PII Leaks and Other Risks From Unsecure E-Commerce APIs
 Download Examining Security Risks in Logistics APIs Used by Online Shopping Platforms
Download Examining Security Risks in Logistics APIs Used by Online Shopping Platforms
Application programming interfaces (APIs) are one of the chief enablers that have made the integration of different systems from different entities a reality. APIs integrate data and services between businesses and third-party vendors to fulfill different market needs, improve the provision of services, and gain consumer insights, thus propelling the remarkable growth of e-commerce in recent years.
In an ideal world, organizations execute API implementation properly to ensure that the integration is airtight and the risk of inadvertent exposure of personally identifiable information (PII) is nonexistent. However, the present reality is far from ideal; the risk of PII leakage associated with API integration remains a serious security concern and is therefore worthy of attention from e-commerce stakeholders and consumers whose private information has become a sought-after commodity in the criminal underground.
Trend Micro Research discovered several e-commerce and logistics platforms that have been leaking PII and purchase information unknowingly due to insufficient API security and authentication measures. While there is no evidence yet that the security flaws we found have been exploited to a large extent, the gravity of the potential harm worsens when leaked PII is combined with information about the items purchased, as this can reveal sensitive information that malicious actors can use to create fraudulent schemes. If left unaddressed, the exploitation can damage business reputation, affect the bottom line, and inflict harm on consumers.
As people adjust to life in the post-pandemic era, the shift in consumer behavior that led to a wider use of e-commerce platforms to access goods and services has become a significant feature of modern trade, so much so that it is almost unthinkable to desire or imagine a life without the conveniences that e-commerce provides.
The online platforms commonly used to buy and sell merchandise is one part of the e-commerce equation; fulfillment services comprise another. Only the largest retailers have the financial wherewithal to set up their own logistics service, which means that most online merchants need to partner with external logistics providers to deliver their products to their customers.
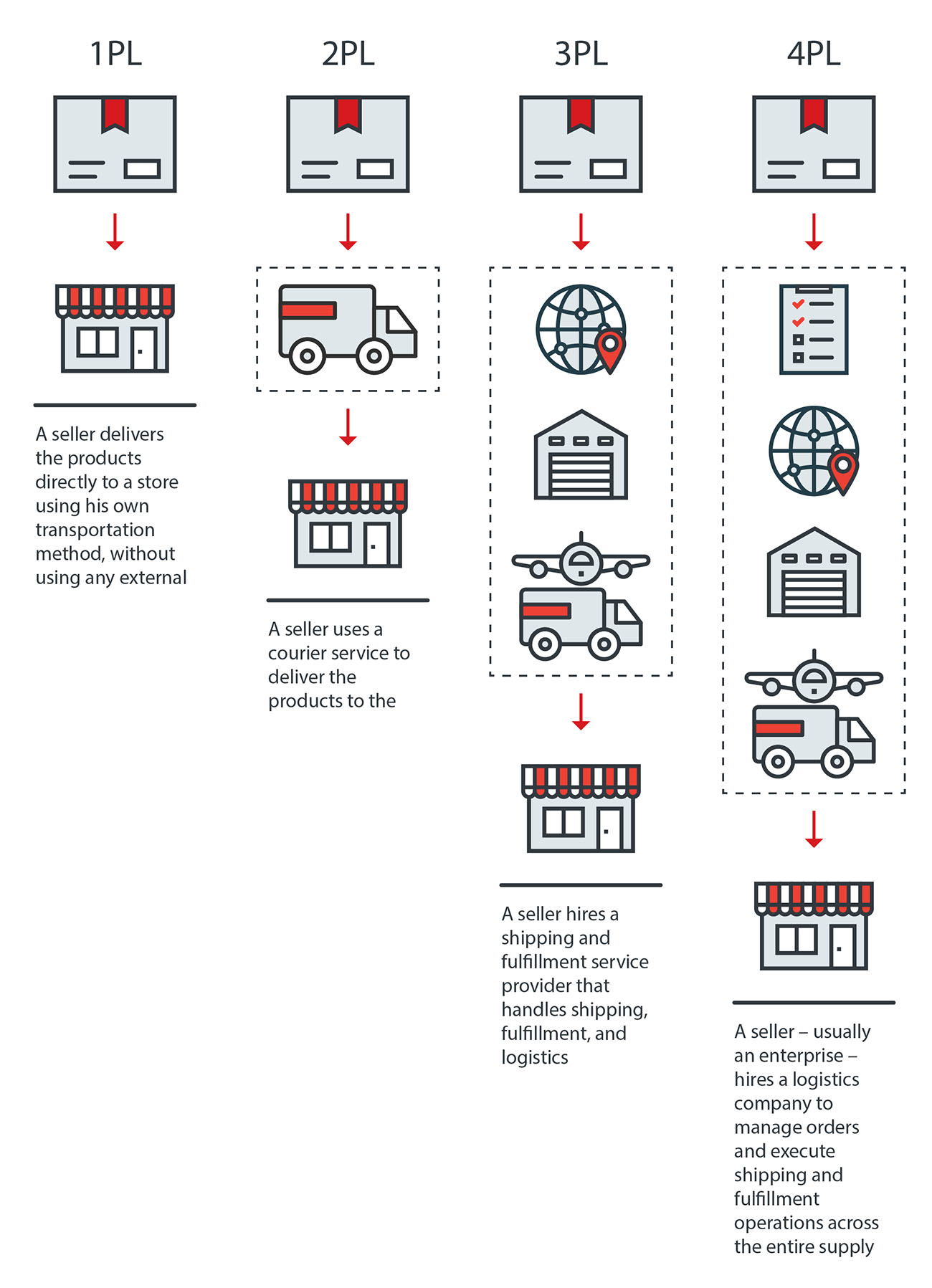
Online merchants need external logistics providers to manage the supply chain logistics process. This can be done either in part or through a complete logistics solution. The level of engagement with logistics providers varies. It can be a basic courier service that merchants use to deliver products referred to as second-party logistics (2PL), or a third-party logistics (3PL) provider that takes care of warehousing, fulfillment, and delivery of products. Enterprises, on the other hand, can hire a fourth-party logistics (4PL) provider to handle the entire supply chain. Figure 1 shows how an external logistics provider works in different use cases.
