Trend Micro Vision One™ is at the core of our unified cybersecurity platform, delivering powerful, industry-leading extended detection and response (XDR), centralized visibility and risk insights. Vision One integrates with Palo Alto Networks Cortex™ XSOAR to drive automated response to incidents uncovered by Vision One. This simplifies investigations and response for SOC analysts, enabling them to easily execute necessary steps all from within Cortex™ XSOAR via commands and playbooks.
At the core of this integration is the creation of Cortex™ XSOAR incidents from Trend Micro Vision One™ workbench alerts.

Having the incident details available in the Cortex™ XSOAR platform enables analysts to execute a series of manual or automated actions through the Trend Micro Vision One™ platform in response to a potential threat. In the initial release of this content pack, we have made the following response actions available:
| Add item to exception list | Adds domains, IP addresses, URLs, or file hashes to the known good list |
| Remove item from the exception list | Removes domains, IP address, URLs, or file hashes from the known good list |
| Add item to suspicious objects list | Adds domains IP addresses, URLs, or file hashes to the suspicious object list and specifies the appropriate action to take if discovered (log or block) |
| Remove item from suspicious objects list | Removes domains IP addresses, URLs, or file hashes from the suspicious object list |
| Collect files | Collects the specified file from an endpoint during an investigation |
| Submit a file for sandbox analysis | Submits a file to the Trend Micro Vision One sandbox for automated analysis |
| Retrieve sandbox analysis report | Retrieves the analysis report, IOCs, or artifacts available after automated analysis |
| Quarantine email message | Removes the specified email message from the user’s mailbox and places it in the mail quarantine |
| Delete email message | Permanently deletes the specified email message from the user’s mailbox |
| Gather information on an endpoint | Gathers information from the endpoint such as the current logged on user, operating system details, IP address, hostname, mac address |
| Terminate process | Terminates the specified process if currently running on an endpoint |
| Isolate endpoint | Blocks all network activity on an endpoint while the system is being investigated |
| Restore endpoint connection | Restores the network connectivity on an endpoint after investigation and/or remediation has occurred |
| Check action status | Checks the status of a triggered Trend Micro Vision One response action |
These actions lend the power of Trend Micro Vision One™ to analysts as they investigate and respond to incidents. All of these actions can be run manually or can be included in the organization’s pre-defined playbooks for automated response.
To demonstrate the value of these integrated platforms, let us walk through a use case where the combination of Trend Micro Vision One™ and Palo Alto Networks Cortex™ XSOAR improved a customer’s ability to investigate and respond to incidents.
Scenario: If credential dumping was detected on a host, the security operations team wanted to automate the collection of artifacts to be used during a subsequent investigation. Threat actors are very efficient at cleaning up their tracks to evade tracing, so this activity would need to be executed quickly.
Trend Micro Vision One™ is very effective at identifying the various techniques threat actors use to discover credentials. One commonly used technique that gets detected is the dumping of credentials via the Local Security Authority Server Service (LSASS) process in Microsoft Windows.

As you can see in this example, it was observed that Windows Task Manager was used to dump the LSASS process to a file. This file can then be analyzed by a threat actor to look for password hashes they can use as part of their attack. Security analysts may also want to examine the content of a credential dump to identify the account information the threat actor may have had access to. Trend Micro Vision One’s contextual response actions could be used to retrieve this information from the endpoint when reviewing an incident.

However, since threat actors tend to cover their tracks quickly, by the time the security analyst is reviewing the incident, there is a chance that critical information may have been permanently deleted and is no longer readily accessible.

Instead of depending on a security analyst to review a credential dumping event and manually collecting artifacts for their investigation, Trend Micro wanted to automate the collection of this evidence as quickly as possible when a detection occurs. This allows for information to be gathered prior to it being exfiltrated and destroyed.
To automate the retrieval of the dumped credentials, we leveraged the powerful integration between Trend Micro Vision One™ and Cortex™ XSOAR to create a playbook for this task.

1. The first step in our playbook is to check if the event is related to credential dumping. If not, there is no point in collecting any files from the endpoint, so we jump to the end.
2. We then use the “trendmicro-visionone-get-endpoint-info” integration command to gather information about the endpoint(s) where the detection occurred that will be used as inputs for commands that will run later. This would include things like the operating system and which Trend Micro product is deployed on the endpoint.

3. After we have gathered the information, the next step is to collect the file from the endpoint using the command “trendmicro-visionone-collect-forensic-file”. Outputs from the “trendmicro-visionone-get-endpoint-info” command will be passed to this command along with details from the incident about the files where the credentials were dumped.

4. We now need to wait for the complete collection of the file(s) so we will run the “trendmicro-visionone-check-status” command to continuously poll for the status of the file collection and wait until it is complete before moving on to the next step.

5. After the file has been collected, it is stored in the Trend Micro Vision One™ platform. We need to request that a download link be generated for the collected files with the “trendmicro-visionone-download-information-for-collected-forensic-file”. These download links are intended to be used quickly, or in automation tasks, and therefore have very short lifetimes.
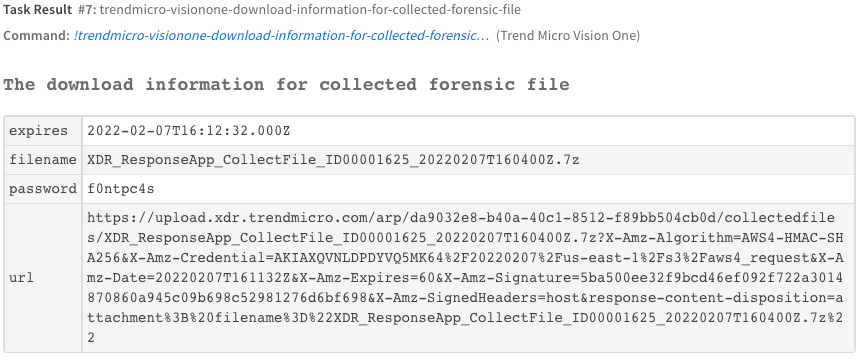
6. Once we have the download link, we can then use the Cortex™ XSOAR built-in command “http” to retrieve the file and save it to the War Room for this incident so that it can be downloaded and analyzed.

This is just one example use case that we have seen implemented to automate security operations by leveraging the integration between Trend Micro Vision One™ and Palo Alto Networks Cortex™ XSOAR. We look forward to seeing how many additional ways these integrated platforms can help organizations improve their security operations.
Why not take Trend Micro Vision One™ for a test drive to see how it can help you see more and respond faster to the threats your organization faces?
Copyright © 2022. Trend Micro Incorporated. All rights reserved. Trend Micro and the t-ball logo are registered trademarks of Trend Micro Incorporated. Cortex XSOAR is a trademark of Palo Alto Networks.

