Exploit kits may be down, but they’re not out. While they're still using the same techniques that involve malvertisements or embedding links in spam and malicious or compromised websites, their latest activities are making them significant factors in the threat landscape again. This is the case with Rig and GrandSoft, as well as the private exploit kit Magnitude — exploit kits we found roping in relatively recent vulnerabilities to deliver cryptocurrency-mining malware, ransomware, botnet loaders, and banking trojans.
Based on the exploit kits’ latest activities, it appears they and their users are shifting tactics by joining the bandwagon, like capitalizing on cryptocurrency’s popularity or using off-the-rack malware. We expect this to be the status quo this year, given the profitability of using cryptocurrency miners and the convenience of using ready-made malware. We also foresee more exploits that work on other software, such as CVE-2018-8174, which can be exploited via Microsoft Word and Internet Explorer.
 Figure 1: Timeline of GrandSoft, Magnitude, and Rig’s activities from January 1 to June 25, 2018
Figure 1: Timeline of GrandSoft, Magnitude, and Rig’s activities from January 1 to June 25, 2018
Exploit kits' shift in tactics
Rig is currently the most active, and has been so since 2017. It is now in its fourth upgraded version. Several factors contributed to Rig's recent popularity: Angler, the most popular exploit kit at the time, disappeared. Then Neutrino went private, and Sundown silently stopped offering their service and their source code was leaked. By the second half of 2017, only Rig, Disdain, and Terror remained the biggest exploit kits, but the latter two also disappeared by the end of that year.
Magnitude, offered in the underground since 2014, became a private exploit kit in 2016 and accordingly narrowed its scope of targets to Taiwan and South Korea. By October 2017, it expressly targeted users in South Korea with the Magniber ransomware.
GrandSoft, which emerged in 2012 and was last seen in 2014, resurfaced in September 2017. We observed this exploit kit frequently being used by threat actors who also used Rig to distribute their malware. They would also switch exploit kits in between their campaigns. This can be an indication that GrandSoft is also offered as a service in the underground.
 Figure 2: Distribution of attacks from GrandSoft, Magnitude, and Rig exploit kits
Figure 2: Distribution of attacks from GrandSoft, Magnitude, and Rig exploit kits
Incorporating exploits for CVE-2018-8174
Uncovered last April and patched the month after, CVE-2018-8174 is a use-after-free vulnerability in Microsoft Windows’ VBScript engine. It was actively exploited in the wild via malicious Office Word documents. But since the security flaw affects the operating system (OS), it means it can be exploited through other means such as Internet Explorer (IE).
Rig was one of the first exploit kits to take advantage of this, employing exploits that work through IE and Office documents that use the vulnerable script engine. Other exploit kits followed suit. Their implementation is similar to a publicly disclosed proof of concept (PoC), with minor differences in random, variable names.
 Figure 3: Code snippets showing (from left to right) the PoC and how Rig, GrandSoft, and Magnitude exploit CVE-2018-8174 (note the differences in the Overloaded “Class_Terminate” function in VBScript)
Figure 3: Code snippets showing (from left to right) the PoC and how Rig, GrandSoft, and Magnitude exploit CVE-2018-8174 (note the differences in the Overloaded “Class_Terminate” function in VBScript)
 Figure 4: Infection chains of Rig (top), Magnitude (center), and GrandSoft (bottom) for exploiting CVE-2018-8174
Figure 4: Infection chains of Rig (top), Magnitude (center), and GrandSoft (bottom) for exploiting CVE-2018-8174
Exploit kits still deliver multifarious threats
Rig and GrandSoft joined the bandwagon by distributing cryptocurrency-mining malware. These were either delivered directly through the exploit kit or a botnet loader installed by the exploit kit, which then drops a miner. We also observed GandCrab ransomware to be a popular payload, and it’s unsurprising why: It is offered as ransomware as a service that reportedly has over 80 affiliates.
Exploit kits also push botnets and banking trojans. Among them is the Karius banking trojan (detected by Trend Micro as TROJ_KARIUS.A) delivered via Rig. It was found to have an implementation similar to that of the notorious Ramnit, which was also distributed by Rig. At the time we uncovered Karius, we found the malware testing their injection-based attacks on banking- and cryptocurrency-related websites to steal credentials and hijack payments.
