ANDROIDOS_FAKETOKEN.A
TrojanSpy:AndroidOS/FakeToken.A (Microsoft); Android.Faketoken (Symantec); Andr/FkToken-A (Sophos)
Information Stealer
Android OS


Threat Type: Spyware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This spyware targets mobile banking users by posing as a fake token generator. During execution it asks for the user's password and generates a fake token while sending the user's information to a specific number and remote servers in the background.
To get a one-glance comprehensive view of the behavior of this Spyware, refer to the Threat Diagram shown below.
This spyware is an application that poses as a token generator from a certain bank. Users must enter a password. Otherwise, it displays an error.
It generates the fake token and executes its malicious code in the background.
This spyware may be unknowingly downloaded by a user while visiting malicious websites. It may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This spyware may be unknowingly downloaded by a user while visiting malicious websites.
It may be manually installed by a user.
NOTES:
It is an application that poses as a token generator from a certain bank. Upon execution, it displays the following:
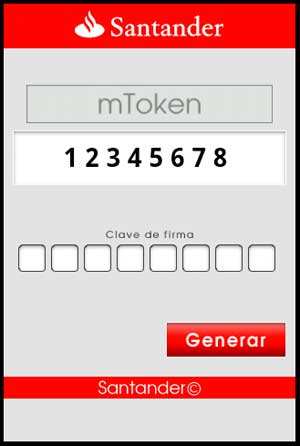
Users must enter a password. Otherwise, it displays an error.
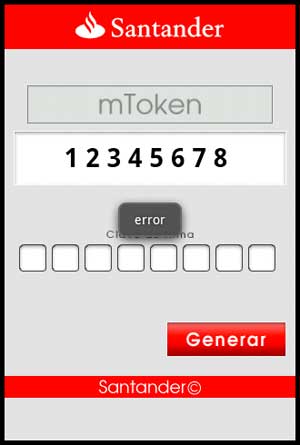
When users click Generar, it generates the fake token and executes its malicious code in the background. It gathers the following information:
- IMEI
- IMSI
- Phone model
- SDK version
- SID
It sends these information along with the password entered to the following number:
- 79021121067
It also sends these information to the following remote servers:
- http://{BLOCKED}hop.ru/cp/server.php
- http://{BLOCKED}shopbest.com/cp/server.php
It also steals the following information from the affected device:
- Contacts list
- Text messages
It also has the capability to execute itself at a scheduled time. This enables the malware to run a background service and listen for commands from the remote servers. These include the following commands:
- Download and install another APK
- Send the contacts list and SMS messages to the remote server
- Update the number where stolen information are sent
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.



