
Learn more about zero trust:
- A Secure Access Service Edge (SASE) Guide for Leaders
- What is Secure Web Gateway’s (SWG) Role in Zero Trust?
- Reduce SaaS App Risks with Cloud Security Broker & Zero Trust
- Data Exfiltration Prevention with Zero Trust
Modern businesses require a modern approach to network security and access control solutions that deliver centralized control and unified visibility across hybrid and remote environments.
It used to make sense to route every network connection through a central data center since it hosted all your business applications. But now, most of your apps live in the cloud—or multiple clouds.
VPNs, which were designed for traditional network architectures, can no longer provide the protection needed when working and building in a hybrid- or multi-cloud environments. In addition, they add unnecessary complexity, impact performance, waste resources, and are costly to maintain.
Continuing our deep dive into Secure Access Service Edge (SASE), this article looks at why 63% of organizations are making the move from Virtual Private Network (VPN) to Zero Trust Network Access (ZTNA) to reduce cyber risk across the attack surface as a part of a broader zero trust strategy.
What is ZTNA?
Zero Trust Network Access is a user and app-centric technology that secures remote access between specific applications and identities based on granular, defined access control polices both in the cloud and on-premises. With ZTNA, authorized users are granted seamless, secure connectivity without being placed on the network or exposing apps to the internet, which improves network security and the user experience.
What is zero trust?
Zero trust is a security model that assumes all devices and users, including those inside the network perimeter, should be untrusted and therefore must be verified before being granted access to resources.
SASE and zero trust can work together to secure and optimize network connections for users and devices. This is because of zero trust’s is ability to authenticate and authorize access to resources based on the principle of "never trust, always verify." This combination of SASE and zero trust provides a more comprehensive and secure network architecture that can protect against both external and internal threats.
ZTNA and SASE
SASE architecture restricts access of resources, including mobile users, sites, cloud applications, and data centers. One of the key elements is ZTNA, which on its own protects one part of the network “plumbing” that is used within a business. But when used in a SASE architecture, it provides extended security services for a user’s contextual identity (including location and device security posture) to dictate policy controls for data movement.
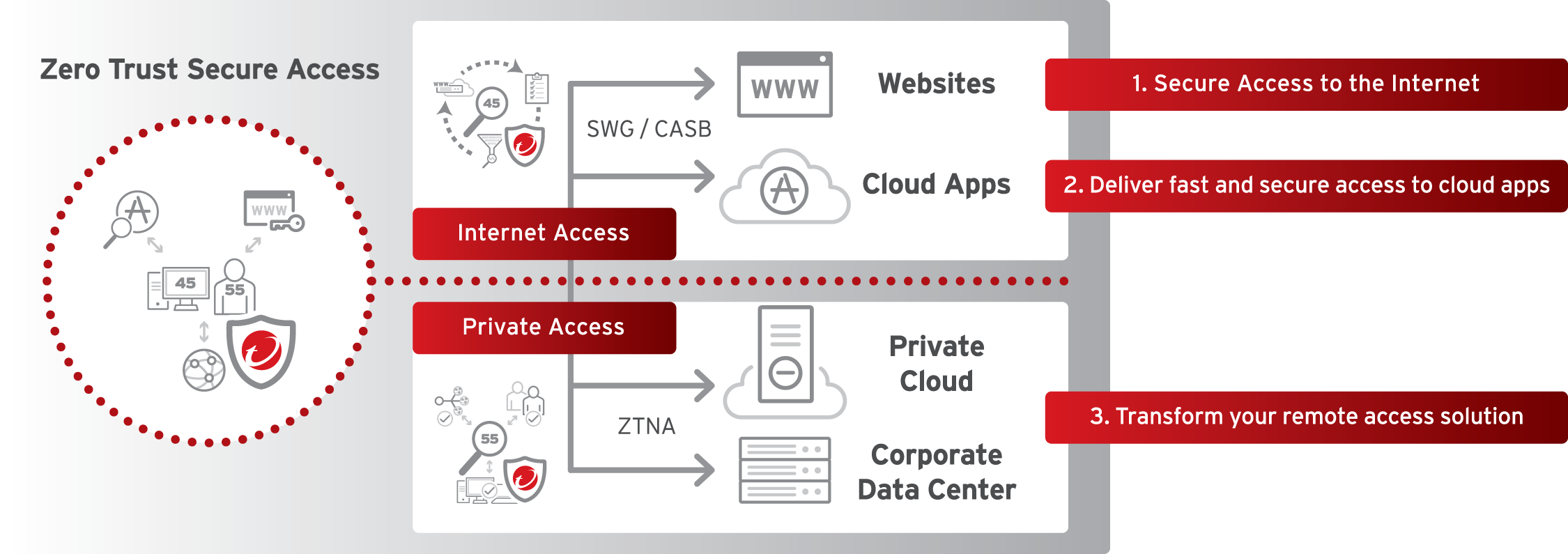
For example, as modern businesses migrate to SaaS applications and cloud services, they need to control data movement for their remote workers who are accessing cloud applications hosted in private and public networks. This requires granular policy controls enabled by adopting ZTNA and SASE capabilities to get the right data to the right people.
