TROJ_POPUREB.SMB
Trojan:Win32/Popureb.C (Microsoft)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware uses complex routines to hide in the infected system's master boot record (MBR) in order to evade detection.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
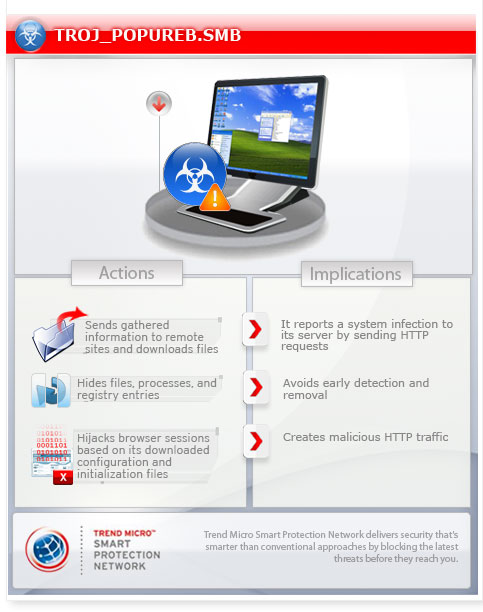
This Trojan connects to certain websites (malware domains) to send information and download files. It downloads a configuration file from a certain site. It then saves the downloaded configuration file. It reports a system infection to its server by sending HTTP requests. It then expects the server to reply with the string "OK".
It downloads an initialization file from a certain site. It saves the downloaded file as %Windows%\vc.ini. The contents of file are then parsed by the malware to aid in its malicious routines.
It searches for a component file named Desktop\*.url and then parses it also to aid in its malicious routines.
It checks for the presence of a browser process in memory. It if finds one, it embeds a thread to it and connects to a certain website.
It hijacks browser sessions based on its downloaded configuration and initialization files in order to create malicious HTTP traffic. Malicious traffic created may involve downloading other possibly malicious file(s), connecting to sites, and displaying online advertisements. It is also capable of affecting certain browsers.
This Trojan may be dropped by other malware.
It also has rootkit capabilities, which enables it to hide its processes and files from the user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be dropped by the following malware:
- TROJ_POPUREB.SMA
Installation
This Trojan drops the following non-malicious files:
- %System Root%\Documents and Settings\All Users\Documents\My Videos\PulgFile.log - config file
- %System Root%\PulgFile.log - config file
- %System Root%\Documents and Settings\All Users\Documents\My Videos\Desktop.ini - non-malicious component
- %User Profile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Internet Explorer.IE - non-malicious component
- %Desktop%\Internet Explorer.IE - non-malicious component
(Note: %System Root% is the root folder, which is usually C:\. It is also where the operating system is located.. %User Profile% is the current user's profile folder, which is usually C:\Windows\Profiles\{user name} on Windows 98 and ME, C:\WINNT\Profiles\{user name} on Windows NT, and C:\Documents and Settings\{user name} on Windows 2000, XP, and Server 2003.. %Desktop% is the current user's desktop, which is usually C:\Windows\Profiles\{user name}\Desktop on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Desktop on Windows NT, and C:\Documents and Settings\{User Name}\Desktop on Windows 2000, XP, and Server 2003.)
