Update as of 18 August, 2:54 a.m. EDT: We updated the section "Trend Micro Vision One™ Hunting Queries" (search queries) to include the latest indicators. Specifically, Figures 21 and 25 address events for the latest PrintNightmare implementation under CVE-2021-36958.
PrintNightmare is one of the latest set of exploits abused for the Print Spooler vulnerabilities that have been identified as CVE-2021-1675, CVE-2021-34527, CVE-2021-34481, and CVE-2021-36958. It is a code execution vulnerability (both remote and local) in the Print Spooler service that affects all Windows versions running the said service. A number of researchers have come up with multiple exploit variants based on different implementations (over TCP and Server Message Block or SMB). By using different function calls for Print System Asynchronous Remote Protocol (MS-PAR) misusing RpcAsyncAddPrinterDriver, PrintNightmare can be exploited on servers and workstations, while abusing Print System Remote Protocol (MS-RPRN) allows PrintNightmare to misuse RpcAddPrinterDriverEx for an impacket implementation.
In this analysis, we look into the implementations of PrintNightmare and the visibility enabled by Trend Micro Vision One™ and Trend Micro Cloud One™ to mitigate the risks brought on by critical gaps found in systems such as the Print Spooler service. Using the indicators and attributes of exploitation attempts logged from network and endpoints, both platforms allow security teams and analysts a wider view of attack attempts for immediate and actionable response.
The timeline of PrintNightmare is as follows:
1. 8 June: As part of the June security update, the bug identified as an elevation of privilege (EOP) in the Print Spooler service was patched. The vulnerability was tagged as CVE-2021-1675.
2. 21 June: The same bug was later classified as both a remote code execution (RCE) and an EOP vulnerability.
3. 29 June: Researchers with different RCE and EOP proofs of concept accidentally disclosed these publicly as a result of the assumption that their findings were exactly the same and that the bug had already been mitigated as part of the June security update. However, it had not been mitigated yet, and though the researchers deleted their proofs of concept, these had already been replicated and eventually cached by search engines.
4. 1 July: A new vulnerability, considered a zero-day flaw, was assigned as CVE-2021-34527.
5. 6 July: Microsoft released an out-of-band patch to mitigate CVE-2021-34527, but it only prevented a part of the RCE. Specifically, the patch only blocked DLLs from path implementations like “\\server\share\”.
6. 7 July: Researchers reported the bypass, along with information that the universal naming convention (UNC) form of denoting paths, “\??\UNC\”, rather than the use of “\\”, could evade the patch.
7. 15 July: Microsoft disclosed that a new EOP vulnerability in the Print Spooler service was found and assigned it as CVE-2021-34481.
8. 10 August: Microsoft updated CVE-2021-34481 and released the patches to prevent exploitation.

Following the different implementations and proofs of concept that are already out in the public, here we detail our observations of PrintNightmare. In the following sections, we identify the potential indicators of compromise (IOCs) in a user’s environment, as well as the protection and visibility offered by both Trend Micro Vision One and Trend Micro Cloud One platforms.
Print Spooler Service
The Print Spooler service enables clients and servers to carry out tasks related to printing. On a print server, the Spooler shares print queues that are exposed to print clients. On a print client, the Spooler service exposes printing APIs to applications, receives the print output of an application, and sends it to a shared print queue or a print server.

To view the details of the Spooler service, we use Sysinternals’ Process Explorer, wherein the binary (“spoolsv.exe”) runs with the highest privilege (that is, the privilege of the SYSTEM user). The service has been riddled with vulnerabilities in the past, and successful exploitation can lead to code execution in the context of the system user. The vulnerabilities revolve around how Print Spooler loads printer drivers. Since the service itself runs with the highest privilege, the code execution also occurs in the highest privilege.
There has been an indication from the Cybersecurity and Infrastructure Security Agency (CISA) regarding the active exploitation of this vulnerability by threat actors. Since the attack is network-based, it can be executed even by other users with lower system privileges since the spooler service is not disabled by default on most machines (such as domain controllers and print servers). Upon exploiting this vulnerability, an attacker can execute code in the context of the system, making the vulnerability a go-to technique to escalate privileges.
Routine
We observed that there are a few indicators suggesting potential exploitation. We detail them in this section for future reference with regard to ensuring robust protection.

