Cyber Threats to the Mining Industry
 View research: Cyber Threats to the Mining Industry
View research: Cyber Threats to the Mining Industry
In today’s competitive global market for commodities and manufactured goods, the reliance on natural resources for economic development and fluctuating geopolitical climates have all contributed to making industries targets for cyber espionage campaigns, and—in extreme cases—disruptive and destructive cyber attacks. These cyber espionage campaigns are designed to make sure that interest groups have access to the latest technical knowledge and intelligence so they can maintain competitive advantage and thrive in a market-driven global economy.
The mining industry is under threat from cyber attacks aimed at exploiting its strategic position in global supply chains. Very targeted and highly coordinated, the attacks are launched by a broad set of attacker groups ranging from hacktivists to hostile governments and organized criminals. These groups have learned how to leverage the significant role that mining commodities play in regional and global supply chains and for national economies, and know how to exploit the vulnerabilities that mining companies are exposed to due to heavy reliance on integrated and automated systems.
Cyber Attacks targeting different Industries
News about cyber attacks targeting different industries is becoming the norm, much like daily news stories about data breaches. Advanced persistent threat (APT) campaigns such as BlackEnergy—originally pure industrial espionage campaigns—have been re-purposed to cause physical impact by attacking and damaging industrial assets. BlackEnergy and another APT campaign, Sandworm, were discovered as the likely perpetrators behind outages at two power generation facilities in Ukraine in December 2015. BlackEnergy and KillDisk were discovered in similar attack attempts against a mining company and a large railway operator, also in Ukraine. This shows that BlackEnergy has evolved from an energy sector threat to one that's applicable to organizations across different sectors.
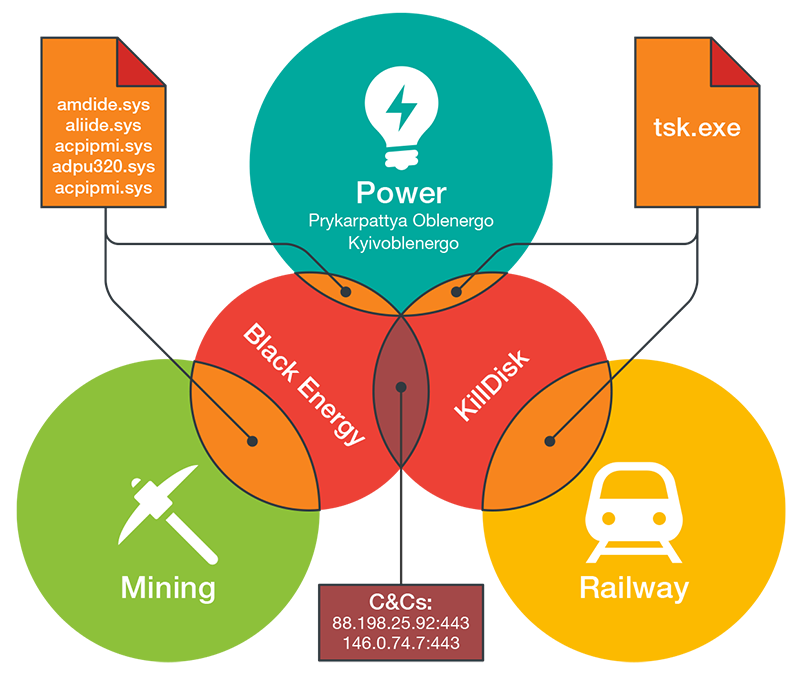
Figure 1: Overlap between sectors, campaigns, malware, and C&C
Why are Industries Vulnerable?
Cyber attacks are not an exclusive IT problem—they have a deep impact on daily business operations such as: operational shutdowns, equipment damage, reputation damage, financial loss, intellectual property loss, competitive advantage loss, health and safety risks, etc. Today’s cybercriminals are not only after money and financial information—they have evolved not only in terms of their technical ability and sophistication but are increasingly aware of the value of stolen sensitive data, how it can be monetized, and how it can influence business dynamics. As an example, one group stole market-sensitive information from 100+ companies, while another group stole pre-release information from financial newswires. In both cases the stolen information was traded for profits in the stock market.
Mining Industry – Prime Goal is Espionage
When we analyze why the mining industry could be a viable and important target, there are three clear factors that explain its relevance.
- Increasing and continued importance of commodities as traded entities on international markets
- Reliance on natural resources for economic development
- The need for countries to benefit from their own mineral deposits
The mining industry is both a geopolitical and an economic target. The threat actors behind foreign cyber espionage campaigns are increasingly interested in learning about governance policies, decisions, and decision-making processes of corporate executives but also in trying to gain a competitive edge by disrupting the advantage of a competitor.
Economic Factors
The mining industry is a commodity-centric global player that is affected by the ups and downs of the market-driven global economy. One of the realities the mining industry has to cope with is that commodity prices are subject to significant short-term volatility as well as longer-term cycles. A contraction in manufacturing will result in reduced demands for raw materials and, in turn, slowdown for the mining industry.
Falling demands and drop in commodity prices have caused economic slowdown in countries that heavily rely on the export of natural resources such as Australia and Canada. On the flipside, in countries like the United States that are less dependent on the export of natural resources, the drop in commodity prices has had a comparatively smaller economic impact. This dimension highlights how vulnerable the economies of some countries are to any disruption affecting a key contributor of the economy.
Theft of Pricing Information
Prices for metals are determined by the weight of a standard unit of refined product. Reference prices for industrial metals or minerals may not be directly applicable to the final product of the mines. Mines will sell their products at different refined levels because of production constraints, transportation capacity, or to meet customer needs. There are two critical dimensions to pricing: transportability (ability to move the mined minerals) and homogeneity (degree of standardization), which ultimately determines the negotiated price between the buyer and seller.
Having insider information about a mine’s pricing data can help a competitor hijack a sales deal by outbidding the competition, or a buyer negotiate a better purchase price. Customer information is another prime target for data theft. Competitors can use the stolen customer information to hijack future sales. This is the type of critical information that threat actors are after.
Hacktivism
Environmentally-conscious activists who are protesting the effects of mining on the environment and wildlife habitats take it upon themselves to retaliate by inflicting damage to the mining companies. Cyber attacks offer these activist groups a new way to disrupt mining operations.
In the new research paper “Cyber Threats to the Mining Industry” Trend Micro examines modern mining industry practices and processes, and identifies vulnerable gaps that threat actors might be able to exploit. The reasoning and motivations of a variety of threat actors are also analyzed. This paper does not look at specific APT campaigns, but gives a general view of the weaknesses existing in a sector that doesn’t seem the most intuitive target at first glance.
Visit the Threat Intelligence Center for more on ICS and SCADA systems and industrial cyber security.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks