Ransomware Recap: The Ongoing Development of Hidden Tear Variants
 Ransomware based on open source code, specifically variants based on Hidden Tear, continues to proliferate. When it was first released, the open source code allowed anyone, even inexperienced developers, to extort victims with ransomware. The first few Hidden Tear-based variants, and even similar open source ransomware like EDA2, didn’t stray far from the originals. But it comes as no surprise that ransomware authors keep building on the released code and creating improved variants.
Ransomware based on open source code, specifically variants based on Hidden Tear, continues to proliferate. When it was first released, the open source code allowed anyone, even inexperienced developers, to extort victims with ransomware. The first few Hidden Tear-based variants, and even similar open source ransomware like EDA2, didn’t stray far from the originals. But it comes as no surprise that ransomware authors keep building on the released code and creating improved variants.
One example is May ransomware (detected by Trend Micro as RANSOM_HIDDENTEARMAY.A), a recently detected variant of Hidden Tear that uses AES256 and RSA4096 encryption. The encryption is actually based on Hidden Tear source code, but the key generation is different. May first selects a random file in C:\Program Files\Internet Explorer. It then reads and shuffles the first 128 bytes of that file, and then it uses those shuffled bytes as the password the AES key is derived from.
To keep the victim’s system running and make it easier for them to pay the ransom, May avoids encrypting files in directories that contain the following strings:
- Program Files
- Windows
- Program Data
MoWare ransomware (detected by Trend Micro as RANSOM_HIDDENTEARMOWARE) is another Hidden Tear variant that deviates from the original source code. To start with, it has a different encryption algorithm from Hidden Tear, using XOR encryption instead of AES. The ransomware encrypts files in the Desktop, Personal, MyMusic, MyPictures and Cookies folder directory. It also checks for an internet connection and disables Registry tools, Task Manager, and CMD.
The ransom note is also quite sophisticated, even “helping out” its victims with a drop down menu for Frequently Asked Questions:
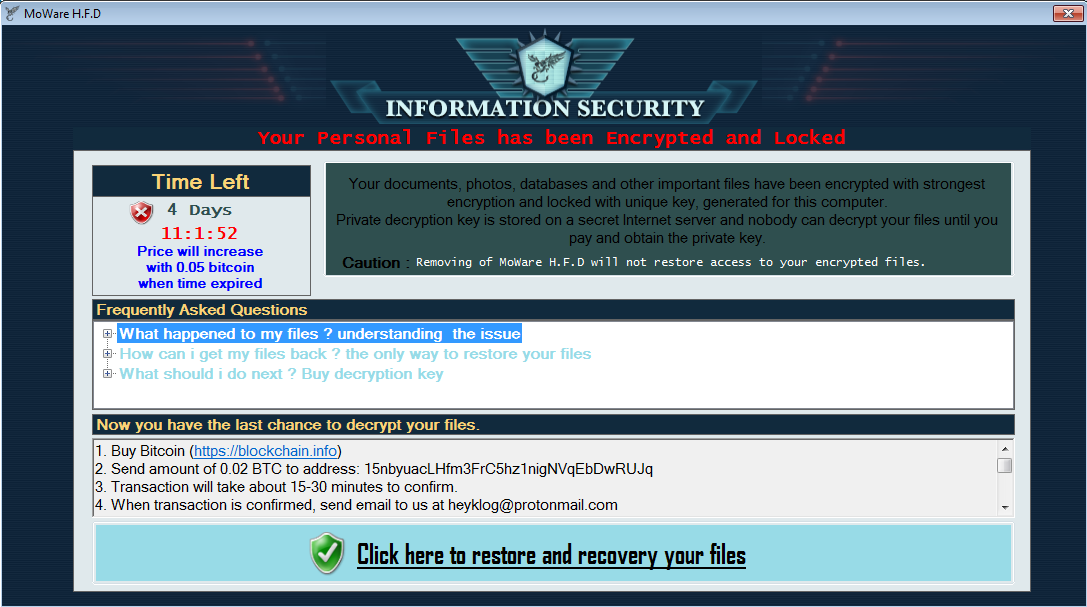 Figure 1. MoWare ransom note
Figure 1. MoWare ransom note
Another Hidden Tear variant called Franzi ransomware (detected by Trend Micro as RANSOM_HIDDENTEARFRANZI.A) scans for Microsoft debugging software. Specifically, it checks for: Crypto Obfuscator, OLLYDBG, IsDebuggerPresent, and CheckRemoteDebuggerPresent. If it detects one of these, it does not continue with its main routine.
New ransomware focuses on graphics and payment plans
We noted that TeslaCrypt closed up shop in May of 2016, even giving away its master key for free. With it gone, a spot opened up for other Tesla-themed ransomware. Taking over the role is one simply called Tesla (detected by Trend Micro as RANSOM_CRYPTEAR.SM). Despite the name, Tesla has a number of distinct differences from the older TeslaCrypt, including a more sophisticated interface and ransom note. It is also written in Microsoft Intermediate Language (MSIL), whereas TeslaCrypt used C++.