The exploitation of the Spooler service can be broken down into the following:
1. The vulnerability in the Print Spooler service is exploited by the attacker.
2. A malicious DLL file on the attacker-controlled SMB share is accessed by the victim machine.
3. The DLL file is written to the disk.
4. The DLL file is loaded and executed by the Print Spooler service.
5. In cases where the DLL file is malformed, the Print Spooler service crashes.
6. Based on the DLL code, command and control (C&C) or privilege escalation is observed.
In case event logging for the Print Spooler service is not enabled by default, we advise administrators and/or users to enable it using the following PowerShell command:
$logs = Get-LogProperties 'Microsoft-Windows-PrintService/Operational' $logs.Enabled = $true Set-LogProperties -LogDetails $logs |
Administrators can also navigate to “Application and Services” logs and enable both Admin and Operational events to detect attempts of abuse.

Upon the exploitation of PrintNightmare, we observed the following activities logged on the vulnerable machine. The malicious DLL file is fetched from the attacker-controlled SMB share and written to the disk of the targeted machine. When a DLL file is injected into the memory of a process (in this case “spoolsv.exe”), then the operation “Load Image” is observed on Process Monitor. Once the DLL is loaded in the process, the malicious code is executed.


The attack is made up of two stages:
A. Stage 0
1. The DLL path in the SMB share makes a single call to “RpcAddPrinterDriver” with the value of “pDataFile”.
2. The DLL is looked for in the path “%windir%\System32\spool\drivers\x64\3\”.
3. A new file handle is opened at “%windir%\System32\spool\drivers\x64\3\New\<name_of_dll>.dll”.
4. Once the “WriteFile” operation has been completed, the path is renamed to “%windir%\System32\spool\drivers\x64\3\<name_of_dll>.dll”.
5. The DLL finally resides at the aforementioned renamed path.

A. Stage 1
1. After completing stage 0, the DLL already resides at the path “%windir%\System32\spool\drivers\x64\3\”.
2. To load the DLL in the Print Spooler service, the “RpcAddPrinterDriver” call is done, specifying the “pConfigFile” as the local path to the uploaded DLL.
3. When the DLL is loaded in the process “spoolsv.exe”, the “Load Image” operation is observed.


Using Process Explorer, we see the process lineage identifying the order in which the processes have been spawned. When “spoolsv.exe” loads the malicious DLL, rundll32 executes the DLL. Based on the code of the DLL (in this case, it will give a reverse shell to the attacker), “cmd.exe” is spawned from “rundll32.exe”, which in turn is spawned from “spoolsv.exe”. From the process lineage, analysts and IT teams can understand where a certain activity originates. This is also helpful in narrowing the processes involved in threat hunting.

When there are attempts to load a DLL in the Print Spooler service, the following event IDs are observed in the event logs for printer service:
1. When the DLL is malformed, event ID 808 is observed from the event source “Microsoft-Windows-PrintService/Operational”. Here we see the path to the DLL that is malformed in the details, indicating that Print Spooler failed to load the malicious DLL. This event ID is a high-confidence indicator of a possible PrintNightmare exploitation (Stage 1).

2. When a new printer driver is added or updated in the Print Spooler, event ID 316 is observed. We can see the name of the DLL file in the details, and the event is logged for both successful and unsuccessful attempts of exploitation (Stage 0).

Trend Micro Cloud One™ – Workload Security
The modules in this section are packaged in a single bundle as part of the Trend Micro Deep Security Agent (DSA). To know more about the onboarding of Cloud One and Trend Micro Vision One, check our guide here.
From your Trend Micro Cloud One console, enable the following modules with the following configuration:
1. Antimalware module with real-time scanning turned on
2. Log Inspection module: Rule 1011017 - Microsoft Windows - Print Spooler Failed Loading Plugin Module (PrintNightmare)
3. Intrusion prevention system (IPS) module in “Prevent Mode”
a. Rule 1011016 - Identified DCERPC AddPrinterDriverEx Call Over TCP Protocol
b. Rule 1011018 - Identified DCERPC AddPrinterDriverEx Call Over SMB Protocol
4. Activity monitoring
The modules enable insight into the workloads and provide visibility for the events that we observed previously. We leverage the detections in a comprehensive manner in Trend Micro Vision One. The images and descriptions in the following section illustrate how the detections appear on the platform once enabled.
Cloud One Detections
The Log Inspection rule “1011017 - Microsoft Windows - Print Spooler Failed Loading Plugin Module (PrintNightmare)” is triggered when a malformed DLL is loaded by the Print Spooler service. The event source is seen as “Microsoft-Windows-PrintService/Admin” and the event ID is 808.

