ANDROIDOS_LOVEFRAUD.HRX
AndroidOS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Trojan gathers device information. This is the Trend Micro detection for Android applications bundled with malicious code.
TECHNICAL DETAILS
Mobile Malware Routine
This Trojan is a file that collects the following information on an affected mobile device:
- wifilist
- location
- gsm
- version
- baseband
- location
- imei
- imsi
- cpuinfo
- meminfo
- deviceid
It gathers the following device information:
- wifilist
- imei
- imsi
- deviceid
- meminfo
- cpuinfo
Once the app is used, it displays the following screen:
- popup- notification that woman say hello
Upon installation, it asks for the following permissions:
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_LOCATION_EXTRA_COMMANDS
- android.permission.ACCESS_NETWORK_STATE
- android.permission.ACCESS_WIFI_STATE
- android.permission.BATTERY_STATS
- android.permission.BLUETOOTH
- android.permission.BLUETOOTH_ADMIN
- android.permission.BROADCAST_STICKY
- android.permission.CAMERA
- android.permission.CHANGE_NETWORK_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.GET_TASKS
- android.permission.INTERNET
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.MOUNT_UNMOUNT_FILESYSTEMS
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.READ_LOGS
- android.permission.READ_PHONE_STATE
- android.permission.READ_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_USER_PRESENT
- android.permission.RECORD_AUDIO
- android.permission.RESTART_PACKAGES
- android.permission.SEND_SMS
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.SYSTEM_OVERLAY_WINDOW
- android.permission.VIBRATE
- android.permission.WAKE_LOCK
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.WRITE_SETTINGS
- com.android.launcher.permission.INSTALL_SHORTCUT
- com.android.launcher.permission.READ_SETTINGS
- com.android.launcher.permission.WRITE_SETTINGS
- com.ut.permission.DEVICE_STATE
It sends out the following messages:
- woman interests you .wants to fall in love with you, talks to you, asks your personal information. All these are from bot machine.
Based on analysis of the codes, it has the following capabilities:
- ask for money
This is the Trend Micro detection for Android applications bundled with malicious code.
NOTES:
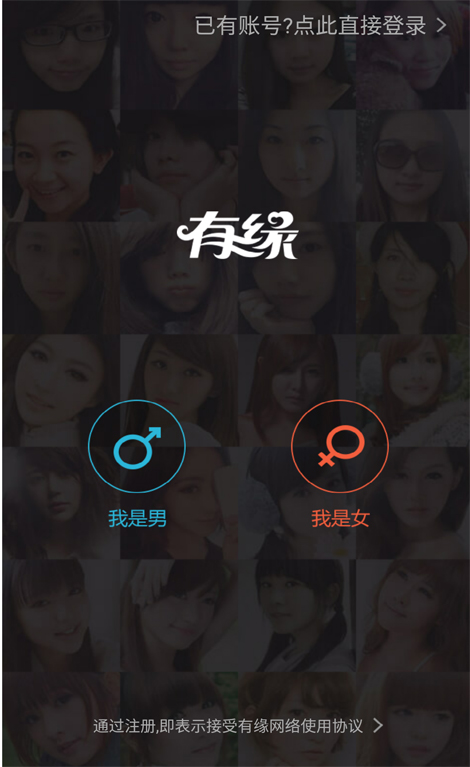
The app installs shortcut automatically. It assigns first name and password automatically. The app uses umeng SDK for big data analysis. It is a bogus dating app and all information someone sends to the users and the voice chats are from a bot. The dating partners are not real people. Once the victim believes that the people they talked to are real users and wants to see more information like pictures, the said app charges payment to the user. The app pushes notifications to remind users to fill the personal information and even pop ups letter to the users. It also displays the following image:
SOLUTION
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android and iOS smartphones and tablets from malicious and Trojanized applications. It blocks access to malicious websites, increase device performance, and protects your mobile data. You may download the Trend Micro Mobile Security apps from the following sites:
Did this description help? Tell us how we did.