We investigated 3PL and 4PL providers that were leaking consumers’ PII through unauthenticated or unsecure methods. Aside from 3PL and 4PL platforms that unwittingly expose PII, we also discovered services that are integrated to them that implement weak API security practices. Some e-commerce platforms allow merchants to integrate existing external logistics providers through APIs to seamlessly consolidate different services into a single platform. To do this, e-commerce platforms integrate with logistics systems platforms to pass along shipping information. Unfortunately, this creates a situation in which a security flaw in the API or authentication chain can disclose PII through HTTP replay attacks because of insufficient authentication measures.
One way that PII is being leaked is through the URL query parameters in e-commerce platforms and logistics API. E-commerce platforms usually require customers to log in to an account to protect PII and provide access to the details of an order. Some platforms offer a guest checkout option as an alternative. A third option involves using unique URLs that e-commerce websites send to the users through email or SMS that redirects them to the website where the order information can be found. Doing so allows guest users to check the order status without the need to authenticate the session. The presumption that the combined use of a unique URL sent to an email address or phone number owned by the recipient sufficiently protects PII is problematic as this creates a false sense of security. Our investigation shows that it is possible for unauthorized parties to retrieve a customer’s PII by directly accessing a URL without the need for further authentication.
Communication between external logistics providers using API to provide seamless integration can also lead to PII exposure. This happens when the tracking link visited by a user needs to make a query through an external service provider to retrieve data and allow users to view the order information.
The practice of passing authentication keys as part of the URL parameter can also potentially leak PII given that such keys can still be retrieved using a variety of means, such as accessing the user’s browsing history and router logs. The use of unencrypted URL query parameters renders the PII susceptible to sniffing and man-in-the-middle attacks.
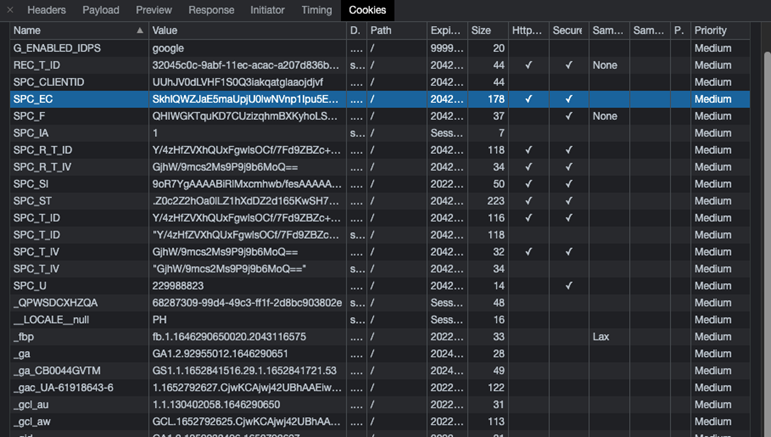
The use of session and cookies that have no set expiration by some 3PL providers also poses a risk for PII leakage. We observed several instances in which 3PL providers did not comply with the security best practices specific to the use of sessions and cookies to regulate authentication. Malicious actors can use the detected cookie key to replay transactions and obtain PII, which they can exploit to launch malicious schemes.
Figure 2. The list shows cookies with expiration dates set beyond the OWASP-recommended duration, thus making the cookie information available for malicious actors to replay a transaction.
The scenarios that we identified in our research describe malevolent schemes that will be greatly aided if malicious actors use the exposed PII and order information for their purpose.
