What Is Phishing?
Stop more threats with Trend Micro Email Security—advanced protection for your inbox!
Definition of phishing
Phishing is a type of cyber-attack involving sending generic emails by cybercriminals pretending to be legitimate. These emails contain fraudulent links to steal user's private information. Phishing attacks are most effective when users are unaware this is happening.
Phishing is an attack method that has been around since the mid-1990s. It started when a group of young people engineered AOL’s chat room feature to impersonate AOL administrators. They stole credit card numbers from other users to ensure they would always have free AOL access.
AOL’s “new member chatroom” was designed for users to receive site access assistance. The hackers created what appeared to be valid AOL administrators’ screen names like “BillingAccounting,” and told users that there were issues with their account.
The user was asked to provide a card number to get the issues resolved. The criminals then used the card numbers to pay for their own accounts. While the term “phishing” was coined to describe this attack and others like it, it has now come to be associated primarily with email scams. Phishing scams continue to this day in abundance. According to the Verizon 2021 Data Breach Investigations Report (DBIR), 36% of breaches involved phishing.
Since phishing primarily relies on social engineering, it is critical for all users to understand how the attackers work to exploit human nature. First, social engineering is a con that hackers use to convince users to do something they wouldn’t normally do.
Social engineering could be as simple as someone with full hands asking that a door be opened. Similarly, a social engineering attack can start with someone dropping USB thumb drives labeled “family photos” in a parking lot. These USB thumb drives could contain malware that gets installed onto a computer, compromising security in some way. This is known as baiting.
Phishing is primarily used in reference to generic email attacks. This is when an attacker sends out emails to as many addresses as possible, using common services like PayPal or Bank of America.
The email states the account is compromised and prompts you to click on a link to verify that the account is legitimate. The link will usually do one of two things, or both:
- It can take you to a malicious website that looks similar to the authentic site, for example, “www.PayPals.com” versus “www.PayPal.com.” Note the extra “s” on the first URL. Once you go to the malicious website, the hacker can capture your user ID and password when you attempt to log in.
The hacker now has access to your bank account and is able to transfer money anywhere. There is a second possible benefit, though. The hacker might now have a password that can be used for your other accounts, including Amazon or eBay. - It can infect your computer with downloaded malicious software called malware. Once installed, the software can be used for future attacks. The malware could be a keystroke logger that captures logins or credit card numbers or it could be ransomware that encrypts drive contents and holds them for ransom, usually in the form of Bitcoin.
It is possible at that point for the hacker to use the infected computer to mine for Bitcoin. This can be done when you are not on the computer, or the malware could lock you out of part of the CPU’s capability at all times. The hacker can now successfully mine for Bitcoin and your computer typically functions more slowly.
Phishing has evolved throughout the years to include attacks that address different types of data. In addition to money, attacks can also target sensitive data or photos.
Phishing attacks
A phishing attack is the action or set of actions a hacker undertakes to exploit you. Email phishing schemes are often easy to spot due to grammar and/or spelling errors in the emails. Attackers are becoming technically sophisticated, however, and new attacks focus on exploiting human emotions to get you to engage, including fear, outrage, and curiosity.
The attack against RSA in 2011 was targeted at just four people within the organization. The email was not very sophisticated, but it was successful because it targeted the right people. The email, entitled “2011 Recruitment plan.xls” was designed to pique the interest of those individuals and would not necessarily be of interest to others in the organization.
