Privacidad y riesgos
Business Email Compromise Attack Tactics
Is BEC more damaging than ransomware? What tactics are BEC actors using? How can organizations bolster their defenses? Jon Clay, VP of threat intelligence, tackles these pertinent questions and more to help reduce cyber risk.
- What is business email compromise (BEC)?
- BEC vs. ransomware
- Types of email services used in BEC attacks
- Defense strategies against BEC scams
- Next steps
What is business email compromise (BEC)?
BEC, also known as email account compromise (EAC), is a type of email cybercrime targeting companies with the typical objective of having company funds wired into the attacker’s bank account. The five types of include: bogus invoices, CEO fraud (impersonating a c-level employee to ask coworkers for money), account compromise, attorney impersonation, and data theft.
BEC vs. ransomware
Seemingly every day there’s news of another cyberattack leading to a multimillion-dollar ransom demand like the Russian-based, ransomware gang REvil initially demanding $70 million from organizations who were crippled by the Kaseya attack. But despite being a mainstay in the media, ransomware losses are dwarfed by those associated with BEC attacks; the FBI reported in 2021 $2.4 billion in adjusted losses from BEC complaints and $49.2 million from ransomware.
There are a couple reasons why BEC losses continue to dwarf ransomware: BEC attacks are historically less technical and rely heavily on social engineering, whereas gaining residence and launching malware to exfiltrate sensitive data requires more skill and time. And due to the expertise required, ransomware gangs tend to be smaller, whereas BEC actors are organized in a looser, more fluid structure, making it difficult for law enforcement to target the leader.
Societal conditions also play a part. The uptick in remote workers using unsecure home networks and personal devices certainly contributed to the increase in BEC losses. Additionally, cybercriminals have upped their game from simple hacking and spoofing to leveraging virtual meeting platforms, creating deep fake videos of CEO/CFOs, and using cryptocurrency to make recovering funds harder.
Types of email services used in BEC attacks
While BEC may be dressed up differently, it is still an email scam at its core. Let’s look at how and why these five types of email services are used by cybercriminals.
1. Free email services
Why it’s used:
- No cost to entry for attackers
- Trusted marketing quality
- Service provides a promise of confidentiality in terms of protecting legitimate users
- Bulk account creation tools can be used to facilitate numerous accounts
Attack tactics:
- Spoof enterprise employees’ names to commit CEO fraud
- Find personal emails through social media scanning, and spoof friend’s email address so you believe it is from your friend
- Use common account naming conventions

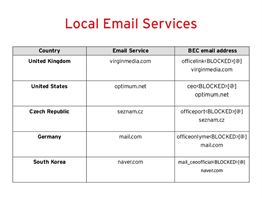
2. Local email services
Why it’s used:
- Appears legitimate since it’s locally recognized and used
- Ease of use
Attack tactics:
- Compromise legitimate accounts
- Create new accounts
- Obtain personal information to use in future attacks (ie., addressing potential victim by their first name)
3. Encrypted email services
Why it’s used:
- Attackers can hide their footprints
- Prevent systems from tracking them
- Higher level of security features
Attack tactics:
- Legitimate email address is displayed in the from header and actor’s malicious email is hidden in the reply section

4. Self-registered domains directed to featured email services
Why it’s used:
- Can create look-alike domains for legitimate companies to deceive victims
Attack tactics:
- Control positive email authentication results such as sender policy framework (SPF) or even DomainKeys Identified Mail (DKIM) when sending email to victims