The implementations MS-RPRN and MS-PAR of PrintNightmare trigger the IPS events log when the agreed dialect for communication between the attacker and the victim is SMBv1 or SMBv2 without encryption.

Additionally, the antimalware module is triggered when there are known malicious signatures observed in the DLL created on the disk. The advanced File Reputation Services, along with Trend Micro™ Smart Protection Network™ (SPN), enables real-time monitoring of new files being created on the machine and flags malicious files based on patterns maintained by SPN.

Trend Micro Vision One™ Workbench App


Looking at the Trend Micro Vision One Workbench’s root cause analysis (RCA), we see the process lineage where “msfvenom.dll” was created by the Print Spooler service (“spoolsv.exe”). This was followed by the spawning of “rundll32.exe”, which executes the malicious DLL.
Upon execution, there is a callback from the child process of the Print Spooler service to the attacker machine that has a meterpreter handler listening on port 4444. Upon getting the meterpreter callback, we drop a command prompt (“cmd.exe”) shell and run “whoami”.
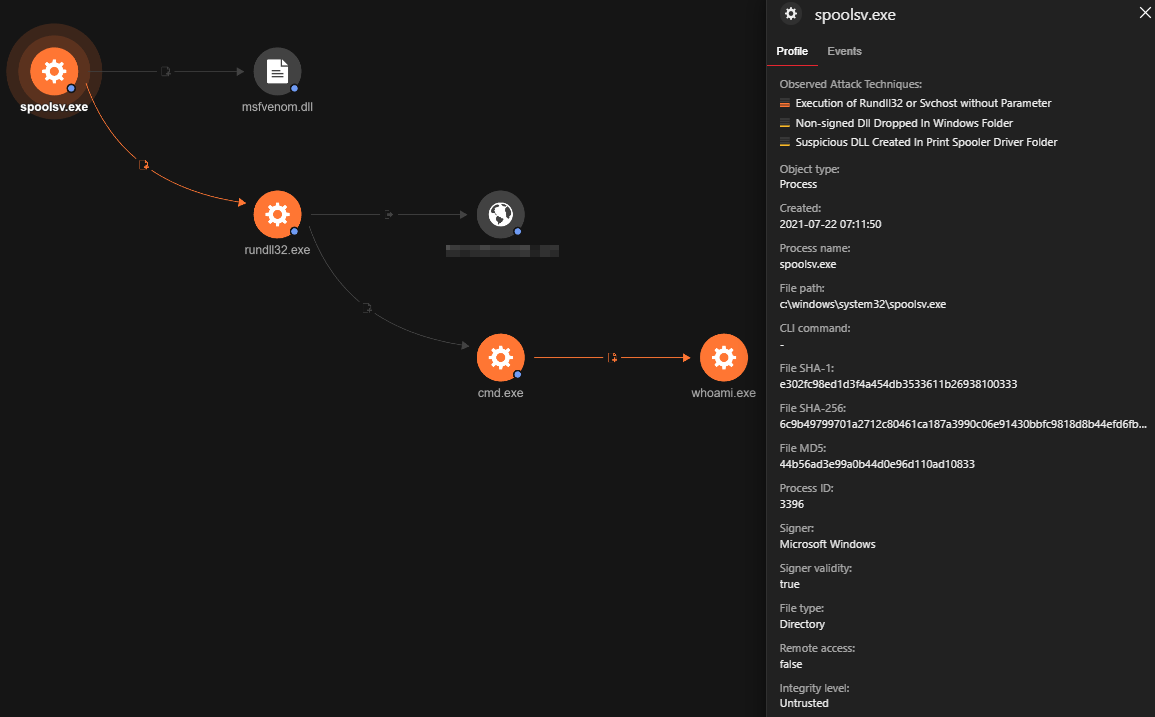
Every single object shown in the RCA has specific attributes associated with them. For example, the object “msfvenom.dll” is associated with the following Observed Attack Techniques (OATs): “Suspicious DLL Created In Print Spooler Driver Folder” and “Non-signed DLL Dropped In Windows Folder,” as seen on the upper right-hand corner of Figure 18.
We also highlight the hash of the DLL, which can be subsequently used to look up possible occurrences within the organisation. Other fields such as “First Seen,” “Last Seen,” and empty “Signer” fields give more insights into the metadata of the DLL.