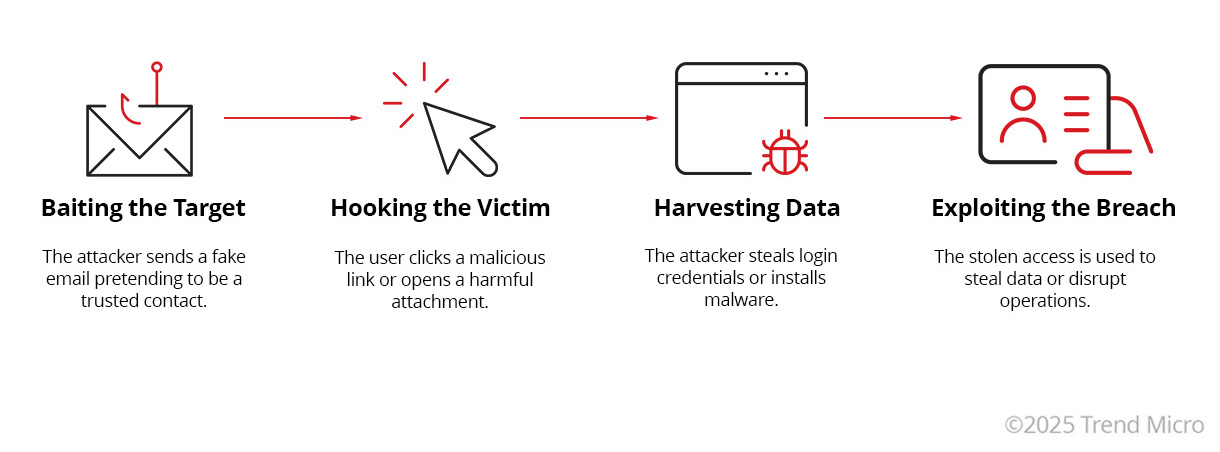
Types of phishing
There are many different types of phishing attacks. These include the classic email attack, social media attacks, and portmanteau-named attacks like smishing and vishing.
Phishing
Phishing involves hackers sending mass emails that appear to come from legitimate sources, such as banks or online services. The goal is to trick recipients into clicking on links that lead to fake websites where they are asked to enter personal information like passwords or credit card numbers.
Spear Phishing
Spear Phishing is a targeted form of phishing aimed at specific organisations or individuals. Hackers will personalise messages using information about the target to increase credibility, making it more likely that the victim will interact and provide sensitive data.
Whaling
Whaling targets high-ranking executives or decision-makers within organizations, such as CEOs or CFOs. These attacks often involve tailored messages that appear to be related to business operations, aiming to gain access to sensitive corporate data or financial information.
Internal Phishing
Internal phishing occurs when hackers compromise an employee's email account and use it to send phishing messages within the organization. These emails appear trustworthy since they come from a known internal source, making it easier to trick recipients into revealing confidential information.
Vishing
Vishing, or voice phishing, involves attackers impersonating trusted entities over the phone. The scammers may claim to be from a bank or government agency, attempting to coax the victim into revealing sensitive information like Social Security numbers or account details.
Smishing
Smishing uses text messages (SMS) to trick victims. Attackers may send fake alerts from banks, delivery companies, or government agencies, urging recipients to click on a link or respond with personal information.
Social Media Phishing
In social media phishing, hackers will create fake profiles or compromise legitimate accounts to reach victims. They send messages or post links that lead to phishing sites or ask for personal information under the guise of friendship or business interest.
Pharming
Pharming redirects users from legitimate websites to fraudulent ones without their knowledge. By corrupting DNS settings or infecting devices, hackers can silently redirect users to phishing sites that collect login credentials and other personal information.
Phishing examples
We observed a phishing campaign dubbed Heatstroke, based on a variable found in their phishing kit code. It demonstrates how far phishing techniques have evolved with its use of more sophisticated techniques such as steganography.
The way Heatstroke's operators do research on their potential victims is notable. They aim for their victim's private email addresses, which they most likely collected from the victim's own address list, which also includes managers and employees in the technology industry. Private email addresses are more likely to be hosted on free email services with lax security and spam filtering. These free email accounts could thus serve as better starting points for attackers to reconnoiter and gather intelligence on their targets compared to business emails, which are typically more secure.
The stolen credentials are sent to an email address using steganography (hiding or embedding data into an image). Over the course of our research, we were able to capture two similar phishing kits — one for Amazon users and the second for stealing PayPal credentials.
The two kits’ tactics and techniques were similar, from the website hosting the phishing kit and the type of information they stole to the masking techniques used. Both kits also seemingly end in the same user verification phase. These similarities could mean that they have the same origin. The similarity could also be buoyed by the timing and scope of the attacks that used these kits, as they were delivered to the same victim.
