Blackhole Exploit Kit Spam Runs: A Threat Vortex?
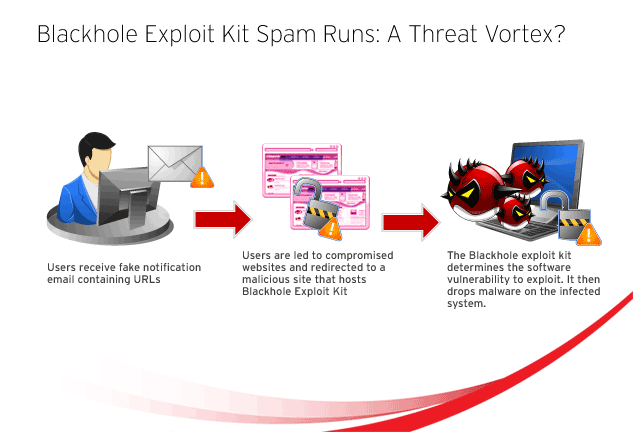
One of the prevalent exploit kits in the cybercrime today is Blackhole Exploit Kit (BHEK), which used spammed message that looks exactly like the legitimate email and leverages relevant and timely topics. This is done to lure users into clicking a URL that points to sites hosting Blackhole Exploit Kit. Over the course of our monitoring and investigation, we saw several changes such as how cybercriminals use Blackhole Expoit Kit and the many lures it has utilized like bogus notifications from social networking website, courier and bank notices, and cable email update, among others.
We noted several related spam campaigns that leveraged newsworthy items such as the birth of the royal baby and the movie, Ender’s Game. It also posed as bogus notifications from Facebook and eBay as a social engineering tactic.
Based on our investigation, the spam volume related to the BHEK spam campaign reached up to 0.8% of the collected spammed messages in mid-2013. The top countries where the spam run originated are US, India, and Kazakhstan. These incidents show that attacks that use exploit kits are an ongoing trend in today’s threat landscape. The popularity of exploit kits particularly the Blackhole Exploit Kit has indeed become a cybercriminal’s favorite.
How do users encounter this threat?
Blackhole exploits kits are hosted on specific malicious sites. The cybercriminals behind the attacks that spread the exploit kit send out spammed messages containing links. The spammed messages often use social engineering techniques to lure recipients into clicking the links. The messages are typically disguised as spoofed notifications of well-known e-commerce and social networking sites. Users are then redirected to compromised sites, and then finally, sites hosting the Blackhole Exploit Kit.
What happens when users click the links in the spammed messages?
Users who are tricked into clicking the links are led to a compromised / abused website that contains a malicious JavaScript. This script uses an embedded iframe that points to strictly malicious site that uses the Blackhole Exploit Kit. Once the iframe loads, another obfuscated script loads from the Blackhole Exploit Kit site. This code is responsible for searching for vulnerable software to exploit. The Blackhole Exploit Kit can target vulnerabilities in several software including third-party applications like Adobe Acrobat, Flash Player, Java and Windows.
Once a successful exploit has taken place, the Blackhole Exploit Kit initiates the malware installation. Based on our investigation, this type of attack spreads information-stealing malware like ZeuS/ZBOT and more recently, TSPY_FAREIT variants.
What happens when user systems become infected with TSPY_FAREIT variants?
TSPY_FAREIT variants specifically TSPY_FAREIT.AFM, which is used in the latest BHEK spam run, steals FTP client account information. It also collects information such as stored email credentials and login details from browsers. Furthermore, it uses a predetermined set of passwords in order to brute force Windows login. As such, users are at risk of having their personal information and credentials related to their bank/financial accounts stolen. This, in turn may be used to launch other attacks or stolen information can be sold in the underground cybercrime.
The people behind these attacks use social engineering techniques to trick users into performing particular actions, like clicking links to lead to the Blackhole exploit kit. One of their tactics is to leverage relevant and hot topics or news items and use popular brand names.
The attacks are also effective because the phishing emails are made to look exactly like authentic email notices from legitimate websites. Not only is this an effective bait, it is also a technique to prevent traditional email blocking methods. As Trend Micro product manager Sandra Cheng pointed out, “The format and wording of these email were made to look legitimate. This is why these messages are difficult to detect using traditional methods.”
This attack also capitalizes on exploiting software vulnerabilities. Note however, that most of these exploits take advantage of old and known vulnerabilities. This just goes to show that reliable exploits have a longer shelf life and attackers can still use it for future attacks.
What are the different attacks related to the Blackhole exploits?
