Status: Deprecated Ensure that Amazon Web Application Firewall (WAF) service is currently in use in order to protect your AWS-powered web applications from security exploits that could affect their availability and overall security, or consume excessive resources (resource starvation attacks). Amazon WAF is a web application firewall service that lets you monitor any HTTP(S) requests that are forwarded to AWS CloudFront or AWS ELB. To enable AWS WAF protection you simply create web Access Control Lists (ACLs), define the ACLs rules, which reference one or more conditions, and the actions to take when each rule is satisfied. Then the newly created WAF ACLs can be attached, for example, to the Amazon CloudFront CDN distribution used by your web applications. To quickly get started with AWS WAF you can also use AWS Pre-configured Protections, an automated solution that consists of a pre-configured AWS WAF template that includes a set of predefined ACL rules, which can be customized to best fit your requirements, designed to block common web-based attacks such as bad bots, Cross-Site Scripting and SQL Injection.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
- Using AWS Web Application Firewall (WAF) service can have a significant impact on the security and availability of the websites/web applications running within your AWS environment. The main benefits of using Amazon WAF are: strong protection against common web-based attacks – safeguards your web applications from SQL Injection (SQLi) attacks, Cross-site scripting (XSS) attacks, Cross-Site Request Forgery (CSRF) and HTTP Flood (DDOS-based) attacks by filtering incoming traffic based on the firewall rules that you create, improved web traffic visibility – provides real-time visibility into your web traffic, insight data that can be used to create custom rules and set alerts in AWS CloudWatch, ease of deployment and maintenance – deploys easily without the need for additional software and provides a full-featured API that you can use to automate the creation, deployment, and maintenance of your web security rules, integrate well with your applications development process – allows you to define application-specific rules that increase security as you develop your web apps, and cost effective – you pay only for what you use as the pricing is based on how many rules you create and how many requests your web applications receive, there are no upfront commitments nor minimum fees.
Audit
To determine if AWS WAF is used as web application firewall service within your AWS account, perform the following:
Remediation / Resolution
In order to enable AWS WAF as the web firewall service to protect your AWS-powered web applications from security exploits, you must create one or more web ACLs, each ACL containing rules and actions to perform when a rule is satisfied. Once the necessary rules and actions are defined, the new web ACL can be assigned to the CloudFront distribution used by your web application as CDN solution or to the Application Load Balancer, managed by the AWS ELB service, used by your application as load balancing solution. To create and assign your first AWS WAF web ACL, perform the following:
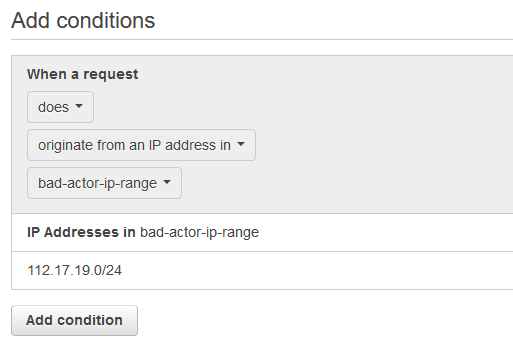
Note: As example, this conformity rule demonstrates how to enable AWS WAF to protect a web application associated with a global AWS Cloudfront distribution from exploits that originate from an IP range that is known to be operated by malicious actors such as spammers, botnets and malware distributors.(Optional): To associate the web ACL created earlier with other CloudFront web distributions (other than the one selected during the ACL setup), perform the following actions:
References
- AWS Documentation
- AWS WAF - Web Application Firewall
- What Is AWS WAF and AWS Shield?
- Preconfigured Rules & Tutorials
- AWS WAF Security Automations
- What Is AWS WAF and AWS Shield?
- Working with Web ACLs
- Values that You Specify When You Create or Update a Web Distribution
- AWS Command Line Interface (CLI) Documentation
- waf
- list-web-acls
- get-change-token
- create-ip-set
- update-ip-set
- create-rule
- create-web-acl
- update-web-acl
- cloudfront
- get-distribution-config
- update-distribution
- AWS Blog(s)
- New – AWS WAF