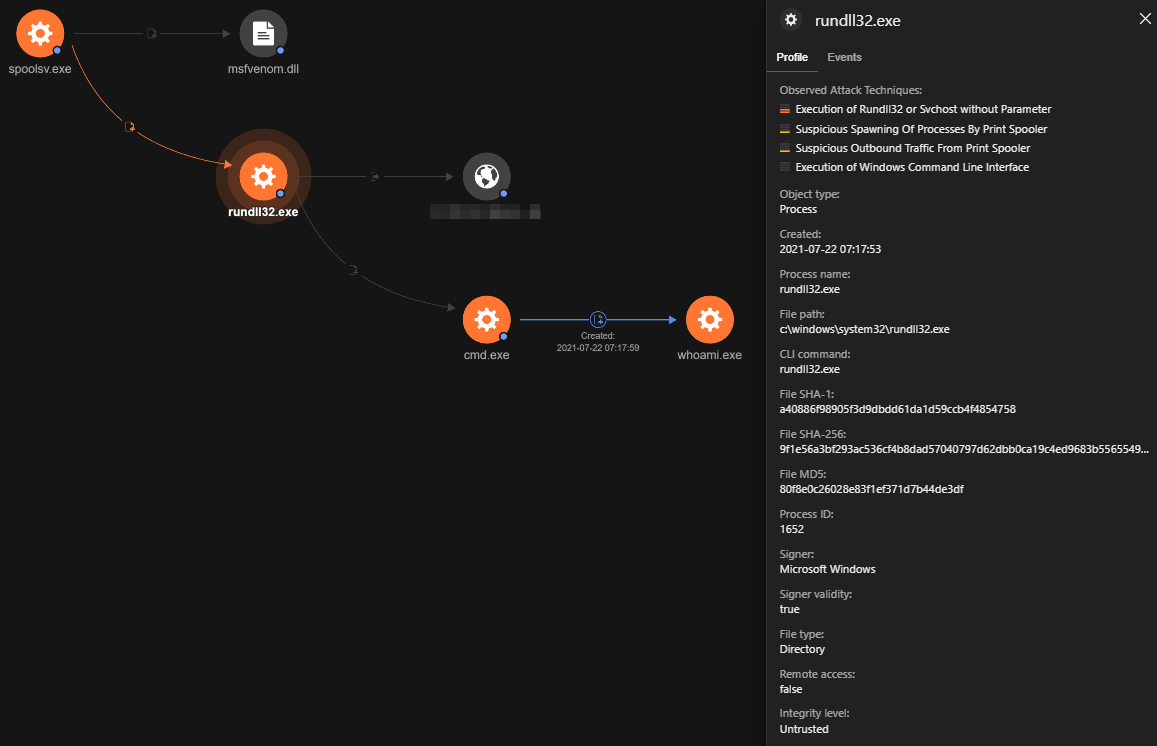
The RCA shows the activities observed from the executable “rundll32.exe” in the Print Spooler service. From the log, we can understand the following:
1. The executable “rundll32.exe” came from “spoolsv.exe”.
2. This event was followed by an outbound connection originating from “rundll32.exe”.
3. Four seconds after the outbound activity was observed, “cmd.exe” was spawned from “rundll32.exe”.
4. Two seconds after “cmd.exe” was observed, “whoami” was run by the attacker.
Trend Micro Vision One™ Hunting Queries
To hunt down potential IOCs in the environment from PrintNightmare, the following Trend Micro Vision One search queries are useful:
1. Creation of new DLL files under “%windir%\spool\drivers”
eventSubId:101 AND (objectFilePath:\\windows\\system32\\spool\\drivers AND objectFilePath:*.dll)

