Mobile
Adware Posing as 85 Photography and Gaming Apps on Google Play Installed Over 8 Million Times
The mobile platform is ubiquitous — enabling users to make online transactions, run their everyday lives, or even use it in the workplace. It’s no surprise that fraudsters and cybercriminals would want to cash in on it. Delivering adware, for example, enables them to monetize affected devices while attempting to be innocuous. And while they may be viewed as a nuisance at best, mobile ad fraud- and adware-related incidents became so rampant last year that it cost businesses hefty financial losses.
The mobile platform is ubiquitous — enabling users to make online transactions, run their everyday lives, or even use it in the workplace. It’s no surprise that fraudsters and cybercriminals would want to cash in on it. Delivering adware, for example, enables them to monetize affected devices while attempting to be innocuous. And while they may be viewed as a nuisance at best, mobile ad fraud- and adware-related incidents became so rampant last year that it cost businesses hefty financial losses.
We found another example of adware’s potential real-life impact on Google Play. Trend Micro detects this as AndroidOS_Hidenad.HRXH. It isn’t your run-of-the-mill adware family: Apart from displaying advertisements that are difficult to close, it employs unique techniques to evade detection through user behavior and time-based triggers.
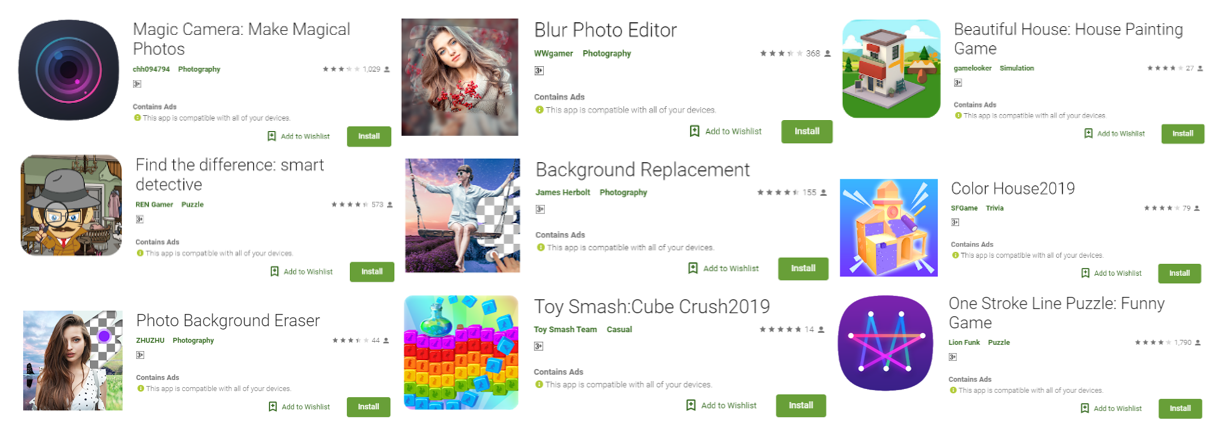
These adware-laden apps posed as 85 photography or gaming applications on Google Play, where they have netted more than eight million in combined downloads. We’ve disclosed our findings to Google, and the adware-embedded apps are no longer on the Play store.
Figure 1. Screenshot of the applications embedded with adware
How the adware checks for user behavior or presence
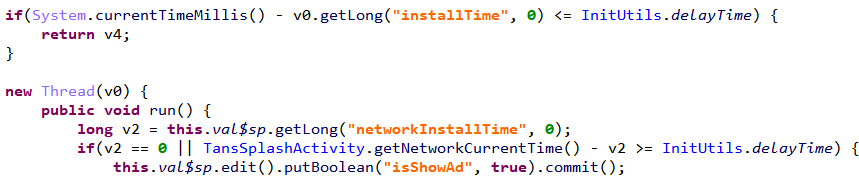
After the app is launched, it first records two timestamps: the current time (the device’s system time) as “installTime”, and the network time, whose timestamp is retrieved by abusing a publicly available and legitimate RESTful application programming interface (API), then stored as “networkInstallTime”.
