Updated as of July 27, 2018, 2:08 AM, PDT to include a report about Underminer in November 2017.
Updated as of July 26, 2018, 11:02 PM, PDT to include an updated visualization for Figure 1.
We discovered a new exploit kit we named Underminer that employs capabilities used by other exploit kits to deter researchers from tracking its activity or reverse engineering the payloads. Underminer delivers a bootkit that infects the system’s boot sectors as well as a cryptocurrency-mining malware named Hidden Mellifera. Underminer transfers malware via an encrypted transmission control protocol (TCP) tunnel and packages malicious files with a customized format similar to ROM file system format (romfs). These make the exploit kits and its payload challenging to analyze. Underminer appears to be an exploit kit that was created in November 2017. In this case, however, the exploits used included ones that exploited Flash vulnerabilities and delivered the payloads filelessly until the malware is installed.
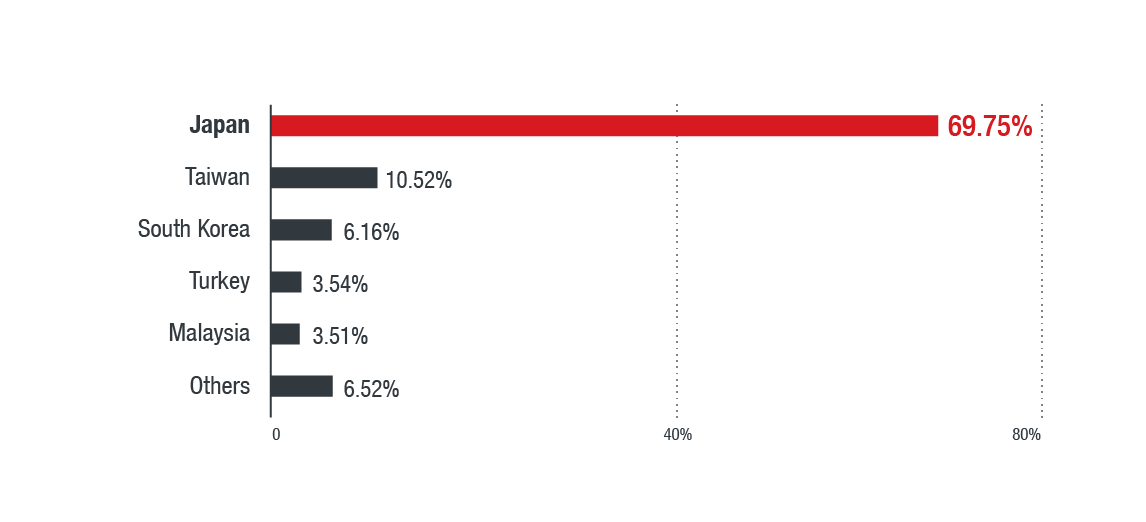
Underminer’s activity in July 17 revealed it is distributing its payloads mainly to Asian countries. Hidden Mellifera emerged in May, and reportedly affected as much as 500,000 machines. Hidden Mellifera’s authors were also linked to the browser-hijacking trojan Hidden Soul reported in August 2017. This correlation indicates that Underminer was developed by the same cybercriminals, as Underminer also pushed Hidden Mellifera. Conversely, Underminer was delivered via an advertising server whose domain was registered using an email address used by Hidden Mellifera’s developers.
Figure 1. Country distribution of Underminer’s activities, from July 17 to July 23
Underminer’s capabilities
Underminer is outfitted with functionalities also employed by other exploit kits: browser profiling and filtering, preventing of client revisits, URL randomization, and asymmetric encryption of payloads. Underminer’s landing page can profile and detect the user's Adobe Flash Player version and browser type via user-agent. If the client’s profile does not match their target of interest, they will not deliver malicious content and redirect it to a normal website instead. Underminer also sets a token to the browser cookie; if the victim already accessed the exploit kit’s landing page, payloads are not pushed and instead delivers an HTTP 404 error message. This prevents Underminer from attacking the same victim and deters researchers from reproducing the attack by revisiting their malicious links. Underminer can also randomize the path in each URL they use in their attacks to evade detection from traditional antivirus (AV) solutions.
