Cyber Threats
Tech Support Scam Uses Iframe to Freeze Browsers
We discovered a new technical support scam (TSS) campaign that makes use of iframe in combination with basic pop-up authentication to freeze a user’s browser. Since this technique is new and unfamiliar, it can potentially evade detection.
We discovered a new technical support scam (TSS) campaign that makes use of iframe in combination with basic pop-up authentication to freeze a user’s browser. Since this technique is new and unfamiliar, it can potentially evade detection. Like many TSS campaigns, it disguises itself as a legitimate or well-known brand’s service provider to lure its victims. This campaign in particular uses Microsoft.
Evasion techniques
Its URLs show a webpage disguised to look like a typical Microsoft tech support page. However, it hides several different functions. Entering any of the involved URLs will open two pop-up windows: One that asks for user authentication and another that simply urges users to ask for technical support. By then the user has unknowingly entered a loop.
Clicking on the Cancel button of the authentication pop-up will only lead back to the URL. The close and OK buttons on the pop-up does not work or do anything, and are only likely there to make it look legitimate.
Figure 1. The frozen fake Microsoft support page used in the campaign
Creating a loop and freezing a browser is a common method used in TSS campaigns. The method that this campaign uses to freeze a user’s browser, along with its second evasion tactic, is what makes it unique. In a typical TSS campaign, cybercriminals would use the basic JavaScript codes alert() and confirm() to put the user in a loop where clicking on any pop-up button would simply take them back to the same pop-up window.
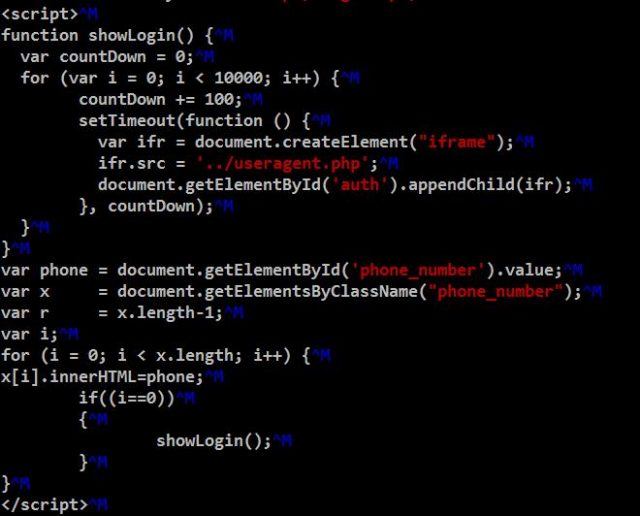
Instead, this campaign keeps adding iframes (an HTML document embedded in another HTML document). It is done by setting iframe as the page’s showLogin, making it appear when the URL is entered. Iframe’s source or contents, in turn, is the authentication page URL and therefore just returns the user to the URL.
Figure 2. Code showing the use of Iframe
Figure 3. A separated useragent.php or authentication pop-up used in the loop
This technique has a result that's similar to putting users in a loop — it constantly takes them back to the authentication URL and pop-up. TSS campaigns bank on the resulting panic caused by a frozen browser, which might push users to immediately act on the presented course of action, which usually involves calling the number on the screen and following whatever the supposed tech support agent might suggest.
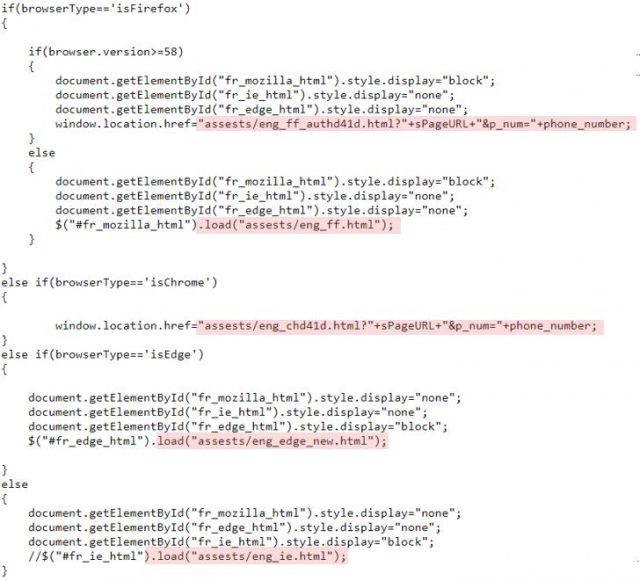
An additional feature of these URLs is that they show a different format depending on the browser version or type like Firefox, Chrome, Edge and others. This information is shown in its source code and highlighted in figure 4, likely just to adapt the campaign to different browsers.
