TROJ_FAKEAV.WKA
Rogue:Win32/FakeSpypro (Microsoft)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
Trend Micro has flagged this Trojan as noteworthy due to the increased potential for damage, propagation, or both, that it possesses. Specifically, it poses as a rogue antivirus software.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
This Trojan connects to websites to download its component file, also detected as TROJ_FAKEAV.WKA. The aforementioned file then connects to remote sites to download another malicious component. Trend Micro also detects the component as this Trojan.
It then connects websites to display fake scanning result. It also connects to a remote site should the affected user chooses to purchase the full version of the fake rogue product.
This Trojan displays the following graphical user interface (GUI):
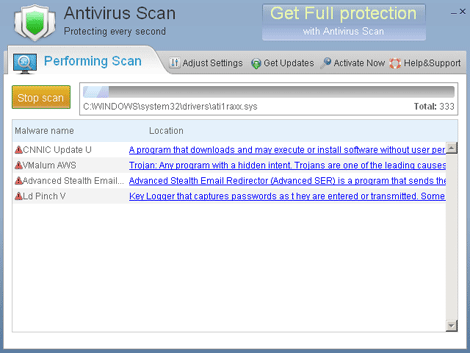
This Trojan displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers.
TECHNICAL DETAILS
Varies
PE
Yes
13 Jan 2011
Downloads files, Displays windows
Arrival Details
This Trojan may be downloaded from the following remote sites:
- http://{BLOCKED}ogle.info/tre/lena.exe/{random characters}
Autostart Technique
This Trojan adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
{random value} = %User Temp%\{random folder}\{random file name}.exe
Other System Modifications
This Trojan modifies the following registry key(s)/entry(ies) as part of its installation routine:
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Download
CheckExeSignatures = no
(Note: The default value data of the said registry entry is yes.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
ProxyEnable = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Hardware Profiles\0001\Software\
Microsoft\windows\CurrentVersion\
Internet Settings
ProxyEnable = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Hardware Profiles\Current\Software\
Microsoft\windows\CurrentVersion\
Internet Settings
ProxyEnable = 1
(Note: The default value data of the said registry entry is 0.)
HKEY_CURRENT_CONFIG\Software\Microsoft\
windows\CurrentVersion\Internet Settings
ProxyEnable = 1
(Note: The default value data of the said registry entry is 0.)
It adds the following registry keys as part of its installation routine:
HKEY_CURRENT_USER\Software\yr87fk3d2dnszapq2
It also creates the following registry entry(ies) as part of its installation routine:
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\PhishingFilter
EnabledV8 = 0
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\PhishingFilter
Enabled = 0
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\Download
RunInvalidSignatures = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
ProxyServer = http={BLOCKED}.{BLOCKED}.0.1:8075
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
ProxyOverride =
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Associations
LowRiskFileTypes = .exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Attachments
SaveZoneInformation = 1
Other Details
This Trojan does the following:
- Connects to any of the following websites to download its component file, which Trend Micro also detects as TROJ_FAKEAV.WKA:
- http://{BLOCKED}ogle.info/tre/lena.exe/wHe46ed9e9V0100f060006R00000000102Ta9406b4e203L656e2d75730000000000
- http://{BLOCKED}ogle.info/tre/lena.exe/xHe46ed9e9V0100f060006R00000000102Ta9406b42203l0409329
- http://{BLOCKED}ogle.info/tre/lena.exe/yHe46ed9e9V0100f060006R00000000102Ta9406b42203l04093020
The aforementioned file will then connect to the following remote sites to download another malicious component, also detected as TROJ_FAKEAV.WKA:
- http://{BLOCKED}.192.250/user/xl3.php
- http://{BLOCKED}.192.250/user/up/xl3.dat
- http://{BLOCKED}ogle.info/tre/lena.exe/xHe46ed9e9V0100f060006R00000000102Ta9406b42203l0409328
- Connects to the following websites to display fake scanning result:
- http://{BLOCKED}resh.com/check?pgid=8
- http://{BLOCKED}resh.com/percer.php?login=ODMuMA==

It also connects to the following remote site should the affected user chooses to purchase the full version of the fake rogue product:
- http://{BLOCKED}resh.com/shop?abc=cGdpZD04JnI9ODMuMA==
Rogue Antivirus Routine
This Trojan displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers.
SOLUTION
8.900
7.766.11
13 Jan 2011
1/13/2011 12:00:00 AM
7.767.00
13 Jan 2011
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Scan your computer with your Trend Micro product and note files detected as TROJ_FAKEAV.WKA
Step 3
Restart in Safe Mode
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- {random value} = %User Temp%\{random folder}\{random file name}.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\PhishingFilter
- EnabledV8 = 0
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\PhishingFilter
- Enabled = 0
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download
- RunInvalidSignatures = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- ProxyServer = http:\\{BLOCKED}.{BLOCKED}.0.1:8075
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- ProxyOverride = <local>
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
- LowRiskFileTypes = .exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments
- SaveZoneInformation = 1
Step 5
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download
- From: CheckExeSignatures = no
To: yes
- From: CheckExeSignatures = no
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- From: ProxyEnable = 1
To: 0
- From: ProxyEnable = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Hardware Profiles\0001\Software\Microsoft\windows\CurrentVersion\Internet Settings
- From: ProxyEnable = 1
To: 0
- From: ProxyEnable = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Hardware Profiles\Current\Software\Microsoft\windows\CurrentVersion\Internet Settings
- From: ProxyEnable = 1
To: 0
- From: ProxyEnable = 1
- In HKEY_CURRENT_CONFIG\Software\Microsoft\windows\CurrentVersion\Internet Settings
- From: ProxyEnable = 1
To: 0
- From: ProxyEnable = 1
Step 6
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry. Before you could do this, you must restart in Safe Mode. For instructions on how to do this, you may refer to this page If the preceding step requires you to restart in safe mode, you may proceed to edit the system registry.
- In HKEY_CURRENT_USER\Software
- yr87fk3d2dnszapq2
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as TROJ_FAKEAV.WKA. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