 Figure 2. Underminer’s traffic patterns exploiting CVE-2016-0189 (top), CVE-2015-5119, and CVE-2018-4878 (bottom)
Figure 2. Underminer’s traffic patterns exploiting CVE-2016-0189 (top), CVE-2015-5119, and CVE-2018-4878 (bottom)
How Underminer hides its exploits
Underminer uses RSA encryption to protect their exploit code and prevent their traffic from being replayed. Before exploiting the vulnerabilities, Underminer generates a random key and sends it to its command-and-control (C&C) server. This key is then used to encrypt their JavaScript code and exploits, specify the symmetric encryption algorithm in the HTTP response header “X-Algorithm,” and send it back to the victim. The symmetric algorithms they used during our tests were either RC4 or Rabbit.
After receiving the response, the code is decrypted with the generated key and executes it. Underminer also employs RSA encryption during the key’s transmission to further protect it (the random key is encrypted with a public key embedded on their code). It can only be decrypted by a private key, which only Underminer’s operators know. Decrypting the exploit payload cannot be done even if the exploit kit’s network traffic is visible or file samples are at hand. This technique is similar to one used by other exploit kits, notably Angler, Nuclear, and Astrum, but those use the Diffie-Hellman algorithm.
 Figure 3. Snippet of JavaScript code that encrypts the random key with RSA public key
Figure 3. Snippet of JavaScript code that encrypts the random key with RSA public key
Underminer’s exploits
Underminer exploits several security flaws that other exploit kits and threat actors also use:
- CVE-2015-5119, a use-after-free vulnerability in Adobe Flash Player patched in July 2015.
- CVE-2016-0189, a memory corruption vulnerability in Internet Explorer (IE) patched in May 2016.
- CVE-2018-4878, a use-after-free vulnerability in Adobe Flash Player patched in February 2018.
When exploiting these vulnerabilities, a malware loader is executed. Each has similar infection chains but differ in execution. When exploiting CVE-2016-0189, a scriptlet (.sct file) containing JScript code is executed via regsvr32.exe. The JScript code will drop a dynamic-link library (DLL) that will be executed with rundll32.exe, which loads and executes a second-stage downloader from the exploit kit.
When exploiting the Flash vulnerabilities, Underminer will directly execute a shellcode to download an executable without the MZ header. This is akin to the first loader or DLL dropped from the scriptlet. The loader will retrieve the same second-stage downloader then inject it to a newly opened rundll32.exe process. The infection chain for the Flash exploits is actually fileless until the malware is installed in the system. How the bookit and cryptocurrency-mining malware are delivered via an encrypted TCP tunnel by the second-stage downloader is further explained in our technical brief.
 Figure 4. Infection flow of Underminer’s exploits
Figure 4. Infection flow of Underminer’s exploits
Mitigation and Trend Micro solutions
Like other exploits before it, we expect Underminer to hone their techniques to further obfuscate the ways they deliver their malicious content and exploit more vulnerabilities while deterring security researchers from looking into their activities. And given the nature of their operations, we also expect them to diversify their payloads.
Exploit kits may be taking a backseat for now, but Underminer shows that they are still relevant threats. They underscore the real-life significance — and to many businesses, a perennial challenge — of patching. For organizations, exploit kits can entail a race against time. Vulnerabilities can be disclosed at any given time, and their window of exposure can open up unpatched systems — and personal or business-critical data stored in them — to unauthorized access or modification. Here are some best practices:
- Keep systems and their applications updated, and consider virtual patching especially to legacy systems and networks.
- Actively monitor the network; firewalls and employ intrusion detection and prevention systems provide layers of security against malicious traffic.
- Enforce the principle of least privilege: restrict or disable unnecessary or dated applications and components that can be used as entry points.
- Implement defense in depth by employing security mechanisms such as application control and behavior monitoring to prevent unauthorized or malicious applications or processes from executing.
A proactive, multilayered approach to security is key against threats that exploit vulnerabilities — from the gateway, endpoints, networks, and servers. Trend Micro™ OfficeScan™ with XGen™ endpoint security has Vulnerability Protection that shields endpoints from identified and unknown vulnerability exploits even before patches are even deployed. Trend Micro’s endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security protect end users and businesses from these threats by detecting and blocking malicious files and all related malicious URLs.
Find our detailed analysis of Underminer’s infection chain as well as the indicators of compromise in this technical brief.
Acknowledgment to Jérôme Segura for identifying Underminer's earlier activities in November 2017.