5. Stolen email credentials and conversations
Why it’s used:
- Trusted accounts
- Improves success of BEC attacks
- Can set up rules on email account that anything sent to their domain can be rerouted, enabling attacker to run scam undetected
Attack tactics:
- Hijack existing conversations where trust is established to trick unsuspecting victim
- Deploy spam campaign with malicious attachments dropping keyloggers or trojan stealers
- Steal credentials in apps like browsers, SMPT, FTP, VPNs, and from computer and systems to spread attack laterally
- Manipulate account or attachments in existing email conversation (ie., sending an “updated” invoice where payment is rerouted to attacker’s account)
Defense strategies against BEC attacks
To strengthen your email security posture and reduce cyber risk, answer the following questions across the four pillars to identify potential gaps in cybersecurity strategy:
1. People: Many BEC attacks start at the employee level, or the “perimeter” of the attack surface. Strengthening this first line of defense is essential.
- Do you have and regularly run a cybersecurity awareness program that addresses email threats?
- Are you ensuring that key c-level employees and high-value departments, like finance, HR, and legal, are aware of socially engineered attacks using their likeness?
- Do you have competent staff? If not or your resources are limited, do you leverage a managed service to help offset shortages?
2. Culture: Strengthening your security posture will be an uphill battle if the only employees that care about security is your security team.
- Have you established a strong cyber culture within the organization wherein everybody from the top down is cognizant of security best practices?
- Do you have buy-in from the executives that security is a priority and a business enabler?
- Do you enable law enforcement to help reduce cybercrime by reporting any incidents?
3. Process: Establishing processes can shift your security defenses from reactive to proactive.
- Do you audit your emails regularly and analyze logs for BEC attacks?
- Do you have an email where employees can forward suspicious messages for further investigation?
- What best practices frameworks are you leveraging?
- Have you established system deployment, management, and maintenance processes?
- Do you have a response plan that includes cyber insurance, direct access to critical bank accounts to stop wire transfers, etc.?
- Have you implemented a two-factor authentication (2FA) process to require wire transfer requests to be verified via a secondary medium to the requestor?
4. Technology: Look to leverage the latest threat defenses like AI, ML, and behavioral analysis within a single dashboard to reduce manual tasks for overstretched security teams.
- How many products are you using? Are you using disparate point products that are creating visibility and security gaps?
- Have you investigated consolidating products to one vendor for improved visibility?
- Do you have a solution that automates virtual patching to limit the scope of an attack?
- Do you have a tool that covers all the different aspects of email security, including internal messages? Bonus: does it integrate with your other security products?
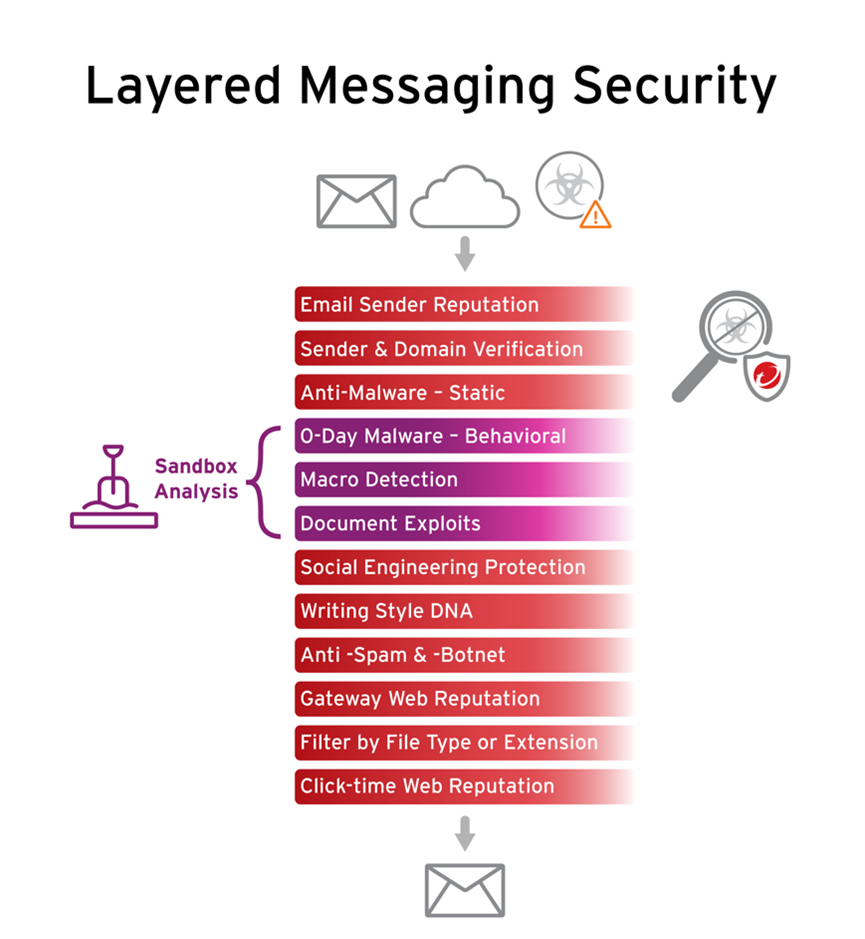
Next steps
While BEC attacks aren’t as headline-grabbing as other forms of cybercrime, it is still a very significant and costly threat to businesses of any size that needs to be continually monitored.
This doesn’t mean you need to add another suite of security products to your IT ecosystem and create more complexity; with the right cybersecurity platform, you can address a gauntlet of critical threats—including email security and ransomware—to reduce cyber risk across the attack surface.
For more information about BEC statistics and managing cyber risk, check out the following resources:
- Worldwide 2021 Email Phishing Statistics & Examples
- Addressing Cyber Risk with a Unified Platform
- Managing Cyber Risk: The People Element

