ANDROIDOS_DROIDD.MJ
Rooting Tool
Android OS


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This hacking tool is used to root Android devices. Rooting enables the users to have elevated rights and permissions to access Android's software.
This hacking tool may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This hacking tool may be downloaded from the following remote sites:
- http://forum.xda-developers.com/showthread.php?t=833953
It may be manually installed by a user.
Installation
This hacking tool drops the following files:
- 755 root.root /system/bin/busybox
- 6755 root.root /system/bin/su
- 755 root.root/system/app/SuperUser.apk
NOTES:
This hacking tool is used to root Android devices. Rooting enables the users to have elevated rights and permissions to access Android's software.
It gets the root shell by extracting and running rageagainstrage.
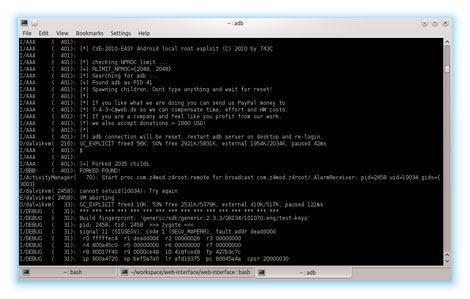
After getting the root shell, it can temporary root/permanent root/unroot the device.
To temporary root, it extracts first busybox,su,SuperSuer.apk to $x, and then runs the following commands:
- chmod 777 $x/busybox
- $x/busybox killall rageagainstthecage
- $x/busybox killall rageagainstthecage
- $x/busybox rm $x/temproot.ext
- $x/busybox rm -rf $x/bin
- $x/busybox cp -rp /system/bin $x
- $x/busybox dd if=/dev/zero of=$x/temproot.ext bs=1M count=15
- $x/busybox mknod /dev/loop9 b 7 9
- $x/busybox losetup /dev/loop9 $x/temproot.ext
- $x/busybox mkfs.ext2 /dev/loop9
- $x/busybox mount -t ext2 /dev/loop9 /system/bin
- $x/busybox cp -rp $x/bin/* /system/bin/
- $x/busybox cp $x/su /system/bin
- $x/busybox cp $x/busybox /system/bin
- $x/busybox chown 0 /system/bin/su
- $x/busybox chown 0 /system/bin/busybox
- $x/busybox chmod 4755 /system/bin/su
- $x/busybox chmod 755 /system/bin/busybox
- pm install $x/SuperUser.apk
To permanent root, it extracts first busybox,su,SuperSuer.apk to $x, and then runs the following commands:
- chmod 777 $x/busybox
- $x/busybox mount -o remount,rw /system
- $x/busybox cp $x/su /system/bin/
- $x/busybox cp $x/SuperUser.apk /system/app
- $x/busybox cp $x/busybox /system/bin/
- chown root.root /system/bin/busybox
- chmod 755 /system/bin/busybox
- chown root.root /system/bin/su
- $x/busybox chmod 6755 /system/bin/su
- chown root.root /system/app/SuperUser.apk
- chmod 755 /system/app/SuperUser.apk
- rm $x/busybox
- rm $x/su
- rm $x/SuperUser.apk
- rm $x/rageagainstthecage
- sync
- sync
- reboot
To unroot, it extracts first busybox to $x, and then runs the following commands:
- $x/busybox mount -o remount,rw /system
- $x/busybox rm /system/bin/su
- $x/busybox rm /system/xbin/su
- $x/busybox rm /system/bin/busybox
- $x/busybox rm /system/xbin/busybox
- $x/busybox rm /system/app/SuperUser.apk
- sync
- sync
- reboot
SOLUTION
Step 1
Remove unwanted apps on your Android mobile device
Step 2
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Did this description help? Tell us how we did.