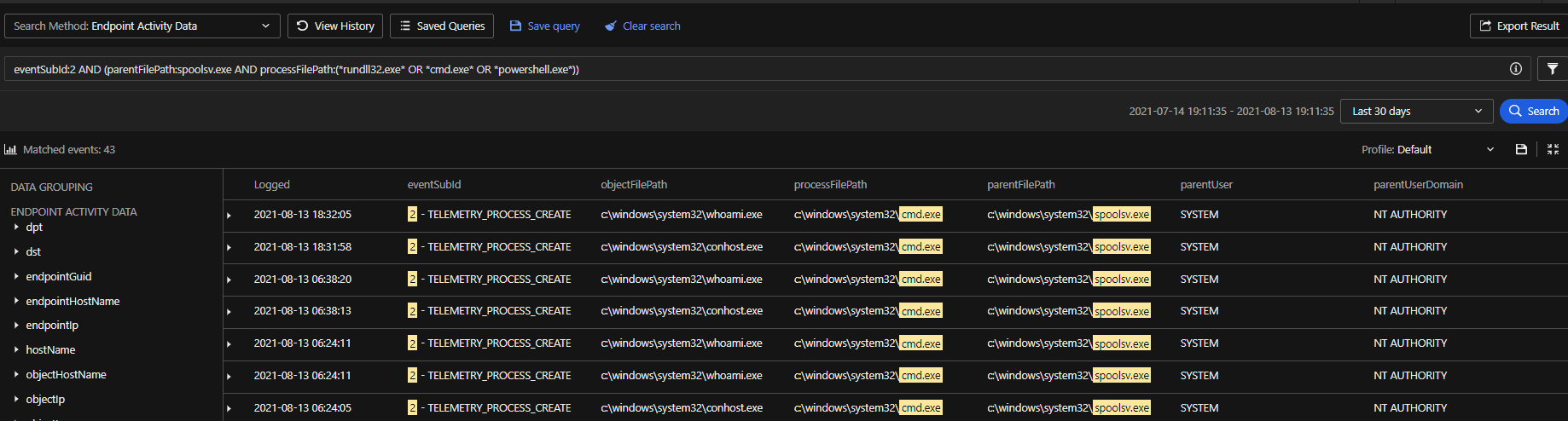
2. Spawning of suspicious processes from the Print Spooler service
eventSubId:2 AND (parentFilePath:spoolsv.exe AND processFilePath:(*rundll32.exe* OR *cmd.exe* OR *powershell.exe*))
3. Outbound connections originating from child processes of the Print Spooler service
eventSubId:204 AND parentFilePath:spoolsv.exe AND (processFilePath: (*cmd.exe* OR *powershell.exe* OR *rundll32.exe*))

4. Malware detection from the file path ‘\\Windows\\System32\\spool\\drivers\\x64\\3\\’
eventName: "MALWARE_DETECTION" AND
filePath:\\Windows\\System32\\spool\\drivers\\x64\\3

5. Finding the malformed DLL loaded in Print Spooler service
eventName:"LOG_INSPECTION_EVENT" AND ruleName:*PrintNightmare*

Conclusion
PrintNightmare started out as a confusion among individual studies by security researchers, ranging from incoherent disclosures to the bypassing of official patches. Proofs of concept have already been accommodated in various frameworks like the Metasploit Framework (MSF) and tools like Mimikatz. Additionally, exploitation of PrintNightmare will soon become an attacker’s go-to method for privilege escalation and lateral movement since the attack vector contains both RCE and local privilege escalation capabilities, does not require user interaction, and can be triggered from the context of a low-privileged user.
Since the Print Spooler service is enabled by default on most Windows versions and is left open in most corporate environments, there is an increased susceptibility for exploitation by a malicious actor. If there is a compromised endpoint in an Active Directory (AD) environment, the threat actor can get the highest privilege on any system (including domain controllers and print servers) running the Print Spooler service.
Through this blog, we attempt to describe how the advanced visibility provided by Trend Micro Vision One and Trend Micro Cloud One thwarts attacks that abuse such critical vulnerabilities. We take into account metrics from the network and endpoints that would indicate potential attempts of exploitation. The Trend Micro Vision One Workbench shows a holistic view of the activities that are observed in a user’s environment by highlighting important attributes related to the attack. Using the RCA feature, a user can look into the details of the attack per step. Lastly, Trend Micro Smart Protection Network (SPN) for threat intelligence creates a lookout for recent advanced threats that are at large to keep users’ assets safe.