Figure 2. Code snippets showing how the adware records the current time (top) and fetches the network time (bottom) via a RESTful API
Afterwards, it registers a Broadcast Receiver (an Android component that lets applications send or receive system or application events) for android.intent.action.USER_PRESENT dynamically. This helps monitor if the user is present after the affected device is woken up.
Figure 3. Code snippet showing how the adware registers a Broadcast Receiver
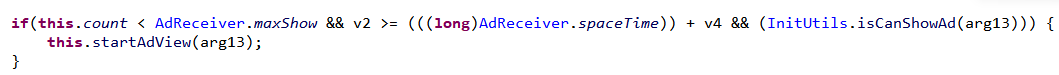
Every time the user unlocks the device, the adware will perform several checks before it executes its routines. It first compares the current time (the device’s system time) with the timestamp stored as installTime; it then compares the current network time (queried via a RESTful API) with the timestamp stored as networkInstallTime. With these, the adware-embedded app can determine if it has been installed on the device long enough, with the default delay time configured to 30 minutes. To a certain extent, using network time can evade time-based detection techniques or triggers employed by traditional sandboxes, as the app’s time settings can be configured by simply using networkInstallTime.
 Figure 4. How the adware-embedded app checks for time via installTime and networkInstallTime
Figure 4. How the adware-embedded app checks for time via installTime and networkInstallTime
If the app has determined that it has been installed for more than 30 minutes, the app will then hide its icon and create a shortcut on the device’s home screen. This routine doesn’t make an apparent difference for the user, unless the device is enabled with a feature that would first notify the user that a shortcut will be created. This would deter the app from being uninstalled by dragging and dropping its icon to the Uninstall section of the screen. To evade detection, the app uses Java reflection — which enables the runtime behaviors of an application to be inspected or modified — and encodes the API strings in base64.
Figure 5. Screenshot of the shortcut being created and displayed in the device’s home screen
Figure 6. Code snapshot showing how Java reflection is used to hide the app’s icon
How the adware displays advertisements
The app also registers another Broadcast Receiver for android.intent.action.USER_PRESENT dynamically to check if the user has unlocked the device. Once conditions are met, advertisements will be displayed on the screen. Similar to how it hides the icon, it also checks for time before displaying advertisements. It also uses installTime and networkInstallTime to identify how long it has been installed on the device. Apart from that, it also checks the last advertisement to make sure that it doesn’t show the same ad too frequently.
While the apps do have actual functionalities of the applications they are posing as, these ads are shown in full screen. Users are forced to view the whole duration of the ad before being able to close it or go back to app itself. Moreover, the frequency of ads being displayed can be remotely configured by the fraudster (the default is five minutes), so it could exacerbate the nuisance for users.
Figure 7. Code snippets showing the Broadcast Receiver registered to display ads (top) and how it performs time checks before showing ads (center, bottom)
Figure 8. Screenshots showing the full-screen advertisements
Figure 9. Screenshots showing reviews of the adware-laden apps
Best Practices and Trend Micro solutions
There are some ways to help lessen the adware’s impact. For example, the latest Samsung Android devices have a feature that restricts the creation of shortcuts on the home screen, which can help users uninstall it. Android 8.0 and later versions also have a function that asks for user confirmation before an application is allowed to create a shortcut. The apps will first hide their icon before generating a shortcut on the home screen; if the shortcut isn’t created, users could be made more aware of its more unusual behaviors. And apart from adopting best practices when securing mobile devices, it also pays to read the app reviews before installing them, as they can help raise red flags if they show suspicious behaviors.
Users can also benefit from security solutions that can thwart stealthy adware, such as the Trend Micro™ Mobile Security™ solution, which blocks malicious apps. End users can also benefit from its multilayered security capabilities that secure the device owner’s data and privacy and that safeguard them from ransomware, fraudulent websites, and identity theft.
For organizations, the Trend Micro™ Mobile Security for Enterprise suite provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability. The Indicators of Compromise (IoCs) are in this appendix.