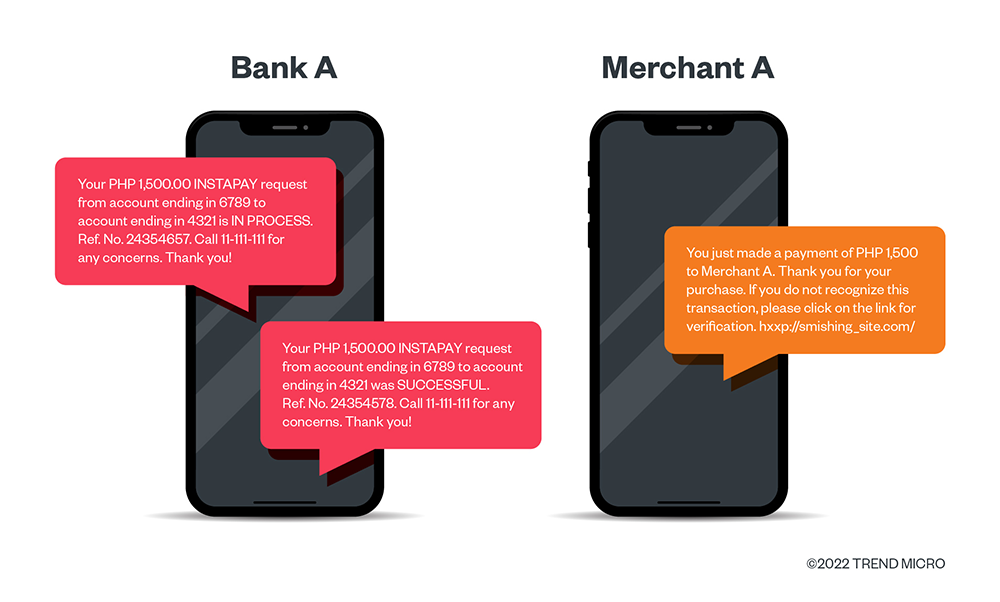
Information such as phone numbers, email addresses, and payment methods can be used to devise SMS fraud and phishing attacks. Criminals can analyze the users’ buying habits and mode of payment if they get hold of such information and craft sophisticated SMS messages or phishing websites.
Figure 3. Cybercriminals can use leaked PII to create fraudulent schemes. They can stealthily make SMS notifications appear legitimate to deceive victims and lead them to phishing websites.
Schemes that involve the interception of packages, also known as cash-on-delivery (COD) scams, became widespread in Southeast Asia. One report was of a social engineering ploy in which a courier of the logistics provider delivered an item that the customers purportedly bought, and persuaded them to pay an amount that was significantly higher than the actual cost of the delivered item.
Another report was of scammers that collected customers’ PII from improperly discarded delivery packages. The malicious actors who used the PII persistently contacted the victims for extortion.
The extortion techniques that we cited were enabled by improperly disposed packaging labels. The PII found on delivery packaging labels provides the malicious actors with the necessary information to identify potential prey for their schemes. In the same vein, PII and order information that are exposed due to poor logistics API implementation are the digital counterparts of improperly disposed packaging labels that crafty cybercriminals can use for scams in the future.
Keeping PII protected from unauthorized use has always been a common goal for e-commerce platforms and logistics providers, but a lot of work still needs to be done to achieve this as security flaws that the Open Web Application Security Project (OWASP) warned about more than 10 years ago still abound. E-commerce platform providers should regularly audit API services aside from implementing encryption on URL query strings to minimize the risk of PII leakage. Here are other recommendations:
- Software developers who design API for use in e-commerce platforms should determine what data needs to be provided throughout the course of the transaction and what authentication measures should be used to prevent data from being exposed to accounts with access restrictions or limited privileges.
- Transactions that involve the transmission of PII to a third party should be done properly by setting security processes in place. Measures to encrypt data and authenticate requests should be implemented each time PII is transmitted. Basic authentication mechanisms like JSON Web Token (JWT) or base64 salted tokens, would suffice.
- Object level authorization checks, which are typically implemented at the code level to ensure that access to objects is granted only to authorized users, should also be implemented in every API endpoint that receives an object's ID and performs any type of operation on the object.
- Consumers should avoid the installation of unknown browser extensions to web browsers that can read and collect unencrypted URL query strings.
- Implementation of two-factor or multi-factor authentication for e-commerce platforms before displaying content with PII should become a standard practice.
- Consumers should also delete their browsing history, especially on public or shared devices.
- Consumers should also properly discard delivery packaging and make sure that the labels with PII are shredded or obfuscated so malicious actors can no longer read them.
The large-scale use of e-commerce platforms has made logistics APIs a necessity, so securing them is critical. Neglecting to do so exposes users to data leaks that enable malicious actors to devise more attacks that can cause more damage. Our research paper, “Examining Security Risks in Logistics APIs Used by Online Shopping Platforms,” can help jumpstart efforts to establish a proactive cybersecurity approach for e-commerce stakeholders who want to make online shopping platforms a safe space for consumers.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks