Introduction
Trend was excited to support the US Cybersecurity and Infrastructure Security Agency’s (CISA) Secure by Design pledge in early 2024, as we’ve focused purely on cybersecurity for over 35 years. Ensuring our products are secure is just as important as making sure our customers are secure from adversaries targeting them. As a pioneer in cybersecurity, we have been innovating and developing products across a wide range of areas, which requires our research and development teams to deal with adversaries regularly targeting our products for weaknesses and security holes. As such, we have a lot of experience building safeguards within these products. Below is our progress to date on the goals laid out in the pledge. Note that this is an ongoing process.
Goal |
Status as at December 2024 |
Drive Adoption of Multi-Factor Authentication |
On Track |
Reduce use of default passwords |
Completed |
Reduce common classes of vulnerabilities |
On Track |
Security Patches |
On Track |
Publish a Vulnerability Disclosure Policy |
Completed |
CVE’s |
Completed |
Evidence of Intrusions |
Completed |
1. Drive Adoption of Multi-Factor Authentication
- "Within one year of signing the pledge, demonstrate actions taken to measurably increase the use of multi-factor authentication (MFA) across the manufacturer’s products."
Progress
With adversaries utilizing credential theft in many attacks, MFA has shown to be a valuable security control to combat this threat. As such, Trend has been implementing an MFA login option in our platform, Trend Vision One™ for some time now.It is currently available on an opt-in basis, and we are plan to implement this by default in 2025.
2. Reduce the use of default passwords
- “Within one year of signing the pledge, demonstrate measurable progress towards reducing default passwords across the manufacturers’ products.”
Progress
All Trend products require a unique, strong password to be generated during initial installation.
3. Reduce common classes of vulnerabilities
- “Within one year of signing the pledge, demonstrate actions taken towards enabling a significant measurable reduction in the prevalence of one or more vulnerability classes across the manufacturer’s products.”
Progress
Trend has been reducing many of the vulnerability classes that can be exploited by adversaries in attacks. Trend Micro’s Zero Day Initiative (ZDI) is the world’s leading vendor-agnostic bug bounty program, and has been disclosing bugs across many vendors, operating systems, and applications for decades. It has paid out more than $25M for bugs and disclosed over 13,000 advisories since 2005. This program has been instrumental in keeping the world safe from adversaries using 0-days by helping vendors disclose and patch their vulnerabilities. ZDI also has bounties for Trend products, which provides another avenue for us to discover bugs besides our own internal programs. Over the past 9 years, we’ve seen submissions across the following class types in which we are trying to reduce their prevalence.
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') |
|
Improper Link Resolution Before File Access ('Link Following') |
|
Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') |
We have a goal of reducing these classes by 50% in 2025.
4. Drive improved customer patching hygiene
- “Within one year of signing the pledge, demonstrate actions taken to measurably increase the installation of security patches by customers.”
Progress
One of the biggest changes in technology over the years has been the shift towards Software as a Service (SaaS), which has allowed vendors to patch products in the cloud versus requiring customers to patch on-premise products. This has significantly improved the mean-time-to-patch. Trend has developed many of its products to be SaaS-based over the years, but we still have a significant number of customers using our on-premise products. In many cases, this is a requirement due to regulations, sovereignty concerns, or privacy. We continue to look to improve our on-premise customer experience with patching by providing a number of options:
- Auto notice of patches
- Auto download of patches
- Staggered patch option (ring deployment) where the customer can identify which systems receive updates and when
- Ability to designate which update a system can utilize (p, p-1, p-2, etc)
Another aspect we are improving for our customers is with support of our ZDI and vulnerability research teams, we’re now providing customers using our Vision One platform more detailed information about vulnerabilities disclosed that affect them. We’re providing more context and risk level of each bug, which in turn allows them to make a much more informed decision on how to manage the patch or virtual patch. This will help their patch management program immensely and allow them to focus on higher risk vulnerabilities.
We will continue to work to improve this area and offer options. Many of our legacy, on-premise customers are being exposed to the value that a SaaS offering brings, but we know many will continue to utilize our on-premise offerings. As such, we will continue to strive to improve their update process and educate them on the benefits of patching sooner than later.
