Blackhat SEO Attacks Use Fake YouTube pages and Flash Installers
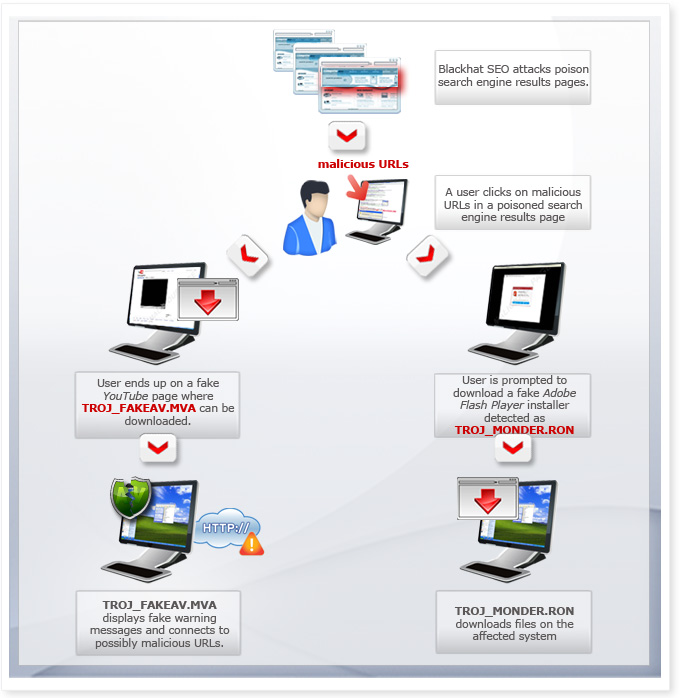
How do users get this Web threat?
Users searching for information via search engines unwittingly fall prey for a new Blackhat SEO attack. Query results for strings such as the video of reality TV celebrity Teresa Guidice, British actress Holly Davidson, and the BP oil spill were found to initially lead to YouTube-like pages before displaying the all-too-familiar fake malware infection warnings. Search results for the string "Mel Gibson tapes" were found redirecting not to pages with fake malware infection warnings, but to a prompt to download a fake Flash Player installer.
What happens once the threat gets inside computers?
User systems infected with TROJ_FAKEAV.MVA see fake warning messages informing them that their system has been infected. The bogus AV software then prompts the user to purchase the full version of the program to remove all detected malware. This routine risks the exposure of the user’s account information, which may then lead to unauthorized use of the stolen data.
Meanwhile, user systems infected with TROJ_MONDER.RON may also see fake security messages about malware detections, warnings, and system tray notifications. The Trojan also downloads and executes malicious files on the affected system.
How are users affected by this threat?
Users looking for information online via search engines inadvertently become victims of a typical FAKEAV attack. By using scareware tactics to trick users into providing their credit card information, which cybercriminals could use to their advantage.
What is the driving force for this threat?
FAKEAV malware are primarily designed to reap profits for cybercriminals. It continues to be a lucrative business which has already resulted to millions of dollars in losses.
What is different in this attack?
This particular attack leverages two of the top Internet activities that users do on a daily basis - using search engines and watching videos - by using blackhat SEO and fake YouTube pages. In a separate infection routine, it also utilizes a bogus Flash Player installer designed to trick users into downloading the installing the malware into their system.
Furthermore, the cybercriminals behind this attack not only used a convincing interface for the fake Adobe installer, they also utilized a URL that strongly suggested that it is an Adobe-related site.
How do affected users remove this threat?
To remove TROJ_FAKEAV.MVA and TROJ_MONDER.RON from their systems, users may use the Trend Micro manual removal instructions.
Are Trend Micro users protected from this threat?
Yes. Solutions supported by the Trend Micro™ Smart Protection Network™ can detect and prevent the execution of the malicious files detected as TROJ_FAKEAV.MVA and TROJ_MONDER.RON via file reputation technology.
What can users do to prevent this threat from entering computers?
Users are highly advised to be wary when searching for information via search engines. With the continued proliferation of blackhat SEO attacks, it would be wise to check website URLs before clicking on them. It would also be a good idea to directly access websites on your browsers instead.
Non-Trend Micro users can also stay protected via HouseCall, a free tool that identifies and removes all kinds of viruses, Trojans, worms, unwanted browser plug-ins, and other malware from affected systems.