It drops the following copies of itself into the affected system:
- %System Root%\Documents and Settings\All Users\Documents\My Videos\Van{3 random characters}.tmp
- %System Root%\Van{3 random characters}.tmp
(Note: %System Root% is the root folder, which is usually C:\. It is also where the operating system is located.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- IE_2011_Mutex
Other System Modifications
This Trojan adds the following registry entries:
HKEY_CLASSES_ROOT\.IE
@ = "IE"
HKEY_CLASSES_ROOT\.JE
@ = "JE"
HKEY_CLASSES_ROOT\IE
@ = "{characters}"
HKEY_CLASSES_ROOT\IE\DefaultIcon
@ = "shdoclc.dll,0"
HKEY_CLASSES_ROOT\JE
@ "¿ì½Ý·½Ê½" = "{characters}"
HKEY_CLASSES_ROOT\JE\shell\
open\command
@ = "C:\Program Files\Internet Explorer\IEXPLORE.EXE "
HKEY_CLASSES_ROOT\IE\shell\
open\command
@ = "%Program Files%\Internet Explorer\IEXPLORE.EXE http://{BLOCKED}3.{BLOCKED}1.info"
HKEY_CLASSES_ROOT\JE\shell\
open\command
@ = "%Program Files%\Internet Explorer\IEXPLORE.EXE "
HKEY_CLASSES_ROOT\CLSID\{2559a1f4-21d7-11d4-bdaf-00c04f60b9f0}\
shell\OpenHomePage
@ = "{characters}"
HKEY_CLASSES_ROOT\CLSID\{2559a1f4-21d7-11d4-bdaf-00c04f60b9f0}\
shell\OpenHomePage\Command
@ = "%Program Files%\Internet Explorer\IEXPLORE.EXE http://{BLOCKED}3.{BLOCKED}1.info"
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Main
Default_Page_URL = "http://{BLOCKED}3.{BLOCKED}21.info"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\ClassicStartMenu
{871C5380-42A0-1069-A2EA-08002B30309D} = "2"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\ClassicStartMenu
{871C5380-42A0-1069-A2EA-08002B30309D}.default = "1"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\NewStartPanel
{871C5380-42A0-1069-A2EA-08002B30309D} = "2"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\ClassicStartMenu
{871C5380-42A0-1069-A2EA-08002B30309D} = "2"
It modifies the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Main
Start Page = "http://{BLOCKED}3.{BLOCKED}21.info"
(Note: The default value data of the said registry entry is {default page}.)
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Main
Default_Page_URL = "http://{BLOCKED}3.{BLOCKED}21.info "
(Note: The default value data of the said registry entry is {default page}.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
Hidden = "2"
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
HideFileExt = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\ClassicStartMenu
{871C5380-42A0-1069-A2EA-08002B30309D}.default = "1"
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
HideDesktopIcons\NewStartPanel
{871C5380-42A0-1069-A2EA-08002B30309D} = "2"
(Note: The default value data of the said registry entry is 1.)
It deletes the following registry keys:
HKEY_CLASSES_ROOT\CLSID\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
HKEY_CURRENT_USER\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
Desktop\NameSpace\{C42EB5A1-0EED-E549-91B0-153485866016}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
CLSID\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
CLSID\{20000000-0000-0000-0000-000000000000}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc850}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
Desktop\NameSpace\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer\
Desktop\NameSpace\{20000000-0000-0000-0000-000000000000}
Rootkit Capabilities
This Trojan also has rootkit capabilities, which enables it to hide its processes and files from the user.
NOTES:
It connects to any of the following sites (malware domain) to send information and download files:
- {BLOCKED}8.info
- {BLOCKED}8.info
It downloads a configuration file from the following site:
- http://{malware domain}/2/logo.gif
It then saves the downloaded configuration file as follows:
- %System Root%\Documents and Settings\All Users\Documents\My Videos\PulgConfig.log
It reports system infection to its server by sending the following HTTP requests:
- http://{malware domain}:83/sms/do.php?userid={user id}&time={date and time}&msg={parameter}&ver=&os={operating system}&fy=0&pauid={parameter}&checkId={parameter}
- http://{malware domain}:83/sms/count.php?userid={user id}
It then expects the server to reply with the string "OK".
It downloads an initialization file in the following site:
- http://{malware domain}:83/2/pop.gif
It saves the downloaded file as %Windows%\vc.ini. The contents of file are then parsed by the malware to aid in its malicious routines.
It searches for a component file named Desktop\*.url and then parses it also to aid in its malicious routines.
