Mobile Payment Systems: How Apple Pay Works
First introduced in 2014, Apple Pay is a payment app exclusive to certain iterations of Apple’s mobile device ecosystem, namely the iPhone 6 (and later), iPad 2 (and later), iPad Mini 3 (and later) and the Apple Watch. It involves the use of a separate Secure Element (a chip akin to chip-and-pin credit cards) to store the user’s credit card information in the device—which is separate from the main processor where apps execute. It also works with the built-in Touch ID Fingerprint Reader feature, at the time one of the latest features to be designed into that particular generation of Apple devices.
How does it work?
Apple Pay uses two methods: a cryptogram, similar to EMV transactions, and tokenization. When the user first inputs their credit card into the Apple Pay app, the credit card brands (Visa, MasterCard, or American Express) will send a token and a cryptogram to the Apple device. The token is a 16-digit number that replaces the actual credit card number. The token and the cryptogram is then stored in the Secure Element chip, and is sent to the card brand’s network for verification each time the user authorizes a transaction (by way of the fingerprint scanner, the only authorizing element needed to do so).
The card brand network receives both elements, decrypts the cryptogram and then checks it for authenticity. If the cryptogram is found to be authentic, the network then passes the token to the issuer bank of the credit card. The issuer decrypts the token, and after a final check for authenticity, completes the transaction. Some transactions in this line also require the user to input their postal code, for added security and verification.
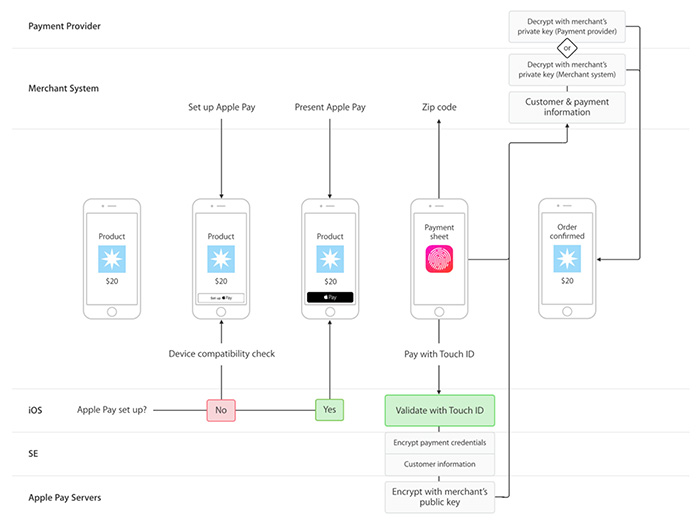 Apple Pay payment flow (Source: developer.apple.com)
Apple Pay payment flow (Source: developer.apple.com)
What are its advantages?
Apple Pay itself can be considered very secure due to its use of certain features. For one, the fact that iOS is closed source. Unlike Google's open source Android OS, it's unlikely for a malicious version of the app to be released into its ecosystem. The use of fingerprints for authorizing transactions also prevents fraud by phishing, as any potential attacker needs to have access to the device and the user’s fingerprints in order to carry out any scheme. Of course, jailbroken Apple devices, which allow unsigned or unverified apps, are vulnerable to malware that can intercept Apple Pay transactions.
What are its disadvantages?
One potential downside exists for Apple Watch users. Its version of Apple Pay uses PIN authorization, due to the device lacking a fingerprint scanning feature, which can theoretically make it vulnerable to transaction fraud. On the other hand, an Apple Watch user can make any amount of transactions with Apple Pay without needing to re-enter their PIN—as long as they don't take it off, as this de-authorizes the account. So a potential attacker would have to phish the user’s PIN number and steal the device in order to perform any type of fraud with it, which is highly improbably even with the most careless of users.
[MORE: Next-Gen Payment Processing Technologies: What They Are, and How They Work]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One