5. Publish a Vulnerability Disclosure Policy
- “Within one year of signing the pledge, publish a vulnerability disclosure policy (VDP) that authorizes testing by members of the public on products offered by the manufacturer, commits to not recommending or pursuing legal action against anyone engaging in good faith efforts to follow the VDP, provides a clear channel to report vulnerabilities, and allows for public disclosure of vulnerabilities in line with coordinated vulnerability disclosure best practices and international standards.”
Progress
Trend Micro has always prioritized product security and has had a public vulnerability disclosure policy since 2017, which coincides with the year Trend became an official CVE Numbering Authority (CNA). (Note, ZDI is also an official CNA) It is updated on a regular basis as needed, and the most recent update to our policy at www.trendmicro.com/vulnerability reflects some of our commitments to the pledge:
- We have added specific language that clearly articulates that it’s Trend general policy not to pursue or recommend legal action against responsible security researchers or others that identify and report vulnerabilities to us in good faith. We strongly believe that a robust and healthy research community ultimately helps organizations stay one step ahead of malicious actors.
- We’ve also publicly acknowledged that we are one of the original signatories to the pledge, reinforcing our overall commitment.
Below is a list of public organizations in which Trend supports and is a member of:
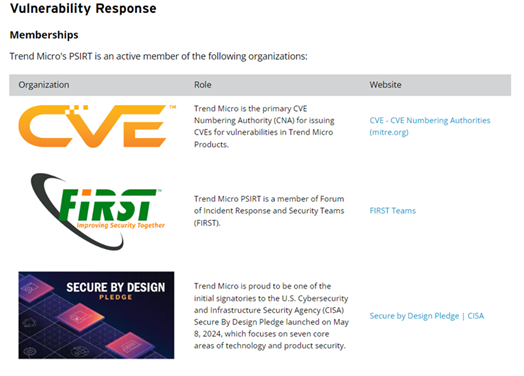
The Trend Micro Zero Day Initiative also discloses advisories for all bugs (patched or not patched) that are sourced from 16,000+ external researchers and our own internal researchers who identify new bugs. This includes Trend Micro bugs we offer bounties for and develop virtual patches for customers. Note, ZDI gives vendors 120 days to develop a patch for any bugs shared with them through their vulnerability disclosure policy. The currently published as well as upcoming advisories can be found here: https://www.zerodayinitiative.com/advisories/published/
Trend Micro has also a published Trust Center where we share many of our company’s policy’s supporting more secure operations, data privacy, and other critical areas. https://www.trendmicro.com/en_us/about/trust-center.html
6. Provide transparency on vulnerabilities
- “Within one year of signing the pledge, demonstrate transparency in vulnerability reporting by including accurate Common Weakness Enumeration (CWE) and Common Platform Enumeration (CPE) fields in every Common Vulnerabilities and Exposures (CVE) record for the manufacturer’s products. Additionally, issue CVEs in a timely manner for, at minimum, all critical or high impact vulnerabilities that either require actions by a customer to patch or have evidence of active exploitation.”
Progress
As of November 2024, Trend Micro now includes CWE and CPE assignments on every new CVE issued against our products. CWE identifiers and CVSS scores are also now prominently included on every publicly disclosed vulnerability security bulletin.
7. Deliver improved logging and monitoring for customers
- “Within one year of signing the pledge, demonstrate a measurable increase in the ability for customers to gather evidence of cybersecurity intrusions affecting the manufacturer’s products.”
Progress
All Trend products offer customers both audit and event logs to utilize in the case of an intrusion. The length of time these are available depends on the type of solution a customer has. SaaS-based solutions can offer up to 6 months, but on-premise are at the discretion of the customer.
Conclusion
Trend Micro is happy to support the US Cybersecurity and Infrastructure Security Agency’s efforts to promote Secure by Design among technology manufacturers. We continue to support other initiatives of CISA like their Known Exploited Vulnerabilities catalog where we contribute new 0-days found by Trend Micro researchers. We hope more manufacturers join the pledge to support improved software development policies within their organization and will help make the world safer. Trend will continue to improve our own software development and help our customers be more secure now and in the future. We will update this page with any new progress we make.