It checks for the presence of a browser process in memory. It if finds one, it embeds a thread to it and connects to http://{BLOCKED}3.765321.info.
It hijacks browser sessions based on its downloaded configuration and initialization files in order to create malicious HTTP traffic. Malicious traffic created may involve downloading other possibly malicious file(s), connecting to sites, and displaying online advertisements. It is capable of affecting the any of the following browsers:
- Chrome
- Firefox
- Iexplore
- Maxthon
- Sogouexplorer
- Theworld
- Traveler
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Remove malware files dropped/downloaded by TROJ_POPUREB.SMB
Step 3
Restart in Safe Mode
Step 4
Search and delete this file
- %System Root%\Documents and Settings\All Users\Documents\My Videos\PulgFile.log
- %System Root%\PulgFile.log
- %System Root%\Documents and Settings\All Users\Documents\My Videos\Desktop.ini
- %User Profile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Internet Explorer.IE
- %Desktop%\Internet Explorer.IE
- %System Root%\Documents and Settings\All Users\Documents\My Videos\PulgConfig.log
- %Windows%\vc.ini
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CLASSES_ROOT\CLSID\{2559a1f4-21d7-11d4-bdaf-00c04f60b9f0}\shell\OpenHomePage
- @ = {characters}
- @ = {characters}
- In HKEY_CLASSES_ROOT\CLSID\{2559a1f4-21d7-11d4-bdaf-00c04f60b9f0}\shell\OpenHomePage\Command
- @ = %Program Files%\Internet Explorer\IEXPLORE.EXE http://{BLOCKED}3.{BLOCKED}21.info
- @ = %Program Files%\Internet Explorer\IEXPLORE.EXE http://{BLOCKED}3.{BLOCKED}21.info
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
- Default_Page_URL = http://{BLOCKED}3.{BLOCKED}21.info
- Default_Page_URL = http://{BLOCKED}3.{BLOCKED}21.info
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {871C5380-42A0-1069-A2EA-08002B30309D}.default = 1
- {871C5380-42A0-1069-A2EA-08002B30309D}.default = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\NewStartPanel
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\HideDesktopIcons\ClassicStartMenu
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
- {871C5380-42A0-1069-A2EA-08002B30309D} = 2
Step 6
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry. Before you could do this, you must restart in Safe Mode. For instructions on how to do this, you may refer to this page If the preceding step requires you to restart in safe mode, you may proceed to edit the system registry.
- In HKEY_CLASSES_ROOT
- .IE
- .IE
- In HKEY_CLASSES_ROOT
- IE
- IE
- In HKEY_CLASSES_ROOT
- JE
- JE
Step 7
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
- From: Start Page = http://{BLOCKED}3.
To: Start Page = {blank}
- From: Default_Page_URL = http://
To: Default_Page_URL = {default page}
- From: Hidden = 2
To: Hidden = 1
- From: HideFileExt = 1
To: HideFileExt = 0
- From: {871C5380-42A0-1069-A2EA-08002B30309D}.default = 1
To: {871C5380-42A0-1069-A2EA-08002B30309D}.default = 0
- From: {871C5380-42A0-1069-A2EA-08002B30309D} = 2
To: {871C5380-42A0-1069-A2EA-08002B30309D} = 1
Step 8
Restart in normal mode and scan your computer with your Trend Micro product for files detected as TROJ_POPUREB.SMB. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 9
Restore this file from backup only Microsoft-related files will be restored. If this malware/grayware also deleted files related to programs that are not from Microsoft, please reinstall those programs on you computer again.
- HKEY_CLASSES_ROOT\CLSID\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{C42EB5A1-0EED-E549-91B0-153485866016}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{20000000-0000-0000-0000-000000000000}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc850}
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{1f4de370-d627-11d1-ba4f-00a0c91eedba}
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{20000000-0000-0000-0000-000000000000}
Did this description help? Tell us how we did.