During the course of our investigation, we encountered several sample messages that spoofed email from different websites. Below are some of the recent noteworthy Blackhole exploit-related attacks.
|
Infection vector |
Social engineering technique |
Exploit and software vulnerability |
Payload |
| Spoofed email notification | Poses as an official announcement from Scribd Live of the birth of Prince William and Kate Middleton's son | Java vulnerabilities | Drops TROJ_MEDFOS.JET that downloads malicious files |
| Spoofed email notification | Guises itself as an email coming from CNN regarding the sci-fi film Ender's Game | Java vulnerabilities | Drops TROJ_MEDFOS.JET that downloads malicious files |
| Spoofed email notification | Poses as a notification from Facebook and eBay | Java vulnerabilities | Leads to the download of TSPY_FAREIT.AFM, which steals stored email and browser credentials |
| Spoofed email notification | Poses as a phone billing notice from Verizon Wireless | Adobe | Leads to TSPY_ZBOT.JBR which gathers sensitive information from infected systems |
| Spoofed email notification | Poses as notice from Citibank online account | Varies | Leads to the download of a Zeu/ZBOT malware |
| Spoofed email notification | Password change notification from LinkedIn | Varies | Leads to TSPY_ZBOT.NT. Modifies Internet Explorer Zone Settings |
| Spoofed email notification | Job opening posting from CareerBuilder | Varies | Leads to TSPY_ZBOT.IZI. Drops files onto the system, steals information |
| Spoofed email notification | Friend notification request from Facebook | CVE-2010-0842 - Oracle Java SE and Java for Business 'MixerSequencer' Remote Code Execution Vulnerability CVE-2010-0840 - Unspecified vulnerability in the Java Runtime Environment component in Oracle Java SE and Java for Business 6 Update 18, 5.0 Update 23, and 1.4.2_25 CVE-2011-3544- Unspecified vulnerability in the Java Runtime Environment CVE-2012-0507 | TSPY_ZBOT.PEJ Steals information, drops files |
| Spoofed email notification | Flight details from US Airways | JAVA_EXPLCVE.RT CVE-2012-0507 | TROJ_PDFJSC.ADR. Connects to malicious sites to download files TSPY_ZBOT.AADR Connects to several sites |
| Spoofed Email notification | Payment notice from PayPal | JAVA_BLACOLE.RCC CVE-2012-0507 | Drops or downloads other files onto the system. |
| Spoofed email notification | Online account changes notice from American Express Bank | JAVA_BLACOLE.RCC CVE-2012-0507 | Drops or downloads other files onto the system. |
| Spoofed email notification | Notice from Better Business Bureau and LinkedIn | JS_BLACOLE.IC CVE-2010-0188 CVE-2010-1885 | WORM_CRIDEX.IC Connects to malicious sites to download other files; generates random domains |
How does the Blackhole Exploit Kit affect users?
The exploit kit downloads or drops another malware onto the system. The typical downloaded/dropped malware are ZeuS variants, which are notorious for information theft.
Are there new developments for Blackhole Exploit Kit?
We have been monitoring BHEK-related spam runs since 2011. It has undergone several developments and continuous improvement, which make it a prominent exploit kits. Here’s a rundown of the modifications that this exploit kit underwent:
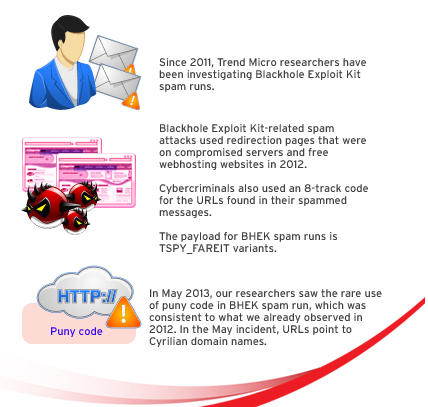
Currently, the latest spam runs related to Blackhole Exploit Kit downloads another malware (TSPY_FAREIT variants). However, there are no new developments with regards to how it was being used by cybercriminals in the wild.
What can I do to prevent this threat?
Users can prevent these threats through these effective steps:
- Patch regularly.The Blackhole exploit kit frequently utilizes exploits that targets old and unpatched versions of software. This means that exploits are still effective since a lot of users keep unpatched software. Vendors like Microsoft, Adobe, and Oracle regularly release security updates to address exploits on their software.Microsoft announces their security bulletins and updates via Patch Tuesday, which happens every second Tuesday of the month. Though it may be inconvenient at times, regularly patching your software is an important step in preventing similar threats.
- Disable JavaScript in your browser. Blackhole exploit kit pages are known to use JavaScript. It might be a good idea to disable JavaScript in your browser. Allow it only for your trusted sites, if necessary.
- Beware of social engineering attacks. Majority of these attacks used social engineering tricks to lure users into clicking the malicious links. Simple common sense like double-checking the validity of an email and being skeptical of email should keep you out of harm’s way.
- Think before you click. Treat any link in an email message as potentially dangerous. Be sure to check where the URLs point to. Also, using a free URL verification system like Trend Micro Site Safety Center can help you verify a possibly malicious link.
Are Trend Micro users protected from this threat?
Trend Micro protects users from this threat via Trend Micro™ Smart Protection Network™. The Email Reputation Services blocks the related spam messages before they even arrive at users’ inboxes. Web Reputation Services prevents users from accessing the related malicious domains, while the file reputation services detects and deletes the related malware. Trend Micro™ Deep Security™ also provides protection from the exploits that abuse those software vulnerabilities related to this attack.
FROM THE FIELD: EXPERT INSIGHTS
"Phishing email that use names of various organizations spread via email to targets predominantly in the United States. The content of these phishing messages were practically indistinguishable from legitimate messages." – Jon Oliver, software architecture director
"Based on our investigation, the variables in the attacks e.g. the links in the spam, are constantly changing, making it difficult to detect and take down the malicious links. Also, smaller botnets, which are running less traffic, are being used to circumvent detection." – Sandra Cheng, product manager