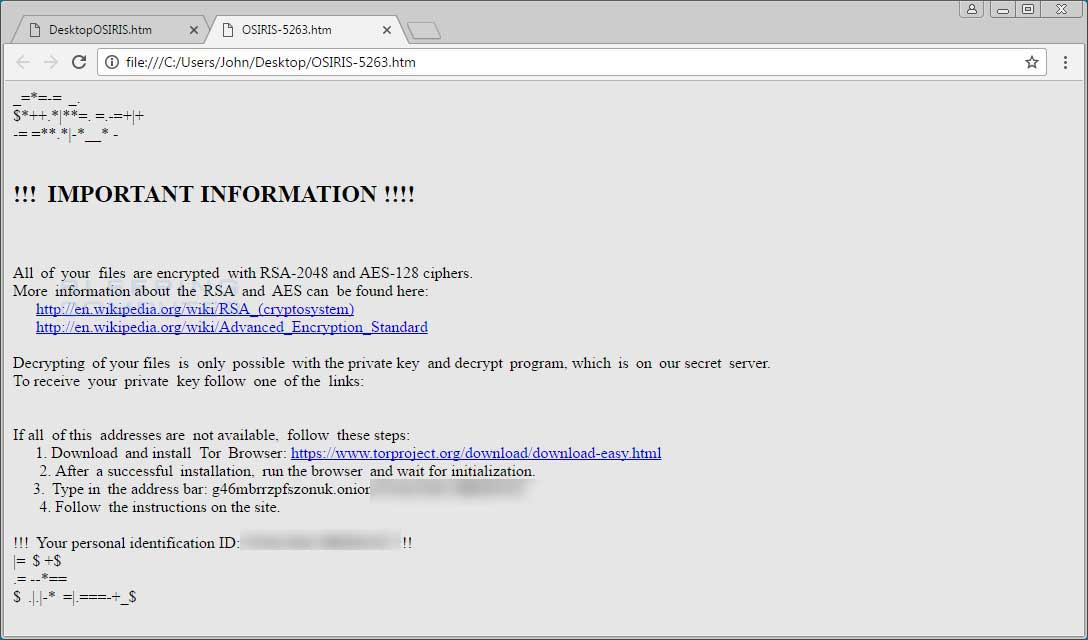
Image c/o Bleeping Computer
CERBER 6
Few ransomware has had as much impact as the CERBER ransomware (detected by Trend Micro as RANSOM_CERBER family). In the amount of time since its first variants were discovered, the notorious ransomware has gone through several iterations—with each variant sporting additions such as anti-sandbox and anti-virus features.
The latest variant in the wild, CERBER 6, is similar to other CERBER variants in that it arrives via spam emails disguised as a courier delivery service. The email contains a zipped attachment alongside malicious javascript (JS) files.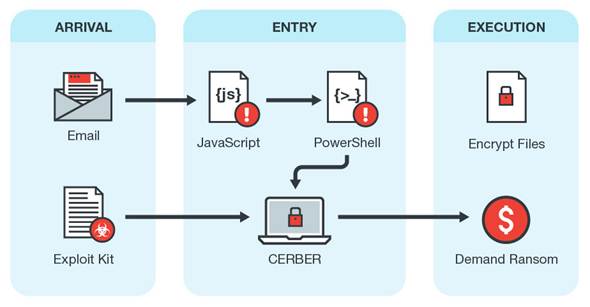
These JS files are designed to perform three functions:
1) Download and execute the ransomware payload
2) Create a scheduled task that will run CERBER 6 after a two minute delay
3) Run and embedded PowerShell script.
Of these three functions, the second one is notable because it will allow CERBER to elude traditional sandbox detection. This variant also continues with the stealth ransomware theme, adding more checks for file extensions that it will avoid encrypting. In particular, CERBER can now utilize Windows firewall rules that block the outbound traffic of all executable binaries of security products installed in the user’s computer, limiting both detection and mitigation capabilities of these applications. This development comes after it was found that CERBER has evolved to evade machine learning. The combination of these features makes the latest CERBER variant a much more stubborn ransomware to deal with.
CradleCore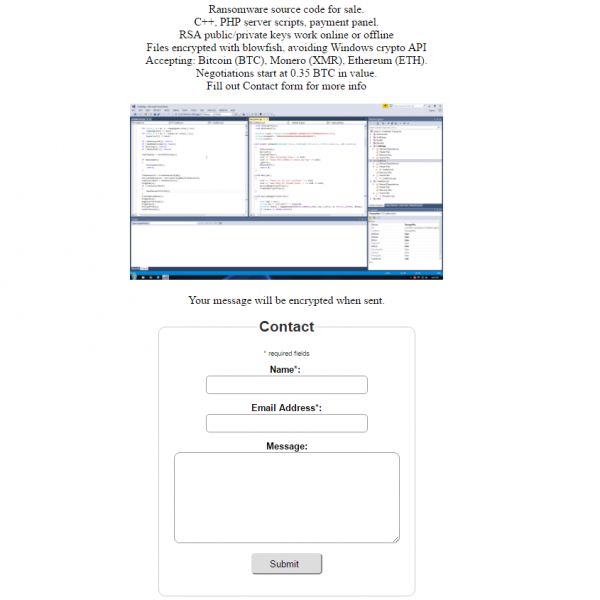
Ransomware-as-a-Service(RaaS) has become a disturbing trend for both users and organizations, as cybercriminals with only perfunctory technical knowledge gain access to dangerous ransomware variants. Most RaaS ransomware are exactly that—services that cyber criminals can use, but do not grant access to the malware’s actual source code. However, a new ransomware kit called CradleCore (Detected by Trend Micro as Ransom_CRADLE.A) changes this model. This malware is being sold as a C++ source code with a relatively comprehensive set of features that include anti-sandbox evasion and offline encryption.
There is little information so far on how CradleCore spreads, but it is reasonable to assume that it propagates via typical ransomware methods such as spam and phishing attacks.
Once the ransomware has been downloaded and executed in a user’s computer, it will display a ransom note with the file name _HOW_TO_UNLOCK_FILES_.html. The note comes with a ransom demand for decryption worth 0.25 bitcoins, or roughly $300. Targeted files are also appended with a .cradle extension.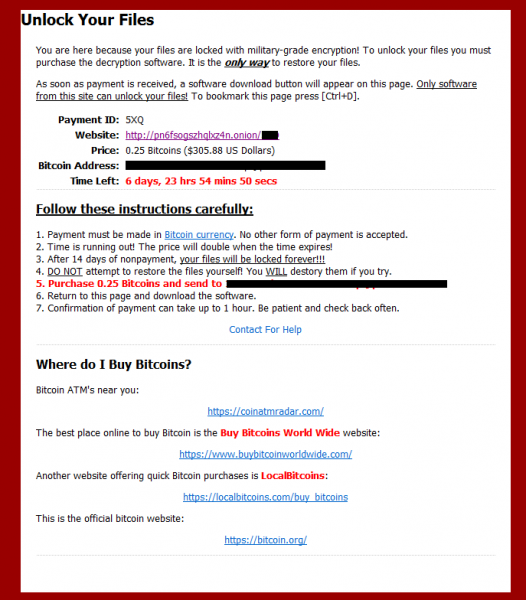
Conclusion
The ransomware found this week demonstrates new features while still relying on typical arrival methods such as spam and phishing. This indicates that the best practices used for identifying and mitigating these types of attacks are still relevant—and are still important measures that both users and organizations should continually practice to defend against these types of threats.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks