Previous posts
- Overlooked attack vectors
- Security risks in industrial application stores
- Trojanized libraries for Industrial IoT devices
On May 11, 2020, Trend Micro released a paper showing the results of proof-of-concept research on new security risks associated with smart factories. In this series of 5 columns, based on the results of this research, we will look at the security risks to be aware of when promoting smart factories by examining overlooked attack vectors, feasible attack scenarios, and recommended defense strategies. This column describes how the MES plays an important role in the manufacturing process and how cyberattacks on the MES can affect production activities.
MES: "The playmaker"
If I had to describe the role of the MES (Manufacturing Execution System) in a single phrase, it would be "manufacturing playmaker." As I mentioned in the previous column, the manufacturing process is divided into multiple layers, and the system performs a different role in each layer. The MES is at the top layer of the IT-OT integration, and it manages the execution of manufacturing processes; thus, it plays a very important role in making factories smarter (Fig.1). Because improving productivity is the manufacturing industry's first priority, how to efficiently use resources such as "people, goods, money, and time" to make good products is key. The MES is typically located between the manufacturing floor network and the ERP, which manages the entire company's resources. The MES receives production orders and distributes production resources, manages the manufacturing process, and gives instructions and provides support to workers. It is the brain of the smart manufacturing process.
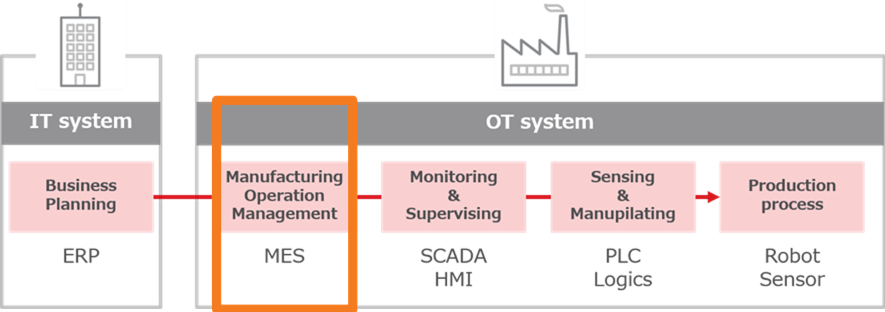
<Fig.1> The MES plays a role in manufacturing operation management
In addition, the MES not only manages the production line, it also "embeds" the skills of field engineers at the production site, which tend to be individualized these days. Since the MES can accumulate the information necessary for actual manufacturing in the form of a "work template," it is possible to store and share ordering work, resource allocation, and production time, which thus far have depended on the intuition and experience of each professional. In this way, the MES can standardize work that previously depended on individuals, and also reduce training time. As a result, this multifunctional system is expected to solve problems caused by labor shortages.
The MES unconditionally trusts what it gets
Now, let's analyze the MES from a cybersecurity angle. By its very nature, the MES acts as a data bridge between IT systems and factory floor networks. The MES in the factory is connected to the MES database and ultimately to IT systems such as the ERP; these systems exchange data with each other (Fig.2).
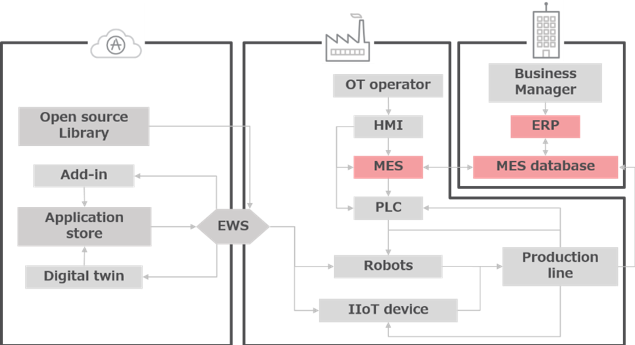
<Fig.2> The MES exchanges data with the MES database and IT systems such as the ERP
This communication improves the efficiency of the manufacturing process, but this efficiency must be based on an assumption of CIA (confidentiality, integrity, availability) with respect to data exchange. Notably, commercially available MESs are designed on the premise that incoming data follows the same principle. This means that if the MES database does not have data-integrity capabilities, an attacker can change the database values, thus causing a change in the manufacturing process. Based on this hypothesis, we conducted the following experiments in this research.
Attack scenario: An MES database compromised by lateral movement
With the exception of cloud-based services, enterprise-class MESs are rarely connected directly to the Internet. Therefore, if the MES is compromised, it is reasonable to assume an attacker has moved horizontally from the IT system. Also, the MES uses an internal database (in this case, Microsoft Access) to store the work plans created by the administrator. When a work plan is executed, the MES uses this database to translate the work plan's operations into a set of parameter values for the selected stations. For example, the operation "Drill to the product's lower right part" corresponds to the parameter value "2," and this is used to communicate the correct, low-level instruction to the station that controls the drill. Given the importance of this data exchange, we considered the impact of tampering with the MES database values. For the above reasons, the following model could function as a realistic attack method against the MES. The MES used in this experiment is "FESTO MES4 (v 1.1.0.9)," but the attack scenario can be applied to all MESs that do not have proper data-integrity functions.
- The attacker obtains access to the MES database.
- The attacker reverse-engineers the database structure.
- The attacker alters a number stored in a row of the database.
Result: Defective products & operation suspension
In this research, the attack method was executed successfully on the smart manufacturing system, thereby confirming that the MES could not authenticate the database and that it did not have a method to verify the integrity of each record. This allows an attacker to tamper with the database and to perform the following attacks.
- Defective products
It was confirmed that changing the parameter values in the database also changed the machine's work content, resulting in the production of defective products. In this research, when the parameter value "2" of "Drill to the product's lower right part" was changed to "1" by operating the database, even though the operator executed the template normally, drilling was executed in an unintended position (Photo 1). This attack can also be applied to other actuators. Similarly, the experiment found that by tampering with the results of the camera check, the quality check system returned "OK" even when defects were present.

<Photo 1> A (dummy) defective product drilled on the wrong side
- Operation suspension
It was confirmed that it is possible to cause a denial of service (DoS) attack by entering an out-of-range value for the parameter in the database. The movement of actuators (equipment such as drills and pressers) at each station is linked to the parameter values in the database. In this case, the parameter that determines the drill's drilling position was limited to two values, "1" and "2." Upon entering "5," which is out of range, the drill did not operate and the production line stopped.
Countermeasures: Database protection & data integrity checking
The best strategy to avoid attacks is to prevent the exposure of critical systems such as databases and the ERP. As described above, all traffic to the MES is allowed, and the MES does not have a data integrity check function. Therefore, database protection is the first thing to consider. To this end, specific measures that are effective include access control to the database, user authentication, and log monitoring. In addition, a data integrity check function must be implemented, such as raising an alert when a database value is changed. Data reliability must be ensured for the MES, which supports the upstream of the manufacturing process in smart factories.
The next post will wrap up this series by examining recommended security strategies and countermeasures.

