In my 27 years in cybersecurity, I have seen a lot over that time, both good and bad. The bad is that it seems malicious actors continue to thrive and be successful at targeting victims and extracting value from them, whether it be stealing data or dropping ransomware on their critical systems. The good news is that technology has allowed businesses to improve their processes and gain value with less by automating many of the tasks previously done by humans. It has also allowed us humans to be more effective and efficient in our daily work.
One thing that hasn’t changed over the years is the notion that a layered security approach is better. As the attack surface has grown over the years, it has allowed malicious actors to continue to expand their attacks across these surfaces. Below are just some of the threats we’ve seen over the years that have caused new security tech to be created to deal with them.
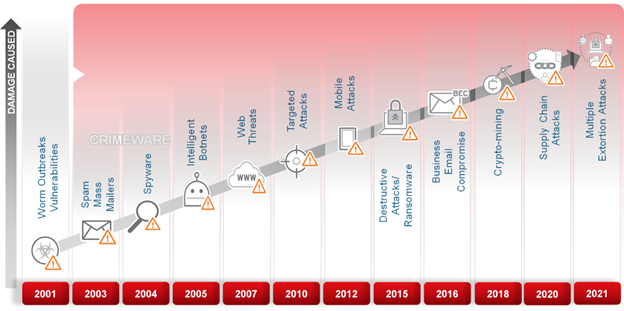
These constant shifts created a cybersecurity paradigm that said more is better than less. Many organizations started investing in multiple security solutions that were “best-of-breed” and allowed them to defend all the areas of their network. Examples are endpoint, messaging, network, web, cloud, and now IoT/IIoT to ensure they protect against threats at all these points. This approach was great when the threats weren’t connected and tended to be one-and-done types of threats. But the world has changed, as have the malicious actors targeting businesses.
Today the attack is likely to cross all these points and may be done by different actor groups working together as part of the same attack. These attacks are now coordinated and can be done within days of the initial access of a network, and attackers can stay resident for weeks, months, and even years using tactics that allow them such access.
Because many organizations supported this old cybersecurity paradigm, they now have anywhere from 10 to 40 cybersecurity products they try to manage. This can be extremely costly for most organizations between monthly subscriptions, support contracts, to incident response costs. Also, these all tend to be siloed and do not communicate nor collaborate with each other, and as such, it makes it very difficult for the organization’s security personnel to manage them, nor able to identify the entire attack chain. As such, many businesses are looking for a better way to help them deal with the attacks today. A few things are driving this:
1. Economics: As businesses look to the future, they are being asked to cut costs. This can be done by doing an audit of all the security products and identifying those that may overlap or may not be performing as well as expected.
2. Lack of Personnel: This is a big one today as most organizations don’t have enough trained personnel to manage their security. Looking for ways to minimize the number of security products to manage and investing in more automation can help improve this.
3. Improved Visibility: Siloed security products will detect stuff and alert you, but in many cases, these alerts can be overwhelming and also may not tell you the root cause of the attack nor give you the ability to identify all components of the attack.
Technology has improved things over the years, and the same is true within the cybersecurity industry. Artificial intelligence and machine learning (AI/ML) has allowed vendors to improve their ability to detect new threats, but more importantly, allowed them to pull in massive amounts of data and deliver contextual information about a threat or an attack.
At Trend Micro, we’ve been doing cybersecurity for 35 years and have extensive knowledge of how attacks work and how to defend against them. We’ve been using AI/ML since 2005 and so have gained a lot of understanding of how to implement this within our solutions. Because of this, and the fact that we have security solutions that go across the whole network stack (endpoint, messaging, network, web, cloud, IoT/IIoT), we’ve been able to develop an integrated cybersecurity platform (Trend Vision One) that consolidates, collaborates, and provides visibility into your entire attack surface. This can allow a business to:
- Consolidate many of their products into one vendor.
- Automate many of the day-to-day tasks security personnel have to do today.
- Utilize a single console that provides visibility into your attack surface and manages triage and push security controls to mitigate an attack.
Many may think consolidating into a single vendor might have an adverse effect on their ability to defend against the myriad of attacks, but while the consolidated solutions may not be the best of the best, they are likely very good still. The integration and collaboration across the platform’s XDR solutions can help improve the ability to defend, as defenders will have improved information about the attack. But if this is a concern, this platform also supports extensive 3rd party integration to pull in threat data from other vendors if you cannot support a single vendor or there are other solutions you like to use. But the main benefit is certainly an opportunity to relook at your overall cybersecurity strategy and models that today can help you lower costs, help with personnel issues, and give you a way to minimize your risks around cyber-attacks. This platform approach will be the new paradigm moving forward and one you should think about moving towards.