ZTNA vs. VPN
While VPNs served their purpose in a strictly on-premises world, the accelerated migration to the cloud has revealed its limitations and new technologies are being ushered in. Amongst those, ZTNA is largely considered the evolution of VPN remote access due to several factors:
Reducing the attack surface
VPNs extend the network fabric across multiple differently located sites, which now includes notoriously insecure home offices. This expands the organization’s attack surface by connecting secure and unsecured networks together, including home networks.
So, while a remote employee may be only accessing legitimate work apps, other users/devices could spread malware through an unsecured machine connected to the VPN. Considering that 82% of data breaches involved a human element, the more devices and users with access to an organization’s entire network, the higher the cyber risk.
On the other hand, ZTNA allows more granular control over who can access what. It operates on the principle of least privilege, thereby only establishing specific application-to-user connections—creating a more defined perimeter for the attack surface.
Furthermore, unlike a VPN, which exposes an application’s backend to the connected user, ZTNA continuously verifies the trust of users and devices, and only grants access to the web-portal frontend. Thus, even if a user is compromised, the cybercriminal won’t have access needed to leapfrog their attack across the attack surface.
Minimizes cyber risk
VPNs approach authentication as “one and done”, meaning after a user is granted access to the network, they can remain connected for a long (or indefinite) amount of time so long as your credentials are valid. In theory, someone could steal your laptop and have immediate access to the organization’s network.
ZTNA goes beyond just confirming credentials by:
- Validating access at a point-in-time by checking that patches are installed, the endpoint is domain-connected, etc.
- Authenticating the user’s identity via multi-factor authentication (MFA)
- Checking what they’re authorized to use and other user behavior markers like: what time do they usually work between, what location do they usually work from, etc.
- Utilizes the pillars of zero trust, as seen below:
After the connection is granted, ZTNA continuously assesses the risk by running user identity checks as well as monitoring the health of the device in line with configured security policies. For example, if a device used by an account is suddenly dumping memory files using PowerShell, the risk score will increase, and the connection will be severed. Similarly, if malware if detected and there’s a change in the device’s security posture, access will be terminated instantly.
Improved scalability
Since VPNs provide a user with access to everything, businesses needed a certain bandwidth to function without impacting workflows. Legacy VPN technology that connects traffic to an on-premises VPN firewall or concentrator aren’t equipped to scale or deliver the user experience needed in an increasingly agile business world.
With ZTNA, the specific application-to-user connection doesn’t require the bandwidth that VPNs do. It is designed for rapid scale while maintaining high-performance availability and consistent delivery needed for modern security solutions without negatively impacting user experience.
Tips for evaluating ZTNA technology
Swapping out VPN for ZTNA can seem overwhelming, especially considering the sheer number of apps, devices, and users that businesses must contend with. Here are three tips for evaluating ZTNA technology:
VPN replacement is a journey
We strongly advise against the rip-and-replace approach. Think of updating your remote access solution as a journey, like that of migrating apps from on-prem to the cloud. Start by migrating low-risk apps to the ZTNA solution to identify any issues and then ramping up (at rate your business can handle) until the VPN can be retired.
Leverage automation
Manual configuration can seem like a Herculean task for security teams of any size given each app needs to be inputted. Look for a ZTNA solution that leverages automatic app discovery, which can look at network traffic and identify where the app is hosted and how it can be accessed. It can also surface any pesky shadow IT that may have gone unnoticed while using a VPN.
Check the bottom line
Lastly, beware of “hidden” costs that can spiral out of control. Many ZTNA suppliers have adopted the same pricing model as the VPN but worse; not only do you have to pay for each user, but also for each app, and if you’re working in the cloud, you’re charged a transfer fee as well. Look for a vendor with consumption-based billing that only charges for the identity, regardless of if a user is connecting with multiple devices.
Modernizing the SOC with ZTNA
Part of SOC modernization is the ability to provide insights into what’s happening across the IT infrastructure. Since VPNs grant access to everything, the lack of context around risky user, device, and application behavior leads to poor quality, unactionable information.
A ZTNA solution can serve up more granular information because it’s directly connected to the endpoint and the app and continuously inspecting all traffic. This helps security operations teams establish a baseline for risk, further minimizing any potential damage from unauthorized access.
Next steps
Convergence is key for stronger security. While ZTNA can run independently, it’s stronger when applied to the SASE architecture, working in combination of a zero trust strategy. Integrating ZTNA with secure web gateways (SWG) and cloud access security brokers (CASB) leads to more streamlined, powerful security across the attack surface.