 Figure 2. Tesla ransomware icon
Figure 2. Tesla ransomware icon
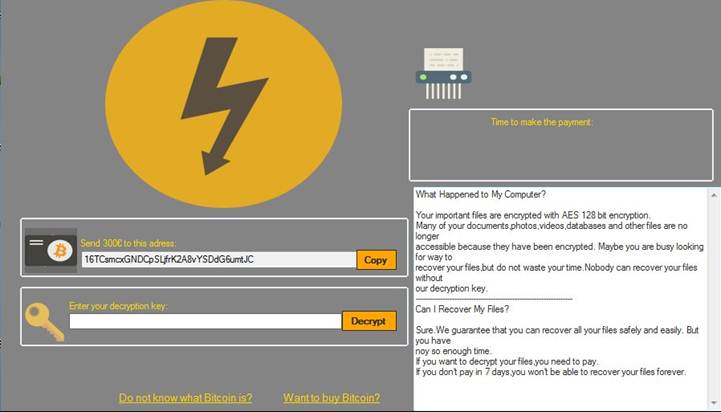
Figure 3. Tesla ransom note
Widia (detected by Trend Micro as RANSOM_WIDIALOCKER.A) is a screenlocker ransomware that is currently in development, possibly originating from Romania. One feature of Widia is that it asks the user to pay the ransom via credit card, an interesting departure from the typical Bitcoin payment. The payment method is an interesting choice for the developers; while credit cards are much more commonly used—making it easier for victims to pay ransom—credit card transactions are also easily traced and don’t guarantee the same level of anonymity as Bitcoin.
Meanwhile, BlueHowl (detected by Trend Micro as RANSOM_BLUEHOWL) is a new screenlocker that has a voiceover and an embedded video of The Final Countdown—both presumably to intimidate victims. For payment, they have the usual Bitcoin option as well as a QR code to facilitate easier payments.
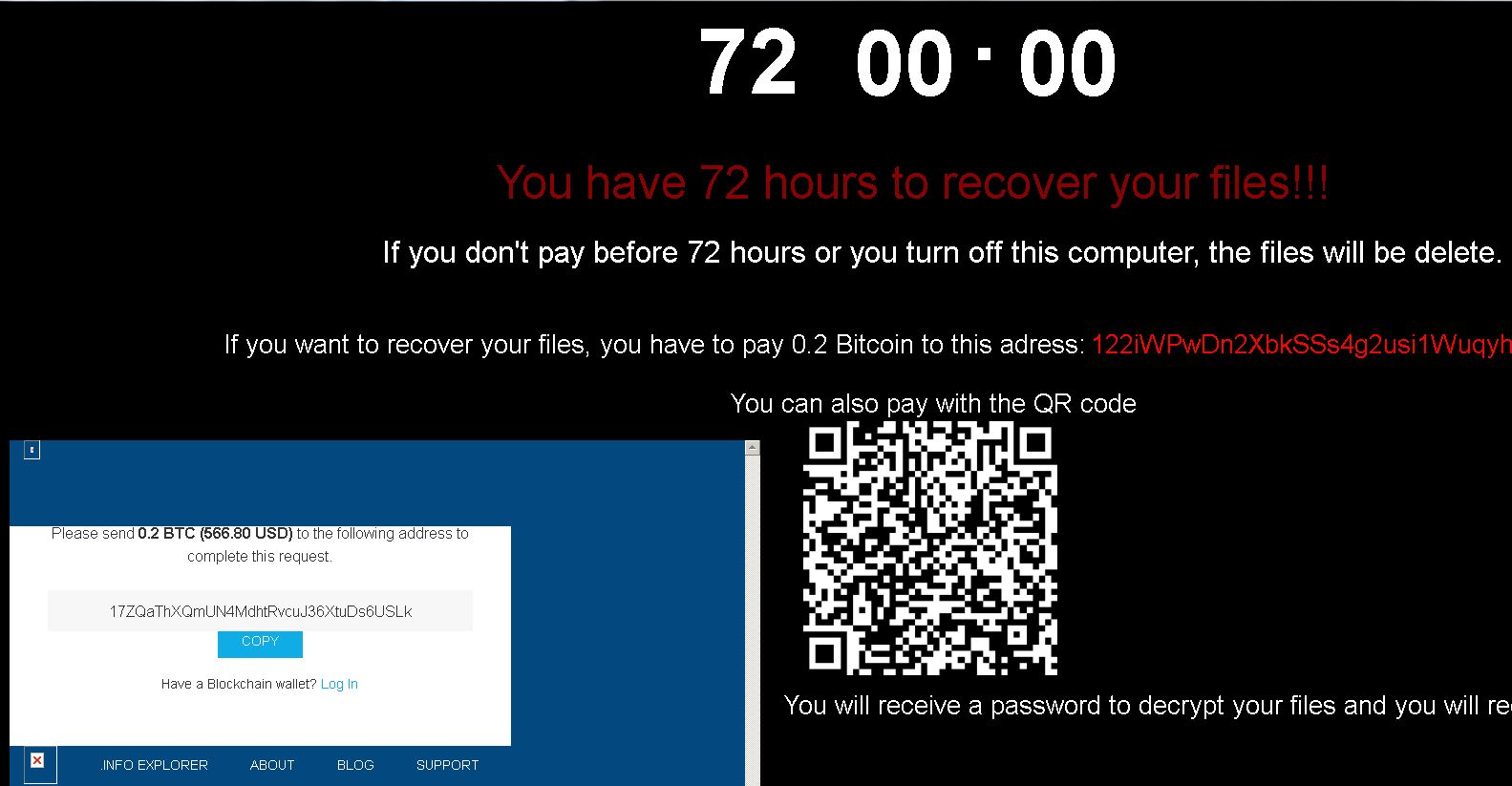
Figure 4. BlueHowl uses a QR code for payment
Ransomware creators are searching for new ways to extract money from their victims, either by creating better interfaces or providing widely used payment options. As ransomware continues to spread and evolve, users have to stay vigilant and make security a priority.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks