Asprox Botnet Reemerges in the Form of KULUOZ
Botnets are one of the most effective means for cybercriminals to distribute malware and generate profit from unsuspecting users. The Asprox botnet, which first emerged in the threat landscape in 2007, has resurfaced with a new and improved modular framework in the form of KULUOZ malware.
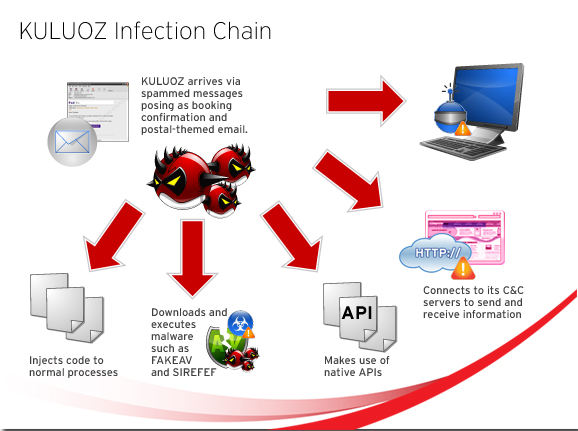
Asprox sends out spammed messages using a wide array of social engineering lures (e.g. booking confirmations, postal-themed spam, etc.) to compromise systems, and consequently, increase the size of this botnet. Once systems are infected by KULUOZ, remote attackers can issue commands like downloading of pay-per-install malware (such as FAKEAV) to gain profit.
How do KULUOZ variants enter systems?
KULUOZ arrives as attachments to spammed messages disguised as notifications from postal companies as well as airline booking confirmations. Some of the known companies it spoofs are U.S. Postal Service (USPS), FedEx, DHL, Delta, and American Airlines, IRS, and PayPal. To lure users into thinking that it is legitimate, KULUOZ often comes in the guise of files like .PDF and .DOC.

Figure 1. Sample spammed message
What does KULUOZ do to an infected system?
When executed on the system, KULUOZ variants drop a .TXT file so that users won’t suspect malicious activity in the background. It also injects its code to certain processes and makes use of native APIs so that it will be difficult to debug and remove from the system.
In addition, KULUOZ downloads other malware like FAKEAV, thus further compromising system security. FAKEAV typically displays fake security alerts to trick users into purchasing fake antivirus software. Once FAKEAV is installed on the system, it connects to its affiliate network to download SIREFEF/ZACCESS and TSPY_PAPRAS variants. SIREFEF is a malware known for its rootkit capabilities, while TSPY_PAPRAS sniffs for passwords in network packets and sends it to a remote site. KULUOZ malware can potentially download any malware since it is built for this function. However, during our analysis, we only observed that KULUOZ downloads FAKEAV, SIREFEF, and TSPY_PAPRAS variants.
On the other hand, BKDR_KULUOZ variants specifically connect to its command-and-control (C&C) servers to send and receive information.
Why is KULUOZ notable?
KULUOZ is notable because it is incorporated into Asprox’s functionalities which keep the botnet operational. KULUOZ is the downloader of the botnet’s other modules, which led to further botnet improvements. Our 2013 predictions mentioned that cybercriminals will improve existing tools and malware instead of creating new ones. We are seeing this prediction come true in the case of Asprox.
Once users download and execute KULUOZ, it connects to its C&C servers to download modules, one of which is the original Asprox module. The said Asprox module is responsible for sending out spammed messages via SMTP. Moreover, this malware is capable of updating itself to prevent detection and removal from the infected systems.
Why should users be concerned with this threat?
Once systems are infected with KULUOZ variants, they become vulnerable to other attacks and can be used to perform actions making Asprox operational. Compromised systems become part of the botnet and cybercriminals can gain profit by commanding these systems to download pay-per-install malware.
KULUOZ also opens the systems to a plethora of threats that can push other malware, thus further compromising system security. Lastly, systems infected with KULUOZ can be used to send out spammed messages, which can further spread this malware.
What can users do to prevent this threat from entering computers?
Since email is the entry point used by KULUOZ variants, users are highly advisable to examine email messages and their attachments even if these came from seemingly known sources. It is also recommended that users install security software that has Web, email, and file reputation technologies that can block all related URLs as well as detect KULUOZ variants.
Are Trend Micro users protected from this threat?
Yes. However, spam will always be a malware gateway to proliferate malicious activities. As such, email reputation technology can help prevent systems from being infected by malware and becoming part of a botnet similar to Asprox. Web reputation technology, on one hand, can block all URLs where Asprox connects to and file reputation technology can detect all KULUOZ variants thus preventing malware infection.
Expert's Insights:
“Spam botnets remain a crucial component of the malware ecosystem and that cybercriminals are always looking for new ways to adopt in response to defenses.” – Nart Villeneuve, senior threat researcher
“Asprox may have tweaked and improved its framework, but its social engineering lures are not very far off from the ones used 5 years ago. And the number of victims who has fallen for these spam mails proves that these old tricks are still very much effective today.” – Jessa Dela Torre, senior threat researcher
“KULUOZ is still one of the most active malware in the wild. Since it has the capability to update itself on affected systems, thus it is no surprise that its routines and payloads will evolve and be more dangerous.” – Romeo Dela Cruz, threat response engineer