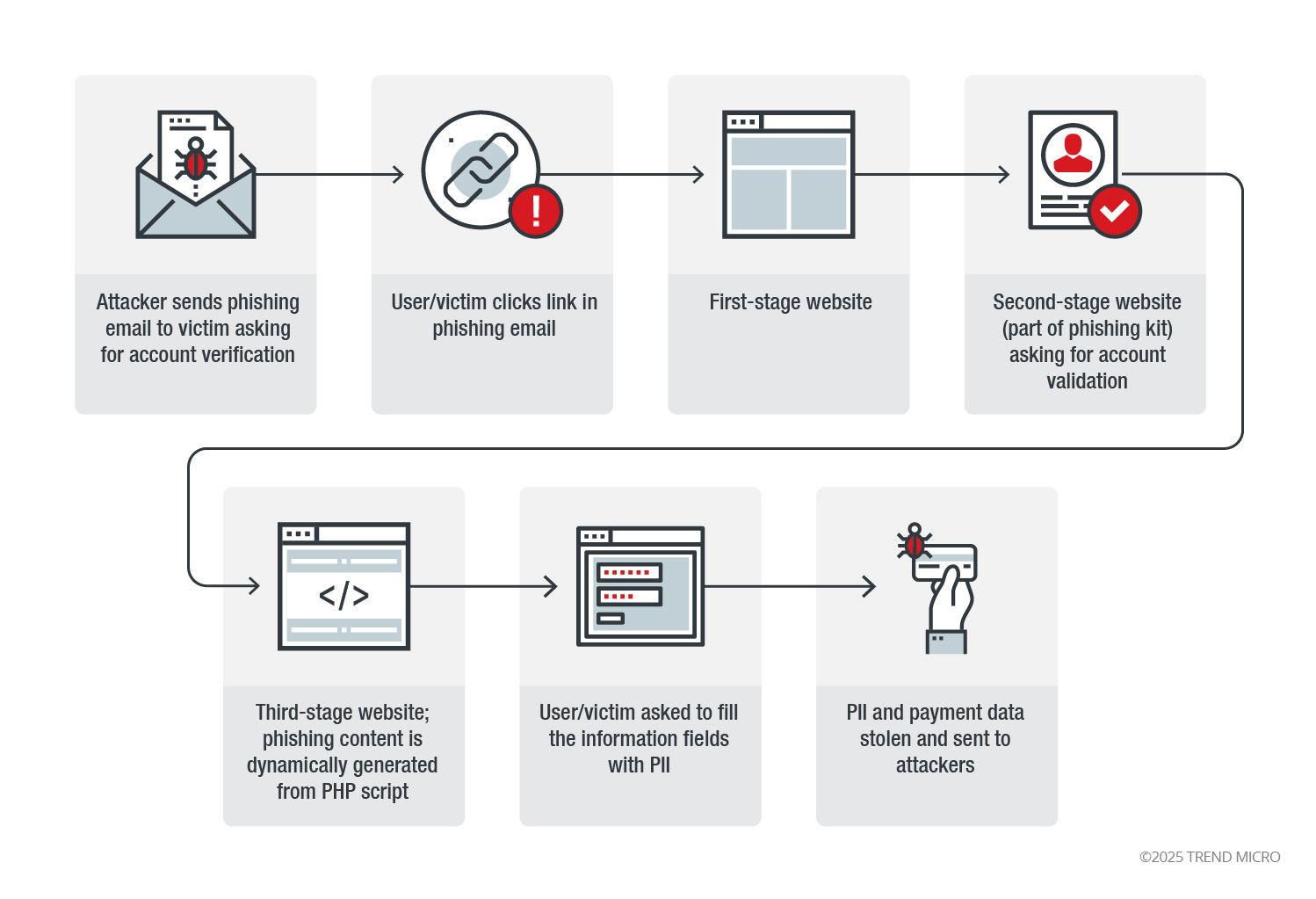
Figure 1. Infection chain of Heatstroke’s phishing attack; note that the infection chain could change depending on user/behavior properties
Click here to learn more about this multi staged phishing attack
How do you prevent phishing attacks?