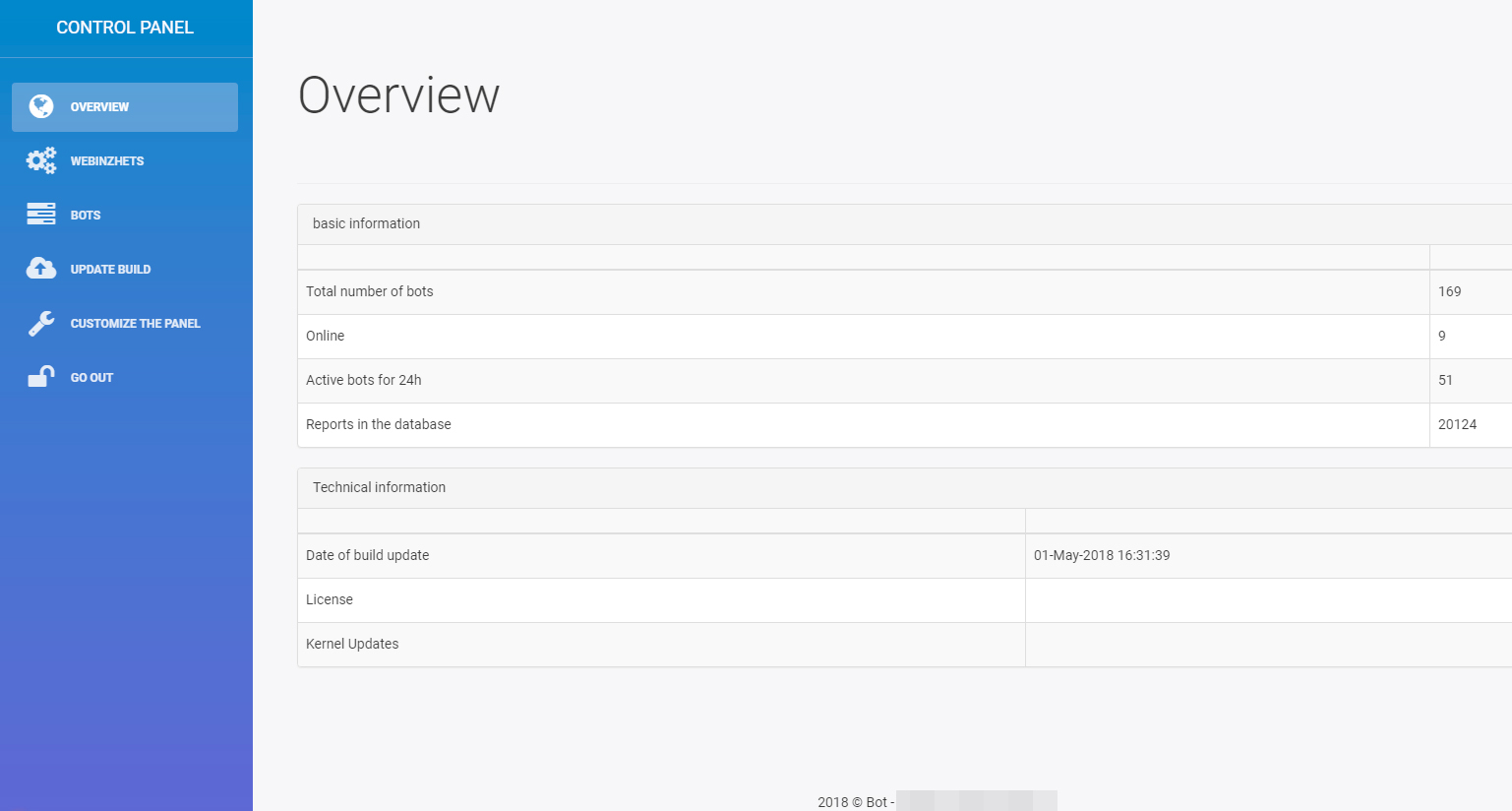 Figure 5. Control panel of the Karius banking trojan
Figure 5. Control panel of the Karius banking trojan
Another is a new loader called “Ascentor Loader” (TROJ_DLOADR.SULQ), used by GrandSoft’s customers. It also displayed the names of two security researchers, although we’re not certain if it’s because they are keeping tabs on GrandSoft’s activities. For now, Ascentor Loader retrieves and helps execute GandCrab ransomware (RANSOM_HPGANDCRAB.SMG).
A month after CVE-2018-8174 was patched, GrandSoft — known for using Internet Explorer-only vulnerabilities — updated its exploit for CVE-2016-0189 to that of CVE-2018-8174. Their implementation appears to be a modified version of the PoC.
 Figure 6: Notable strings such as “Ascentor Loader” (top) and the names/handles of the researchers (top, bottom; highlighted and blurred)
Figure 6: Notable strings such as “Ascentor Loader” (top) and the names/handles of the researchers (top, bottom; highlighted and blurred)
Rig’s payload when exploiting CVE-2018-8174 is a Monero miner. It’s not their vulnerability of choice, as they also retained their exploits for CVE-2016-0189 and CVE-2015-2419 (both of which affect Internet Explorer) as well as CVE-2018-4878, a remote code execution vulnerability in Adobe Flash.
Apart from adding an exploit for CVE-2018-8174, we also saw Rig’s customer/s using Kardon Loader (TROJ_KARDONLDR.A) — peddled in hacking forums — to download a Monero miner (COINMINER_MALXMR.SM4-WIN32). This reflects how Rig is a rather active exploit kit, as we’ve seen it use different downloaders like QuantLoader and Smoke Loader to retrieve payloads such as the Pony/ZeuS banking trojan, ransomware, and cryptocurrency miners.
