ELF_SHISHIGA.A
Backdoor.Linux.Luabot!c(AegisLab)
Linux


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This malware was discovered on early May 2017 and is found to be capable of brute-forcing Telnet and SSH logins. Users affected by this malware may find the security of their systems compromised and at risk of information theft.
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan drops the following files:
- $HOME/.local/check
- $HOME/.local/nodes.cfg
- $HOME/.local/script.bt
- $HOME/.local/server.bt
- $HOME/.local/ssh.txt
- $HOME/.local/syslog
- $HOME/.local/syslog.pid
- $HOME/.local/telnet.txt
- $HOME/.local/update.bt
- $HOME/.local/{armv4l,i686,mips,mipsel,powerpc}.lm
- $HOME/.local/{armv4l,i686,mips,mipsel}.{dl,dm}
- /bin/syslogd
- /etc/cron.hourly/syslogd
- /etc/init.d/syslogd
- /etc/rc2.d/S04syslogd
- /etc/rc3.d/S04syslogd
- /etc/rc4.d/S04syslogd
- /etc/rc5.d/S04syslogd
- /tmp/.local/*
- /tmp/drop
- /tmp/srv
Information Theft
This Trojan gathers the following data:
- OS version
- Mac Address
- Ip Address
- User Name
- Password
- Malware Version
Other Details
This Trojan connects to the following URL(s) to get the affected system's IP address:
- http://myip.ru
It connects to the following website to send and receive information:
- {BLOCKED}.{BLOCKED}.137.35:8888
It does the following:
- It uses the following list of user names and passwords to bruteforce Telnet and SSH logins:
- acer acer
- adm
- adm adm
- admin
- admin admin
- local accounts=
- pi pi
- root
- root 1
- root 111111
- root 12
- root 123
- root 123123
- root 1234
- root 12346
- root 123467
- root 1234678
- root 12346789
- root 123467890
- root 1q2w3e
- root 1q2w3e4r
- root 1qaz
- root 1qaz2wsx
- root abc123
- root asdfgh
- root oracle
- root p@ssw0rd
- root pass
- root pass123
- root passw0rd
- root passw0rds
- root password
- root password123
- root password123456
- root qwe123
- root qwerty
- root root
- root roottoor
- root test
- root toor
- security security
- ubnt ubnt
- user
- user user
NOTES:
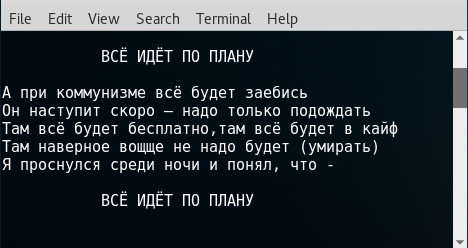
It displays the following graphics:
SOLUTION
Scan your computer with your Trend Micro product to delete files detected as ELF_SHISHIGA.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.