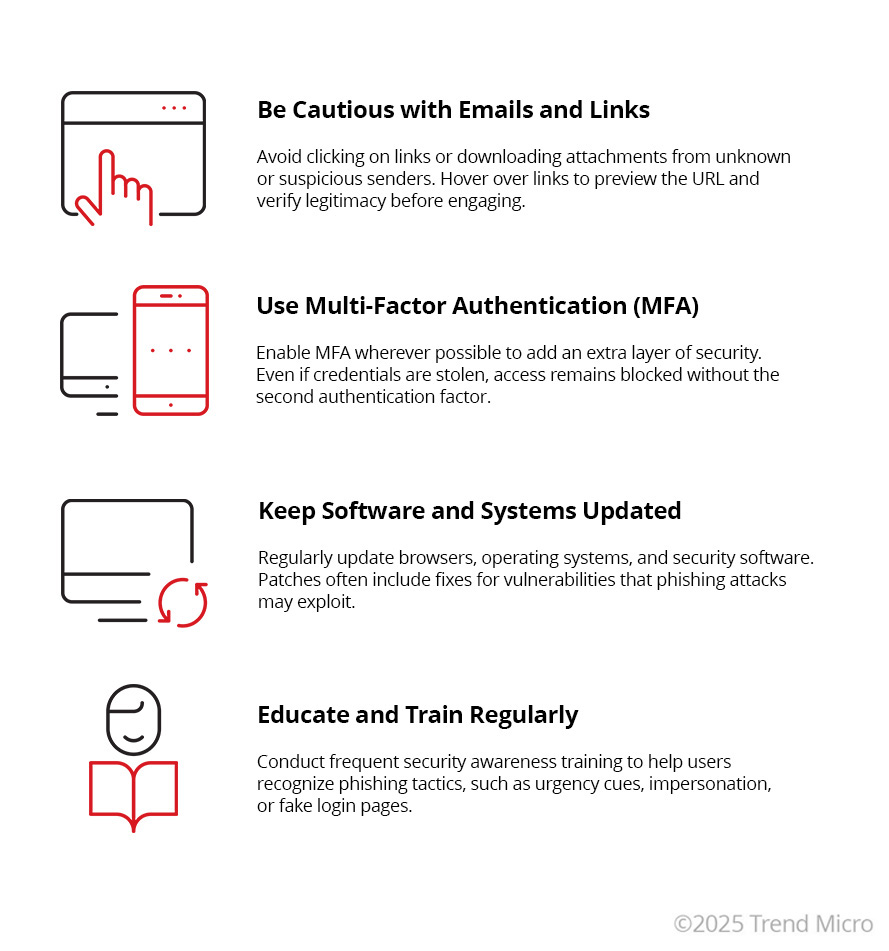
There are some very specific things you can do as an individual to protect yourself:
- Enable two-factor authentication (2FA) on any qualifying account
- Use anti-malware programs
- Use firewalls
- Be suspicious of pop-ups and pop-unders
- Be suspicious of email attachments from known and unknown sources
- Be suspicious of text messages or IMs from known and unknown sources that want you to click through to some destination or result in a query about your personal information
- Don’t give out your personal information
In addition to the recommendations above, an organization should do the following:
- Filter for phishing email and malicious web traffic at the gateway
- Authenticate email senders using Domain-Based Message Authentication, Reporting, and Conformance (DMARC)
- Filter for phishing emails based on sender and content, and analyze URLs and attachments for malicious attributes using static and dynamic techniques
- Employ advanced filtering techniques that use artificial intelligence (AI) to spot business email compromise (BEC) and credential-stealing attacks
- Prevent internal phishing attacks with a service-integrated security solution for your cloud or on-premises email platform using APIs. These are available for Microsoft 365, Google G Suite, Microsoft Exchange Server, and IBM Domino server
Trend Micro Email Security Solution
Trend Vision One™ Email and Collaboration Security delivers industry-leading protection against advanced threats targeting email and collaboration platforms. It stops phishing, business email compromise (BEC), ransomware, and other targeted attacks with AI-powered threat detection and dynamic sandbox analysis.
By validating sender identity, scanning URLs and attachments in real time, and leveraging cross-generational threat defense techniques, it provides comprehensive visibility and control across your cloud-based communication channels.
Related information about Smishing

Worldwide 2023 Email Phishing Statistics and Examples
Explore the need for going beyond built-in Microsoft 365 and Google Workspace™ security based on email threats detected in 2023.

Email Security Best Practices for Phishing Prevention
Explore the latest phishing trends and email security best practices to enhance your email security and reduce cyber risk.