 Figure 7: Advertisement for Kardon Loader (left) and a snapshot of a control panel of a botnet that uses Kardon Loader (right)
Figure 7: Advertisement for Kardon Loader (left) and a snapshot of a control panel of a botnet that uses Kardon Loader (right)
A few days after Rig updated its exploit, Magnitude also implemented its own exploit for CVE-2018-8174 to deliver the Magniber ransomware. This replaced their previous modus of using an exploit for CVE-2016-0189, a memory corruption flaw in IE. As with the case in their previous campaigns, Magnitude also limits their targets to South Korea. This could mean that cybercriminals are trying to avoid detection and increase their infection rate or stay under law enforcement and security researchers’ radars.

Figure 8: Code snippet showing how Magnitude exploits CVE-2018-8174
Exploit kits are still relevant threats
The arrests of their operators, a dearth of zero-day vulnerabilities, and vendors proactively improving the security of their products contribute of the decline of exploit kits. They are still a relevant threat, however. Exploit kits are opportunistic: The fact that they’re still exploiting old vulnerabilities, for instance, implies that they’re still having some success with them. Their creators can easily integrate new vulnerabilities or rehash PoCs as soon as they become available.
Indeed, exploit kits may have plateaued, but that doesn’t mean organizations and end users have to be complacent. In 2017, for instance, there were 119 zero-day vulnerabilities — for exploit kits, it only takes one to get a foothold into the system. Apart from patching (or employing virtual patching for legacy systems), organizations can further mitigate exploit kits by enforcing more robust patch management policies to determine which security gaps need to be addressed immediately. Applying the principle of least privilege and implementing defense in depth also helps — from employing firewalls and intrusion detection and prevention systems to incorporating application control and behavior monitoring. Users should also be more prudent: Back up your personal and corporate data and think before you click.
Trend Micro Solutions
A proactive, multilayered approach to security is key against threats that exploit vulnerabilities — from the gateway, endpoints, networks, and servers. Trend Micro™ OfficeScan™ with XGen™ endpoint security has Vulnerability Protection that shields endpoints from identified and unknown vulnerability exploits even before patches are even deployed. Trend Micro’s endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security protect end users and businesses from these threats by detecting and blocking malicious files and all related malicious URLs.
Indicators of Compromise (IOCs)
Related hashes (SHA-256):
- 69ec63646a589127c573fed9498a11d3e75009751ac5e16a80e7aa684ad66240 — Ascentor Loader (TROJ_DLOADR.SULQ)
- f75c442895e7b8c005d420759dfcd4414ac037cf6bdd5771e23cedd73693a075— GandCrab ransomware (RANSOM_HPGANDCRAB.SMG)
- aca8e9ecb7c8797c1bc03202a738a0ad586b00968f6c21ab83b9bb43b5c49243 — Kardon Loader (TROJ_KARDONLDR.A)
- 5f7d3d7bf2ad424b8552ae78682a4f89080b41fedbcc34edce2b2a2c8baf47d4 — Karius (TROJ_KARIUS.A)
- 24d17158531180849f5b0819ac965d796886b8238d8a690e2a7ecb3d7fd3bf2b — Magniber ransomware (RANSOM_MAGNIBER.Q)
- a0bff2cf5497d9b36c384e2410cb63f17b127e1b10d76263bb37eced93a73b66— Monero miner (COINMINER_MALXMR.SM4-WIN32)
Malicious domains and IP addresses related to Rig exploit kit
- 188[.]225[.]37[.]242 (Rig EK; also where Kardon Loader was downloaded)
- 193[.]23[.]181[.]154
- 193[.]23[.]181[.]154/crypto/?placement=198395354
- hxxp[://193.23.181[.154/dl/miner/ipodservice2.exe (Monero Miner)
- hxxp[://proxyservice[.site/updates/gateway[.]php (Karius)
Malicious domains and IP addresses related to Magnitude exploit kit
- [ID].bitslot[.]website (Magniber Payment Server)
- [ID].carefly[.]space (Magniber Payment Server)
- [ID].farmand[.]site (Magniber Payment Server)
- [ID].trapgo[.]host (Magniber Payment Server)
- 54[.]37[.]57[.]152 (Magniber Payment Server)
- 64[.]188[.]10[.]44 (Magniber Payment Server)
- 139[.]60[.]161[.]51 (Magniber Payment Server)
- 149[.]56[.]159[.]203 (Magnigate Step 1)
- 167[.]114[.]191[.]124 (Magnitude EK)
- 167[.]114[.]33[.]110 (Magnigate Step 2)
- 185[.]244[.]150[.]110 (Magniber Payment Server)
- fedpart[.]website (Magnigate Step 2)
- addrole[.]space (Magnitude landing page)
- taxhuge[.]com (Magnigate Step 1)
Malicious domains and IP addresses related to GrandSoft exploit kit
- 91[.]210[.]104[.]247/debug[.]txt
- 91[.]210[.]104[.]247/putty.exe (GandCrab Ransomware)
- 200[.]74[.]240[.]219 (BlackTDS IP)
- carder[.]bit (GandCrab C&C)
- ethical-buyback[.]lesbianssahgbrewingqzw[.]xyz
- ethical-buyback[.]lesbianssahgbrewingqzw[.]xyz/masking_celebration-skies
- papconnecting[.]net/wp-content/traffic[.]php
Hat tip to Kafeine for sharing IoCs related to the Magnitude exploit kit.