Figure 4. Source code showing these URLs having different formats for different browsers
We’ve recorded that the URLs related to this campaign have been visited at most 575 times in a day, as can be seen in table 1. These recorded clicks were from several different URLs, as the other evasion technique this campaign employed involves changing its host IP address approximately 12 times a day. We don’t have enough evidence to conclusively say how these URLs are distributed, but if it follows past TSS campaigns, they are likely distributed through deployed advertisements.
Figure 5. Number of recorded daily hits of the URLs related to the campaign
Conclusion
Fortunately, the success of TSS attacks largely depends on how users respond to their tricks. As has been highlighted in this new campaign, users can look out for suspicious characteristics of a webpage, such as unfamiliar URLs, pop-ups asking for authentication, or any sort of information and messages that raise panic and alarm.
Users should remember that there are other ways to recover their browser. Users that encounter a similar attack can simply close the browser using Task Manager. If they are truly worried about the security of their device and system, they can find other legitimate means of confirming the status of their systems.
Users and businesses should consider adopting security solutions that can protect systems from various threats through a cross-generational blend of threat defense techniques. Trend Micro endpoint solutions such as the Smart Protection Suites and Worry-Free Business Security can protect users and businesses from threats by detecting malicious files and messages as well as blocking all related malicious URLs. Trend Micro™ Deep Discovery™ has an email inspection layer that can protect enterprises by detecting malicious attachments and URLs.
Indicators of Compromise (IoCs)
| URLs |
| hxxp://18[.]206[.]159[.]176/assests/eng_edge_new[.]html |
| hxxp://45[.]32[.]156[.]135/assests/eng_edge_new[.]html |
| hxxp://45[.]32[.]205[.]54/assests/eng_edge_new[.]html |
| hxxp://45[.]76[.]166[.]173/assests/eng_edge_new[.]html |
| hxxp://45[.]76[.]166[.]231/assests/eng_edge_new[.]html |
| hxxp://45[.]76[.]2[.]215/assests/eng_edge_new[.]html |
| hxxp://45[.]76[.]4[.]128/assests/eng_edge_new[.]html |
| hxxp://45[.]76[.]6[.]92/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]109[.]221/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]149[.]225/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]154[.]214/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]218[.]239/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]64[.]207/assests/eng_edge_new[.]html |
| hxxp://45[.]77[.]67[.]129/assests/eng_edge_new[.]html |
| hxxp://80[.]240[.]16[.]81/assests/eng_edge_new[.]html |
| hxxp://80[.]240[.]19[.]216/assests/eng_edge_new[.]html |
| hxxp://95[.]179[.]167[.]173/assests/eng_edge_new[.]html |
| hxxp://95[.]179[.]168[.]138/assests/eng_edge_new[.]html |
| hxxp://140[.]82[.]36[.]155/assests/eng_edge_new[.]html |
| hxxp://140[.]82[.]38[.]211/assests/eng_edge_new[.]html |
| hxxp://140[.]82[.]42[.]6/assests/eng_edge_new[.]html |
| hxxp://140[.]82[.]46[.]46/assests/eng_edge_new[.]html |
| hxxp://140[.]82[.]9[.]45/assests/eng_edge_new[.]html |
| hxxp://149[.]28[.]36[.]182/assests/eng_edge_new[.]html |
| hxxp://149[.]28[.]45[.]200/assests/eng_edge_new[.]html |
| hxxp://149[.]28[.]56[.]4/assests/eng_edge_new[.]html |
| hxxp://199[.]247[.]3[.]159/assests/eng_edge_new[.]html |
| hxxp://207[.]246[.]127[.]175/assests/eng_edge_new[.]html |
| hxxp://216[.]155[.]135[.]180/assests/eng_edge_new[.]html |